Recommended
More Related Content
What's hot
What's hot (20)
Wireshark course, Ch 02: Introduction to wireshark

Wireshark course, Ch 02: Introduction to wireshark
SSL basics and SSL packet analysis using wireshark

SSL basics and SSL packet analysis using wireshark
Viewers also liked
Viewers also liked (12)
Similar to Basic config
Similar to Basic config (20)
Ch11 Hacking Wireless Networks it-slideshares.blogspot.com

Ch11 Hacking Wireless Networks it-slideshares.blogspot.com
MikroTik Basic Training Class - Online Moduls - English

MikroTik Basic Training Class - Online Moduls - English
Zdalna komunikacja sieciowa - zagadnienia sieciowe 

Zdalna komunikacja sieciowa - zagadnienia sieciowe
[Advantech] ADAM-3600 open vpn setting Tutorial step by step ![[Advantech] ADAM-3600 open vpn setting Tutorial step by step](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Advantech] ADAM-3600 open vpn setting Tutorial step by step](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Advantech] ADAM-3600 open vpn setting Tutorial step by step
More from lyndyv
More from lyndyv (17)
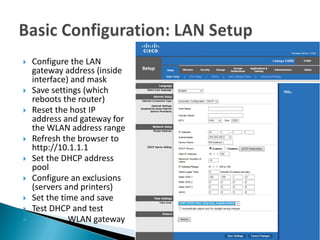
Basic config
- 1. Configure the LAN gateway address (inside interface) and mask Save settings (which reboots the router) Reset the host IP address and gateway for the WLAN address range Refresh the browser to http://10.1.1.1 Set the DHCP address pool Configure an exclusions (servers and printers) Set the time and save Test DHCP and test WLAN gateway
- 2. Select manual For 5GHz and 2.4 GHZ ◦ Select the Network Mode ◦ Enter the SSID ◦ Leave Channel width and Channel to auto ◦ Set SSID broadcast Save Test by connecting wireless host
- 3. For Windows 7: Network and Sharing Centre Setup a new connection or network Manually connect to a wireless network Enter information for the wireless network Select the network from the Wireless network connection list Connect to the network Test the connection by pinging the LAN interface (LAN gateway) from a wireless host
- 4. Select the best security mode supported by your wireless hosts for both bands Set up a strong secure password Save and test and document
- 5. Select enabled Select Permit PCs or Prevent PCs Add the Mac address of host to either permit or prevent to the Wireless Client List Save and Test Document