A4 Cybersecurity Awareness Posters Part 9
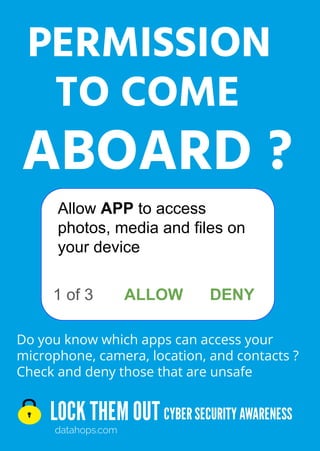
- 1. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS Do you know which apps can access your microphone, camera, location, and contacts ? Check and deny those that are unsafe PERMISSION ABOARD ? TO COME 1 of 3 Allow APP to access photos, media and files on your device ALLOW DENY
- 2. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS DO YOU WANT TO SWAP? Set a PIN code for your SIM card to protect it in case of theft and prevent an attacker from Taking over your phone number and stealing your information
- 3. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS WHO’S WATCHING WHO ? An attacker can access your security camera and spy on you. To protect yourself. 1. Set a strong password for your router 2. Set up multi factor authentication 3. Keep your cameras firmware updated
- 4. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS Check your privacy settings to control who can see and access your profile, the way your data is used, collected and shared WHO WANTS TO KNOW? P R I VA T E
- 5. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS HOW SMART! An attacker can access your Smart TV through your home network. Protect Yourself 1. Set a strong password for your router 2. Install updates if prompted 3. Adjust privacy settings
- 6. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS JUST LIKE HADRIAN’S WALL Enable a firewall to prevent unauthorized access to your network and block unwanted connections to the internet and attempts to install malware
- 7. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS TIME FOR A CHECK UP Review your security settings on all accounts periodically. Set up multifactor authentication. You can see which actions need urgent attention
- 8. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS FEEL LIKE YOU'RE BEEN FOLLOWED? Use a privacy browser to stop websites collecting data about you, your devices, and what you do online
- 9. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS SINK OR SWIM ? Avoid that sinking feeling. Do a regular backup of files in case of an unexpected occurrence. This can help you restore your files quickly and easily.
- 10. LOCK THEM OUT datahops.com CYBER SECURITY AWARENESS IS PRICELESS PEACE OF MIND Turn on encryption to protect your files if your device gets lost or stolen. It cannot be accessed by anyone without the password or recovery key