Lecture34_RoutingAlgorithmsLSR.pdf
•
0 likes•4 views
1. Link state routing involves each router discovering its neighbors, measuring link costs, constructing link state packets with this information, flooding these packets to all other routers, and using the packets to construct shortest paths to every other router. 2. Link state packets contain fields for sequence number, age, flags, and neighbor information to prevent old packets from being used and ensure consistent routing tables across routers. 3. Hierarchical routing is used to scale routing in large networks, using backbone routers to route between regions and regional routers to route within regions.
Report
Share
Report
Share
Download to read offline
Recommended
Lecture32_RoutingAlgorithmsDV.pdf

The document discusses routing algorithms used in computer networks. It covers adaptive routing algorithms that reflect changes in network topology and non-adaptive static routing algorithms. Static routing algorithms like shortest path routing and multipath routing are described, where shortest path routing finds the shortest path between node pairs and multipath routing uses multiple random paths. Dijkstra's algorithm is provided as an example of shortest path routing. Distance vector routing is also discussed, where each router maintains a table of distances and routes that is updated through information exchanges between routers. Issues like counting to infinity in distance vector routing are mentioned.
Routing algorithm

The network layer is responsible for routing packets from the source to destination. The routing algorithm is the piece of software that decides where a packet goes next (e.g., which output line, or which node on a broadcast channel).For connectionless networks, the routing decision is made for each datagram. For connection-oriented networks, the decision is made once, at circuit setup time.
Routing Issues
The routing algorithm must deal with the following issues:
Correctness and simplicity: networks are never taken down; individual parts (e.g., links, routers) may fail, but the whole network should not.
Stability: if a link or router fails, how much time elapses before the remaining routers recognize the topology change? (Some never do..)
Fairness and optimality: an inherently intractable problem. Definition of optimality usually doesn't consider fairness. Do we want to maximize channel usage? Minimize average delay?
When we look at routing in detail, we'll consider both adaptive--those that take current traffic and topology into consideration--and nonadaptive algorithms.
Unit 3_Network Layer_Part II.pptx

The document provides information about network layer concepts including routing, forwarding, routing tables, routing algorithms, and routing protocols.
It discusses key network layer duties like interconnecting networks, assigning unique addresses, and encapsulating data for transfer between networks. Forwarding techniques like next-hop routing and network-specific routing are covered. Popular routing algorithms like distance vector routing, link state routing, and path vector routing are summarized.
Common routing protocols for both unicast (RIP) and multicast (MOSPF, DVMRP, CBT, PIM) are introduced along with their basic operations and differences between source-based and group-shared routing trees. IPv4 addressing and IPv6 improvements like larger addresses
Unit 4_Network Layer_Part II.pptx

The document discusses network layer concepts including routing, forwarding, routing algorithms, and routing protocols.
It begins by explaining the duties of the network layer including interconnecting networks, assigning unique addresses, and encapsulating data from the transport layer. It then discusses routing concepts such as delivery, forwarding using techniques like next-hop routing, and routing tables.
Common routing algorithms are also summarized like distance vector routing using RIP, link state routing using OSPF, and path vector routing. Popular unicast routing protocols and multicast protocols are also briefly mentioned including MOSPF, DVMRP, CBT, and PIM.
computer Netwoks - network layer

link state routing,unicast routing, multicast routing,broadcast routing, hierarical routing,congestion control, approach,
Presentation 2

The document discusses routing algorithms used in computer networks. It describes how routing algorithms determine the path that packets take from source to destination. Dynamic routing algorithms adapt to changing network conditions by updating routing tables. Common dynamic algorithms include distance vector routing and link state routing. The document also covers challenges like routing in hierarchical networks, broadcast routing, multicast routing, and routing for mobile and ad-hoc networks.
NetworkAlgorithms.ppt

Network routing algorithms aim to optimize two key performance measures: throughput (quantity of service) and average packet delay (quality of service). Adaptive routing algorithms dynamically change routes based on current network conditions, while nonadaptive algorithms use static routes. Common routing algorithms include shortest path routing, distance vector routing, link state routing, and flooding. Challenges include balancing optimality, fairness, and preventing problems like congestion.
Routing Presentation

routing table ,What is routing ? , what is static routing , what is dynamic routing , types of routing , routing protocols , routing strategy , Download Routing pdf , Download routing ppt , download routing notes , paper on routing
To Download Complete Documentation Visit My Blog
http://studyofcs.blogspot.com/2015/06/what-is-routerwhat-is-routing.html
Download completer BS Computer Science Degree Study Data
http://studyofcs.blogspot.com/p/bs.html
Recommended
Lecture32_RoutingAlgorithmsDV.pdf

The document discusses routing algorithms used in computer networks. It covers adaptive routing algorithms that reflect changes in network topology and non-adaptive static routing algorithms. Static routing algorithms like shortest path routing and multipath routing are described, where shortest path routing finds the shortest path between node pairs and multipath routing uses multiple random paths. Dijkstra's algorithm is provided as an example of shortest path routing. Distance vector routing is also discussed, where each router maintains a table of distances and routes that is updated through information exchanges between routers. Issues like counting to infinity in distance vector routing are mentioned.
Routing algorithm

