Recommended
Recommended
More Related Content
What's hot
What's hot (20)
CCTV System - Close circuit television System - UCJ

CCTV System - Close circuit television System - UCJ
CCTV System - Close circuit television System - UCJ

CCTV System - Close circuit television System - UCJ
Types of CCTV Cameras & Uses - Techno Edge Systems

Types of CCTV Cameras & Uses - Techno Edge Systems
Close Circuit Television (CCTV SURVEILLANCE SYSTEMS)

Close Circuit Television (CCTV SURVEILLANCE SYSTEMS)
Viewers also liked
Viewers also liked (20)
Nācija un nacionālās identitātes diskurss: politiskās elites vēstījumu analīze

Nācija un nacionālās identitātes diskurss: politiskās elites vēstījumu analīze
A peek into the world of WordPress plugin development

A peek into the world of WordPress plugin development
Curriculumvitaeworkshopfall2014 141210221540-conversion-gate02

Curriculumvitaeworkshopfall2014 141210221540-conversion-gate02
Switching On the Growth Engine in Your Small Consulting Practice

Switching On the Growth Engine in Your Small Consulting Practice
Similar to Presant
CCTV Surveillance System Including Sensor For Infrastructure Protection

CCTV Surveillance System Including Sensor For Infrastructure ProtectionNeometrix_Engineering_Pvt_Ltd
Similar to Presant (20)
DSS ITSEC CONFERENCE - Q1 Labs - Intelligent network security - next genera...

DSS ITSEC CONFERENCE - Q1 Labs - Intelligent network security - next genera...
8 WAYS TO PROTECT THE DATA IN YOUR OFFICE: #3 Trust in your office solutions

8 WAYS TO PROTECT THE DATA IN YOUR OFFICE: #3 Trust in your office solutions
CCTV Surveillance System Including Sensor For Infrastructure Protection

CCTV Surveillance System Including Sensor For Infrastructure Protection
Defending our datacenters (BICSI 2016 ASEAN conference)

Defending our datacenters (BICSI 2016 ASEAN conference)
More from riskis
More from riskis (20)
Recently uploaded
Recently uploaded (20)
Snow Chain-Integrated Tire for a Safe Drive on Winter Roads

Snow Chain-Integrated Tire for a Safe Drive on Winter Roads
Unlocking the Potential of the Cloud for IBM Power Systems

Unlocking the Potential of the Cloud for IBM Power Systems
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
"Federated learning: out of reach no matter how close",Oleksandr Lapshyn

"Federated learning: out of reach no matter how close",Oleksandr Lapshyn
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
Designing IA for AI - Information Architecture Conference 2024

Designing IA for AI - Information Architecture Conference 2024
Artificial intelligence in the post-deep learning era

Artificial intelligence in the post-deep learning era
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Presant
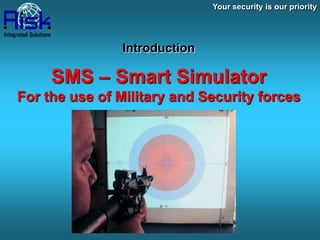
- 1. Your security is our priority Introduction SMS – Smart Simulator For the use of Military and Security forces
- 2. Your security is our priority System Parts Camera + basis Laser + batteries Barrel connector Trigger micro switch Computer software and speakers Projector with camera
- 3. Your security is our priority System Configuration Projector screen / wall Training range 1-20 m. Cables Projector + IR camera Speakers Laptop
- 4. Your security is our priority System calibration and weapon zeroing System calculate average hit point and software process the calibration
- 5. Your security is our priority Friendly control on operation and data
- 6. Your security is our priority 1-4 trainees
- 7. Your security is our priority On motion drills
- 8. Your security is our priority Technical drills
- 9. Your security is our priority Tactical drills
- 10. Your security is our priority Graphic firing range drills
- 11. Your security is our priority Video realistic drills
- 12. Your security is our priority SMS – allow firing training to every end user