Securing ARP in Software Defined Networks
•Download as PPTX, PDF•
0 likes•142 views
The mapping of Layer 3 (IP) to Layer 2 (MAC) addresses is a key service in IP networks, and is achieved via the ARP protocol in IPv4, and the NDP protocol in IPv6. Due to their stateless nature and lack of authentication, both ARP and NDP are vulnerable to spoofing attacks, which can enable Denial of Service (DoS) or man-in-the-middle (MITM) attacks. In this paper, we discuss the problem of ARP spoofing in the context of Software Defined Networks (SDNs), and present a new mitigation approach which leverages the centralised network control of SDN.
Report
Share
Report
Share
More Related Content
What's hot
What's hot (20)
APNIC Hackathon IPv4 & IPv6 security & threat comparisons

APNIC Hackathon IPv4 & IPv6 security & threat comparisons
SSL basics and SSL packet analysis using wireshark

SSL basics and SSL packet analysis using wireshark
Address resolution protocol and internet control message protocol

Address resolution protocol and internet control message protocol
Viewers also liked
Software Defined Networks Network Function Virtualization Pivotal Technologies

Software Defined Networks Network Function Virtualization Pivotal TechnologiesOpen Networking Summits
Viewers also liked (13)
Software Defined Networks Network Function Virtualization Pivotal Technologies

Software Defined Networks Network Function Virtualization Pivotal Technologies
Similar to Securing ARP in Software Defined Networks
Similar to Securing ARP in Software Defined Networks (20)
AN ACTIVE HOST-BASED INTRUSION DETECTION SYSTEM FOR ARP-RELATED ATTACKS AND I...

AN ACTIVE HOST-BASED INTRUSION DETECTION SYSTEM FOR ARP-RELATED ATTACKS AND I...
Recently uploaded
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Securing ARP in Software Defined Networks
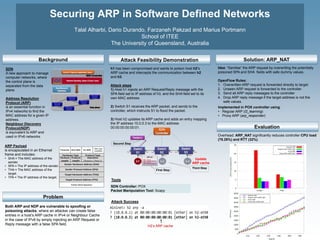
- 1. Securing ARP in Software Defined Networks Talal Alharbi, Dario Durando, Farzaneh Pakzad and Marius Portmann School of ITEE The University of Queensland, Australia Solution: ARP_NAT Both ARP and NDP are vulnerable to spoofing or poisoning attacks, where an attacker can create false entries in a host’s ARP cache in IPv4 or Neighbour Cache in the case of IPv6 by simply injecting an ARP Request or Reply message with a false SPA field. h1 has been compromised and wants to poison host h2’s ARP cache and intercepts the communication between h2 and h3. Attack steps 1) Host h1 injects an ARP Request/Reply message with the SPA field set to IP address of h3, and the SHA field set to its own MAC address 2) Switch S1 receives the ARP packet, and sends to the controller, which instructs S1 to flood the packet. 3) Host h2 updates its ARP cache and adds an entry mapping the IP address 10.0.0.3 to the MAC address 00:00:00:00:00:01. Idea: “Sanitise” the ARP request by overwriting the potentially poisoned SPA and SHA fields with safe dummy values. OpenFlow Rules: 1. Overwritten ARP request is forwarded directly to target 2. Unseen ARP request is forwarded to the controller 3. Send all ARP reply messages to the controller 4. Drop ARP reply message if the target address is not the safe values. SDN A new approach to manage computer networks, where the control plane is separated from the data plane. Address Resolution Protocol (ARP) is an essential function in IPv4 networks to find the MAC address for a given IP address. Neighbour Discovery Protocol(NDP) is equivalent to ARP and used in IPv6 networks. ARP Payload is encapsulated in an Ethernet frame and includes: • SHA = The MAC address of the sender. • SPA = The IP address of the sender. • THA = The MAC address of the target. • TPA = The IP address of the target. Overhead: ARP_NAT significantly reduces controller CPU load (78.26%) and RTT (32%). Topology Discovery Update ARP cache Port 1 Port 2 Port 3 Port 2 Port 3 Port 1 Port 1 Port 2 Port 3 h1 h3h2 ARP pkt SPA = 10.0.0.3 SHA = 00:00:00:00:00:01 TPA = 10.0.0.2 THA = 00:00:00:00:00:00 First Step Second Step Third Step SDN Controller: POX Packet Manipulation Tool: Scapy Implemented in POX controller using: • Regular ARP (l2_learning) • Proxy ARP (arp_responder) H2’s ARP cache Evaluation Attack Feasibility DemonstrationBackground Problem Attack Success Tools