The network layer is responsible for routing packets from the source to destination. The routing algorithm is the piece of software that decides where a packet goes next (e.g., which output line, or which node on a broadcast channel).For connectionless networks, the routing decision is made for each datagram. For connection-oriented networks, the decision is made once, at circuit setup time.
Routing Issues
The routing algorithm must deal with the following issues:
Correctness and simplicity: networks are never taken down; individual parts (e.g., links, routers) may fail, but the whole network should not.
Stability: if a link or router fails, how much time elapses before the remaining routers recognize the topology change? (Some never do..)
Fairness and optimality: an inherently intractable problem. Definition of optimality usually doesn't consider fairness. Do we want to maximize channel usage? Minimize average delay?
When we look at routing in detail, we'll consider both adaptive--those that take current traffic and topology into consideration--and nonadaptive algorithms.
Unit 3_Network Layer_Part II.pptx

The document provides information about network layer concepts including routing, forwarding, routing tables, routing algorithms, and routing protocols.
It discusses key network layer duties like interconnecting networks, assigning unique addresses, and encapsulating data for transfer between networks. Forwarding techniques like next-hop routing and network-specific routing are covered. Popular routing algorithms like distance vector routing, link state routing, and path vector routing are summarized.
Common routing protocols for both unicast (RIP) and multicast (MOSPF, DVMRP, CBT, PIM) are introduced along with their basic operations and differences between source-based and group-shared routing trees. IPv4 addressing and IPv6 improvements like larger addresses
Unit 4_Network Layer_Part II.pptx

The document discusses network layer concepts including routing, forwarding, routing algorithms, and routing protocols.
It begins by explaining the duties of the network layer including interconnecting networks, assigning unique addresses, and encapsulating data from the transport layer. It then discusses routing concepts such as delivery, forwarding using techniques like next-hop routing, and routing tables.
Common routing algorithms are also summarized like distance vector routing using RIP, link state routing using OSPF, and path vector routing. Popular unicast routing protocols and multicast protocols are also briefly mentioned including MOSPF, DVMRP, CBT, and PIM.
computer Netwoks - network layer

link state routing,unicast routing, multicast routing,broadcast routing, hierarical routing,congestion control, approach,
Presentation 2

The document discusses routing algorithms used in computer networks. It describes how routing algorithms determine the path that packets take from source to destination. Dynamic routing algorithms adapt to changing network conditions by updating routing tables. Common dynamic algorithms include distance vector routing and link state routing. The document also covers challenges like routing in hierarchical networks, broadcast routing, multicast routing, and routing for mobile and ad-hoc networks.
NetworkAlgorithms.ppt

Network routing algorithms aim to optimize two key performance measures: throughput (quantity of service) and average packet delay (quality of service). Adaptive routing algorithms dynamically change routes based on current network conditions, while nonadaptive algorithms use static routes. Common routing algorithms include shortest path routing, distance vector routing, link state routing, and flooding. Challenges include balancing optimality, fairness, and preventing problems like congestion.
Routing Presentation

routing table ,What is routing ? , what is static routing , what is dynamic routing , types of routing , routing protocols , routing strategy , Download Routing pdf , Download routing ppt , download routing notes , paper on routing
To Download Complete Documentation Visit My Blog
http://studyofcs.blogspot.com/2015/06/what-is-routerwhat-is-routing.html
Download completer BS Computer Science Degree Study Data
http://studyofcs.blogspot.com/p/bs.html
Routing algorithms mehodology materials doc1

Routing algorithms in computer networks determine the best path for data transfer between nodes. There are two main types - non-adaptive algorithms which use static routes regardless of network conditions, and adaptive algorithms which can change routes dynamically based on conditions. Examples of routing algorithms include flooding, which broadcasts to all nodes, and link state routing which uses Dijkstra's algorithm to calculate the most efficient paths based on information shared between nodes.
MOBILE COMPUTING Unit 4.pptx

The document provides information about ad-hoc networks, including their characteristics, applications, design issues, and routing protocols. Some key points:
- Ad-hoc networks are infrastructure-less and use multi-hop wireless links between mobile nodes, requiring distributed routing protocols. They are suitable for situations requiring quick deployment like emergencies or military operations.
- Challenges for routing in ad-hoc networks include the dynamic topology, limited bandwidth and energy of nodes, and lack of a centralized entity. Traditional link-state and distance-vector routing protocols are examined.
- Popular link-state protocols like OSPF work by flooding link-state information to build a shared topology database and calculate the shortest path tree
Routing algorithms

Routing Algorithms. Distance Vector routing Algorithm. link state routing algorithm. path vector routing algorithm
11 routing

This document discusses routing in IP networks. It begins by introducing routing and routing protocols. Routers use routing protocols to decide the best path between networks based on metrics like link costs and current congestion. It then provides an example of router and network configurations with link costs. The document discusses routing tables, which contain the next hop for each destination network. It also covers different types of routing like fixed, adaptive, flooding and random routing. Adaptive routing aims to dynamically change paths in response to failures or congestion but faces challenges. The document classifies adaptive routing strategies and algorithms like distance-vector, link-state, and path-vector routing. It concludes by explaining the Dijkstra's and Bellman-Ford least cost
Packet Switching Technique in Computer Network

