Controls in information system
•Download as PPT, PDF•
0 likes•57 views
PPt on categories of control in IS on the basis of function, objective & audit
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (20)
Use of IoT in increasing opeartional efficiency in manufacturing plants- a ca...

Use of IoT in increasing opeartional efficiency in manufacturing plants- a ca...
edischallengestheprevailingviewofelectricalcompliancemanagement

edischallengestheprevailingviewofelectricalcompliancemanagement
Vulnerability Management for Healthcare Enterprise Networks

Vulnerability Management for Healthcare Enterprise Networks
Similar to Controls in information system
PACE-IT, Security+2.7: Physical Security and Enviornmental Controls

PACE-IT, Security+2.7: Physical Security and Enviornmental ControlsPace IT at Edmonds Community College
Tips for IT Risk Management Prof. Hernan Huwyler Information Security Institute

Tips for IT Risk Management Prof. Hernan Huwyler Information Security InstituteHernan Huwyler, MBA CPA
Similar to Controls in information system (20)
Operational Efficiency Based on Innovative Automation, Industry Expertise, En...

Operational Efficiency Based on Innovative Automation, Industry Expertise, En...
Asset intelligence | Bridging the gap between corporate strategy and operatio...

Asset intelligence | Bridging the gap between corporate strategy and operatio...
PACE-IT, Security+2.7: Physical Security and Enviornmental Controls

PACE-IT, Security+2.7: Physical Security and Enviornmental Controls
Health apps regulation and quality control case studies and session 2 present...

Health apps regulation and quality control case studies and session 2 present...
Health apps regulation and quality control case studies and session 2 present...

Health apps regulation and quality control case studies and session 2 present...
Tips for IT Risk Management Prof. Hernan Huwyler Information Security Institute

Tips for IT Risk Management Prof. Hernan Huwyler Information Security Institute
Business Objectives & Control Objectives in Information Technology

Business Objectives & Control Objectives in Information Technology
OPAL-RT Smart transmission grid applications for real-time monitoring

OPAL-RT Smart transmission grid applications for real-time monitoring
Recently uploaded
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Controls in information system
- 3. Sensitive information Strategic plan – m & a pending, crucial decisions, major expension Business operation – client lists, process and procedures (proprietary) Finances - cost sheet, ratios(GP, NP), salaries wages, precise salary information, loans, dividends
- 4. Need for control in IS Increase the ability to capture, store, analyze and process data Safeguard assets to maintain data integrity Covering access safeguards over computer programs, data and any related equipment System effectiveness and efficiency Control built in well designed system
- 5. Impact of tech. on IC
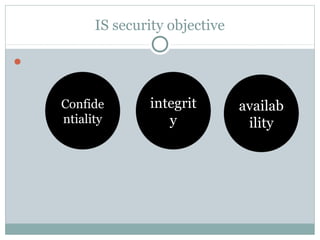
- 6. Categories of control 1. PREVENTIVE 1. ADMIN 1. PHYSICAL 1. MGMT. 2. DETECTIVE 2. OPERATION 2. LOGICAL 2. APP. 3. CORRECTIVE 3. ACCOUNTS 3. ENVIORNMENTAL 4. COMPENSATORY OBJECTIVE FUNCTION AUDIT FUNCTION IS RESOURCES
- 7. FUNCTION Admin – lawful, compliance of mgmt and other statutory requirements Operation – effectiveness, efficiency, objective achieve, day to day business Accounts – balance sheet, true & fair view, reliability of financial control
- 8. OBJECTIVE Preventive – designed to prevent and control error and any malicious activity anti virus, passwords, firewall, smart cards, skilled personnel, segregation of duties, Detective – designed to detect errors or malicious activity cctv, log, anti virus, audit, reconciliation Corrective – designed to reduce the impact of error or malicious activity anti virus, back up, insurance, fire extinguisher, recovery plan Compensatory - reduce the probability of threats, many devices are used in, cost of the lock should not be more than assets, organization may not be able to implement control in that cast compensatory control are used to such appropriateness OTP, Buying something from reliance industries,
- 9. IS RESOURCES
- 10. Environmental Issues Primarily due to elements of nature Natural resources, AC failure, electrical shock
- 11. Issues and revelations Power supply to compiler equipment remains in specifications AC system properly working Back up media protected from damage, magnet effect etc. Equipment kept free from dust and smoke Food, beverage and tobaco product are prohibited
- 12. controls Water/smoke detectors Hand held fire extinguisher Fire suppression system a) Dry pipe b) water based c) halogen • Regular inspection • Electrical surge protectors • Two substations • Emergency power off switches • wires in conduit and panels • Documented and tested emergency evacuation plans
Editor's Notes
- 3.8
- 3.12
- 3.14
- 3.16
