Your Mission: Identify & Eliminate Cyber Attacks
•
0 likes•303 views
The document discusses the need for organizations to have real-time, actionable intelligence to prevent cyber attacks and security breaches. Without adequate threat intelligence, a business can suffer losses from financial data and customer data theft, compliance penalties, lost revenue and customer confidence. The document cites statistics showing that the majority of organizations have outdated tools for threat detection and are often unaware of attacks until notified by external parties. It promotes the benefits of advanced security analytics and machine learning for rapidly detecting, analyzing and responding to threats.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...

SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...
Embracing Threat Intelligence and Finding ROI in Your Decision

Embracing Threat Intelligence and Finding ROI in Your Decision
Cylance Information Security: Compromise Assessment Datasheet

Cylance Information Security: Compromise Assessment Datasheet
Vulnerability Assessment and Penetration Testing Framework by Falgun Rathod

Vulnerability Assessment and Penetration Testing Framework by Falgun Rathod
Cyber Security Testing - Protect Your Business From Cyber Threats

Cyber Security Testing - Protect Your Business From Cyber Threats
Adapted from an ESG report - Seeing Is Securing - Protecting Against Advanced...

Adapted from an ESG report - Seeing Is Securing - Protecting Against Advanced...
Penetration Testing, Auditing & Standards Issue : 02_2012-1

Penetration Testing, Auditing & Standards Issue : 02_2012-1
The real cost of a cheap security operations center

The real cost of a cheap security operations center
Executive Summary of the 2016 Scalar Security Study

Executive Summary of the 2016 Scalar Security Study
Viewers also liked
Viewers also liked (14)
Similar to Your Mission: Identify & Eliminate Cyber Attacks
Incident Response Management: How European Enterprises are Planning to Prepare for a Cyber Security BreachBreaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...Hewlett Packard Enterprise Business Value Exchange
Similar to Your Mission: Identify & Eliminate Cyber Attacks (20)
Netwealth educational webinar: Peace of mind in a digital world

Netwealth educational webinar: Peace of mind in a digital world
Security Whack-a-Mole: SANS 2017 Threat Landscape Survey

Security Whack-a-Mole: SANS 2017 Threat Landscape Survey
Strategies of Identity Access Management - Bahaa Abdul Hadi.pdf

Strategies of Identity Access Management - Bahaa Abdul Hadi.pdf
Security Analytics and Big Data: What You Need to Know

Security Analytics and Big Data: What You Need to Know
How Federal Agencies Can Build a Layered Defense for Privileged Accounts

How Federal Agencies Can Build a Layered Defense for Privileged Accounts
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...
Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...

Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...
More from Enterprise Management Associates
Discover the latest insights and trends shaping the landscape of workload automation and orchestration, featuring highlights from the latest "EMA Radar™ Report for Workload Automation and Orchestration."
You will learn more about:
- Workflow Orchestration - Uncover the evolving role of orchestration in simplifying complex workflows in the era of digital transformation.
- Data Pipeline Orchestration – Learn more about WLA support for DataOps, including the integration of Apache Airflow.
- Mainframe Modernization - Gain a deeper understanding of how organizations are embracing modernization while still leveraging their mainframe investments.
- DevOps Support and Collaboration - Explore the pivotal role of workload automation in DevOps practices.
Highlights from the EMA Radar™ Report for Workload Automation and Orchestrati...