This document discusses different packet switching paradigms including virtual circuit switching, datagram switching, and source routing. It describes how bridges and extended local area networks (LANs) connect multiple LANs using a spanning tree algorithm to prevent loops. Finally, it covers limitations of bridges and how virtual LANs (VLANs) increase scalability and security by separating broadcast domains.
Lecture number 5 Theory.pdf(machine learning)

This document discusses computer networks and routing protocols. It provides an overview of key topics including:
- The difference between routed protocols like IPv4 and IPv6 that transfer user data, and routing protocols like RIP and OSPF that send route update packets.
- Common routing and routed protocols including IGPs, EGPs, RIP, OSPF, EIGRP and BGP.
- Desirable properties of routing algorithms such as correctness, robustness, stability, fairness and efficiency.
- Types of routing including fixed, flooding, dynamic and default routing. Characteristics of distance vector and link state routing protocols are also outlined.
A Scalable, Commodity Data Center Network Architecture

A Scalable, Commodity Data Center Network Architecture
source : http://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=6&cad=rja&uact=8&ved=0CFUQFjAF&url=http%3A%2F%2Fpages.cs.wisc.edu%2F~akella%2FCS740%2FF08%2FDataCenters.ppt&ei=BVxPVIy_Bse68gWwy4HAAw&usg=AFQjCNGYUB_rhG5dbCNAJyvYrhuZ0L7upg&sig2=yYxOytU7vpT7TT8-qD48CA&bvm=bv.77880786,d.dGc
Routing and IP in Advance Computer Network,Vikram Snehi

This document provides an overview of routing in IP networks. It discusses different routing protocols and algorithms used by routers to determine the best path between networks. Distance-vector protocols like RIP use hop count as the routing metric and exchange full routing tables periodically. Link-state protocols like OSPF use link costs and flood link state information to all routers to build a topology map and calculate shortest paths using Dijkstra's algorithm. BGP is used as the exterior routing protocol between autonomous systems. Areas are used in large OSPF networks to reduce routing overhead.
MobileAdHocRoutingProtocols.pptx

The lecture discusses routing in mobile wireless networks. It covers issues like limited transmission range, mobility-induced route changes, and security hazards in wireless transmissions. Various routing protocols are introduced, including proactive protocols that maintain routing information independently, on-demand protocols that discover routes only when needed, and hybrid approaches that combine the two. Specific protocols discussed include DSR, AODV, ZRP, LAR, and protocols for mesh and cellular networks. The tradeoffs between different routing approaches are also summarized.
Network layer

The document discusses network layer design issues and protocols. It covers store-and-forward packet switching, the functions of the network layer including routing and congestion control. It then describes the implementation of connectionless and connection-oriented services, comparing virtual circuits and datagrams. Various routing algorithms are also summarized, such as shortest path, flooding, distance vector, and link state routing.
Lecture 7

This document discusses wireless ad hoc and sensor networks and routing protocols. It begins by defining routing as the process of moving data packets from a source to destination, which is usually performed by routers. Common objectives of routing protocols are to route packets along optimal paths while adapting to changing network conditions. Routing protocols are then categorized as link-state or distance-vector protocols. The document also discusses the purposes and challenges of routing in wireless ad hoc networks, as well as requirements for ad hoc routing protocols. Finally, it provides an overview of different types of ad hoc unicast routing protocols, including table-driven, on-demand, and hybrid protocols.
QSpiders - Good to Know Network Concepts

The network layer is concerned with routing packets from the source to the destination across multiple networks. It must understand the topology of connected networks and choose optimal paths while avoiding overloading some lines. The network layer provides either connection-oriented or connectionless services to the transport layer and deals with differences when sources and destinations are in different networks. Dynamic routing algorithms like distance vector routing are used to adaptively route packets based on current network conditions.
routing 23.pptx

Routing is a crucial aspect of packet switched networks that determines the path of packets between source and destination nodes. There are several routing strategies including fixed, flooding, random, and adaptive routing. Fixed routing uses predetermined routes that do not change, while adaptive routing allows routes to change in response to network conditions. Key algorithms for adaptive routing include Bellman-Ford and Dijkstra's algorithm, which calculate least cost paths through a network based on performance criteria like minimum hop count or link costs. These algorithms allow routing decisions to adapt over time based on updated network information.
Classification of routing protocols

This document discusses different types of routing protocols for mobile ad hoc networks. It begins by classifying routing protocols into four categories: proactive (table-driven), reactive (on-demand), hybrid, and geographic location-assisted. It then provides more details on proactive protocols like DSDV, and reactive protocols like DSR and AODV. For DSDV, it describes how routing tables are regularly exchanged and updated when link breaks occur. For DSR and AODV, it explains how routes are discovered on-demand via route requests and replies. Key differences between DSR and AODV are also summarized.
Routing protocols-network-layer

