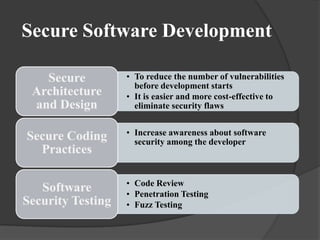
This document discusses secure programming practices, including incorporating security into the software development lifecycle, common vulnerabilities like buffer overflows and integer overflows, and secure coding guidelines for languages like Java and C++. It emphasizes practices like input validation, error handling, and using the latest compilers. It also covers the High Integrity C++ framework for developing safety-critical applications.










![References
[1]. Kevin Soo Hoo, Andrew W. Sudbury and Andrew R. Jaquith,
‘Tangible ROI through Secure Software Engineering’, 2006.
[2]. Michael Howard, David LeBlanc and John Viega, ‘19 Deadly Sins
of Software Security’, 2005.
[3]. Andrew van der Stock, Jeff Williams, Dave Wichers ‘OWASP top
10: The 10 most critical web application security vulnerabilities’,
2007.
[4]. Noopur Davis, ‘Secure Software Development Life Cycle
Processes: A technology Scouting Report’,2006.
[5]. Michael Howard, Steve Lipner , ‘The Security Development Life
Cycle’, 2006.](https://image.slidesharecdn.com/secureprogramminglanguagebasis-130208110229-phpapp02/85/Secure-programming-language-basis-12-320.jpg)
![References
[6]. Sun Microsystems, Inc., ‘Secure Coding Guidelines for the Java
Programming Language, version 2.0’, 2007
[7]. Mark G. Graff, Kenneth R. van Wyk, ‘Secure Coding Principles,
and Practices’, 2003.
[8]. Dave Dyer, ‘Can Assure save Java from the perils of
multithreading’, 1998
[9]. Flight Lieutenant Derek W. Reinhardt, ‘Use of the C++
Programming Language in Safety Critical Systems’, 2004
[10]. Trupti Shiralkar and Brenda Grove,’ Guidelines for Secure
Coding’, 2009](https://image.slidesharecdn.com/secureprogramminglanguagebasis-130208110229-phpapp02/85/Secure-programming-language-basis-13-320.jpg)
