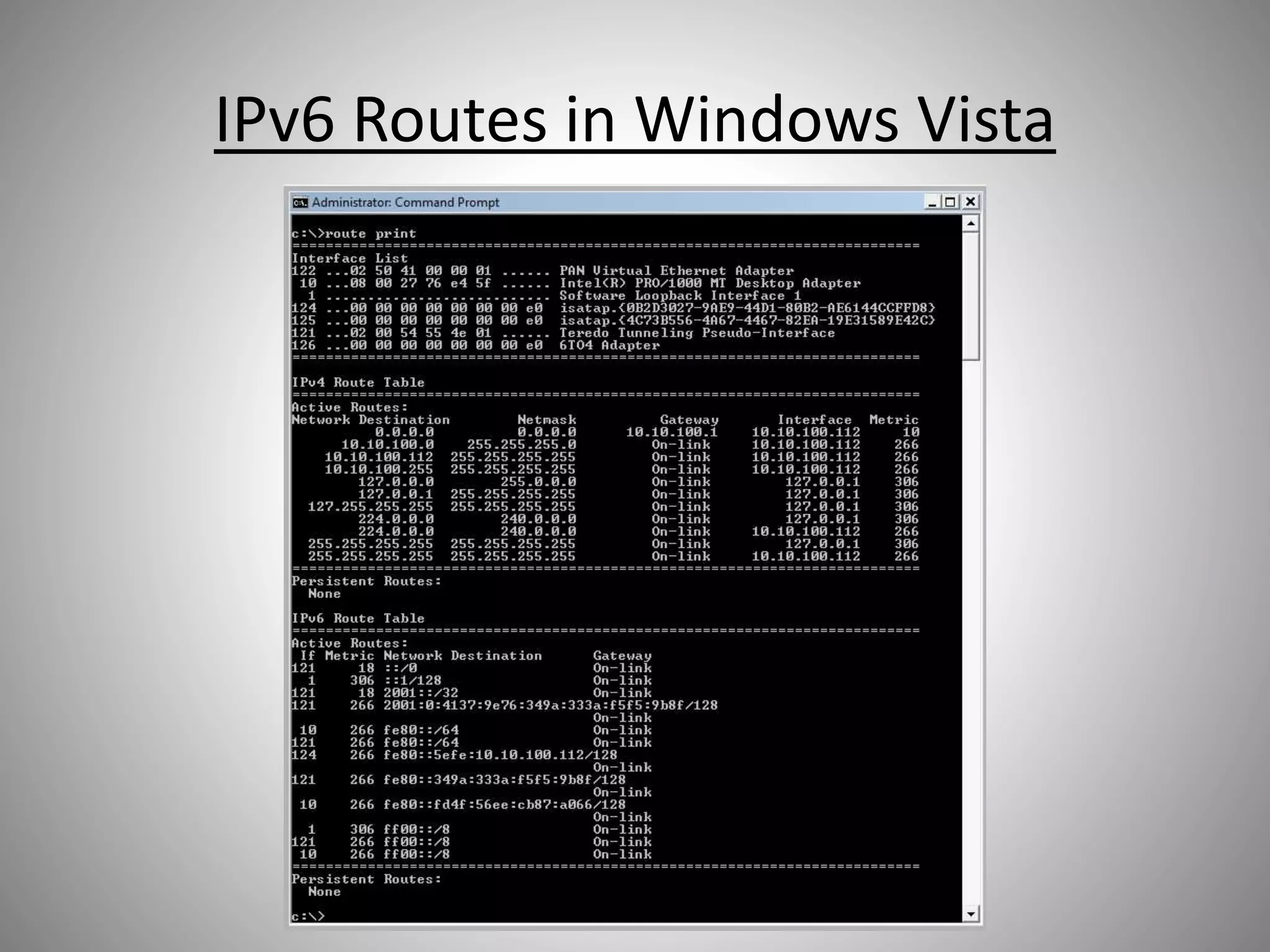
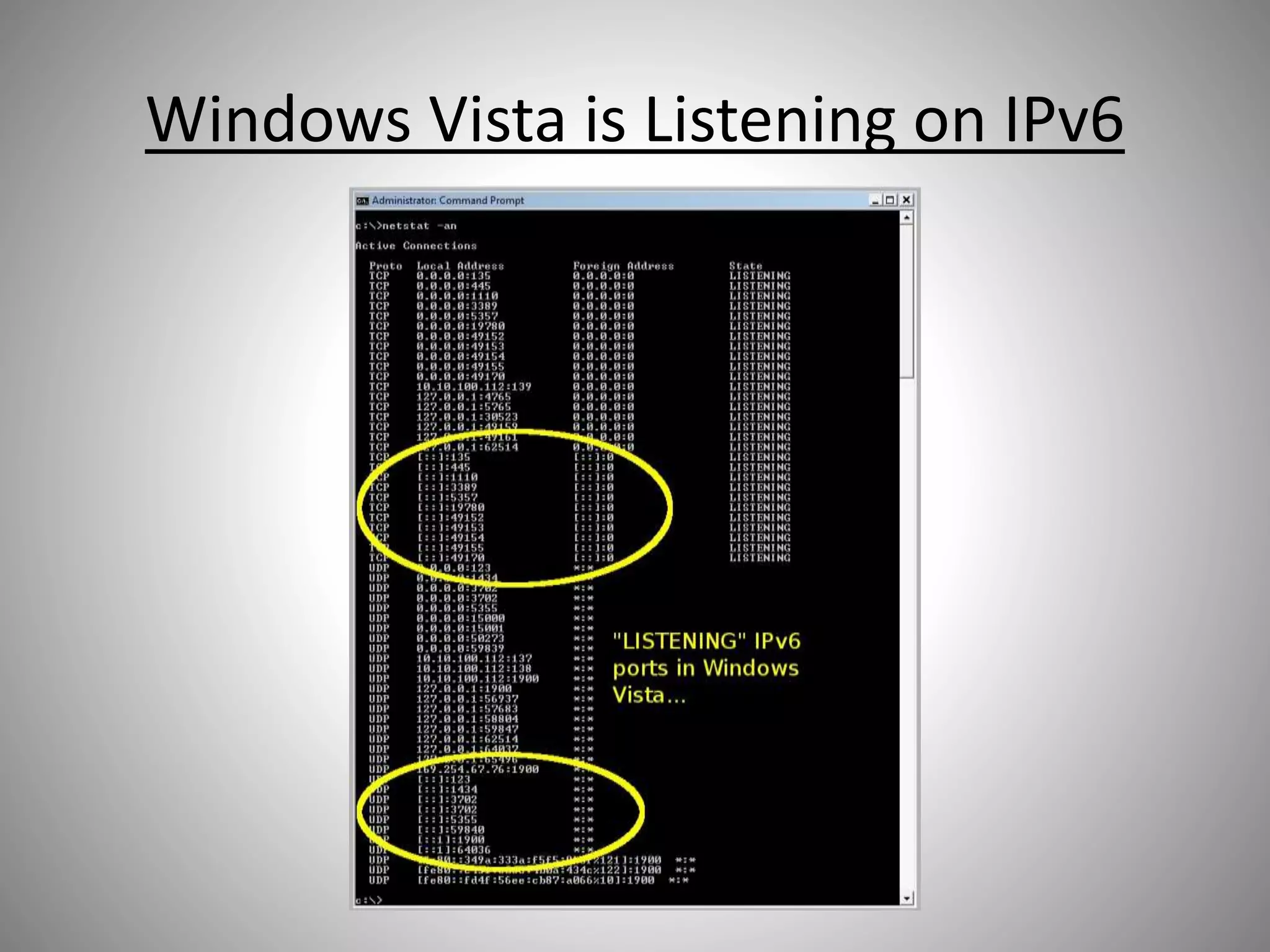
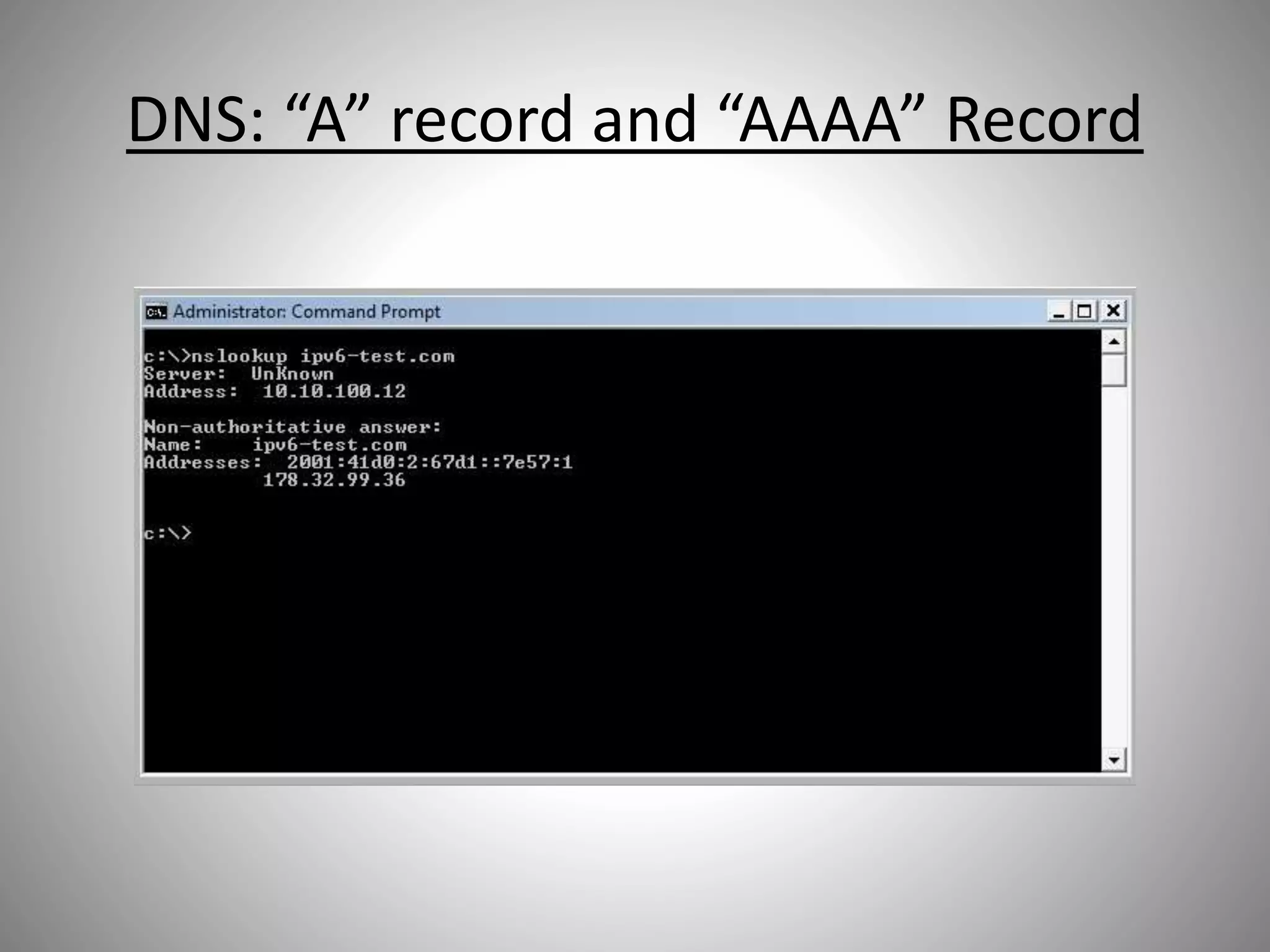