This document provides an overview of key concepts in network layer delivery, forwarding, and routing. It discusses delivery and forwarding of packets, including direct vs indirect delivery and next-hop vs route forwarding methods. It also summarizes several unicast routing protocols, including distance vector protocols like RIP and link state protocols like OSPF. Finally, it discusses path vector routing and Border Gateway Protocol (BGP) for interdomain routing.
Networking devices

This document discusses different types of networking devices used to connect local area networks (LANs). It describes hubs, repeaters, bridges, routers, and gateways. Hubs and repeaters operate at the physical layer, bridges operate at the physical and data link layers, and routers and gateways operate at the network layer and above to connect multiple networks and perform protocol conversion. The document provides details on the functions and characteristics of each type of device.
Computer network switching

This document discusses different types of computer networks, including switched, circuit-switched, packet-switched, and datagram networks. It explains that switched networks connect devices through switches that create temporary connections. Circuit-switched networks require connection setup and teardown and dedicate resources to each connection. Packet-switched networks divide messages into packets that are routed independently without resource reservation. Datagram networks treat each packet independently and use dynamic routing tables to route packets by destination address. Virtual circuit networks combine aspects of circuit-switched and datagram networks by routing packets along the same path with connection setup and teardown phases.
Routing Protocols.pdf

The document discusses IP addresses, subnetting, and routing algorithms. It provides information on:
- IP addresses containing a network and host portion, allowing a hierarchical structure.
- Subnetting allowing a single IP network address to span multiple physical networks.
- Link-state and distance-vector routing algorithms, with distance-vector using the distributed Bellman-Ford algorithm and link-state using Dijkstra's algorithm.
Networkingdevices 120505003202-phpapp02

Networking devices can be categorized into five groups based on the OSI layer in which they operate: hubs, repeaters, bridges, routers, and gateways. Hubs and repeaters operate at the physical layer, bridges operate at the data link layer, and routers and gateways operate at the network layer or above. Bridges connect local area networks (LANs) by filtering and forwarding traffic between them based on MAC addresses, while routers connect LANs and wide area networks by routing packets based on logical network layer addresses.
16 bgp

Policy-based path-vector routing protocols like BGP allow autonomous systems (ASes) to apply local policies to control routing behavior and influence path selection. BGP advertises the entire path to destinations rather than just distances, enabling faster detection of routing loops. Each AS can filter and modify routing attributes to apply import and export policies that implement traffic engineering, business relationships, and security policies.
22CYT12-Unit-V-E Waste and its Management.ppt

Introduction- e - waste – definition - sources of e-waste– hazardous substances in e-waste - effects of e-waste on environment and human health- need for e-waste management– e-waste handling rules - waste minimization techniques for managing e-waste – recycling of e-waste - disposal treatment methods of e- waste – mechanism of extraction of precious metal from leaching solution-global Scenario of E-waste – E-waste in India- case studies.
Electric vehicle and photovoltaic advanced roles in enhancing the financial p...

Climate change's impact on the planet forced the United Nations and governments to promote green energies and electric transportation. The deployments of photovoltaic (PV) and electric vehicle (EV) systems gained stronger momentum due to their numerous advantages over fossil fuel types. The advantages go beyond sustainability to reach financial support and stability. The work in this paper introduces the hybrid system between PV and EV to support industrial and commercial plants. This paper covers the theoretical framework of the proposed hybrid system including the required equation to complete the cost analysis when PV and EV are present. In addition, the proposed design diagram which sets the priorities and requirements of the system is presented. The proposed approach allows setup to advance their power stability, especially during power outages. The presented information supports researchers and plant owners to complete the necessary analysis while promoting the deployment of clean energy. The result of a case study that represents a dairy milk farmer supports the theoretical works and highlights its advanced benefits to existing plants. The short return on investment of the proposed approach supports the paper's novelty approach for the sustainable electrical system. In addition, the proposed system allows for an isolated power setup without the need for a transmission line which enhances the safety of the electrical network
More Related Content
Similar to Lecture34_RoutingAlgorithmsLSR.pdf
Routing algorithms mehodology materials doc1

Routing algorithms in computer networks determine the best path for data transfer between nodes. There are two main types - non-adaptive algorithms which use static routes regardless of network conditions, and adaptive algorithms which can change routes dynamically based on conditions. Examples of routing algorithms include flooding, which broadcasts to all nodes, and link state routing which uses Dijkstra's algorithm to calculate the most efficient paths based on information shared between nodes.
MOBILE COMPUTING Unit 4.pptx

The document provides information about ad-hoc networks, including their characteristics, applications, design issues, and routing protocols. Some key points:
- Ad-hoc networks are infrastructure-less and use multi-hop wireless links between mobile nodes, requiring distributed routing protocols. They are suitable for situations requiring quick deployment like emergencies or military operations.
- Challenges for routing in ad-hoc networks include the dynamic topology, limited bandwidth and energy of nodes, and lack of a centralized entity. Traditional link-state and distance-vector routing protocols are examined.
- Popular link-state protocols like OSPF work by flooding link-state information to build a shared topology database and calculate the shortest path tree
Routing algorithms

