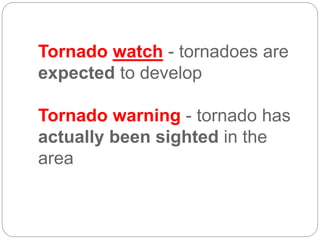
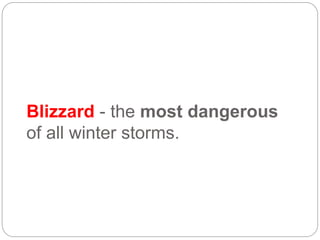
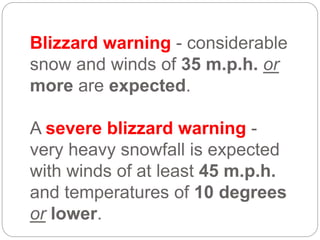
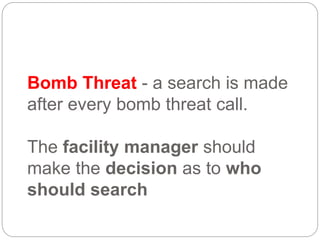
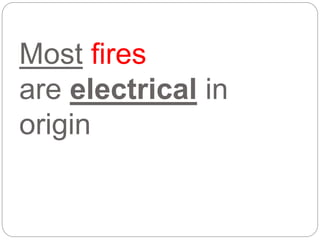
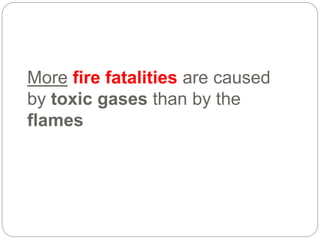
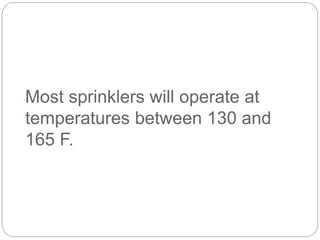
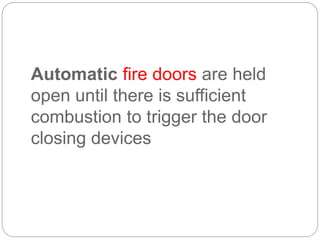
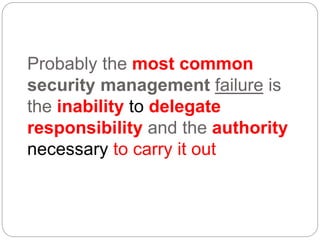
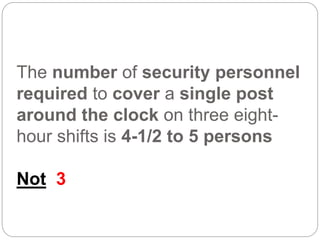
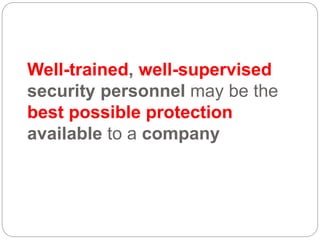
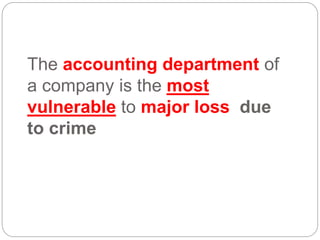
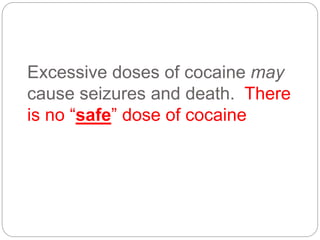
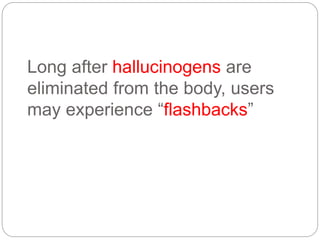
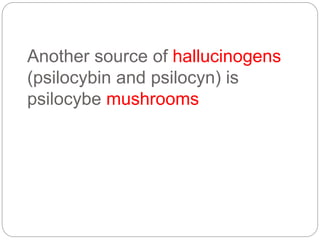
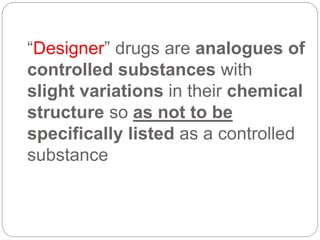
