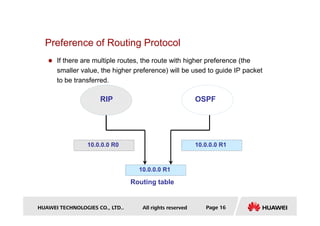
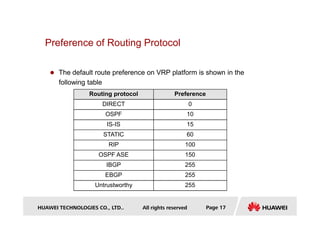
This document provides an overview of routing protocols and concepts:
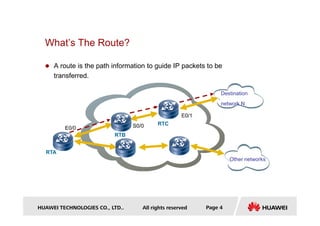
- It defines what a route is and explains that routing protocols are used to exchange route information between routers to direct packet flow.
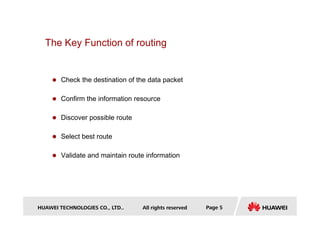
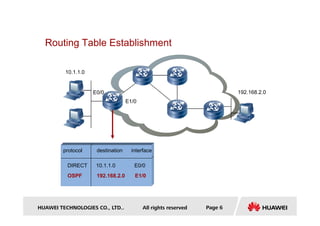
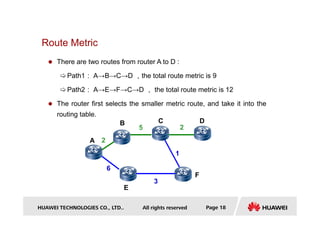
- Key concepts covered include the routing table, static and dynamic routes, classification of routing protocols by area and algorithm, and route metrics.
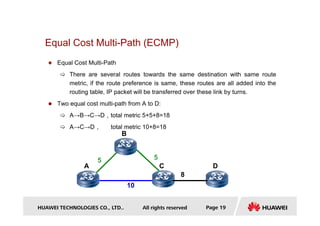
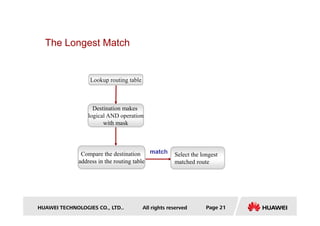
- It also discusses routing protocol preference, equal cost multi-path routing, and the longest prefix match method used to select routes.



![Routes—Discovered by Data Link Layer
[RTB]display ip routing-table
Routing Tables: Public
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost NextHop Interface
10.1.1.0/30
RTA
10.1.2.0/24
.1
.1 .2
.2
RTB
HUAWEI TECHNOLOGIES CO., LTD.. All rights reserved Page 7
Destination/Mask Proto Pre Cost NextHop Interface
10.1.1.0/30 Direct 0 0 10.1.1.1 Serial0/0/0
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoopBack0
……
10.1.2.1/32 Direct 0 0 127.0.0.1 InLoopBack0
10.1.2.2/32 Direct 0 0 10.1.2.2 Serial0/0/1
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoopBack0
RTC](https://image.slidesharecdn.com/2routingprotocolbasis-220729143141-71b4e9d9/85/2-Routing-Protocol-Basis-pdf-7-320.jpg)
![Routes—Static Route
[RTA] display ip routing-table
Routing Tables: Public
RTB
2.2.2.2/32
10.1.1.0/30
RTA
.1 .2
Configure static route towards
destination network 2.2.2.2/32
HUAWEI TECHNOLOGIES CO., LTD.. All rights reserved Page 8
Routing Tables: Public
Destinations : 8 Routes : 8
Destination/Mask Proto Pre Cost NextHop Interface
2.2.2.2/32 Static 60 0 10.1.2.2 Ethernet0
10.1.1.0/30 Direct 0 0 10.1.1.1 Serial0
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoopBack0
10.1.1.2/32 Direct 0 0 10.1.1.2 Serial0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoopBack0](https://image.slidesharecdn.com/2routingprotocolbasis-220729143141-71b4e9d9/85/2-Routing-Protocol-Basis-pdf-8-320.jpg)
![Routes—Discovered by Dynamic Routing
Protocol
[RTB]display ip routing-table
Routing Tables: Public
10.1.2.0/24
.1
OSPF
RIP
RTA
RTC
172.16.1.1/32
.2
HUAWEI TECHNOLOGIES CO., LTD.. All rights reserved Page 9
Routing Tables: Public
Destinations : 10 Routes : 10