Routing Algorithms. Distance Vector routing Algorithm. link state routing algorithm. path vector routing algorithm
11 routing

This document discusses routing in IP networks. It begins by introducing routing and routing protocols. Routers use routing protocols to decide the best path between networks based on metrics like link costs and current congestion. It then provides an example of router and network configurations with link costs. The document discusses routing tables, which contain the next hop for each destination network. It also covers different types of routing like fixed, adaptive, flooding and random routing. Adaptive routing aims to dynamically change paths in response to failures or congestion but faces challenges. The document classifies adaptive routing strategies and algorithms like distance-vector, link-state, and path-vector routing. It concludes by explaining the Dijkstra's and Bellman-Ford least cost
Packet Switching Technique in Computer Network

This document discusses different packet switching paradigms including virtual circuit switching, datagram switching, and source routing. It describes how bridges and extended local area networks (LANs) connect multiple LANs using a spanning tree algorithm to prevent loops. Finally, it covers limitations of bridges and how virtual LANs (VLANs) increase scalability and security by separating broadcast domains.
Lecture number 5 Theory.pdf(machine learning)

This document discusses computer networks and routing protocols. It provides an overview of key topics including:
- The difference between routed protocols like IPv4 and IPv6 that transfer user data, and routing protocols like RIP and OSPF that send route update packets.
- Common routing and routed protocols including IGPs, EGPs, RIP, OSPF, EIGRP and BGP.
- Desirable properties of routing algorithms such as correctness, robustness, stability, fairness and efficiency.
- Types of routing including fixed, flooding, dynamic and default routing. Characteristics of distance vector and link state routing protocols are also outlined.
A Scalable, Commodity Data Center Network Architecture

A Scalable, Commodity Data Center Network Architecture
source : http://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=6&cad=rja&uact=8&ved=0CFUQFjAF&url=http%3A%2F%2Fpages.cs.wisc.edu%2F~akella%2FCS740%2FF08%2FDataCenters.ppt&ei=BVxPVIy_Bse68gWwy4HAAw&usg=AFQjCNGYUB_rhG5dbCNAJyvYrhuZ0L7upg&sig2=yYxOytU7vpT7TT8-qD48CA&bvm=bv.77880786,d.dGc
Routing and IP in Advance Computer Network,Vikram Snehi

This document provides an overview of routing in IP networks. It discusses different routing protocols and algorithms used by routers to determine the best path between networks. Distance-vector protocols like RIP use hop count as the routing metric and exchange full routing tables periodically. Link-state protocols like OSPF use link costs and flood link state information to all routers to build a topology map and calculate shortest paths using Dijkstra's algorithm. BGP is used as the exterior routing protocol between autonomous systems. Areas are used in large OSPF networks to reduce routing overhead.
MobileAdHocRoutingProtocols.pptx

The lecture discusses routing in mobile wireless networks. It covers issues like limited transmission range, mobility-induced route changes, and security hazards in wireless transmissions. Various routing protocols are introduced, including proactive protocols that maintain routing information independently, on-demand protocols that discover routes only when needed, and hybrid approaches that combine the two. Specific protocols discussed include DSR, AODV, ZRP, LAR, and protocols for mesh and cellular networks. The tradeoffs between different routing approaches are also summarized.
Network layer

The document discusses network layer design issues and protocols. It covers store-and-forward packet switching, the functions of the network layer including routing and congestion control. It then describes the implementation of connectionless and connection-oriented services, comparing virtual circuits and datagrams. Various routing algorithms are also summarized, such as shortest path, flooding, distance vector, and link state routing.
Lecture 7

This document discusses wireless ad hoc and sensor networks and routing protocols. It begins by defining routing as the process of moving data packets from a source to destination, which is usually performed by routers. Common objectives of routing protocols are to route packets along optimal paths while adapting to changing network conditions. Routing protocols are then categorized as link-state or distance-vector protocols. The document also discusses the purposes and challenges of routing in wireless ad hoc networks, as well as requirements for ad hoc routing protocols. Finally, it provides an overview of different types of ad hoc unicast routing protocols, including table-driven, on-demand, and hybrid protocols.
QSpiders - Good to Know Network Concepts

The network layer is concerned with routing packets from the source to the destination across multiple networks. It must understand the topology of connected networks and choose optimal paths while avoiding overloading some lines. The network layer provides either connection-oriented or connectionless services to the transport layer and deals with differences when sources and destinations are in different networks. Dynamic routing algorithms like distance vector routing are used to adaptively route packets based on current network conditions.
routing 23.pptx

Routing is a crucial aspect of packet switched networks that determines the path of packets between source and destination nodes. There are several routing strategies including fixed, flooding, random, and adaptive routing. Fixed routing uses predetermined routes that do not change, while adaptive routing allows routes to change in response to network conditions. Key algorithms for adaptive routing include Bellman-Ford and Dijkstra's algorithm, which calculate least cost paths through a network based on performance criteria like minimum hop count or link costs. These algorithms allow routing decisions to adapt over time based on updated network information.
Classification of routing protocols

