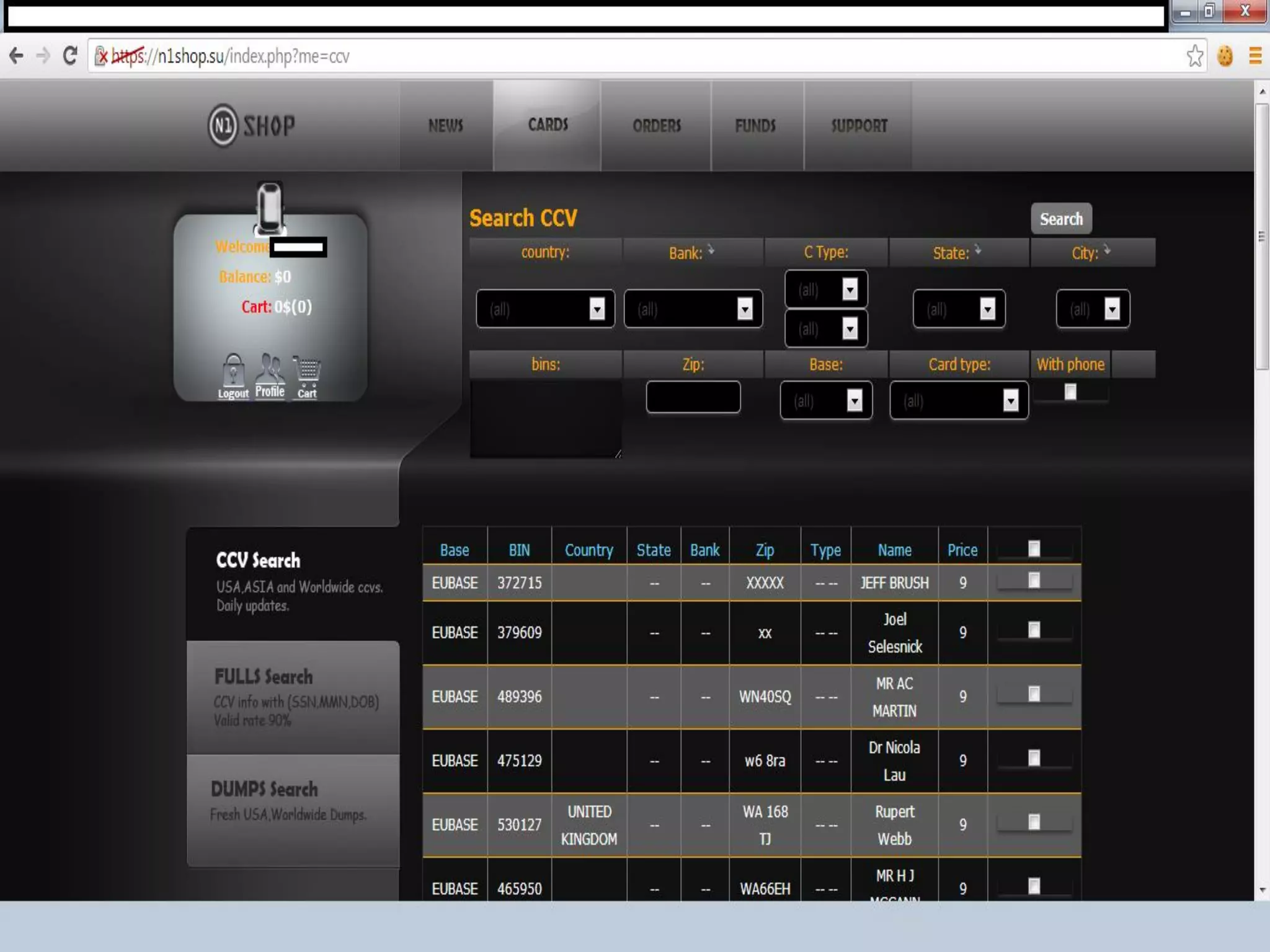
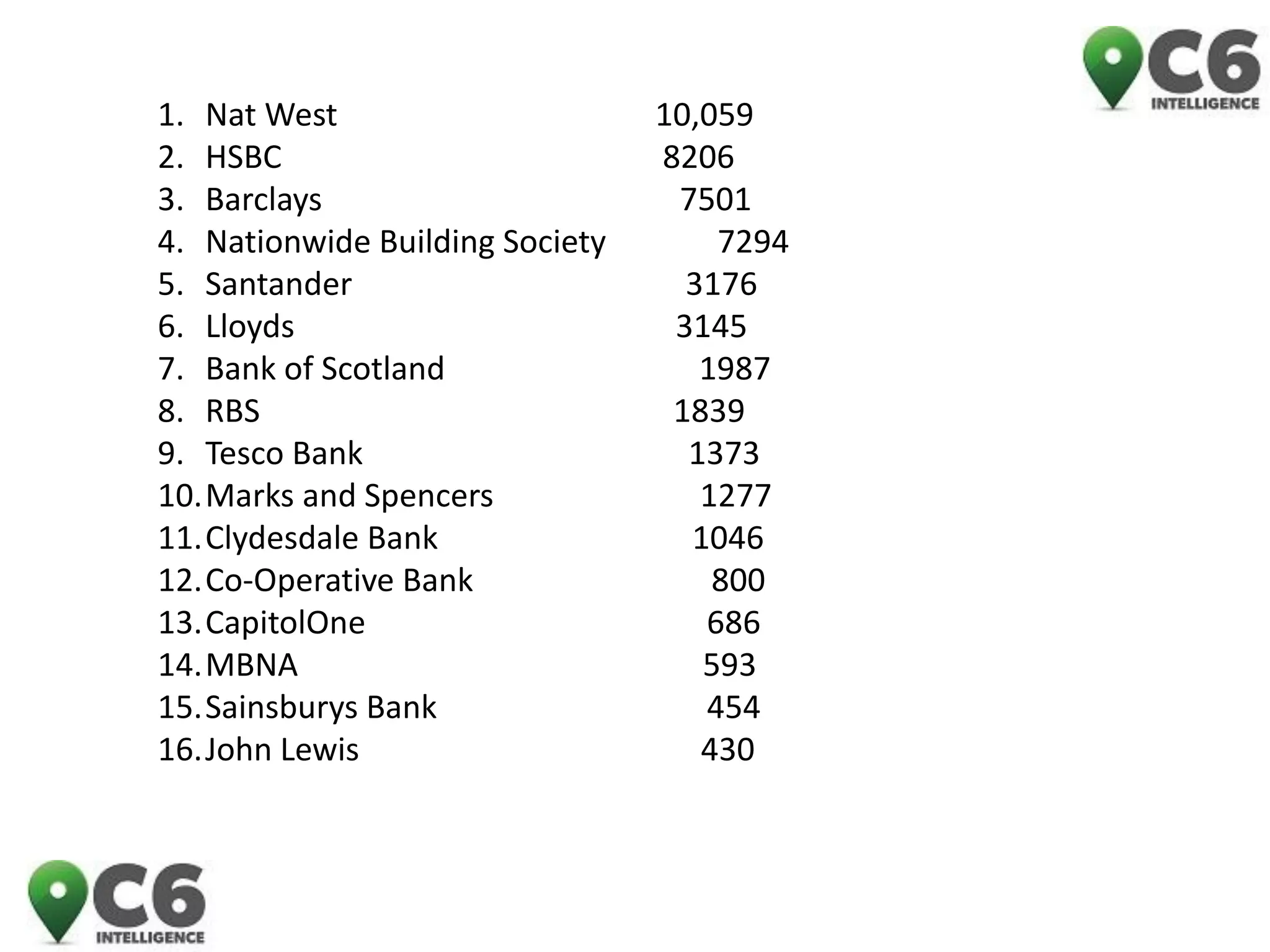
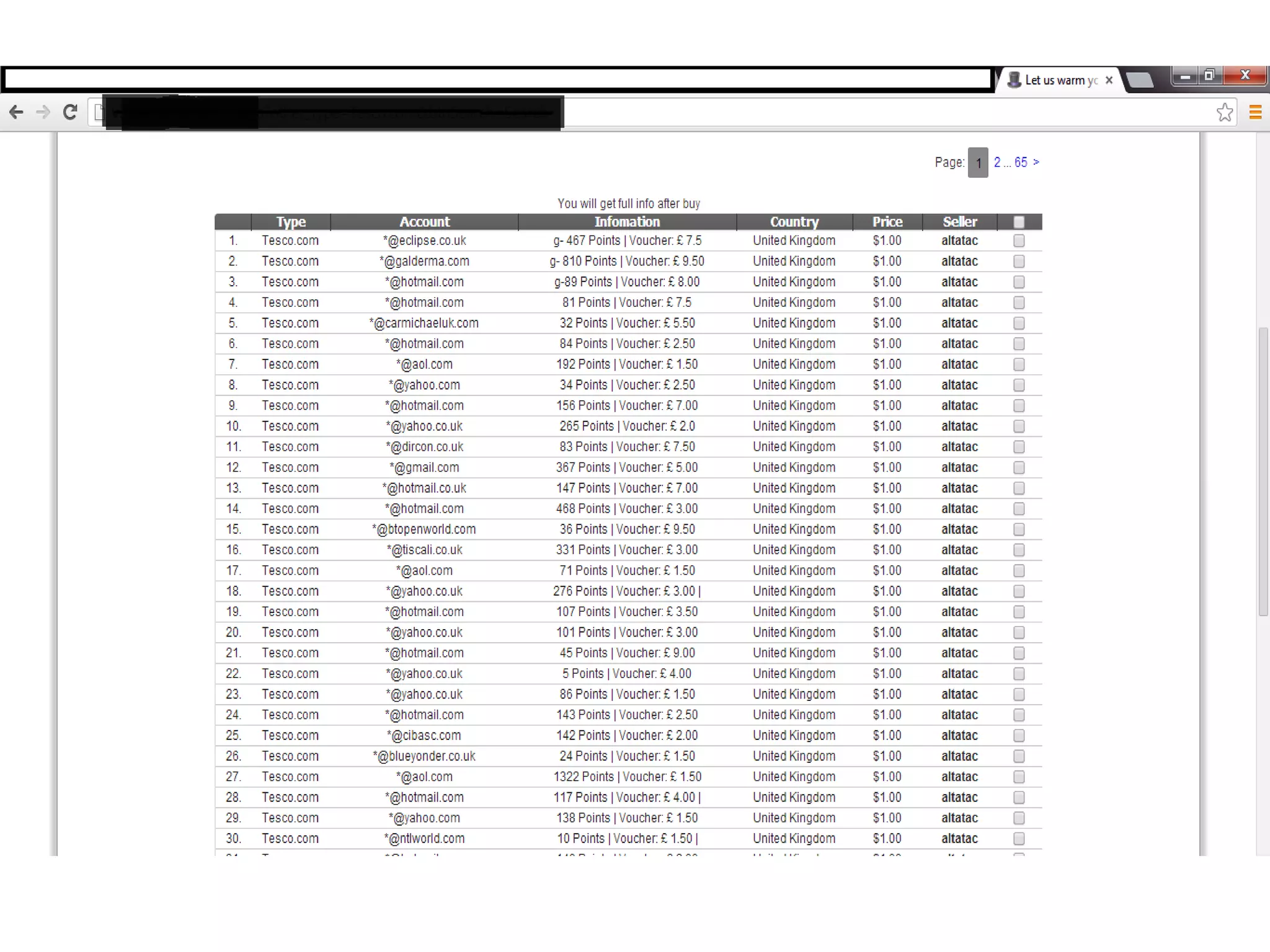