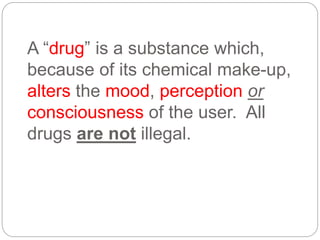
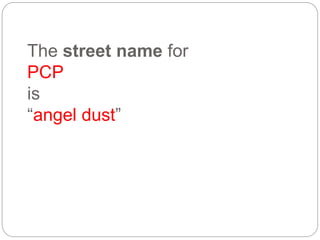
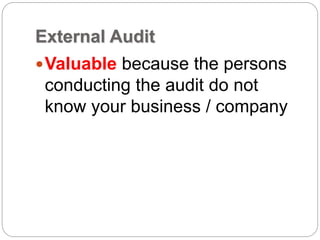
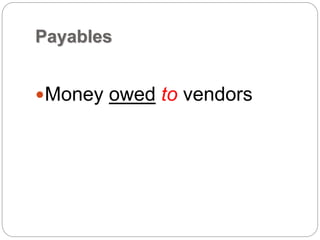
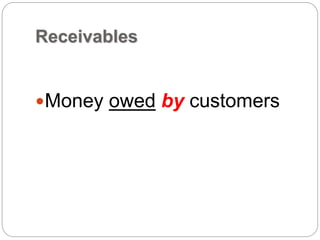
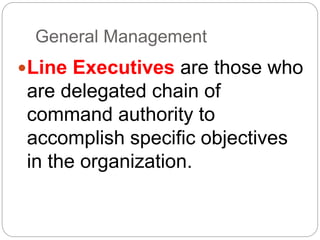
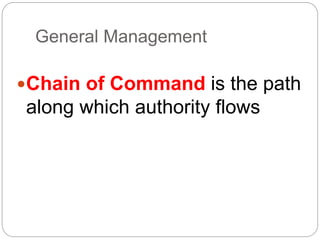
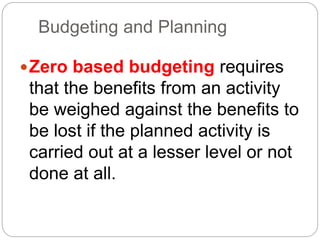
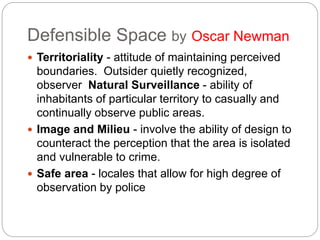
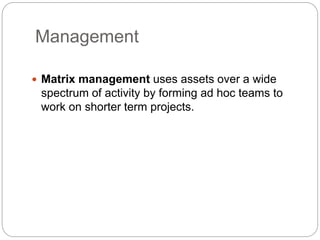
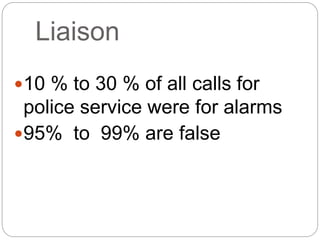
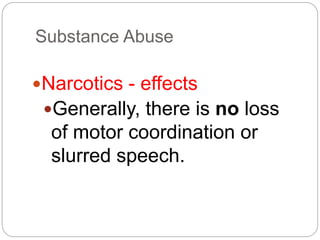
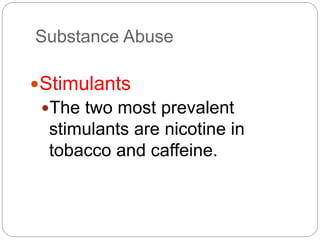
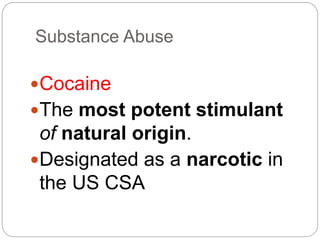
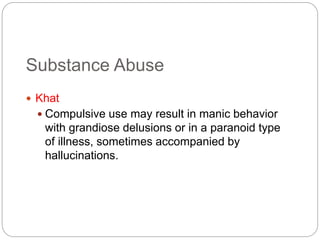
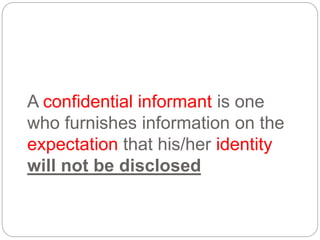