This document discusses different types of routing protocols for mobile ad hoc networks. It begins by classifying routing protocols into four categories: proactive (table-driven), reactive (on-demand), hybrid, and geographic location-assisted. It then provides more details on proactive protocols like DSDV, and reactive protocols like DSR and AODV. For DSDV, it describes how routing tables are regularly exchanged and updated when link breaks occur. For DSR and AODV, it explains how routes are discovered on-demand via route requests and replies. Key differences between DSR and AODV are also summarized.
Routing protocols-network-layer

This document provides an overview of key concepts in network layer delivery, forwarding, and routing. It discusses delivery and forwarding of packets, including direct vs indirect delivery and next-hop vs route forwarding methods. It also summarizes several unicast routing protocols, including distance vector protocols like RIP and link state protocols like OSPF. Finally, it discusses path vector routing and Border Gateway Protocol (BGP) for interdomain routing.
Networking devices

This document discusses different types of networking devices used to connect local area networks (LANs). It describes hubs, repeaters, bridges, routers, and gateways. Hubs and repeaters operate at the physical layer, bridges operate at the physical and data link layers, and routers and gateways operate at the network layer and above to connect multiple networks and perform protocol conversion. The document provides details on the functions and characteristics of each type of device.
Computer network switching

This document discusses different types of computer networks, including switched, circuit-switched, packet-switched, and datagram networks. It explains that switched networks connect devices through switches that create temporary connections. Circuit-switched networks require connection setup and teardown and dedicate resources to each connection. Packet-switched networks divide messages into packets that are routed independently without resource reservation. Datagram networks treat each packet independently and use dynamic routing tables to route packets by destination address. Virtual circuit networks combine aspects of circuit-switched and datagram networks by routing packets along the same path with connection setup and teardown phases.
Routing Protocols.pdf

The document discusses IP addresses, subnetting, and routing algorithms. It provides information on:
- IP addresses containing a network and host portion, allowing a hierarchical structure.
- Subnetting allowing a single IP network address to span multiple physical networks.
- Link-state and distance-vector routing algorithms, with distance-vector using the distributed Bellman-Ford algorithm and link-state using Dijkstra's algorithm.
Networkingdevices 120505003202-phpapp02

Networking devices can be categorized into five groups based on the OSI layer in which they operate: hubs, repeaters, bridges, routers, and gateways. Hubs and repeaters operate at the physical layer, bridges operate at the data link layer, and routers and gateways operate at the network layer or above. Bridges connect local area networks (LANs) by filtering and forwarding traffic between them based on MAC addresses, while routers connect LANs and wide area networks by routing packets based on logical network layer addresses.
16 bgp

Policy-based path-vector routing protocols like BGP allow autonomous systems (ASes) to apply local policies to control routing behavior and influence path selection. BGP advertises the entire path to destinations rather than just distances, enabling faster detection of routing loops. Each AS can filter and modify routing attributes to apply import and export policies that implement traffic engineering, business relationships, and security policies.
Similar to Lecture34_RoutingAlgorithmsLSR.pdf (20)
A Scalable, Commodity Data Center Network Architecture

A Scalable, Commodity Data Center Network Architecture
Routing and IP in Advance Computer Network,Vikram Snehi

Routing and IP in Advance Computer Network,Vikram Snehi
Recently uploaded
22CYT12-Unit-V-E Waste and its Management.ppt

Introduction- e - waste – definition - sources of e-waste– hazardous substances in e-waste - effects of e-waste on environment and human health- need for e-waste management– e-waste handling rules - waste minimization techniques for managing e-waste – recycling of e-waste - disposal treatment methods of e- waste – mechanism of extraction of precious metal from leaching solution-global Scenario of E-waste – E-waste in India- case studies.
Electric vehicle and photovoltaic advanced roles in enhancing the financial p...

Climate change's impact on the planet forced the United Nations and governments to promote green energies and electric transportation. The deployments of photovoltaic (PV) and electric vehicle (EV) systems gained stronger momentum due to their numerous advantages over fossil fuel types. The advantages go beyond sustainability to reach financial support and stability. The work in this paper introduces the hybrid system between PV and EV to support industrial and commercial plants. This paper covers the theoretical framework of the proposed hybrid system including the required equation to complete the cost analysis when PV and EV are present. In addition, the proposed design diagram which sets the priorities and requirements of the system is presented. The proposed approach allows setup to advance their power stability, especially during power outages. The presented information supports researchers and plant owners to complete the necessary analysis while promoting the deployment of clean energy. The result of a case study that represents a dairy milk farmer supports the theoretical works and highlights its advanced benefits to existing plants. The short return on investment of the proposed approach supports the paper's novelty approach for the sustainable electrical system. In addition, the proposed system allows for an isolated power setup without the need for a transmission line which enhances the safety of the electrical network
KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions

K8sGPT is a tool that analyzes and diagnoses Kubernetes clusters. This presentation was used to share the requirements and dependencies to deploy K8sGPT in a local environment.
Computational Engineering IITH Presentation

This Presentation will give you a brief idea about what Computational Engineering at IIT Hyderabad has to offer.
学校原版美国波士顿大学毕业证学历学位证书原版一模一样

原版一模一样【微信:741003700 】【美国波士顿大学毕业证学历学位证书】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
Advanced control scheme of doubly fed induction generator for wind turbine us...