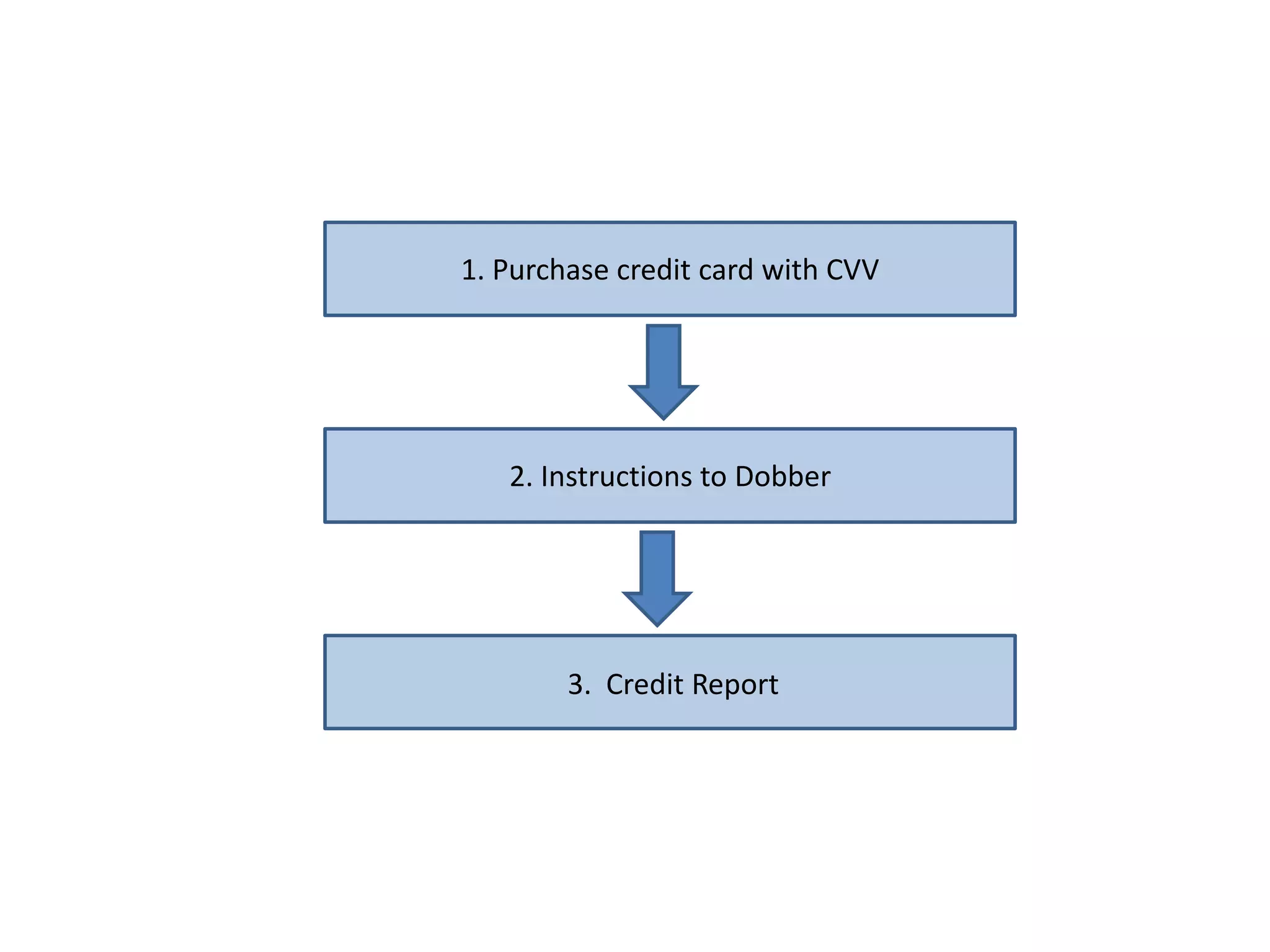
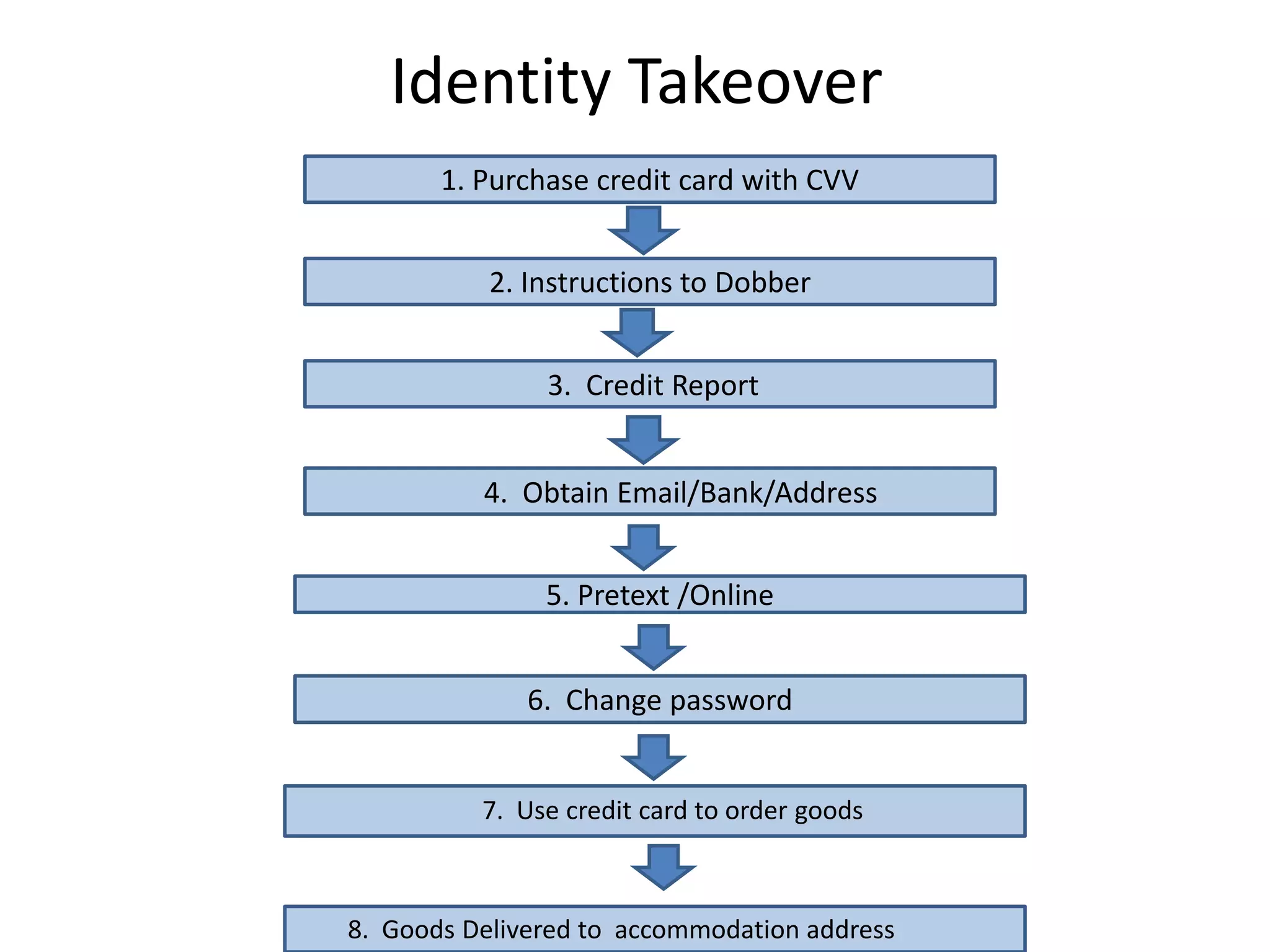
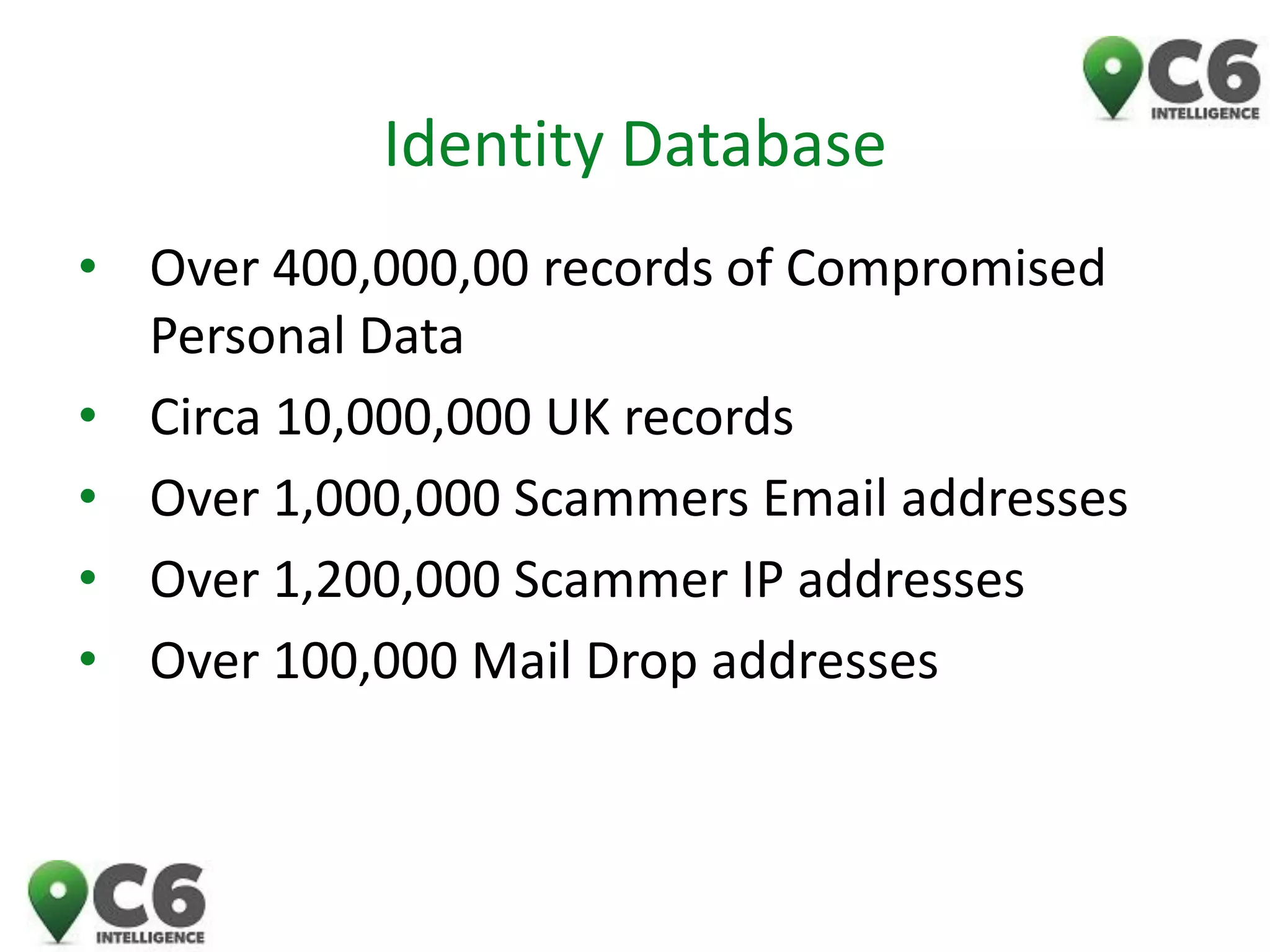
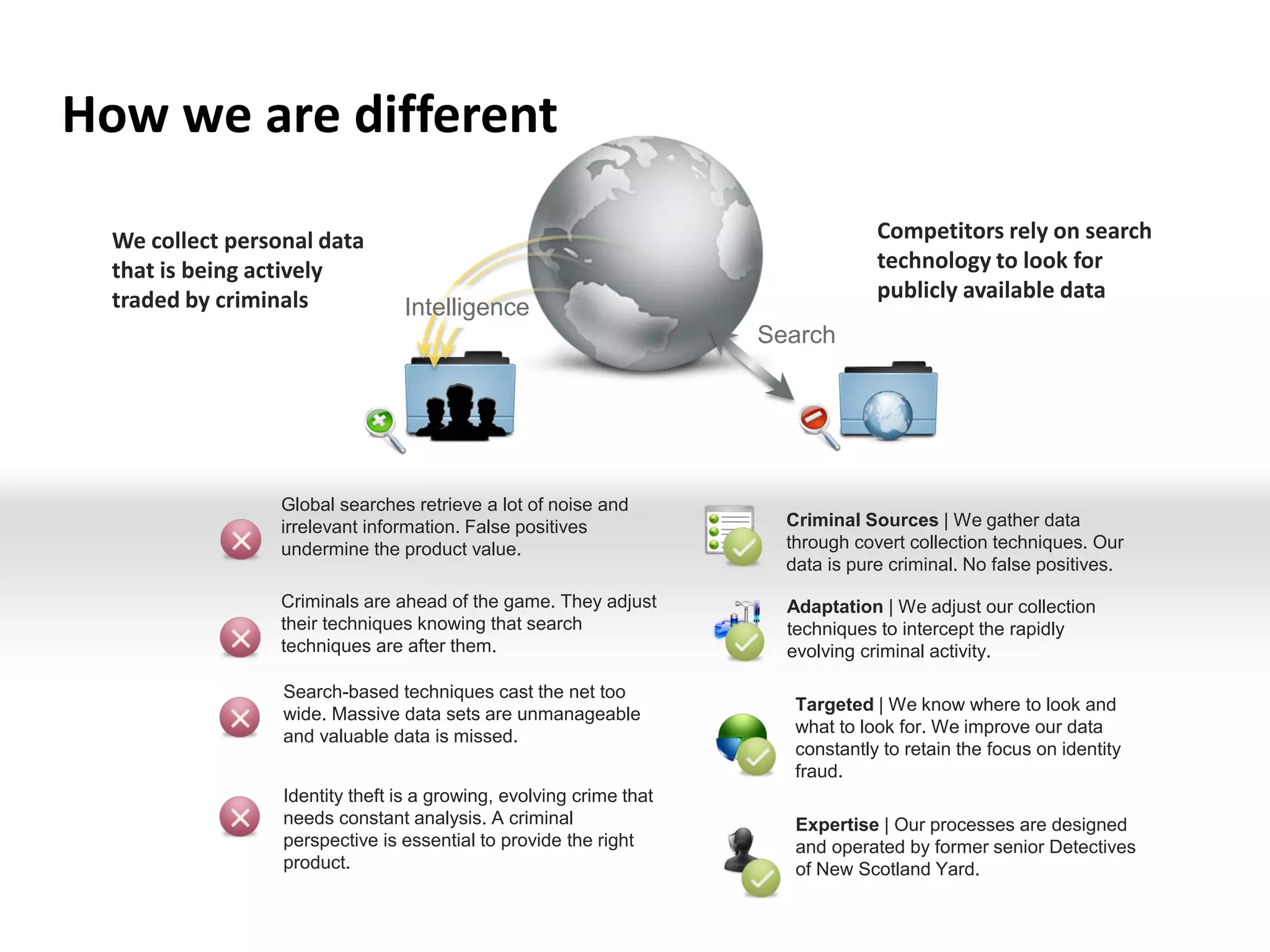
This document discusses identity theft and fraud. It provides information on the top banks affected by identity theft in the UK and lists many popular retailers and services that criminals use stolen credit cards and personal information to make fraudulent purchases from. It also outlines the types of private and government data that criminals can access to steal identities and describes the large identity theft database collected by the company C6 Intelligence, which gathers stolen identity records and scamming information to provide intelligence and risk assessment services to over 300 clients globally, including many banks and retailers.