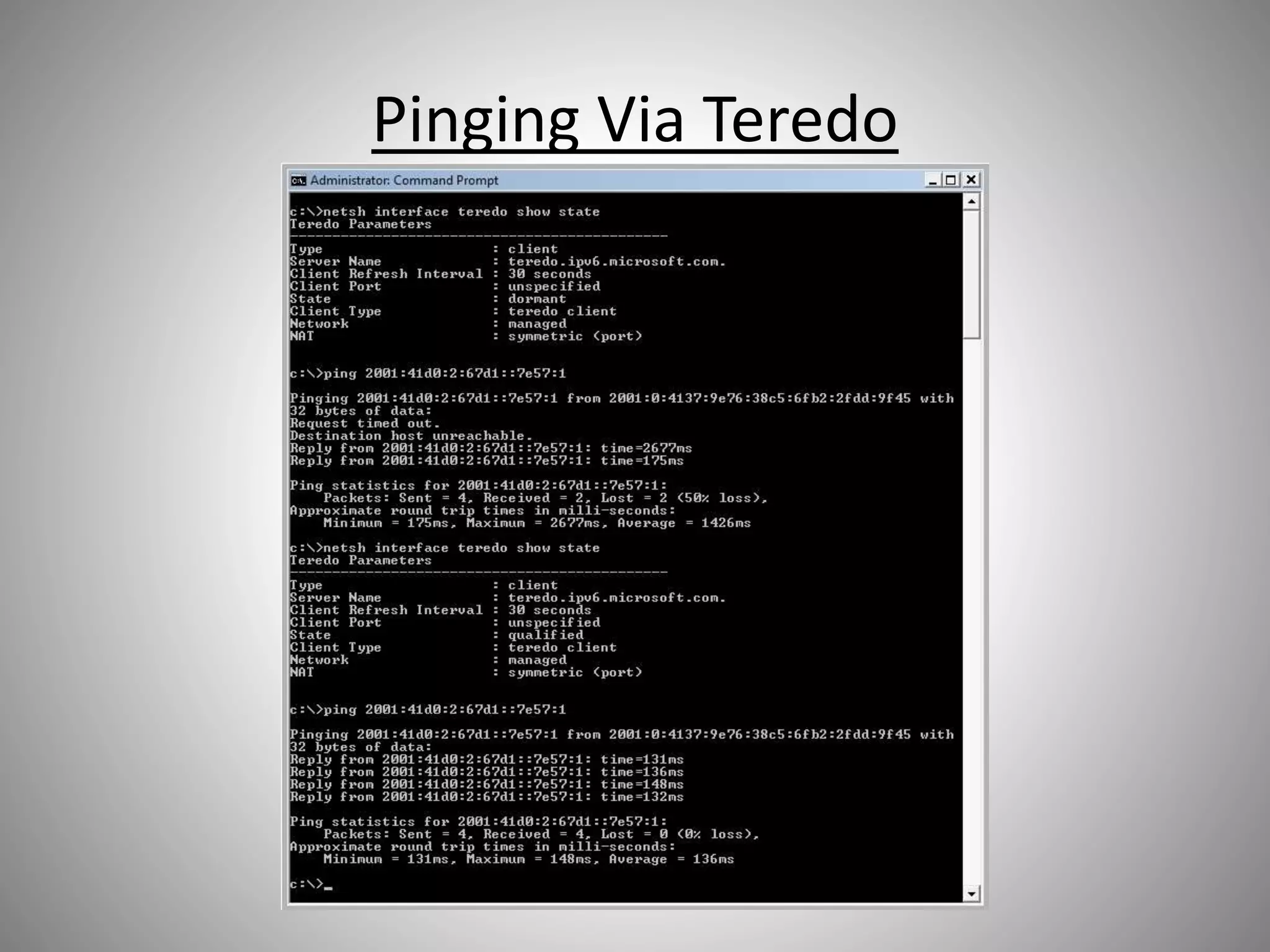
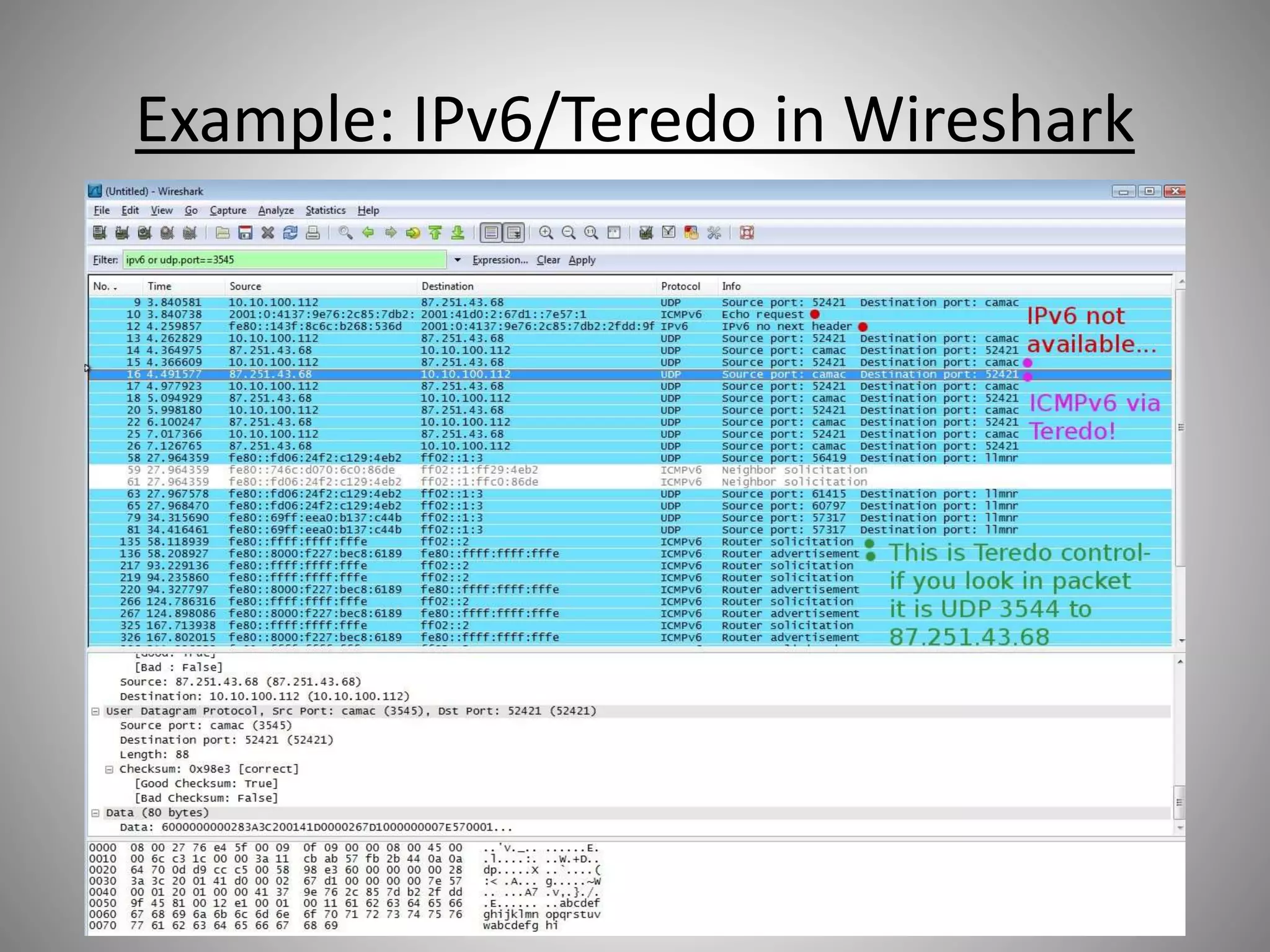