This paper describes a speed control device for generating electrical energy on an electricity network based on the doubly fed induction generator (DFIG) used for wind power conversion systems. At first, a double-fed induction generator model was constructed. A control law is formulated to govern the flow of energy between the stator of a DFIG and the energy network using three types of controllers: proportional integral (PI), sliding mode controller (SMC) and second order sliding mode controller (SOSMC). Their different results in terms of power reference tracking, reaction to unexpected speed fluctuations, sensitivity to perturbations, and resilience against machine parameter alterations are compared. MATLAB/Simulink was used to conduct the simulations for the preceding study. Multiple simulations have shown very satisfying results, and the investigations demonstrate the efficacy and power-enhancing capabilities of the suggested control system.
Comparative analysis between traditional aquaponics and reconstructed aquapon...

The aquaponic system of planting is a method that does not require soil usage. It is a method that only needs water, fish, lava rocks (a substitute for soil), and plants. Aquaponic systems are sustainable and environmentally friendly. Its use not only helps to plant in small spaces but also helps reduce artificial chemical use and minimizes excess water use, as aquaponics consumes 90% less water than soil-based gardening. The study applied a descriptive and experimental design to assess and compare conventional and reconstructed aquaponic methods for reproducing tomatoes. The researchers created an observation checklist to determine the significant factors of the study. The study aims to determine the significant difference between traditional aquaponics and reconstructed aquaponics systems propagating tomatoes in terms of height, weight, girth, and number of fruits. The reconstructed aquaponics system’s higher growth yield results in a much more nourished crop than the traditional aquaponics system. It is superior in its number of fruits, height, weight, and girth measurement. Moreover, the reconstructed aquaponics system is proven to eliminate all the hindrances present in the traditional aquaponics system, which are overcrowding of fish, algae growth, pest problems, contaminated water, and dead fish.
cnn.pptx Convolutional neural network used for image classication

Convolutional Neural Network used for image classification
BRAIN TUMOR DETECTION for seminar ppt.pdf

BRAIN TUMOR DETECTION
AND CLASSIFICATION USING
ARTIFICIAL INTELLIGENCE
CHINA’S GEO-ECONOMIC OUTREACH IN CENTRAL ASIAN COUNTRIES AND FUTURE PROSPECT

The rivalry between prominent international actors for dominance over Central Asia's hydrocarbon
reserves and the ancient silk trade route, along with China's diplomatic endeavours in the area, has been
referred to as the "New Great Game." This research centres on the power struggle, considering
geopolitical, geostrategic, and geoeconomic variables. Topics including trade, political hegemony, oil
politics, and conventional and nontraditional security are all explored and explained by the researcher.
Using Mackinder's Heartland, Spykman Rimland, and Hegemonic Stability theories, examines China's role
in Central Asia. This study adheres to the empirical epistemological method and has taken care of
objectivity. This study analyze primary and secondary research documents critically to elaborate role of
china’s geo economic outreach in central Asian countries and its future prospect. China is thriving in trade,
pipeline politics, and winning states, according to this study, thanks to important instruments like the
Shanghai Cooperation Organisation and the Belt and Road Economic Initiative. According to this study,
China is seeing significant success in commerce, pipeline politics, and gaining influence on other
governments. This success may be attributed to the effective utilisation of key tools such as the Shanghai
Cooperation Organisation and the Belt and Road Economic Initiative.
官方认证美国密歇根州立大学毕业证学位证书原版一模一样

原版一模一样【微信:741003700 】【美国密歇根州立大学毕业证学位证书】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
ISPM 15 Heat Treated Wood Stamps and why your shipping must have one

For International shipping and maritime laws all wood must contain the ISPM 15 Stamp. Here is how and why.
The Python for beginners. This is an advance computer language.

Python language is very important language at this time. we can easily understand this language by these notes.
AI assisted telemedicine KIOSK for Rural India.pptx

It gives the overall description of SIH problem statement " AI assisted telemedicine KIOSK for Rural India".
Recently uploaded (20)
Electric vehicle and photovoltaic advanced roles in enhancing the financial p...

Electric vehicle and photovoltaic advanced roles in enhancing the financial p...
KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions

KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions
Advanced control scheme of doubly fed induction generator for wind turbine us...

Advanced control scheme of doubly fed induction generator for wind turbine us...
Generative AI leverages algorithms to create various forms of content

Generative AI leverages algorithms to create various forms of content
Comparative analysis between traditional aquaponics and reconstructed aquapon...

