Report
Share
Download to read offline
Recommended
What if my Software is a Medical Device?
Impacts Design/Development
Impacts Maintenance
PMA or 510K?
If PMA, Clinical Data is NeededCritical Steps in Software Development: Enhance Your Chances for a Successful...

Critical Steps in Software Development: Enhance Your Chances for a Successful...Sterling Medical Devices
Recommended
What if my Software is a Medical Device?
Impacts Design/Development
Impacts Maintenance
PMA or 510K?
If PMA, Clinical Data is NeededCritical Steps in Software Development: Enhance Your Chances for a Successful...

Critical Steps in Software Development: Enhance Your Chances for a Successful...Sterling Medical Devices
More Related Content
What's hot
What's hot (8)
QAdvis - software risk management based on IEC/ISO 62304

QAdvis - software risk management based on IEC/ISO 62304
Reliability Instrumented System | Arrelic Insights 

Reliability Instrumented System | Arrelic Insights
Similar to Common Areas of Data Breach
Similar to Common Areas of Data Breach (20)
511718784-maintain-inventory-of-equipment-software-and-documentation.pptx

511718784-maintain-inventory-of-equipment-software-and-documentation.pptx
BRKDCT-3144 - Advanced - Troubleshooting Cisco Nexus 7000 Series Switches (20...

BRKDCT-3144 - Advanced - Troubleshooting Cisco Nexus 7000 Series Switches (20...
V center operations enterprise standalone technical presentation

V center operations enterprise standalone technical presentation
.conf2011: Web Analytics Throwdown: with NPR and Intuit

.conf2011: Web Analytics Throwdown: with NPR and Intuit
Permission Driven Malware Detection using Machine Learning

Permission Driven Malware Detection using Machine Learning
More from William Kiss
More from William Kiss (8)
Common Areas of Data Breach
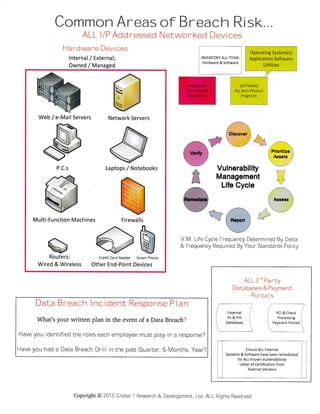
- 1. Common Areas ALL l/P Add ressed Hardware Devices lnternal / External; Owned / Managed of Breach Risk,,, Networked Devices a.' Dimver --8 . t l @ , J ,.!::&!-;€g;&. t*;-;.t 1:j -11:: e*:% F' €=*re Prioritize 81re Aasets q:=====7 r€======7 T Vulnerability ,r:: F=q Management *=:g ...: , '-' INVENTORY ALL ITEMS: Hardware & Software Operating System(s) Application Software Utilities Life Cycle -*;., t' I Ate*e l 1i1' I 1.. l---f3h f-::.V i.alw,t,..i llt,.l.. ' ..: .1,, 1 1':r' ::-;i V M. Life Cycle Frequency Determined By Delta & Frequency Required By Your Standards Policy Data Breach I ncident Response P I an What's your written plan in the event of a Data Breach? Have you identified the roles each employee must play in a response? Have you had a Data Breach Drill in the past Quarter, 6-Months, Year? ALL 3'o Pa rty Databases & Payment Porta I s Ensure ALL External Systems & Software have been remediated for ALL Known Vulnerabilities Letter of Certification from External Vendors Web / e-Mail Servers Network Servers Laptops / Notebooks Multi-Function Machines &Routers: Wired & Wireless Credit Card Reader Smart Phone Other End-Point Devices Firewalls Copyright@ 2015 Global 1 Research & Deveiopment, Ltd, ALL Rights Reserved
