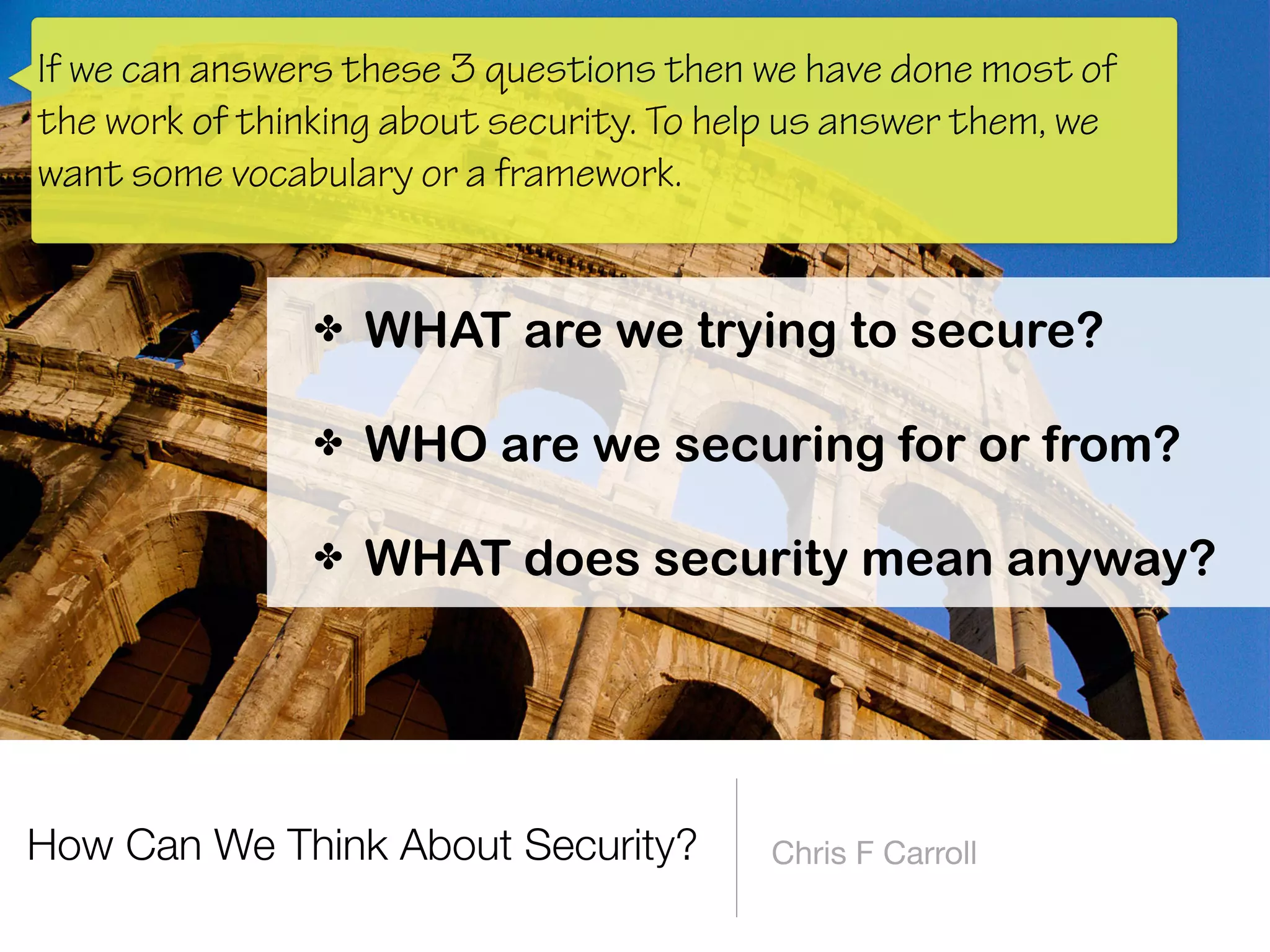
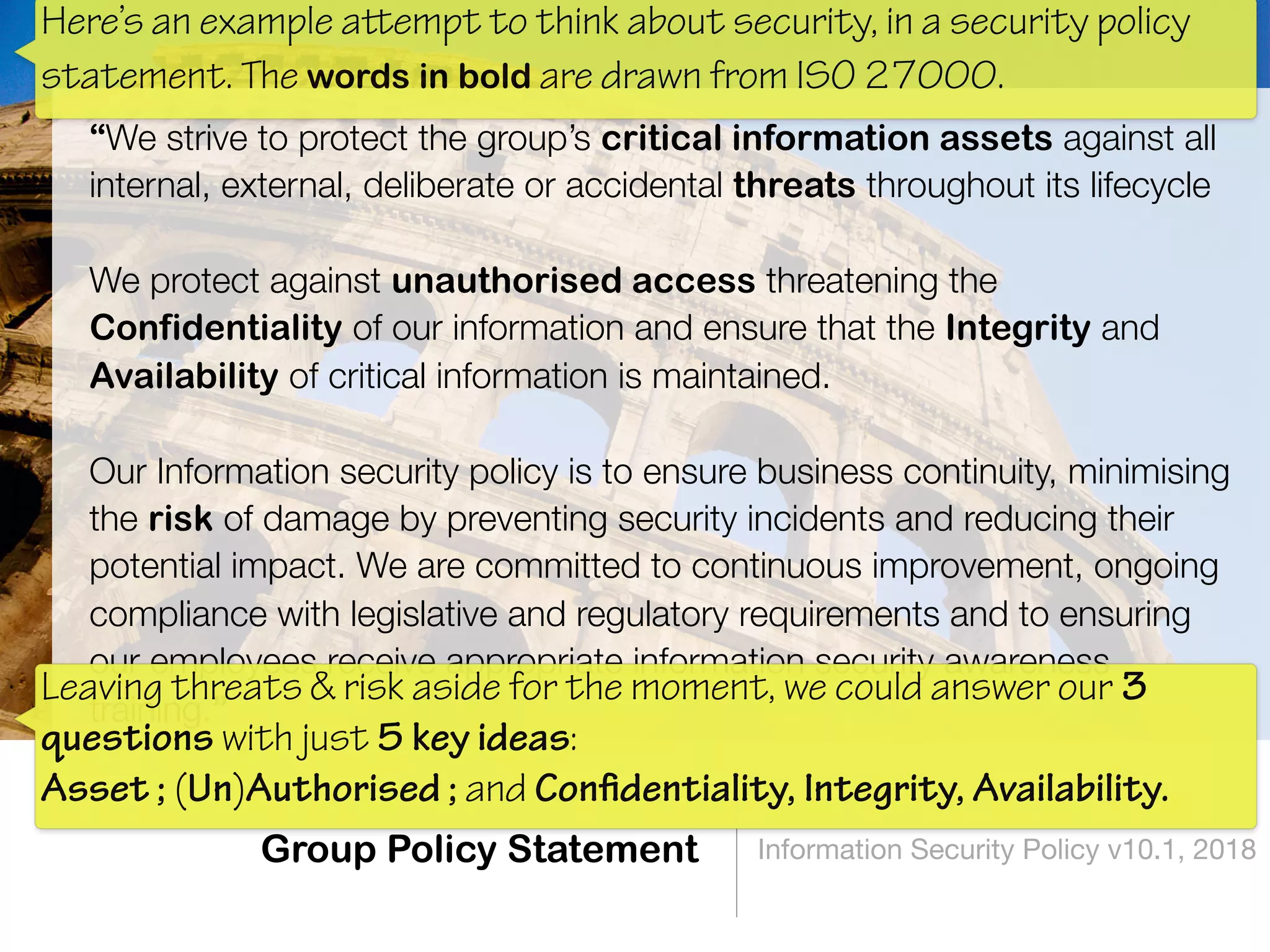
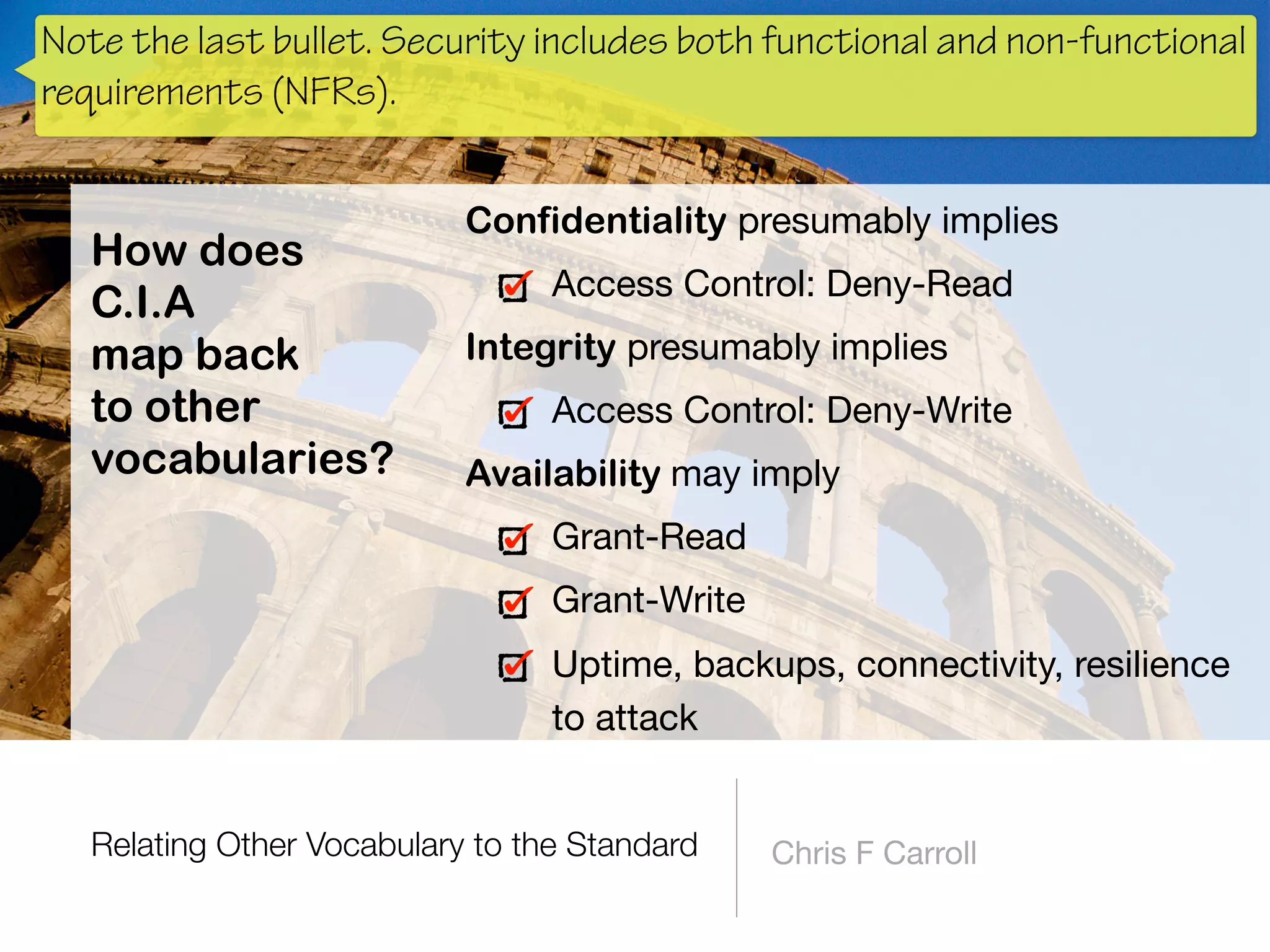