Highlights from the EMA Radar™ Report for Workload Automation and Orchestrati...Enterprise Management Associates
These slides from Enterprise Management Associates (EMA) present a wealth of research data from EMA’s recent study of real-world adoption patterns, challenges, trends, and enterprise-priorities related to infrastructure and application observability. Observability: Challenges, Priorities, Solutions, and the Role of OpenTelemetry

Observability: Challenges, Priorities, Solutions, and the Role of OpenTelemetryEnterprise Management Associates
According to new EMA research, 84% of enterprises are seeing increased collaboration between their network and security teams. This NetSecOps convergence allows these teams to support new technologies, such as hybrid, multi-cloud architecture, and secure access service edge (SASE).
These slides from EMA Vice President of Research, Shamus McGillicuddy, provide highlights from his market research report, “NetSecOps: Examining How Network and Security Teams Collaborate for a Better Digital Future.”
Check out these slides to discover:
- What causes network and security team collaborations to fail
- How network data, especially packets and DNS logs, play a critical role in partnerships between
- Why network automation and network monitoring tools are critical to collaboration
- How SASE and multi-cloud are impacting collaboration
NetSecOps: Examining How Network and Security Teams Collaborate for a Better ...

NetSecOps: Examining How Network and Security Teams Collaborate for a Better ...Enterprise Management Associates
Based on the IT Executive Survey 2023 fielded by leading IT analyst research firm EMA and global analytics software firm FICO, these slides explore key trends and opportunities shaping the technology landscape in the global banking, finance, and insurance industries. It will also examine how technology executives are aligning with their business counterparts to drive strategic outcomes.
You will also learn more about:
- Top technology-related priorities for banks and insurers, along with strategies to address significant challenges.
- Changing technology buying behavior and considerations for selecting new technology solutions.
- Strategies for maximizing the value of data and AI investments within enterprises.
- The benefits of a unified platform approach and its impact on other initiatives, such as cloud adoption and legacy modernization.
Unveiling Strategic Trends in Global Finance, Banking, and Insurance - IT Ex...

Unveiling Strategic Trends in Global Finance, Banking, and Insurance - IT Ex...Enterprise Management Associates
In a landscape where data is king, master data management (MDM) plays a pivotal role in ensuring data quality and consistency across organizations. Enterprise Management Associates (EMA) research shows that 96% of enterprises have one or more MDM tools or are planning to add one in the next 24 months. Achieving a successful MDM implementation, however, proves challenging for many, with 30% of organizations failing on their first attempt to deploy an MDM. Implementation teams struggle with data quality, data mapping and transformation, integration complexity, and many other challenges. What is the secret to a successful MDM implementation?
Check out these slides from EMA and Semarchy to find out!Unlocking Master Data Management (MDM) Success: Real-World Insights and Strat...

Unlocking Master Data Management (MDM) Success: Real-World Insights and Strat...Enterprise Management Associates
These research slides provide insights into the critical issues involved in handling application- and infrastructure-complexity in ever-changing hybrid multi-cloud settings. Torsten Volk, Managing Research Director at EMA, and Jasper Paul, a Principal Product Manager at ManageEngine Site24x7, explore:
The Anatomy of Complexity: Understand and escape the complexity trap of distributed cloud native applications.
Monitoring and Metrics: Examine approaches for effective monitoring of resource utilization and performance as key components of complexity management.
AIOps: Examine the capabilities of AIOps.
FinOps Strategies: Explore frameworks and best practices for efficiently managing your cloud's financial operations without compromising on performance, resilience, or security.
Case Studies: Gain insights from real-world instances where companies have successfully mitigated the complexities and risks associated with distributed microservices architectures.
Navigating the Complexity of Distributed Microservices across AWS, Azure, and...

Navigating the Complexity of Distributed Microservices across AWS, Azure, and...Enterprise Management Associates
Enterprise Management Associates (EMA) has published the most comprehensive market research study on DDI solutions in over a decade, “DDI Directions: DNS, DHCP and IP Address Management Strategies for the Multi-Cloud Era.” Based on a survey of 333 enterprise DDI experts, this research found that less than 40% of enterprises are fully successful in their approach to DDI technology.
These slides created by Shamus McGillicuddy, EMA vice president of research, provide insights into the following:
- Why only 31% of enterprise are confident in the security of their DNS infrastructure
- How DDI enables network automation
- How cloud migration disrupts DDI strategy and what you can do about it
- What to look for in an ideal DDI product
DDI Directions: DNS, DHCP and IP Address Management Strategies for the Multi-...

