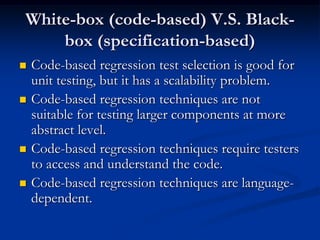
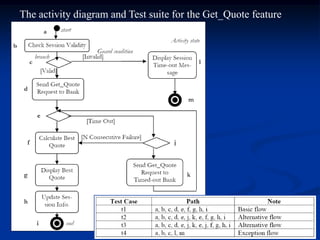
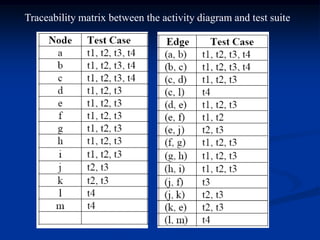
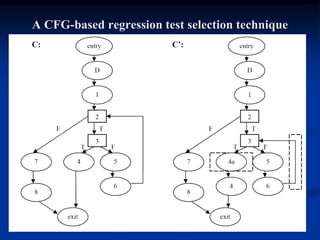
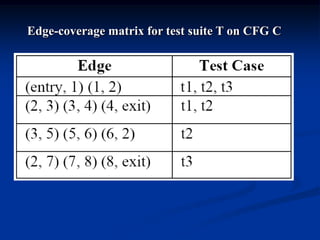
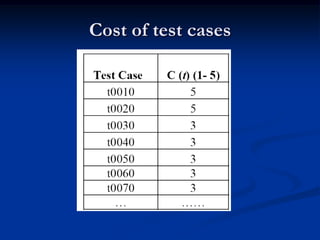
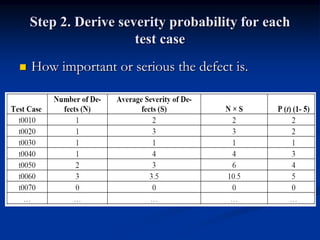
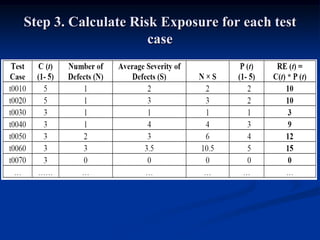
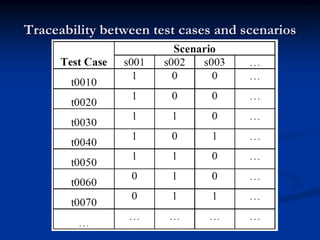
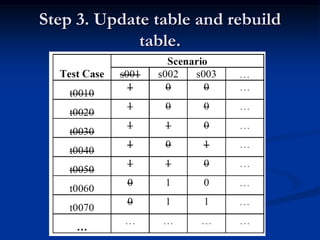
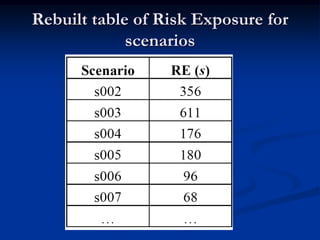
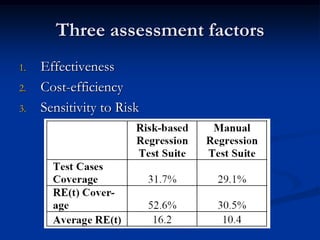
This document describes a specification-based regression test selection technique with risk analysis. It selects targeted tests to cover changes in code or specifications, and safety tests directed by risk analysis. Safety tests are chosen using a risk exposure model factoring probability and cost of faults. Scenarios simulating user profiles are also selected based on their risk exposure covering critical test cases. The approach was evaluated on an IBM project and found effective, cost-efficient, and sensitive to risk. Future work includes determining when to stop testing and implementing the approach in a production environment.