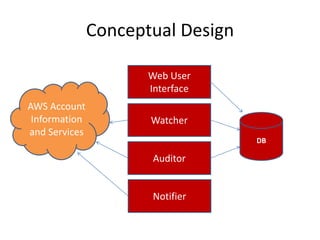
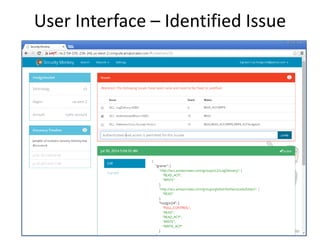
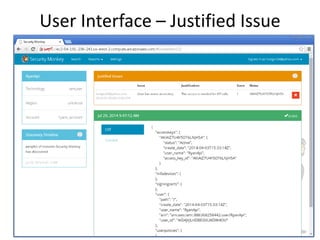
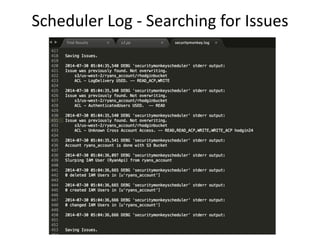
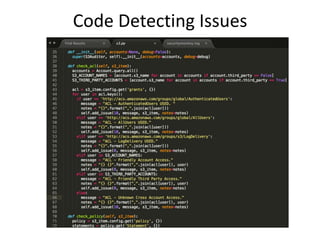
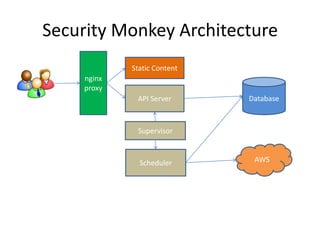
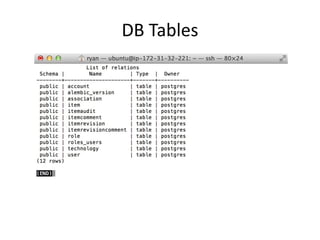
Security Monkey is an open-source cloud security tracking system developed by Netflix to monitor security policies for its AWS accounts starting in 2011. It features AWS resource inspection, change notifications, and historical data maintenance, while supporting multiple accounts and custom rule creation. The system utilizes a range of technologies, including Python, Flask, and PostgreSQL, to provide various user interfaces for managing and auditing security settings across multiple AWS services.