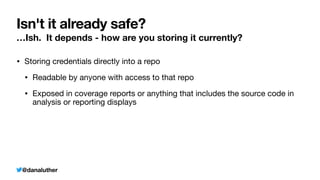
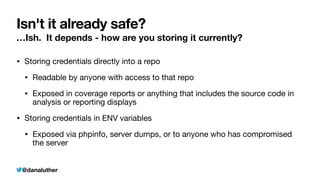
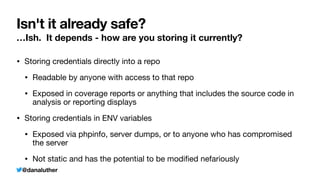
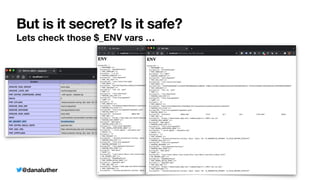
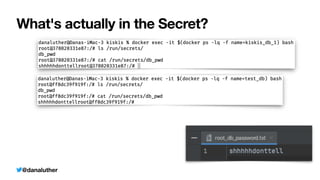
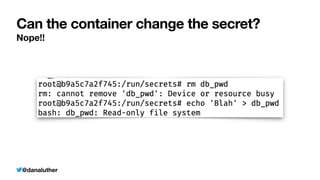
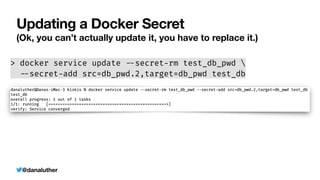
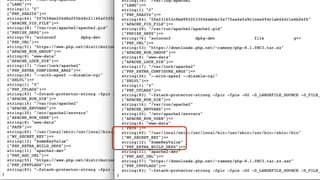
The document discusses various methods for managing sensitive credentials in application development, specifically focusing on Docker secrets, dependency injection, and best practices for securing APIs. It emphasizes the importance of protecting file-based, variable, and API credential strings, demonstrating code examples for improved security. Furthermore, it outlines Docker's capabilities in creating secure environments for sensitive information, while also cautioning against common pitfalls in credential management.


















![@danaluther
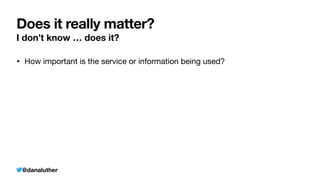
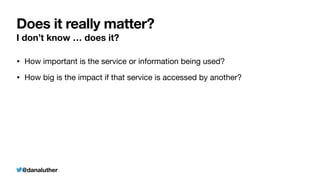
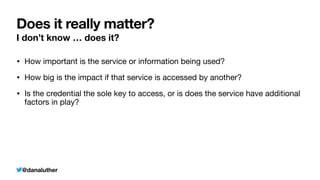
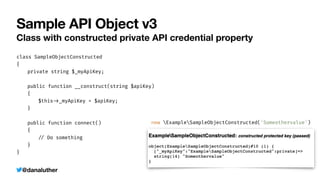
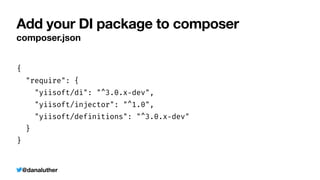
Sample API Object v3 with $_ENV
Class with constructed private API credential property
class SampleObjectConstructed
{
private string $_myApiKey;
public function __construct(string $apiKey)
{
$this
-
>
_myApiKey = $apiKey;
}
public function connect()
{
/
/
Do something
}
}
new ExampleSampleObjectConstructed($_ENV['MY_SECRET_KEY'])](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-29-320.jpg)
![@danaluther
Sample API Object v3 with $_ENV
Class with constructed private API credential property
class SampleObjectConstructed
{
private string $_myApiKey;
public function __construct(string $apiKey)
{
$this
-
>
_myApiKey = $apiKey;
}
public function connect()
{
/
/
Do something
}
}
new ExampleSampleObjectConstructed($_ENV['MY_SECRET_KEY'])](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-30-320.jpg)


![@danaluther
Sample API Object v3 with $_ENV via DI
Constructor moved to DI Container
require 'vendor/autoload.php';
use YiisoftDiContainer;
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[$_ENV['MY_SECRET_KEY']]
],
]);](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-38-320.jpg)
![@danaluther
Sample API Object v3 with $_ENV via DI
Constructor moved to DI Container
require 'vendor/autoload.php';
use YiisoftDiContainer;
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[$_ENV['MY_SECRET_KEY']]
],
]);](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-39-320.jpg)
![@danaluther
Sample API Object v3 with $_ENV via DI
Constructor moved to DI Container
require 'vendor/autoload.php';
use YiisoftDiContainer;
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[$_ENV['MY_SECRET_KEY']]
],
]); $container
-
>
get(ExampleSampleObjectConstructed
:
:
class)](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-40-320.jpg)








