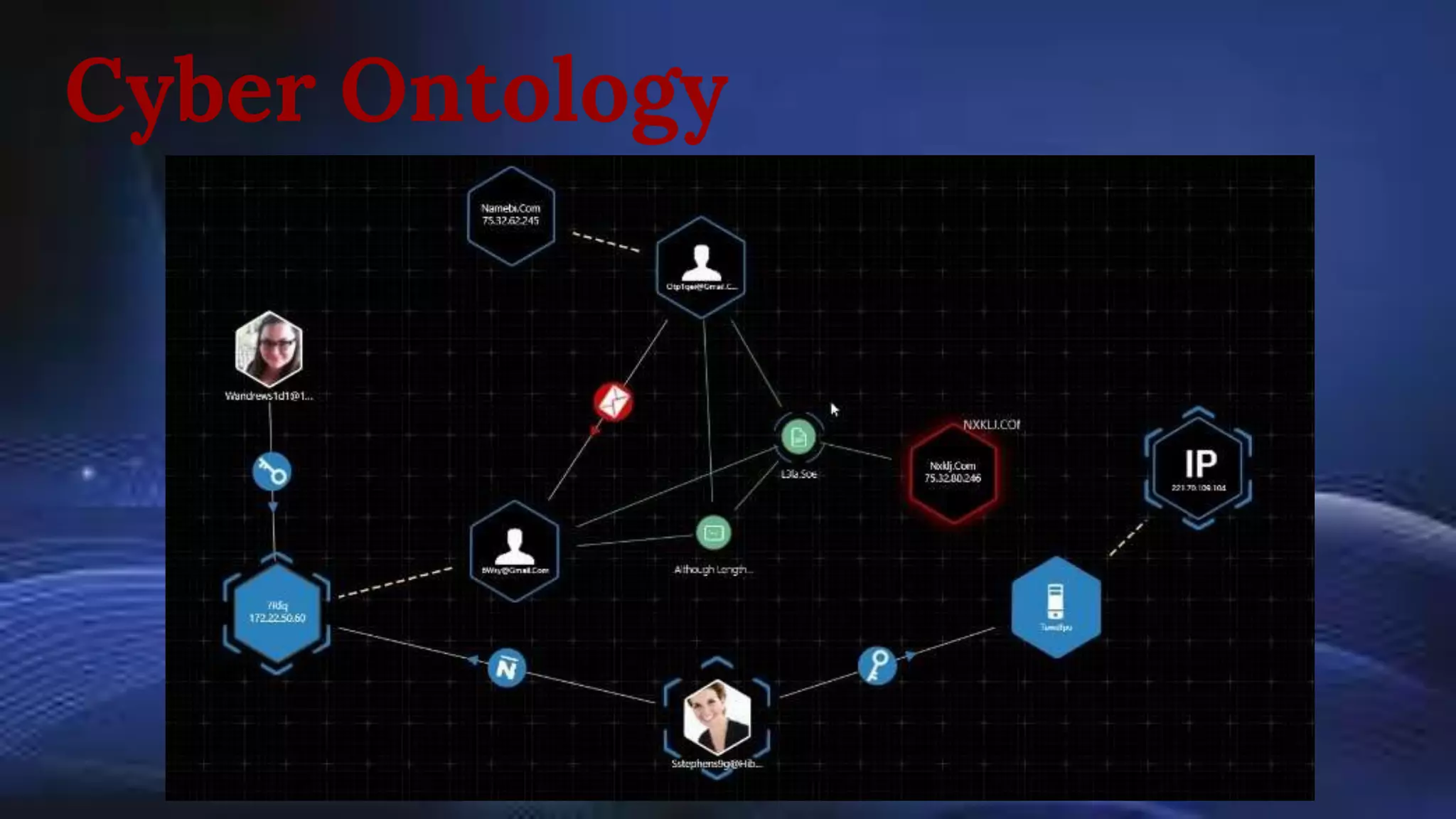
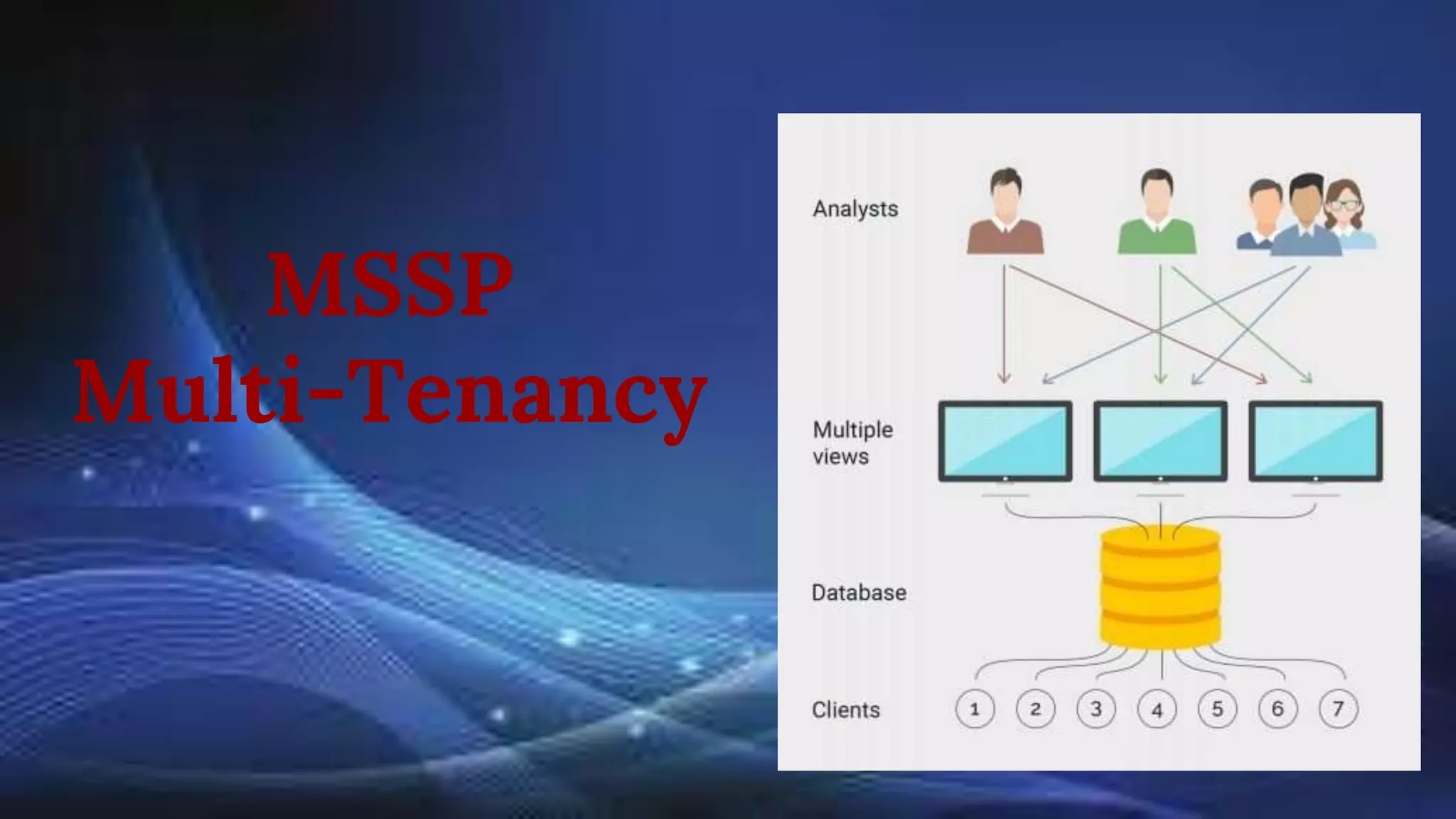
Managed Security Service Providers (MSSPs) face unique challenges in security orchestration due to their multi-tenant environments and the need to manage a wide array of security tools. Essential features for security orchestration solutions include centralized operations, triage and case management, automation capabilities, and multi-tenancy support. MSSPs should seek solutions that facilitate integration with various technologies and streamline reporting and collaboration with customers to enhance their security operations.