DDI Directions: DNS, DHCP and IP Address Management Strategies for the Multi-...Enterprise Management Associates
By the end of 2023, 83% of enterprises expect to connect operational technology (OT) and IoT devices to their enterprise networks, according to Enterprise Management Associates (EMA) research. IT and OT are converging so that enterprises can analyze OT data, innovate, and optimize industrial systems. A new approach to OT security is required.
Enterprises need to modernize network architecture to protect these critical assets, especially by updating their network security and modernizing their approach to network segmentation.
These slides explore how enterprises can use OT-dedicated firewalls and zero trust network access to protect OT systems from malicious actors.
Challenges and Best Practices for Securing Modern Operational Technology Netw...

Challenges and Best Practices for Securing Modern Operational Technology Netw...Enterprise Management Associates
For all its benefits, remote work puts tremendous pressure on network infrastructure and operations teams, who must maximize network experience while maintaining security. Enterprise Management Associates (EMA) explores this issue in depth with its market research report, “Modernizing Network Engineering and Operations in the Era of Hybrid and Remote Work,” based on a survey of 354 IT professionals.
Get insights when you check out these research slides. Modernizing Network Engineering and Operations in the Era of Hybrid and Remot...

Modernizing Network Engineering and Operations in the Era of Hybrid and Remot...Enterprise Management Associates
As security leaders evaluate the vast array of tools available to combat ransomware attacks, endpoint and extended detection and response solutions still stand out as the best defense against emerging threats. How can an enterprise know which of these tools is the best though?
Enterprise Management Associates (EMA) surveyed IT professionals, information security practitioners, and technology business leaders across all verticals to discover their attitudes and perspectives toward XDR solutions. The primary goal was to use survey responses and third-party interviews to create a comprehensive definition of “What is XDR?” for leaders to use as part of their solution evaluation process.
Check out these research slides featuring Christopher Steffen, CISSP, CISA, and vice president of research at EMA, to discover the definition and get results from this research.
Why Should Organizations Consider Extended Detection and Response (XDR)?

Why Should Organizations Consider Extended Detection and Response (XDR)?Enterprise Management Associates
With users working remotely and data now housed in multiple cloud applications, securing access to data is essential to a modern digital infrastructure. The rise of hybrid work has challenged the scalability of traditional VPNs, and hybrid multi-cloud architectures have made legacy centralized VPN concentrators impractical.
Zero trust network access (ZTNA) is an emerging class of technology that addresses these new remote access requirements and challenges.
Check out these slides to discover why it’s time to transition from legacy VPNs to ZTNA solutions. You will also learn more about:
- Why legacy VPN technologies cannot address the needs of modern enterprises
- How ZTNA helps secure remote access in the era of hybrid work and multi-cloud architectures
- The best way to transition to a next-generation solution
Moving Beyond Remote Access: Discover the Power of Zero Trust Network Access

Moving Beyond Remote Access: Discover the Power of Zero Trust Network AccessEnterprise Management Associates
Enterprises have been trying to automate their networks for decades, but manual tasks continue to dominate operations. According to Enterprise Management Associates (EMA) research, only 34% of IT organizations have been able to automate more than half of their network provisioning and change management tasks. With so many commercial and open source network automation tools available, why aren’t organizations doing better?
These slides—based on the webinar featuring Shamus McGillicuddy (EMA Vice President of Research) and Jason Edelman (Founder and CTO of network automation solution provider Network to Code) —provide guidance on how to set a network automation strategy. You will also get insights on:
- Whether a network team should use open source, homegrown, or commercial network automation solutions
- How to establish a data-driven source of truth for your network
- How to build the right team for enabling your network automation strategy
[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...![[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...Enterprise Management Associates
More from Enterprise Management Associates (20)
Highlights from the EMA Radar™ Report for Workload Automation and Orchestrati...

