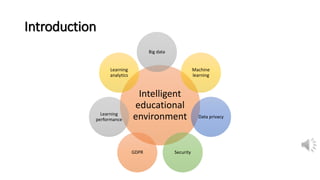
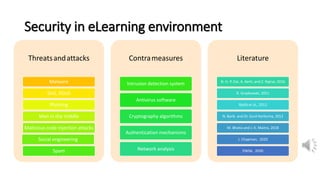
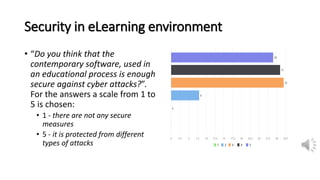
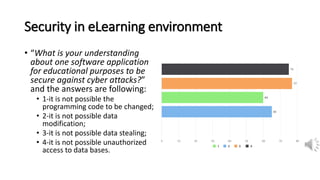
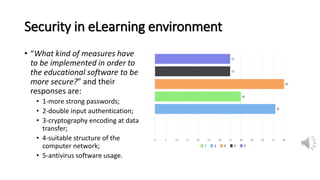
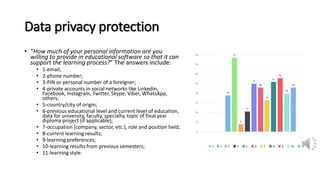
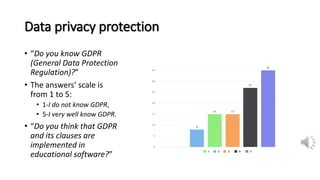
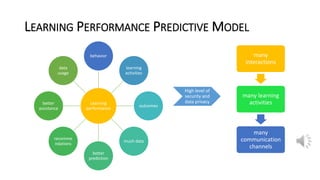
The document discusses security, data privacy, and learning performance in eLearning environments. It presents a predictive model created using machine learning to analyze the relationships between these factors. A survey was conducted of students to understand their perspectives on security of educational software, data privacy, and the value of intelligent learning environments. The results showed students believe software security has improved but cyberattacks remain a risk. Students are willing to share personal data to benefit from intelligent assistance and recommendations. Ensuring privacy through technical and policy approaches like GDPR is important to support learning performance. The predictive model accurately characterizes these relationships to help learning.