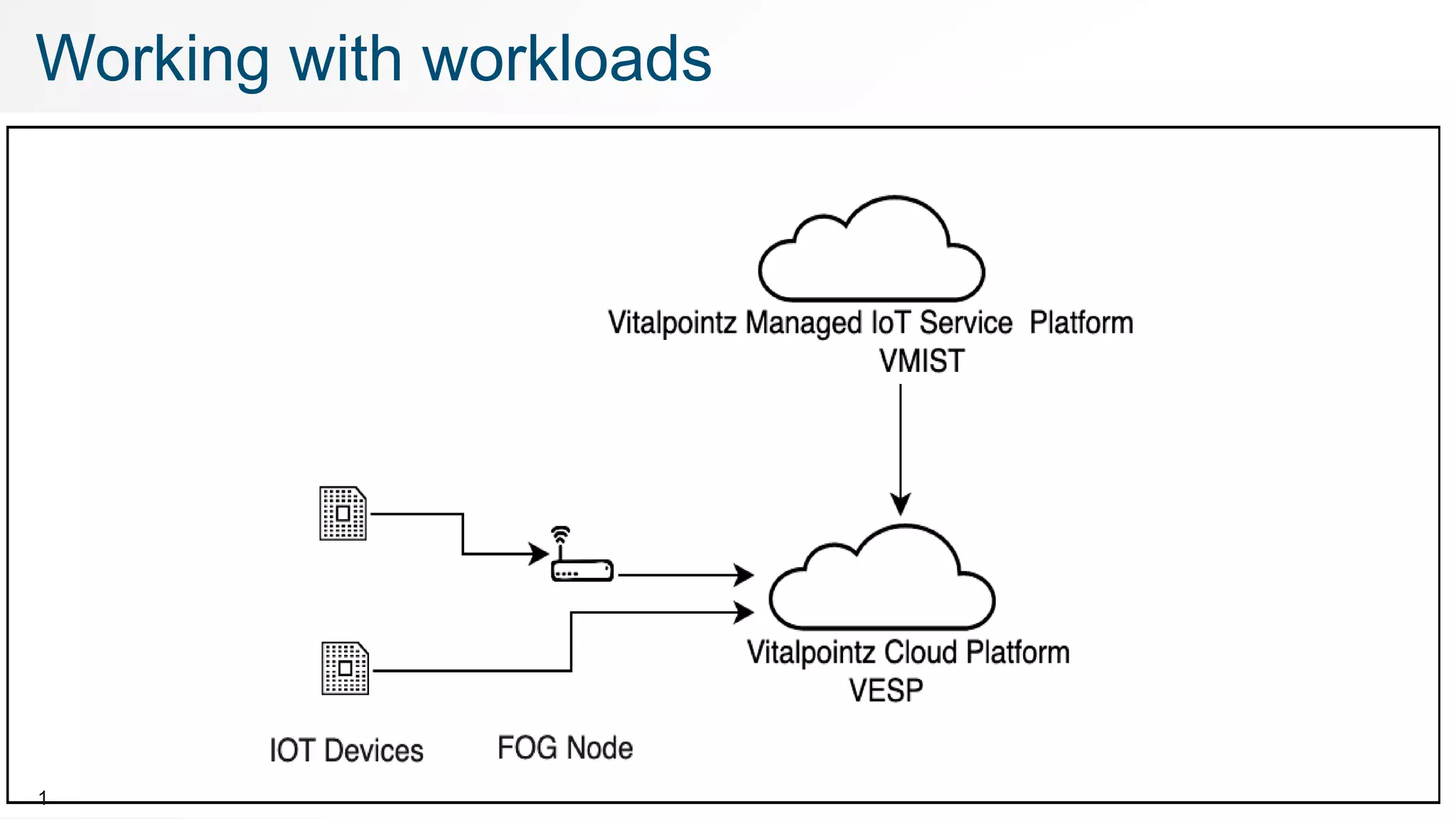
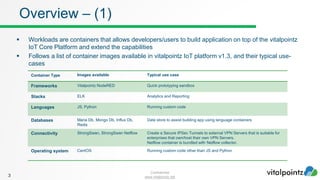
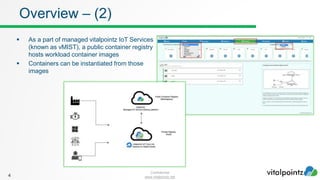
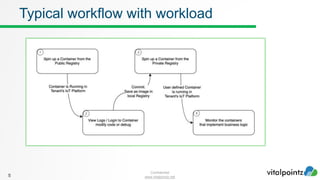
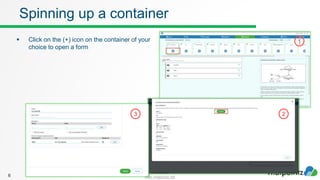
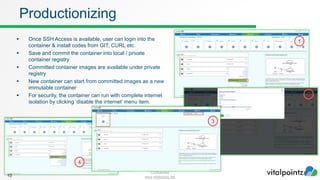
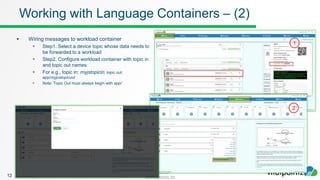
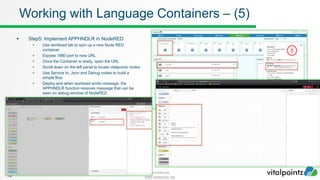
The document discusses how to work with workloads in the vitalpointz IoT Core platform. It describes that workloads allow developers to build applications using container images provided in the platform. These include frameworks like NodeRED, databases like MariaDB and MongoDB, and operating systems like CentOS. The typical workflow to use a workload involves selecting an image, configuring settings like ports and volumes, and wiring rules to route device messages to the container. Language containers can then process messages and return responses. Workloads allow custom code deployment and integration with devices and functions on the platform.