![@danaluther
version: “3.7"
services:
php:
image: php:7.4-apache
ports:
- 8080
:
80
volumes:
- ./src:/var/
w
w
w
/html
command:[
‘bash’, ‘
-
c’,
‘docker
-
php
-
ext
-
install
-
j$$(nproc) mysqli pdo_mysql
&
&
apache2-foreground’
]
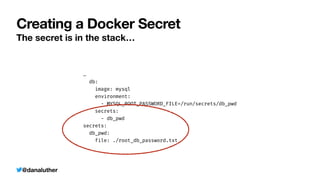
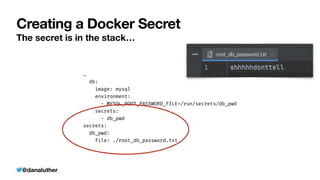
db:
image: mysql
environment:
- MYSQL_ROOT_PASSWORD_FILE=/run/secrets/db_pwd
secrets:
- db_pwd
secrets:
db_pwd:
file: ./root_db_password.txt](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-53-320.jpg)
![@danaluther
version: “3.7"
services:
php:
image: php:8.0-apache
ports:
- 8080
:
80
volumes:
- ./src:/var/
w
w
w
/html
command:[
‘bash’, ‘
-
c’,
‘docker
-
php
-
ext
-
install
-
j$$(nproc) mysqli pdo_mysql
&
&
apache2-foreground’
]
db:
image: mysql
environment:
- MYSQL_ROOT_PASSWORD_FILE=/run/secrets/db_pwd
secrets:
- db_pwd
secrets:
db_pwd:
file: ./root_db_password.txt](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-54-320.jpg)
![@danaluther
version: “3.7"
services:
php:
image: php:8.1-rc—apache
ports:
- 8080
:
80
volumes:
- ./src:/var/
w
w
w
/html
command:[
‘bash’, ‘
-
c’,
‘docker
-
php
-
ext
-
install
-
j$$(nproc) mysqli pdo_mysql
&
&
apache2-foreground’
]
db:
image: mysql
environment:
- MYSQL_ROOT_PASSWORD_FILE=/run/secrets/db_pwd
secrets:
- db_pwd
secrets:
db_pwd:
file: ./root_db_password.txt](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-55-320.jpg)







![@danaluther
Sample API Object v3 with $_ENV via DI
Constructor moved to DI Container
require 'vendor/autoload.php';
use YiisoftDiContainer;
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[$_ENV['MY_SECRET_KEY']]
],
]); $container
-
>
get(ExampleSampleObjectConstructed
:
:
class)](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-82-320.jpg)
![@danaluther
Sample API Object v3 with $_ENV via DI
Constructor moved to DI Container
require 'vendor/autoload.php';
use YiisoftDiContainer;
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[$_ENV['MY_SECRET_KEY']]
],
]); $container
-
>
get(ExampleSampleObjectConstructed
:
:
class)](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-83-320.jpg)

![@danaluther
Sample API Object v3 with secret via DI
Container populated from secret
require 'vendor/autoload.php';
use YiisoftDiContainer;
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[file_get_contents('/run/secrets/hiddenkey')]
],
]);](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-86-320.jpg)
![@danaluther
Sample API Object v3 with secret via DI
Container populated from secret
require 'vendor/autoload.php';
use YiisoftDiContainer;
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[file_get_contents('/run/secrets/hiddenkey')]
],
]); $container
-
>
get(ExampleSampleObjectConstructed
:
:
class)](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-87-320.jpg)
![@danaluther
Define multiple objects in the container
Multiple classes, multiple con
fi
gurations of one class
$container = new Container([
ExampleSampleObjectConstructed
:
:
class
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[file_get_contents('/run/secrets/hiddenkey')]
],
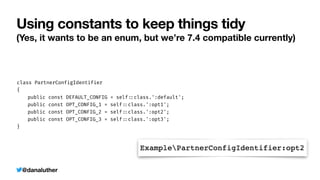
ExamplePartnerConfigIdentifier
:
:
OPT_CONFIG_1
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
[file_get_contents('/run/secrets/hiddenkey2')]
],
ExamplePartnerConfigIdentifier
:
:
OPT_CONFIG_2
=
>
[
'class'
=
>
ExampleSampleObjectConstructed
:
:
class,
'__construct()'
=
>
['You can read me in the source repo.']
],
]);](https://image.slidesharecdn.com/kiskisdockersecretsanddi-longhorn-211015205612/85/Keep-it-Secret-Keep-it-Safe-Docker-Secrets-and-DI-88-320.jpg)