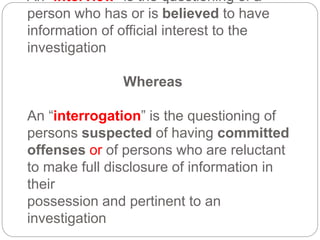
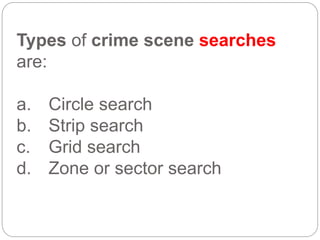
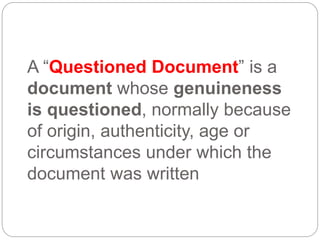
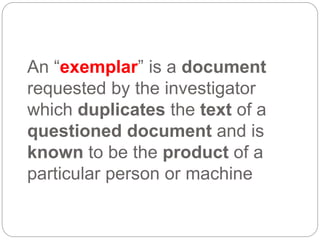
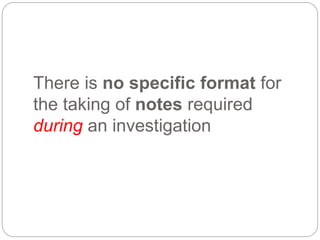
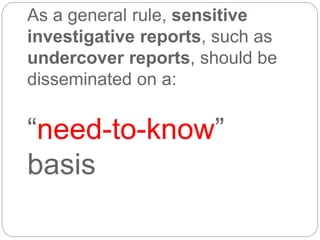
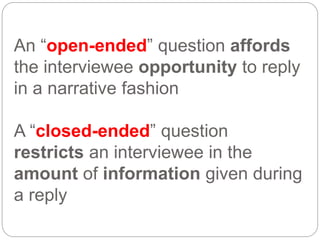
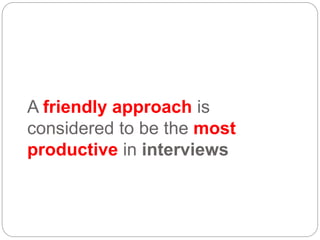
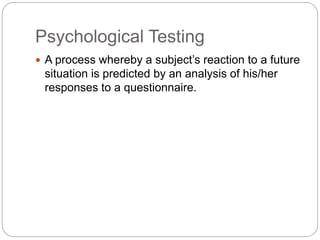
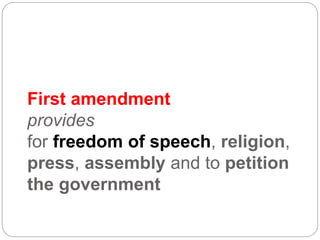
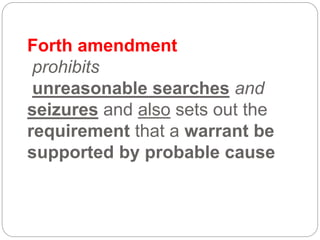
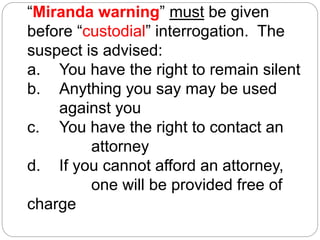
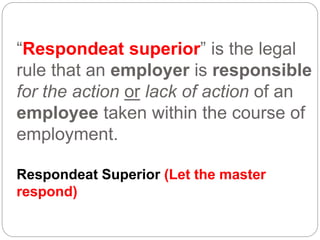
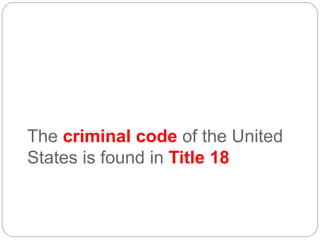
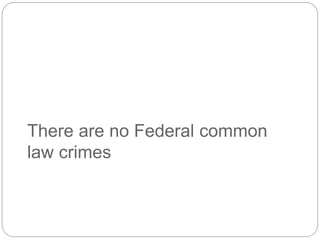
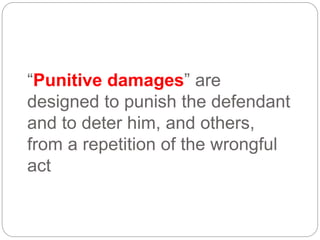
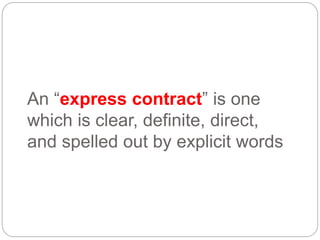
