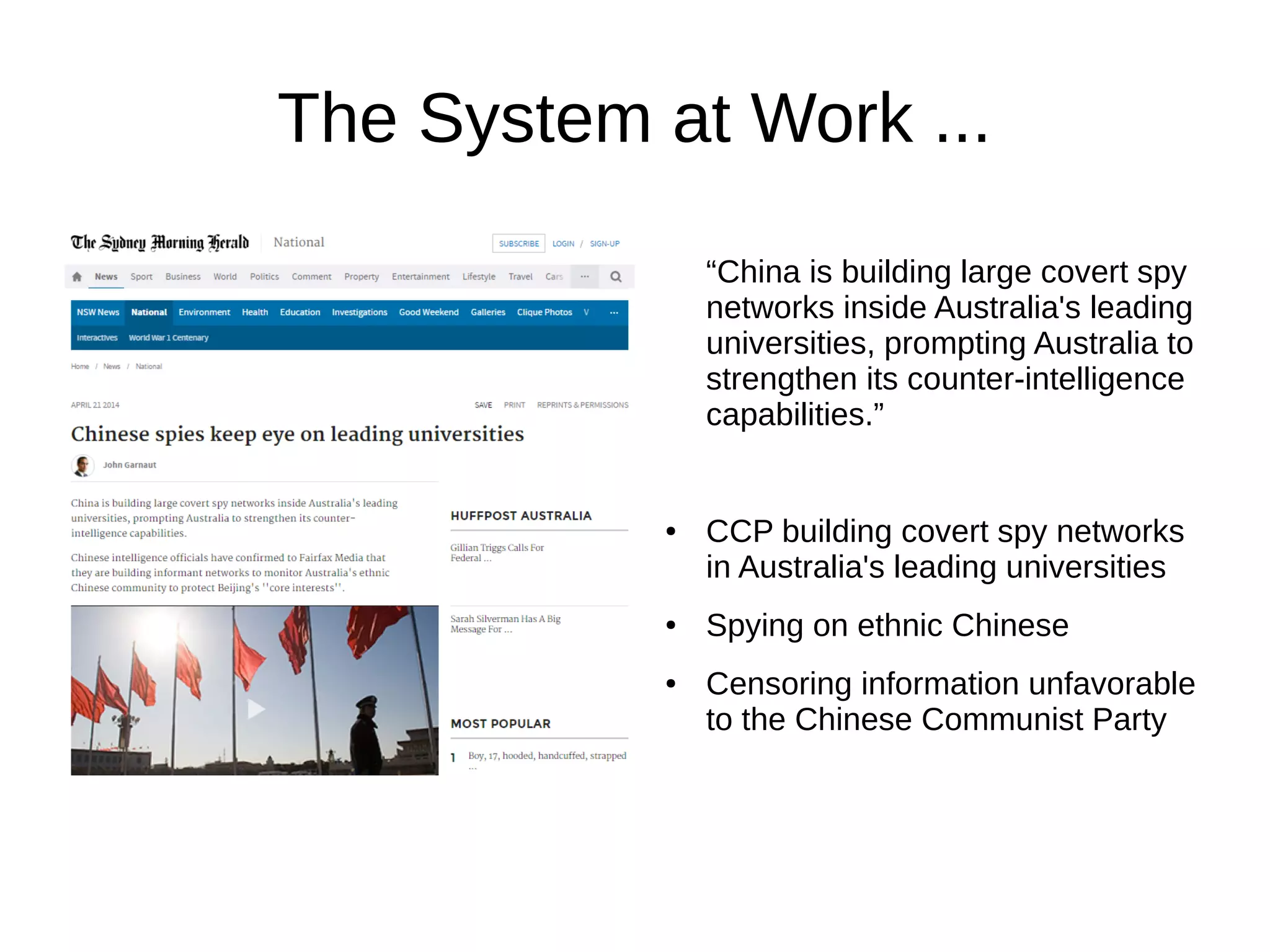
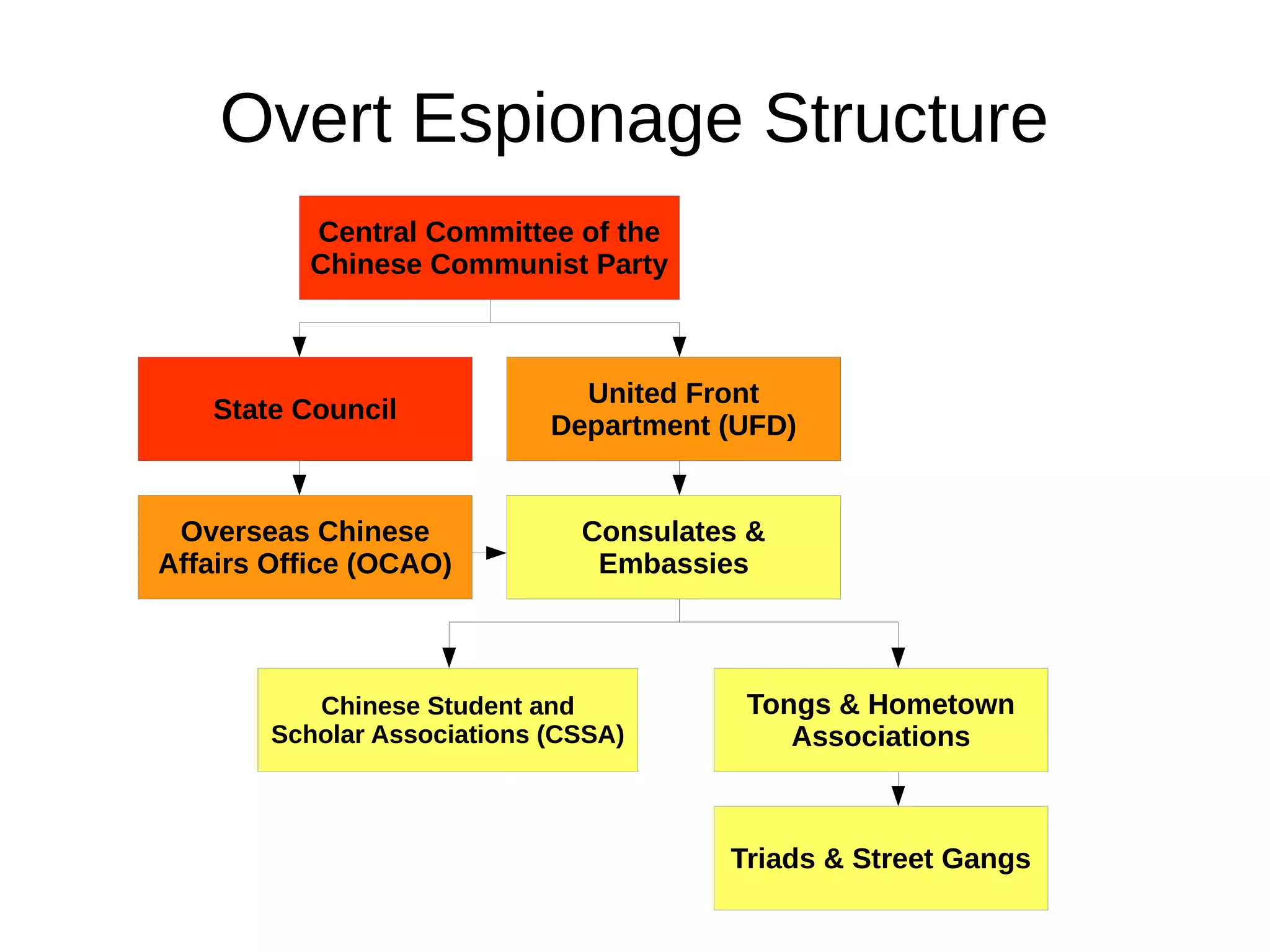
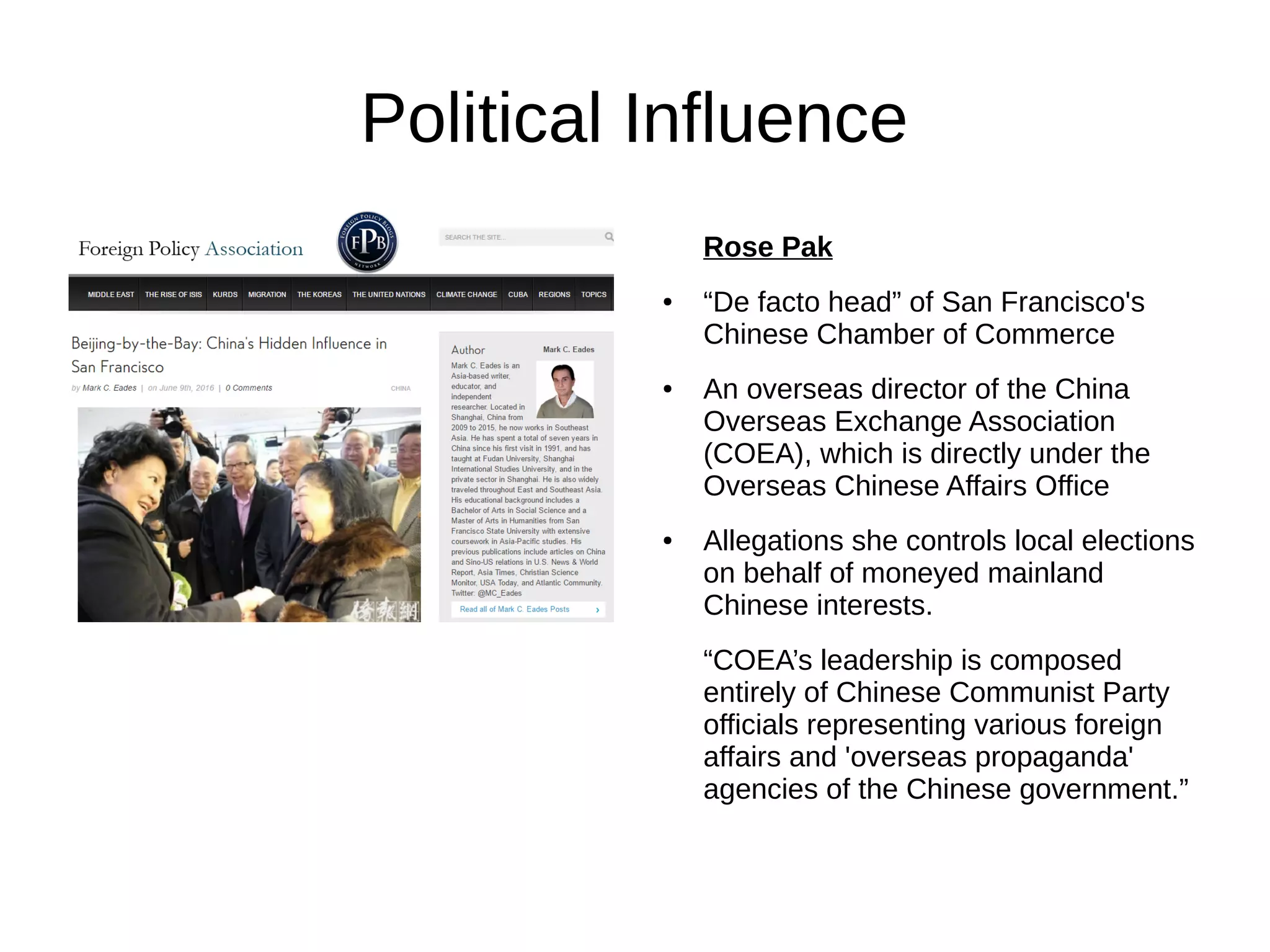
The document outlines the extensive espionage operations by the Chinese Communist Party (CCP) targeting overseas Chinese communities, particularly in the U.S., leveraging various organizations for influence and intelligence gathering. It details a structured approach involving student groups, local businesses, and media to control narratives and mobilize support while suppressing dissent. The CCP's methods include intimidation, economic espionage, and the utilization of consulates and community organizations to manipulate perceptions and govern overseas Chinese populations.












![Triads & Street Gangs
“Once that organization, the Fukien
American Association, became one of the
leading [China]-supported organizations,
they became the host of almost all these
Chinese officials who are visiting New York.”
- Ko-lin Chin, Professor, Rutgers School of
Criminal Justice, interview with Epoch Times
“The Fuk Ching, for example, are affiliated
with the Fukien American Association ...
They allow the gang to operate on their (the
tong’s) territory, thus legitimizing them with
the community.”
- “Chinese Transnational Organized Crime: The
Fuk Ching,” by James O. Finckenauer, Ph.D.,
International Center, National Institute of Justice
● Used for strong-arm tactics
● Used when violence is needed
● Valuable for smuggling channels
● Drug warfare, culture warfare, etc](https://image.slidesharecdn.com/chinaovertspystructure-160818135616/75/Cyber-and-Beyond-The-Inner-Workings-of-Chinese-Espionage-16-2048.jpg)