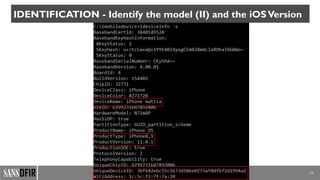
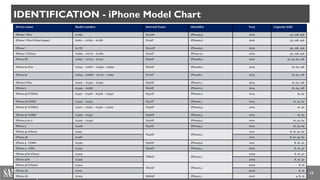
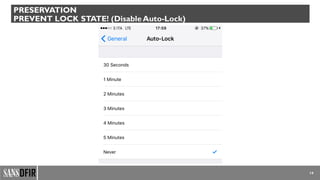
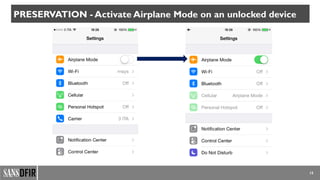
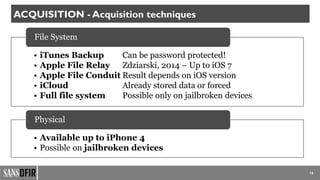
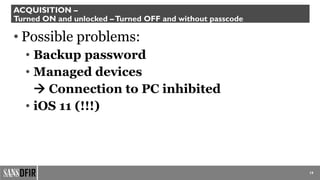
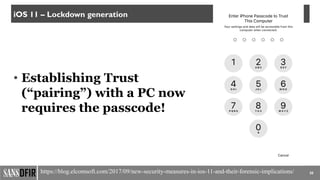
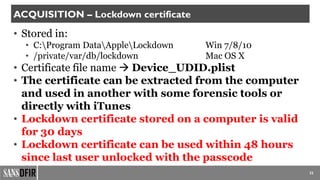
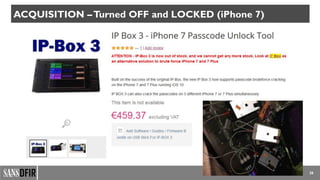
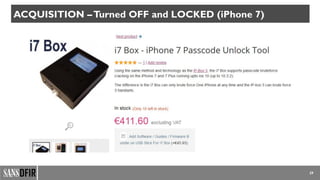
The document discusses iOS forensics, detailing acquisition challenges, techniques for data retrieval from iOS devices, and the importance of device model and iOS version identification. It outlines specific rules and preservation methods for forensic analysis, including the prevention of device locking and techniques for data extraction. Additionally, it highlights experimental techniques and tools that can be used for effective iOS forensic investigations.
















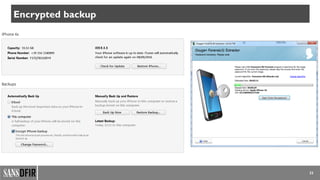
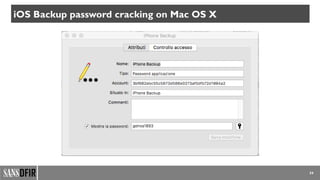
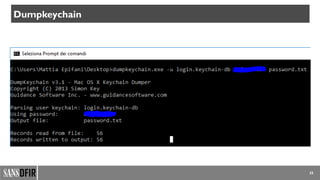
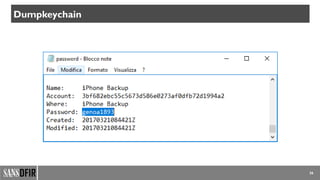
![37
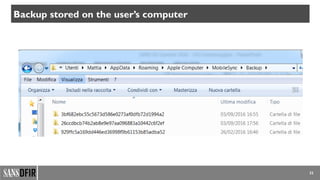
Other data stored on the user’s computer
• Windows
• C:ProgramDataAppleComputer
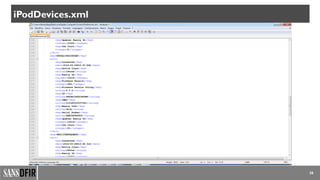
• iTunesiPodDevices.xml Connected iOS devices
• C:Users[username]AppDataRoamingApple Computer
• MobileSyncBackup Device Backup
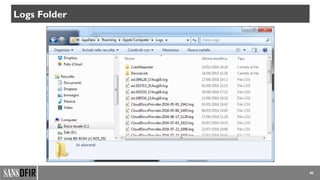
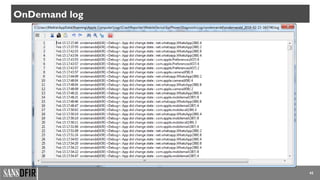
• Logs Various device logs
• MediaStream PhotoStream information
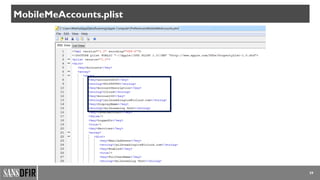
• iTunes iTunes Preferences and Apple
account information
• Mac OS X
• https://www.mac4n6.com/resources/
• Sarah Edwards
• Ubiquity Forensics - Your iCloud and You](https://image.slidesharecdn.com/iosforensicspraguedfir2017-180111173313/85/iOS-Forensics-where-are-we-now-and-what-are-we-missing-37-320.jpg)