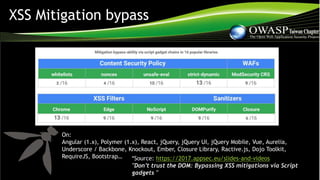
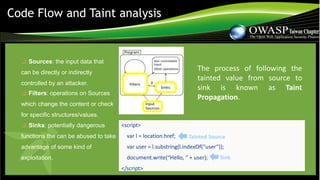
The document discusses the evolution of client-side security, specifically focusing on vulnerabilities such as XSS and the necessity for secure coding standards. It highlights challenges posed by modern JavaScript frameworks and the inadequacy of traditional security tools for analyzing complex JavaScript code. The document emphasizes the importance of implementing sophisticated coding techniques and dynamic analysis for effective security in a rapidly evolving landscape.



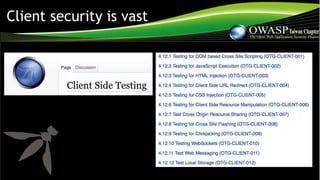




![So…Problem Solved?
Sources:
https://snyk.io/blog/xss-attacks-the-next-wave/
https://nvd.nist.gov/vuln/detail/CVE-2017-1160
“DOM-Based XSS is notoriously hard to
detect, as the server never gets a chance
to see the attack taking place.[…]”](https://image.slidesharecdn.com/2017owasptaiwanweekjssecurityautosavedautosaved-171127102627/85/JavaScript-security-and-tools-evolution-at-2017-OWASP-Taiwan-Week-9-320.jpg)