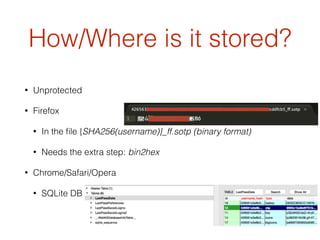
The document discusses the vulnerabilities associated with LastPass, a widely used password management service. It details various attacks like bypassing two-factor authentication and account recovery vulnerabilities, exposing how attackers can gain access to user vaults by exploiting weaknesses in the browser extensions and the storage methods of sensitive data. The document concludes by suggesting measures to harden LastPass security against potential threats.














![siesta.py
• Beautifies every JS file
• Injects a payload to every function
• console.log([file] [function] [params])
• Credits to Alberto Garcia (@algillera)](https://image.slidesharecdn.com/shakaconpreso-171203091107/85/Breaking-vaults-Stealing-Lastpass-protected-secrets-15-320.jpg)







![Storage
Chrome Firefox Safari Opera
Windows
#{user_profile['LocalApp
Data']}/Google/Chrome/
User Data/Default/
databases/chrome-
extension_hdokiejnpimak
edhajhdlcegeplioahd_0
#{user_profile[
'AppData']}/
Mozilla/
Firefox/Profiles
#{user_profile['LocalAppData
']}/Apple Computer/Safari/
Databases/safari-
extension_com.lastpass.lpsaf
ariextension-n24rep3bmn_0
#{user_profile['AppData']}/
Opera Software/Opera
Stable/databases/chrome-
extension_hnjalnkldgigidg
gphhmacmimbdlafdo_0
Mac
#{user_profile['LocalApp
Data']}/Google/Chrome/
Default/databases/
chrome-
extension_hdokiejnpimak
edhajhdlcegeplioahd_0
#{user_profile['
LocalAppData']
}/Firefox/
Profiles
#{user_profile['AppData']}/
Safari/Databases/safari-
extension_com.lastpass.lpsaf
ariextension-n24rep3bmn_0
#{user_profile['LocalAppData']
}/com.operasoftware.Opera/
databases/chrome-
extension_hnjalnkldgigidggph
hmacmimbdlafdo_0
Unix
#{user_profile['LocalApp
Data']}/.config/google-
chrome/Default/
databases/chrome-
extension_hdokiejnpimak
edhajhdlcegeplioahd_0
#{user_profile['
LocalAppData']
}/.mozilla/firefox
#{user_profile[‘LocalApp
Data’]}/.opera/widgets/
wuid-*/pstorage
Internet Explorer uses Protected Storage](https://image.slidesharecdn.com/shakaconpreso-171203091107/85/Breaking-vaults-Stealing-Lastpass-protected-secrets-23-320.jpg)