Highlights from the EMA Radar™ Report for Workload Automation and Orchestrati...
Real-world incident response, management, and prevention

Real-world incident response, management, and prevention
Observability: Challenges, Priorities, Solutions, and the Role of OpenTelemetry

Observability: Challenges, Priorities, Solutions, and the Role of OpenTelemetry
NetSecOps: Examining How Network and Security Teams Collaborate for a Better ...

NetSecOps: Examining How Network and Security Teams Collaborate for a Better ...
Modern ITSM—the untapped game-changer for midsize organizations

Modern ITSM—the untapped game-changer for midsize organizations
Unveiling Strategic Trends in Global Finance, Banking, and Insurance - IT Ex...

Unveiling Strategic Trends in Global Finance, Banking, and Insurance - IT Ex...
Unlocking Master Data Management (MDM) Success: Real-World Insights and Strat...

Unlocking Master Data Management (MDM) Success: Real-World Insights and Strat...
Transcending Passwords: Emerging Trends in Authentication

Transcending Passwords: Emerging Trends in Authentication
Modernize NetOps with Business-Aware Network Monitoring

Modernize NetOps with Business-Aware Network Monitoring
Navigating the Complexity of Distributed Microservices across AWS, Azure, and...

Navigating the Complexity of Distributed Microservices across AWS, Azure, and...
Navigating Today’s Threat Landscape: Discussing Hype vs. Reality

Navigating Today’s Threat Landscape: Discussing Hype vs. Reality
Kubernetes Unveiled: Trends, Challenges, and Opportunities

Kubernetes Unveiled: Trends, Challenges, and Opportunities
DDI Directions: DNS, DHCP and IP Address Management Strategies for the Multi-...

DDI Directions: DNS, DHCP and IP Address Management Strategies for the Multi-...
Challenges and Best Practices for Securing Modern Operational Technology Netw...

Challenges and Best Practices for Securing Modern Operational Technology Netw...
Modernizing Network Engineering and Operations in the Era of Hybrid and Remot...

Modernizing Network Engineering and Operations in the Era of Hybrid and Remot...
Why Should Organizations Consider Extended Detection and Response (XDR)?

Why Should Organizations Consider Extended Detection and Response (XDR)?
Moving Beyond Remote Access: Discover the Power of Zero Trust Network Access

Moving Beyond Remote Access: Discover the Power of Zero Trust Network Access
[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...![[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Analyst Research Slides] Build vs. Buy: Finding the Best Path to Network Aut...
Recently uploaded
Recently uploaded (20)
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
WSO2 Micro Integrator for Enterprise Integration in a Decentralized, Microser...

WSO2 Micro Integrator for Enterprise Integration in a Decentralized, Microser...
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
WSO2's API Vision: Unifying Control, Empowering Developers

WSO2's API Vision: Unifying Control, Empowering Developers
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
API Governance and Monetization - The evolution of API governance

