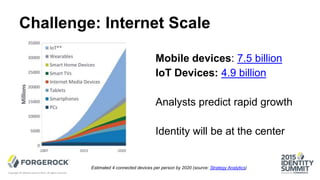
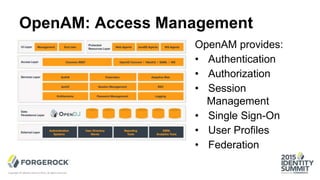
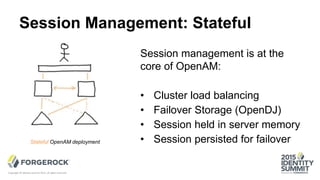
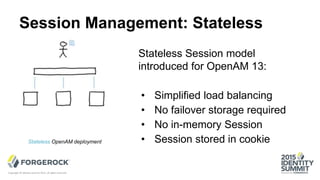
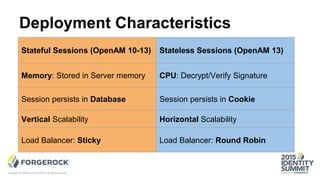
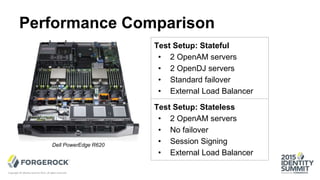
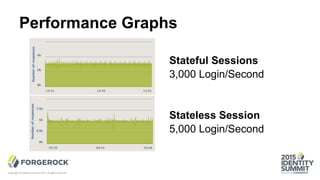
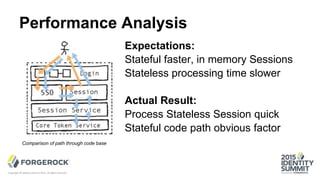
The document discusses the challenges of internet-scale session management, focusing on the transition from stateful to stateless sessions in OpenAM. It highlights the benefits of stateless sessions, such as simplified load balancing and reduced complexity in failover recovery, while also noting scenarios where stateful sessions may still be necessary. Performance comparisons indicate that stateless sessions can handle more logins per second than stateful sessions, demonstrating the advantages of this approach in modern, elastic deployments.