IoT vendor questions
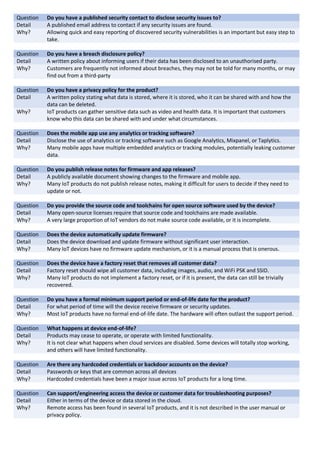
- 1. Question Do you have a published security contact to disclose security issues to? Detail A published email address to contact if any security issues are found. Why? Allowing quick and easy reporting of discovered security vulnerabilities is an important but easy step to take. Question Do you have a breach disclosure policy? Detail A written policy about informing users if their data has been disclosed to an unauthorised party. Why? Customers are frequently not informed about breaches, they may not be told for many months, or may find out from a third-party Question Do you have a privacy policy for the product? Detail A written policy stating what data is stored, where it is stored, who it can be shared with and how the data can be deleted. Why? IoT products can gather sensitive data such as video and health data. It is important that customers know who this data can be shared with and under what circumstances. Question Does the mobile app use any analytics or tracking software? Detail Disclose the use of analytics or tracking software such as Google Analytics, Mixpanel, or Taplytics. Why? Many mobile apps have multiple embedded analytics or tracking modules, potentially leaking customer data. Question Do you publish release notes for firmware and app releases? Detail A publicly available document showing changes to the firmware and mobile app. Why? Many IoT products do not publish release notes, making it difficult for users to decide if they need to update or not. Question Do you provide the source code and toolchains for open source software used by the device? Detail Many open-source licenses require that source code and toolchains are made available. Why? A very large proportion of IoT vendors do not make source code available, or it is incomplete. Question Does the device automatically update firmware? Detail Does the device download and update firmware without significant user interaction. Why? Many IoT devices have no firmware update mechanism, or it is a manual process that is onerous. Question Does the device have a factory reset that removes all customer data? Detail Factory reset should wipe all customer data, including images, audio, and WiFi PSK and SSID. Why? Many IoT products do not implement a factory reset, or if it is present, the data can still be trivially recovered. Question Do you have a formal minimum support period or end-of-life date for the product? Detail For what period of time will the device receive firmware or security updates. Why? Most IoT products have no formal end-of-life date. The hardware will often outlast the support period. Question What happens at device end-of-life? Detail Products may cease to operate, or operate with limited functionality. Why? It is not clear what happens when cloud services are disabled. Some devices will totally stop working, and others will have limited functionality. Question Are there any hardcoded credentials or backdoor accounts on the device? Detail Passwords or keys that are common across all devices Why? Hardcoded credentials have been a major issue across IoT products for a long time. Question Can support/engineering access the device or customer data for troubleshooting purposes? Detail Either in terms of the device or data stored in the cloud. Why? Remote access has been found in several IoT products, and it is not described in the user manual or privacy policy.