API Governance and Monetization - The evolution of API governance
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
Your Mission: Identify & Eliminate Cyber Attacks
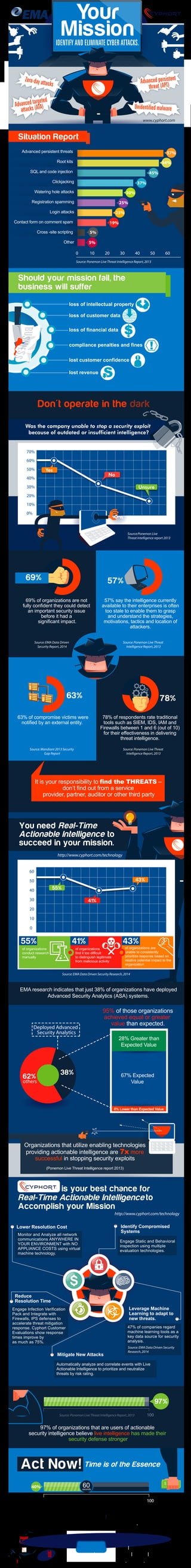
- 1. loss of intellectual property loss of financial data compliance penalties and fines lost customer confidence lost revenue loss of customer data 70% 60% 50% 40% 30% 20% 10% 0% Your MissionIDENTIFY AND ELIMINATE CYBER ATTACKS. Should your mission fail, the business will suffer Zero-day attacks Advanced targeted attacks (ATA) Unidentified malware Advanced persistent threat (APT) It is your responsibility to find the THREATS – don’t find out from a service provider, partner, auditor or other third party 0 10 20 30 40 50 60 57% 54% 45% 37% 30% 25% 23% 19% 5% 5% Advanced persistent threats Root kits SQL and code injection Clickjacking Watering hole attacks Registration spamming Login attacks Contact form on comment spam Cross -site scripting Other Situation Report Source:Ponemon Live Threat Intelligence Report,2013 Source:Ponemon Live Threat Intelligence report 2013 78% of respondents rate traditional tools such as SIEM, IDS, IAM and Firewalls between 1 and 6 (out of 10) for their effectiveness in delivering threat intelligence. 78% 57% say the intelligence currently available to their enterprises is often too stale to enable them to grasp and understand the strategies, motivations, tactics and location of attackers. 57% 69% of organizations are not fully confident they could detect an important security issue before it had a significant impact. 69% Don't operate in the dark 63% of compromise victims were notified by an external entity. 63% You need Real-Time Actionable Intelligence to succeed in your mission. EMA research indicates that just 38% of organizations have deployed Advanced Security Analytics (ASA) systems. of organizations conduct research manually of organizations find it too difficult to distinguish legitimate from malicious activity of organizations are unable to consistently prioritize response based on relative potential impact to the organization 55% 41% 41% 55% 43% 43% 0 10 20 30 40 50 60 Organizations that utilize enabling technologies providing actionable intelligence are 7x more successful in stopping security exploits (Ponemon Live Threat Intelligence report 2013) Lower Resolution Cost Leverage Machine Learning to adapt to new threats. Mitigate New Attacks 97% of organizations that are users of actionable security intelligence believe live intelligence has made their security defense stronger 100Source:Ponemon Live Threat Intelligence Report,2013 Action within 60 seconds of an incident can reduce the resolution cost of a breach by an average of 40%. 100 40% Source:Ponemon Live Threat Intelligence Report,2013 60seconds $ Engage Infection Verification Pack and Integrate with Firewalls, IPS defenses to accelerate threat mitigation response. Cyphort Customer Evaluations show response times improve by as much as 75%. 47% of companies regard machine learning tools as a key data source for security analysis. Engage Static and Behavioral inspection using multiple evaluation technologies. Monitor and Analyze all network communications ANYWHERE IN YOUR ENVIRONMENT with NO APPLIANCE COSTS using virtual machine technology. Automatically analyze and correlate events with Live Actionable Intelligence to prioritize and neutralize threats by risk rating. Reduce Resolution Time www.cyphort.com Was the company unable to stop a security exploit because of outdated or insufficient intelligence? Yes No Unsure Source:EMA Data Driven Security Report,2014 Source:Mandiant 2013 Security Gap Report Source:Ponemon Live Threat Intelligence Report,2013 http://www.cyphort.com/technology http://www.cyphort.com/technology is your best chance for to Accomplish your Mission Source:EMA Data Driven Security Research,2014 97% Time is of the EssenceAct Now! Real-Time Actionable Intelligence Real-Time Actionable Intelligence Source:EMA Data Driven Security Research,2014 Contact to get a glimpse of our detection technology with free online malware scanning service at http://www.cyphort.com/infographic 38% 62% others 28% Greater than Expected Value 67% Expected Value 95% of those organizations achieved equal or greater value than expected. Deployed Advanced Security Analytics 6% Lower than Expected Value Identify Compromised Systems Source:Ponemon Live Threat Intelligence Report,2013
