Report on Human factor in the financial industry
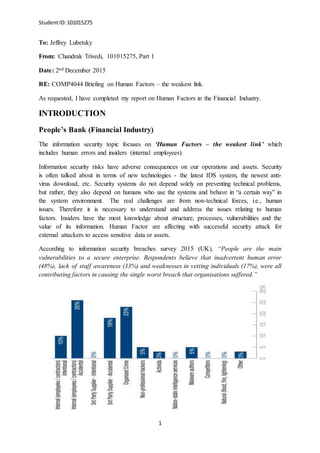
- 1. StudentID:101015275 1 To: Jeffrey Lubetsky From: Chandrak Trivedi, 101015275, Part 1 Date: 2nd December 2015 RE: COMP4044 Briefing on Human Factors – the weakest link. As requested, I have completed my report on Human Factors in the Financial Industry. INTRODUCTION People’s Bank (Financial Industry) The information security topic focuses on ‘Human Factors – the weakest link’ which includes human errors and insiders (internal employees). Information security risks have adverse consequences on our operations and assets. Security is often talked about in terms of new technologies - the latest IDS system, the newest anti- virus download, etc. Security systems do not depend solely on preventing technical problems, but rather, they also depend on humans who use the systems and behave in “a certain way” in the system environment. The real challenges are from non-technical forces, i.e., human issues. Therefore it is necessary to understand and address the issues relating to human factors. Insiders have the most knowledge about structure, processes, vulnerabilities and the value of its information. Human Factor are affecting with successful security attack for external attackers to access sensitive data or assets. According to information security breaches survey 2015 (UK), “People are the main vulnerabilities to a secure enterprise. Respondents believe that inadvertent human error (48%), lack of staff awareness (33%) and weaknesses in vetting individuals (17%), were all contributing factors in causing the single worst breach that organisations suffered.”
- 2. StudentID:101015275 2 IMPACT The greatest impacts of successful security breach attacks involving human factor to our bank will be business operations, reputational damage, revenue loss and exposure of cooperate sensitive data and personal customer data and the introduction of malware in the network. This successful security attacks exploit human interest factor, involves social engineering and spear-phishing scams with emails containing malicious attachments that can cause malware to be downloaded onto the user’s computing device. This gives attackers a foothold inside from which they can move laterally in search of valuable information, such as confidential data. Impact on technology by human factors will be introduction to malware or viruses in the network or DDoS attack blocking the website which will directly impact the business operations and can also add vulnerabilities in our network that will be unknown to bank’s security professionals and other external attacker to gain access to confidential data by using that vulnerabilities such as backdoor which will impact reputation of the bank. Impact on privacy by human factors will be access to personal customer information along with credit cards details, cooperate confidential data which can be used by attacker. Impact on people (users) by human factors will be change in transactions or entries with their accounts and also users can start receiving phishing emails from the attacker. RECOMMENDATION Procedural recommendation: Policies and processes must be acknowledged and enforced. Technology recommendation: The step in mitigating the risk of privileged (Apply the principle of least privilege) account exploitation is to identify all privileged accounts, credentials and immediately terminate those that are no longer in use or are connected to employees that are no longer at the company. Closely monitor, control and manage privileged credentials to prevent exploitation. Finally, implementing necessary protocols and infrastructure to track, log and record privileged account activity and create alerts, to allow for a quick response to malicious activity and mitigate potential damage early in the attack cycle. People recommendation: Improve awareness campaign, employees must be aware of the principal risks related to the use of most common platforms and devote more resources to the employee – to training, education, testing and to the culture of your organization.