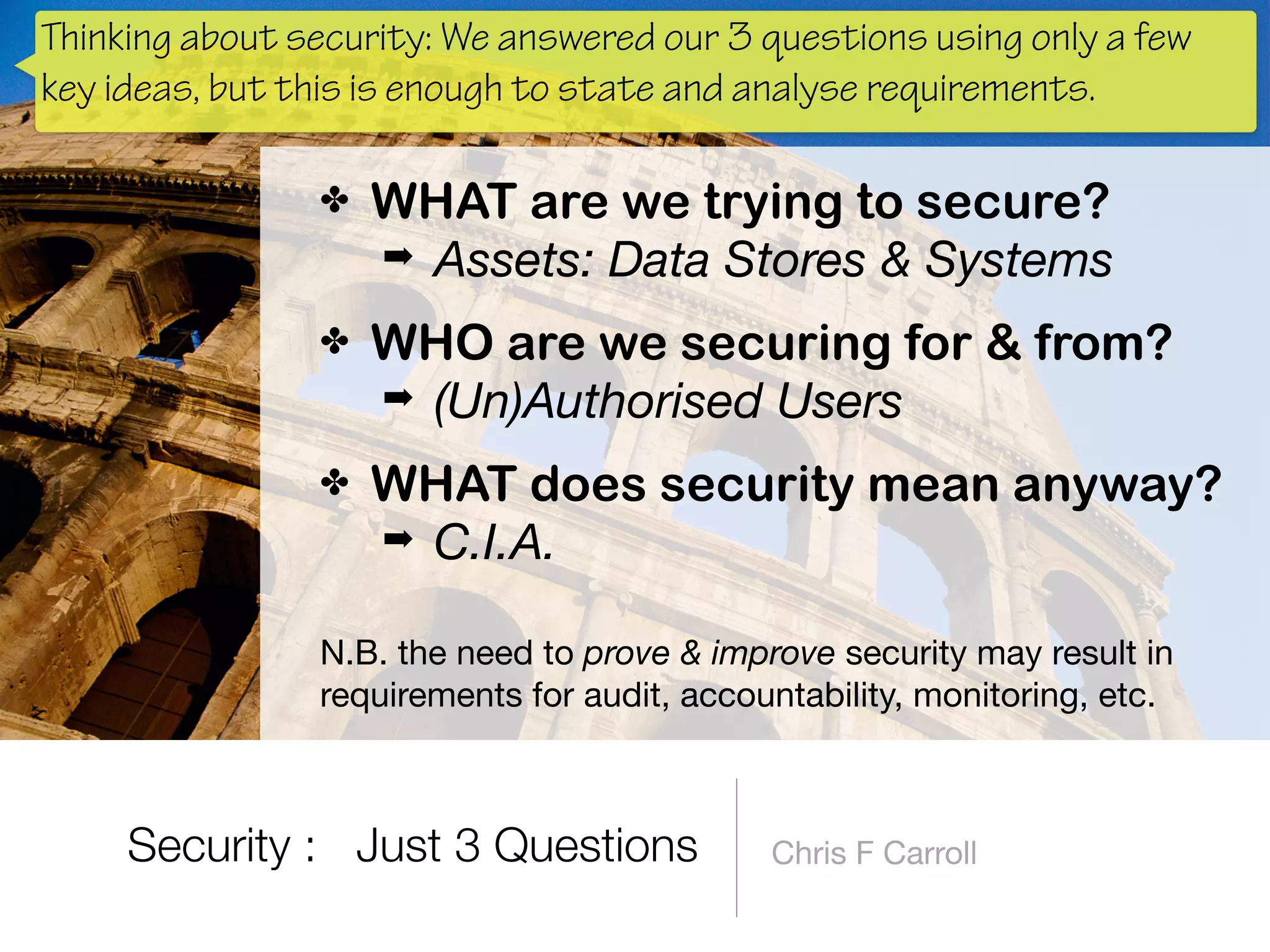
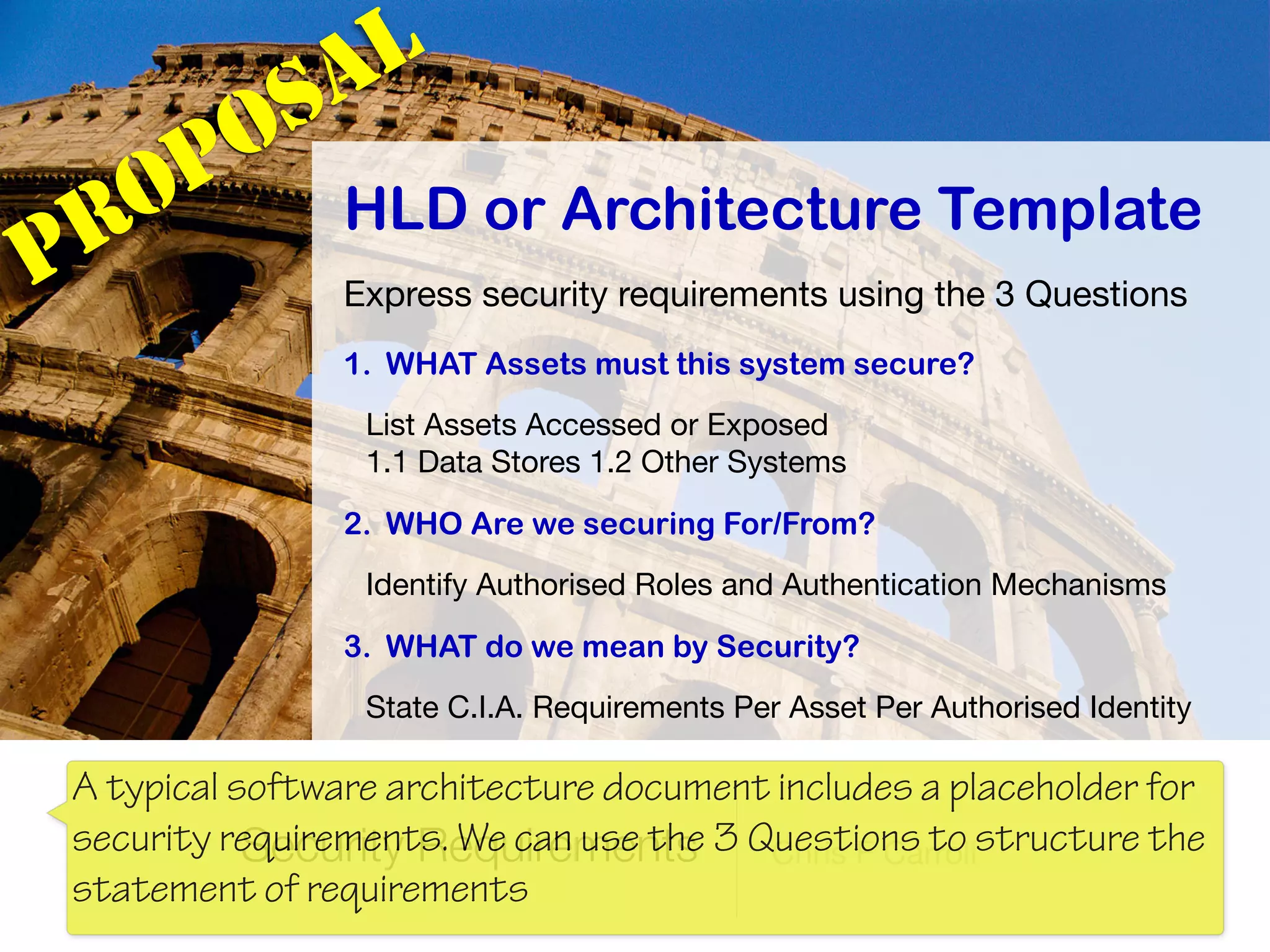