Destination/Mask Proto Pre Cost NextHop Interface
10.1.1.0/30 Direct 0 0 10.1.1.2 Serial0/0/0
10.1.1.1/32 Direct 0 0 10.1.1.1 Serial0/0/0
……
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoopBack0
172.16.1.1/32 OSPF 10 1563 10.1.2.2 Serial0/0/1
192.168.1.0/24 RIP 100 1 10.1.1.1 Serial0/0/0
10.1.1.0/8
RTB
.1
192.168.2.1/24
.2](https://image.slidesharecdn.com/2routingprotocolbasis-220729143141-71b4e9d9/85/2-Routing-Protocol-Basis-pdf-9-320.jpg)

![Routing Table
[Quidway] display ip routing-table
Routing Tables:
Destination/Mask proto pref Metric Nexthop Interface
0.0.0.0/0 Static 60 0 120.0.0.2 Serial0/0
8.0.0.0/8 RIP 100 3 120.0.0.2 Serial0/1
HUAWEI TECHNOLOGIES CO., LTD.. All rights reserved Page 15
8.0.0.0/8 RIP 100 3 120.0.0.2 Serial0/1
9.0.0.0/8 OSPF 10 50 20.0.0.2 Ethernet0/0
9.1.0.0/16 RIP 100 4 120.0.0.2 Serial0/0
11.0.0.0/8 Static 60 0 120.0.0.2 Serial0/1
20.0.0.0/8 Direct 0 0 20.0.0.1 Ethernet0/2
20.0.0.1/32 Direct 0 0 127.0.0.1 LoopBack0](https://image.slidesharecdn.com/2routingprotocolbasis-220729143141-71b4e9d9/85/2-Routing-Protocol-Basis-pdf-15-320.jpg)
![Equal Cost Multi-Path
[RTB] display ip routing-table
Routing Tables: Public
Destinations : 13 Routes : 15
Destination/Mask Proto Pre Cost NextHop Interface
3.3.3.0/24 Direct 0 0 3.3.3.2 Serial2
3.3.3.1/32 Direct 0 0 3.3.3.1 Serial2
3.3.3.2/32 Direct 0 0 127.0.0.1 InLoopBack0
HUAWEI TECHNOLOGIES CO., LTD.. All rights reserved Page 20
10.1.1.1/32 Static 60 0 1.1.1.1 Serial0
Static 60 0 2.2.2.1 Serial1
Static 60 0 3.3.3.1 Serial2
20.1.1.1/32 Direct 0 0 127.0.0.1 InLoopBack0
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoopBack0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoopBack0
Equal Cost Multi-Path
realizes load-balance](https://image.slidesharecdn.com/2routingprotocolbasis-220729143141-71b4e9d9/85/2-Routing-Protocol-Basis-pdf-20-320.jpg)
![The Example of Longest Match
[Quidway] display ip routing-table
Routing Tables:
Destination/Mask proto pref Metric Nexthop Interface
0.0.0.0/0 Static 60 0 120.0.0.2 Serial0/0
The data packet of destination 9.1.2.1 will match the route 9.1.0.0/16
HUAWEI TECHNOLOGIES CO., LTD.. All rights reserved Page 22
8.0.0.0/8 RIP 100 3 120.0.0.2 Serial0/1
9.0.0.0/8 OSPF 10 50 20.0.0.2 Ethernet0/0
9.1.0.0/16 RIP 100 4 120.0.0.2 Serial0/0
11.0.0.0/8 Static 60 0 120.0.0.2 Serial0/1
20.0.0.0/8 Direct 0 0 20.0.0.1 Ethernet0/2
20.0.0.1/32 Direct 0 0 127.0.0.1 LoopBack0](https://image.slidesharecdn.com/2routingprotocolbasis-220729143141-71b4e9d9/85/2-Routing-Protocol-Basis-pdf-22-320.jpg)