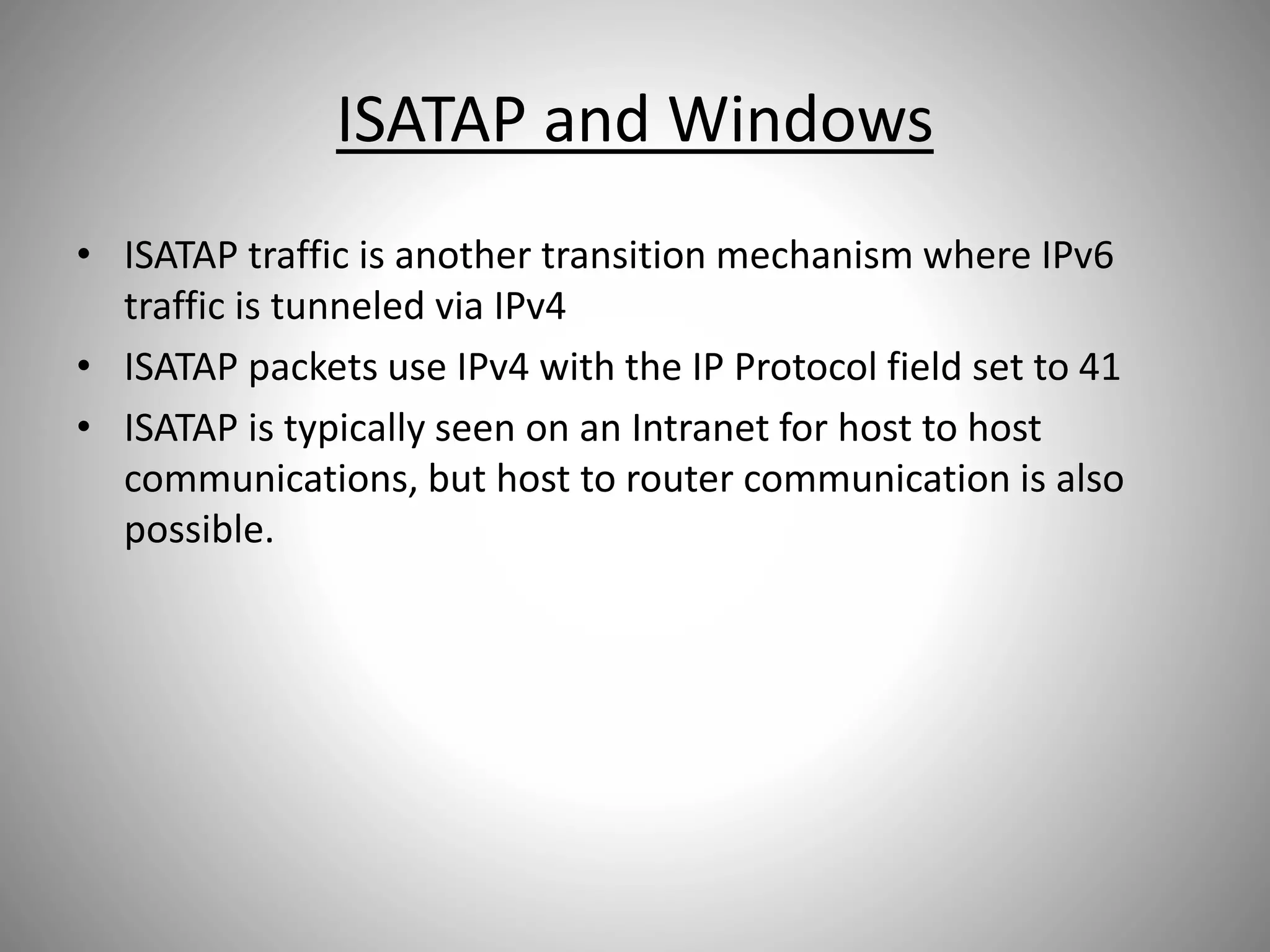
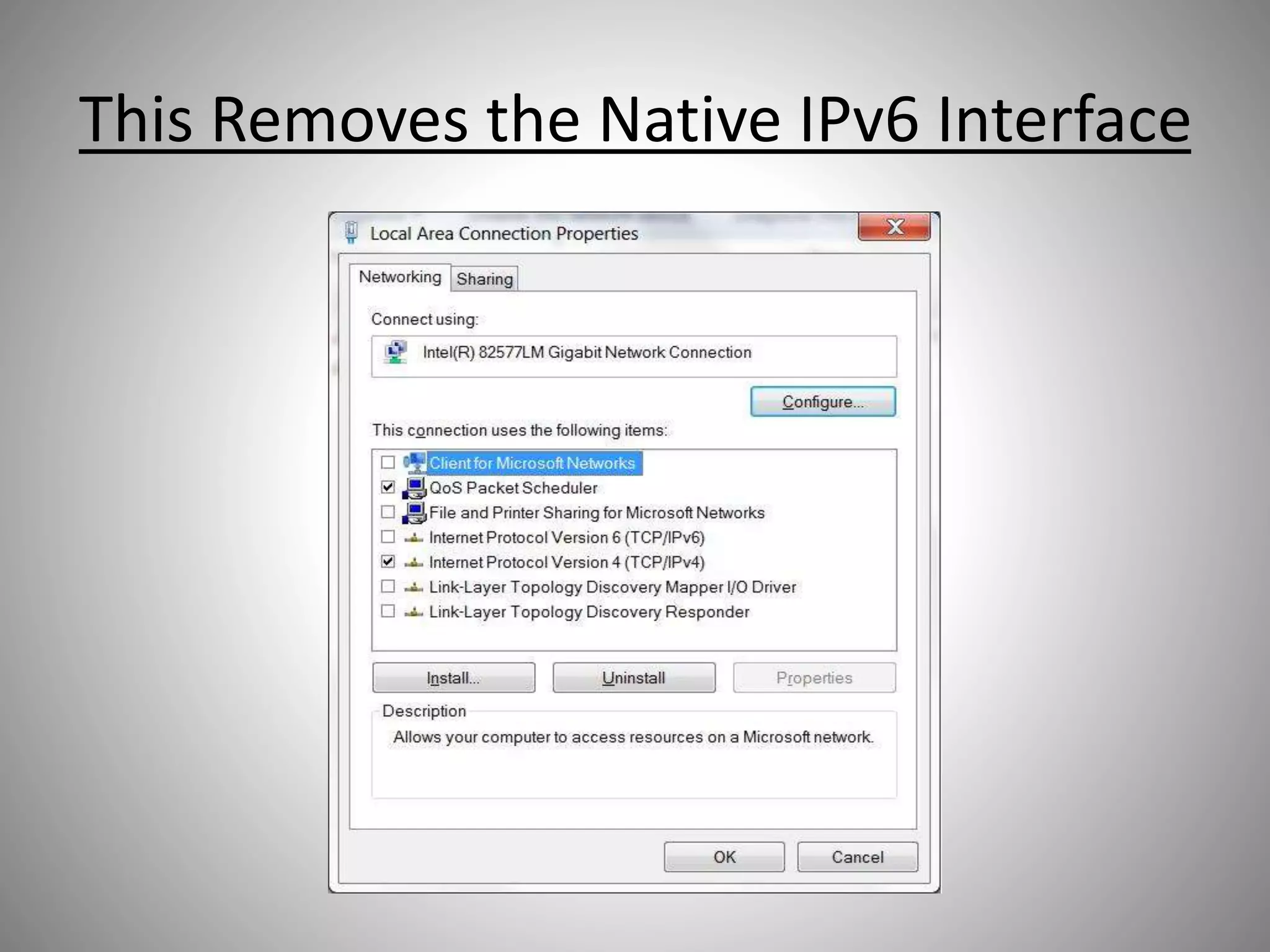
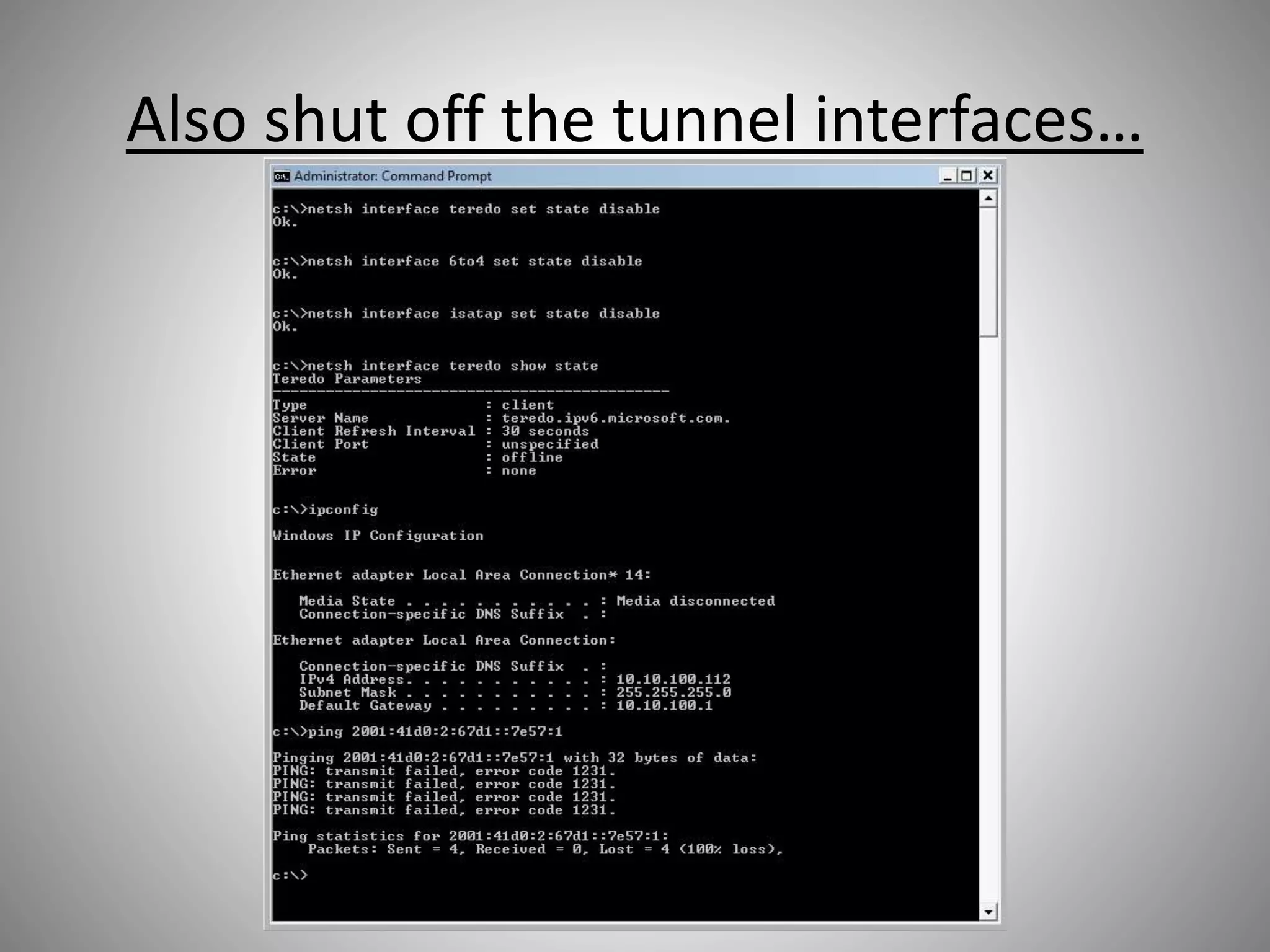