Comparative analysis between traditional aquaponics and reconstructed aquapon...
cnn.pptx Convolutional neural network used for image classication

cnn.pptx Convolutional neural network used for image classication
CHINA’S GEO-ECONOMIC OUTREACH IN CENTRAL ASIAN COUNTRIES AND FUTURE PROSPECT

CHINA’S GEO-ECONOMIC OUTREACH IN CENTRAL ASIAN COUNTRIES AND FUTURE PROSPECT
Introduction to AI Safety (public presentation).pptx

Introduction to AI Safety (public presentation).pptx
ISPM 15 Heat Treated Wood Stamps and why your shipping must have one

ISPM 15 Heat Treated Wood Stamps and why your shipping must have one
The Python for beginners. This is an advance computer language.

The Python for beginners. This is an advance computer language.
AI assisted telemedicine KIOSK for Rural India.pptx

AI assisted telemedicine KIOSK for Rural India.pptx
Engineering Drawings Lecture Detail Drawings 2014.pdf

Engineering Drawings Lecture Detail Drawings 2014.pdf
Lecture34_RoutingAlgorithmsLSR.pdf
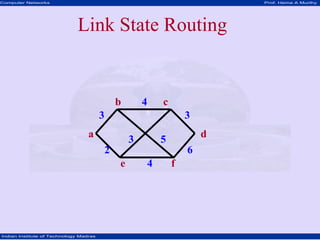
- 1. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras a b c d f e 3 4 6 5 3 4 3 2 Link State Routing
- 2. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Link State Routing • Discover its neighbour and learn network addresses – Measure cost to each of its neighbours – Construct a packet telling what it has learnt – Send packet to all other routers – With link state packets from all router construct shortest path to every other router
- 3. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras b seqno age 3 4 5 f c d e seqno age 2 3 f c a f seqno age 5 6 e d b c seqno age 3 e d b 4 3 4 4 a seqno age 3 2 c b d seqno age 3 f c 6 Links State Packets from Different Routers
- 4. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Link State Routing • Flags – Send flags • On which lines should the packets be sent – Ack flags • On which lines should the packets be acked – Seqno • Sequence number of packet – Useful to distinguish between new and old packets – Age • Remove packets that are circulating that are aged
- 5. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Link State Routing • Distribution of link state packets: – Periodically flood – dam the flood – seqno – • new forward • old discard • lower discard • What if seqno corrupted – Packet discarded after it has aged – decrementing age by route – Decrement age also on time • All link state packet acked echo reply/ echo request with timestamp
- 6. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Link state packet information (router b) 1 0 0 0 1 1 59 21 d 1 0 1 0 1 0 60 20 c 0 1 0 1 0 1 51 21 e 1 1 0 0 0 1 60 21 f 0 1 1 1 0 0 60 21 a src seqno age ack send a c f a c f Once all link state packets available – compute SSSP on all possible destination Data
- 7. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Distributed Routing • Too many routers: – Hierarchical routing – Backbone routers – Regional routers (Points of Presence) – Subnetting
- 8. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Distributed Routing • Flooding (Broadcast routing) – Send distinct packet to every host (wasteful of network bw) – Every incoming packet sent on every out going line except the line on which it arrived. – Generates large number of packets • Use hop count – Seqno to prevent reflooding – Selective flooding • East west need not be sent south north • Flooding in military – When master dies
- 9. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras 1a 1b 1c 2a 2b 2c 2d 3a 3b 3c 3d 3e 4a 4b 4c 5a 5b Hierarchical routing
- 10. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras 1 5b 1 5a 1 1b 0 0 1c 1 1a 1b 1c 5a 2 1c 3 1c 4 1c 2 1b 1 1a 1 1b - - 1a 1b 1c 5 2 3 4 Full table 1a Line Hop Hierarchical routing table 1a Line Hop Path 1a to 3a via 1c = 6 1a to 3a via 2a = 5 Therefore not always the best.
- 11. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Distributed Routing (Miscellaneous) • Multi destination routing: – Each packet contains a list of destinations – Router check destinations for choosing output lines – Copy of packet made and forwarded only line where destination exists – Partitioning of destination into the output lines – After sufficient number of hops – each packet only one destination
- 12. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Distributed Routing (Miscellaneous) • Multidestination Routing – Sending a message to a group of hosts – Routers must know about hosts that belong to the same group – Prune spanning tree to include only the edges of hosts in the group – Forward packets in that group • Link state / distance vector • Node not in group tells host not to send – n groups – m members
- 13. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Distributed Routing (Miscellaneous) • Sink tree router / spanning tree – Each router copies packets on to output lines on spanning tree except line it arrived. • Reverse Path Forwarding: – Broadcast packet at router forwarded on all lines other line it arrived – Provided packet arrived on preferred – Otherwise discarded – No need to know spanning tree
- 14. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Distributed Routing (Miscellaneous) • When a router receives a multicast packet – Examines spanning tree – Prune tree to lead to hosts only on the group – Forward packets only on pruned tree • Link state pruning: – Each router aware of the complete subnet topolo – Prune spanning tree • Start from end of each path and work toward the root – Distance vector approach • Reverse path forwarding – Send message back to host to prune its tree
- 15. Computer Networks Prof. Hema A Murthy Indian Institute of Technology Madras Distributed Routing (Miscellaneous) • Core base tree – Single spanning tree / group – Root near middle of the group – Host sends multicast packet send to the root – Multicast along spanning tree