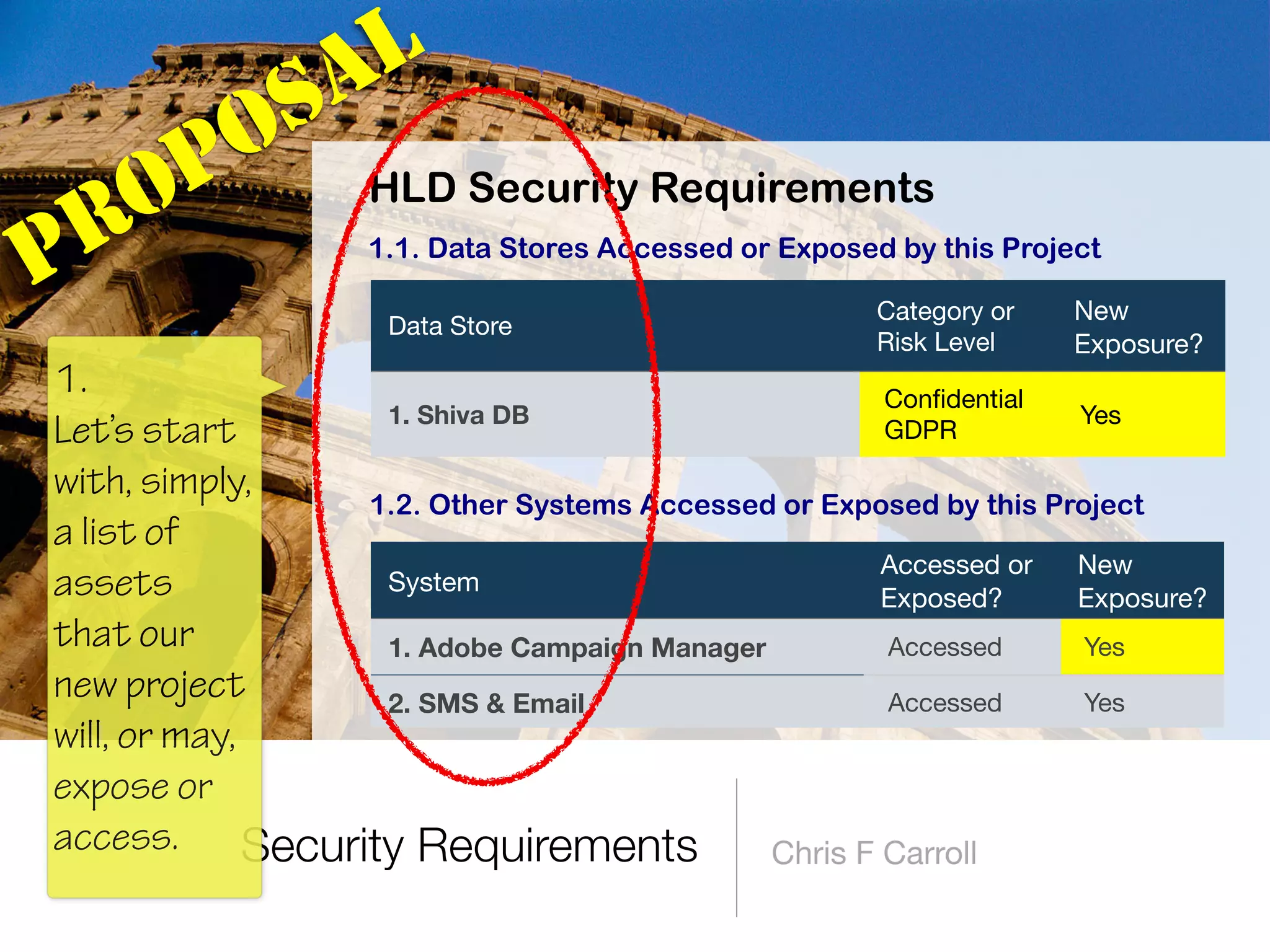
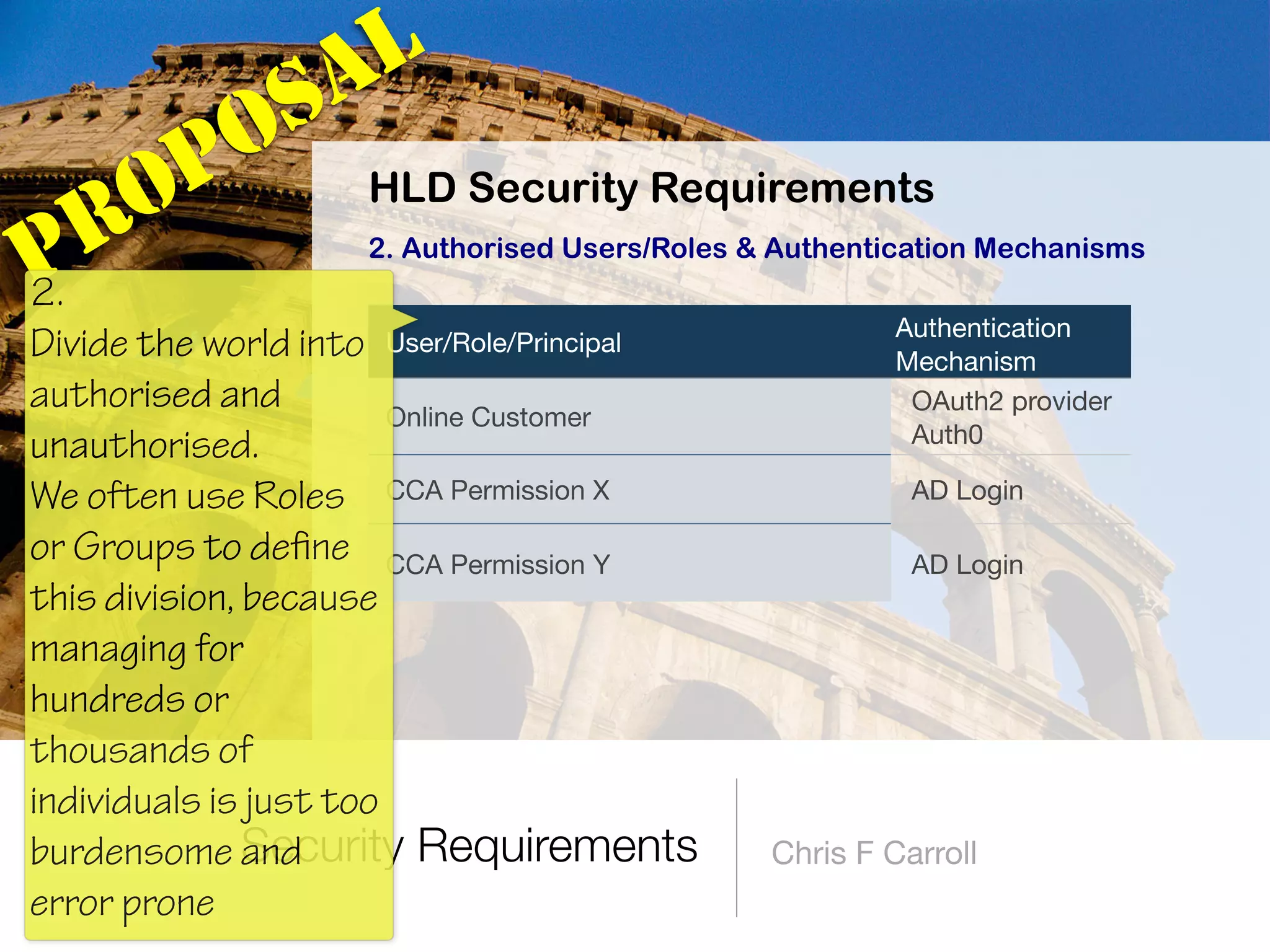
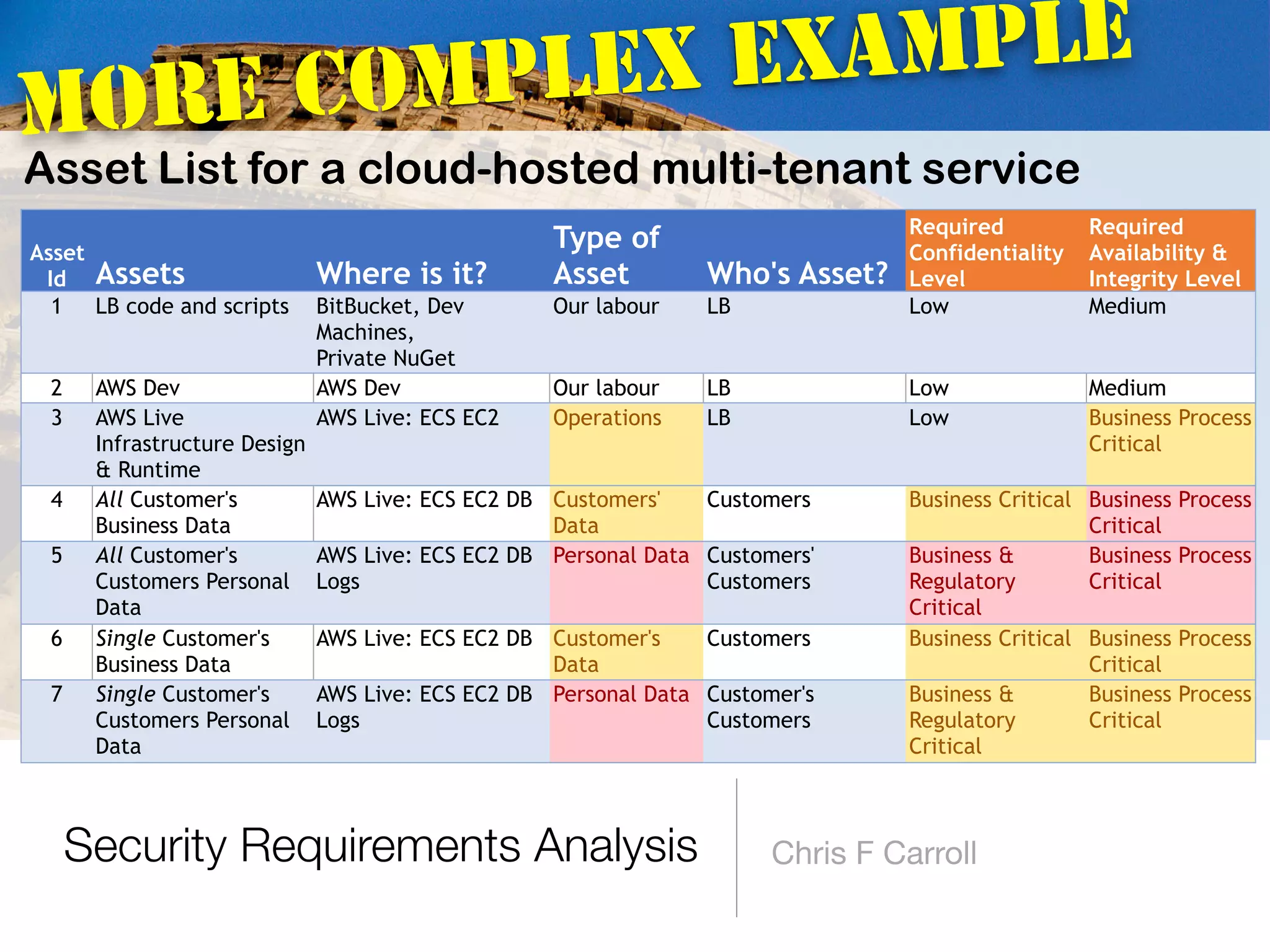
The document discusses the fundamentals of software architecture focusing on information security requirements, emphasizing the importance of understanding core security concepts such as assets, users, and the CIA triad (confidentiality, integrity, availability). It utilizes the ISO 27000 series to provide a vocabulary for establishing security requirements throughout the software development lifecycle. The presentation also outlines how to identify assets, roles, and necessary security measures in creating effective security policies.