5 Effective Ways for Website Protection
•
0 likes•125 views
Website protection can immensely fortify web application security and save businesses from hefty costs. Read on to know 5 effective ways for website protection.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
Similar to 5 Effective Ways for Website Protection
Similar to 5 Effective Ways for Website Protection (20)
10 Ways For Mitigating Cybersecurity Risks In Project Management.docx

10 Ways For Mitigating Cybersecurity Risks In Project Management.docx
Web Application Security Vulnerability Management Framework

Web Application Security Vulnerability Management Framework
7 Best Practices to Protect Critical Business Information [Infographic]![7 Best Practices to Protect Critical Business Information [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![7 Best Practices to Protect Critical Business Information [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
7 Best Practices to Protect Critical Business Information [Infographic]
Strategies for Effective Cybersecurity in Web Development pdf.pdf

Strategies for Effective Cybersecurity in Web Development pdf.pdf
Vast ites inc. - 6 steps to improve your life (1).pdf

Vast ites inc. - 6 steps to improve your life (1).pdf
Application Hackers Have A Handbook. Why Shouldn't You?

Application Hackers Have A Handbook. Why Shouldn't You?
How to Build and Validate Ransomware Attack Detections (Secure360)

How to Build and Validate Ransomware Attack Detections (Secure360)
Web Application Security - Everything You Should Know

Web Application Security - Everything You Should Know
Effective Cybersecurity Strategies for Web Developers

Effective Cybersecurity Strategies for Web Developers
Why-Cyber-Security-Matters-Protecting-Your-Business-and-Your-Reputation.pptx

Why-Cyber-Security-Matters-Protecting-Your-Business-and-Your-Reputation.pptx
More from IndusfacePvtLtd
More from IndusfacePvtLtd (11)
Why Manual Pen-Testing is a must have for comprehensive application security ...

Why Manual Pen-Testing is a must have for comprehensive application security ...
Why Startups Need to Strengthen Application Security

Why Startups Need to Strengthen Application Security
Api economy and why effective security is important (1)

Api economy and why effective security is important (1)
Recently uploaded
Recently uploaded (20)
Azure Monitor & Application Insight to monitor Infrastructure & Application

Azure Monitor & Application Insight to monitor Infrastructure & Application
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
5 Effective Ways for Website Protection
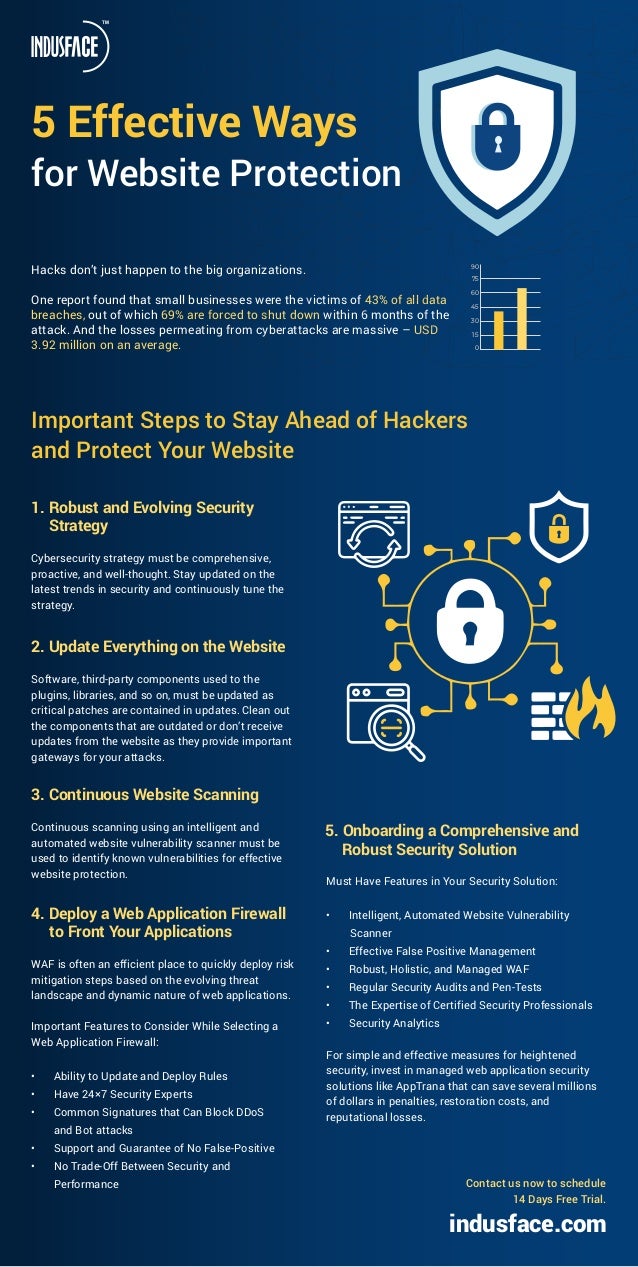
- 1. Important Steps to Stay Ahead of Hackers and Protect Your Website Hacks don’t just happen to the big organizations. One report found that small businesses were the victims of 43% of all data breaches, out of which 69% are forced to shut down within 6 months of the attack. And the losses permeating from cyberattacks are massive – USD 3.92 million on an average. 1. Robust and Evolving Security Strategy Cybersecurity strategy must be comprehensive, proactive, and well-thought. Stay updated on the latest trends in security and continuously tune the strategy. 2. Update Everything on the Website Software, third-party components used to the plugins, libraries, and so on, must be updated as critical patches are contained in updates. Clean out the components that are outdated or don’t receive updates from the website as they provide important gateways for your attacks. 3. Continuous Website Scanning Continuous scanning using an intelligent and automated website vulnerability scanner must be used to identify known vulnerabilities for effective website protection. 4. Deploy a Web Application Firewall to Front Your Applications WAF is often an efficient place to quickly deploy risk mitigation steps based on the evolving threat landscape and dynamic nature of web applications. Important Features to Consider While Selecting a Web Application Firewall: • Ability to Update and Deploy Rules • Have 24×7 Security Experts • Common Signatures that Can Block DDoS and Bot attacks • Support and Guarantee of No False-Positive • No Trade-Off Between Security and Performance 5. Onboarding a Comprehensive and Robust Security Solution Must Have Features in Your Security Solution: • Intelligent, Automated Website Vulnerability Scanner • Effective False Positive Management • Robust, Holistic, and Managed WAF • Regular Security Audits and Pen-Tests • The Expertise of Certified Security Professionals • Security Analytics For simple and effective measures for heightened security, invest in managed web application security solutions like AppTrana that can save several millions of dollars in penalties, restoration costs, and reputational losses. Contact us now to schedule 14 Days Free Trial. indusface.com 5 Effective Ways for Website Protection 0 15 30 45 60 75 90