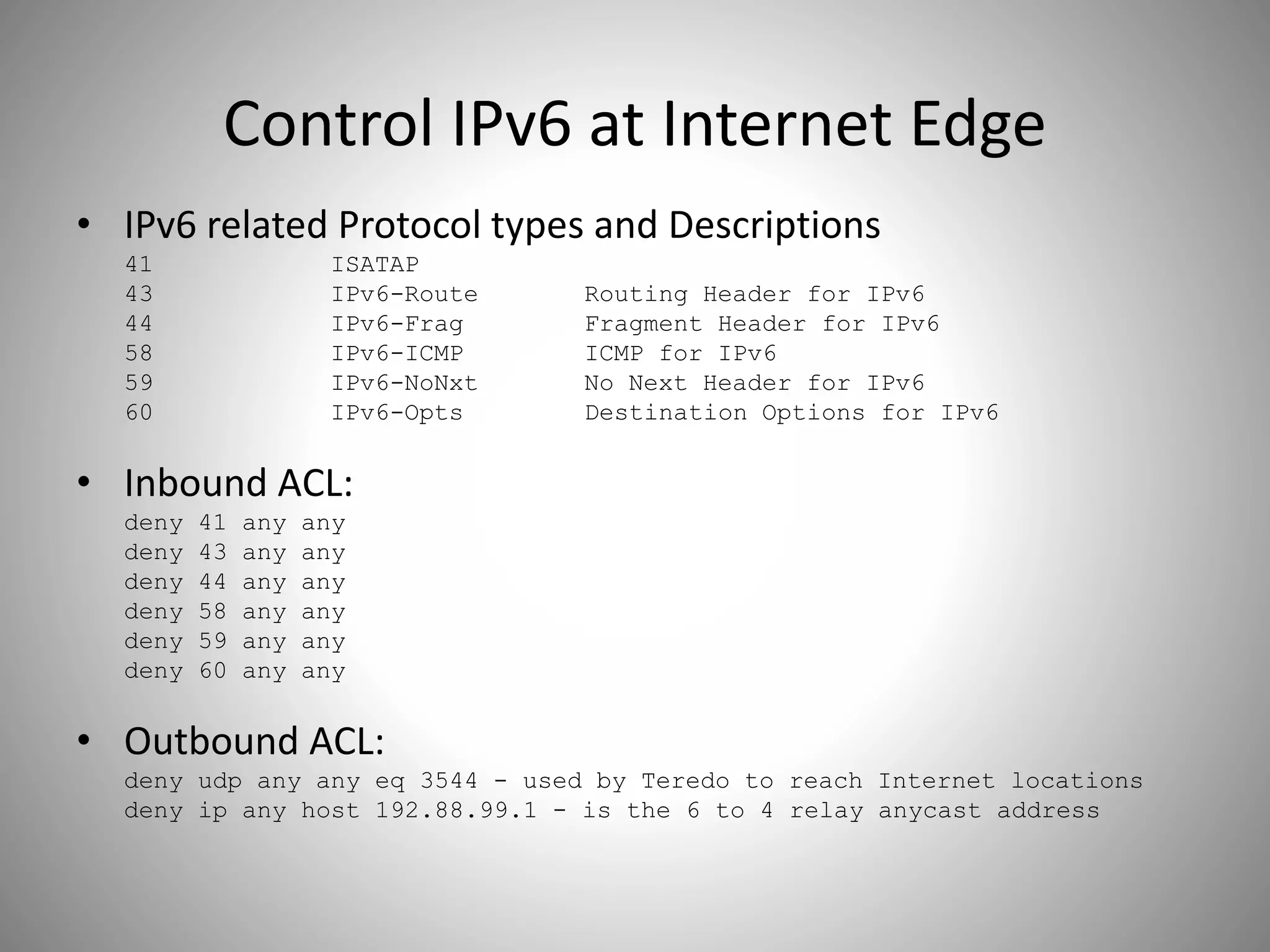
The document discusses the transition from IPv4 to IPv6, highlighting potential security risks associated with unmonitored IPv6 traffic and encapsulation mechanisms that aid this transition. It emphasizes the importance for IT administrators to recognize and control IPv6 usage within their networks, especially as IPv4 addresses become depleted. Recommendations include implementing policies to disable unnecessary IPv6 support and enhancing monitoring capabilities to mitigate associated threats.