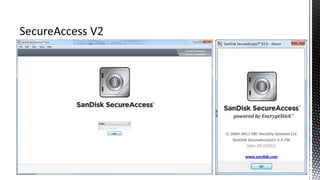
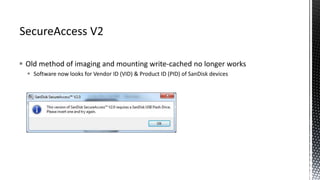
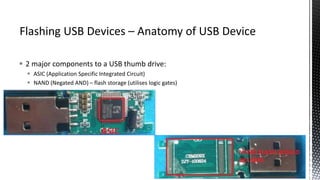
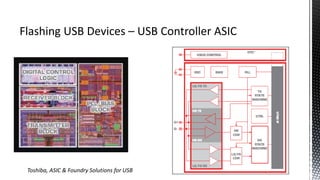
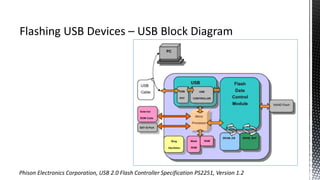
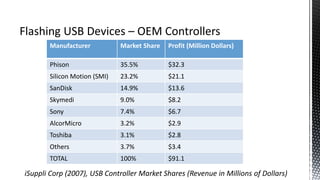
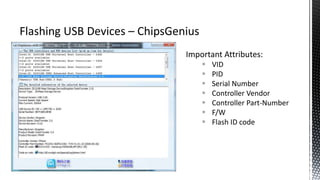
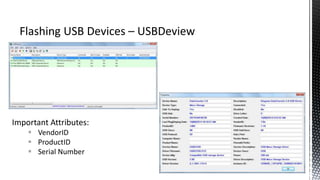
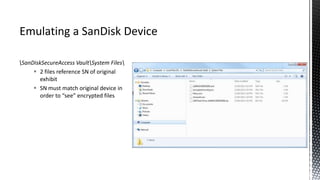
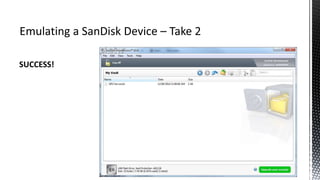
The document outlines forensic methods for accessing encrypted data on USB devices, particularly focusing on the SecureAccess software and its vulnerabilities. It discusses bypass techniques, hardware components involved in USB drives, and the importance of various identifiers such as VID, PID, and serial numbers for successful data recovery. Additionally, it provides insights into the flashing process and tools required to recreate compatible USB devices for forensic examination.