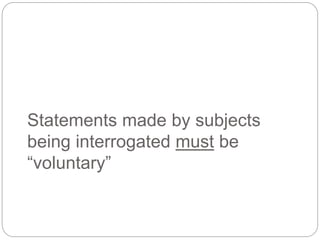
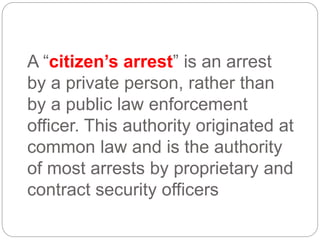
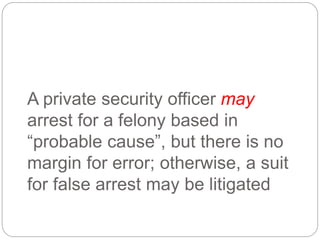
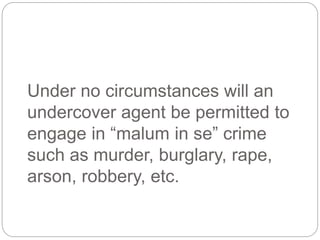
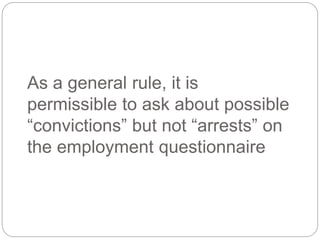
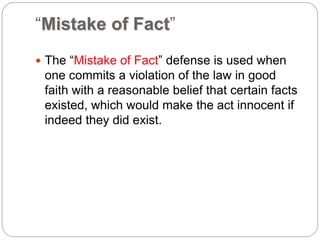
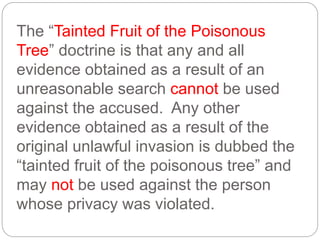
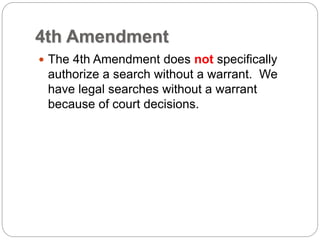
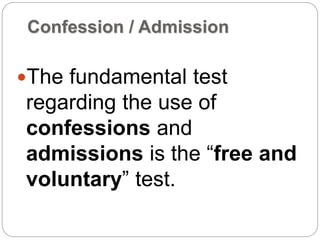
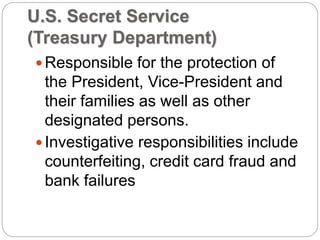
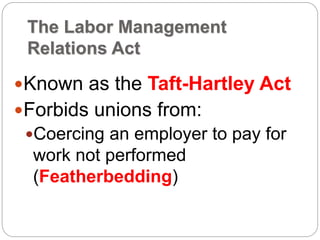
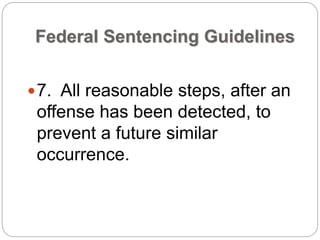
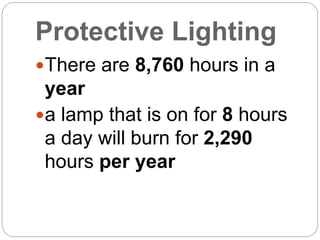
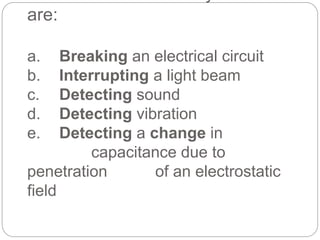
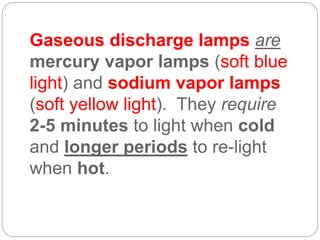
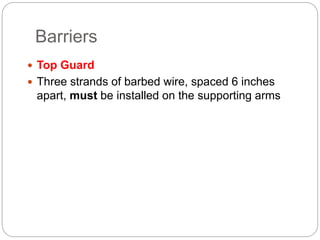
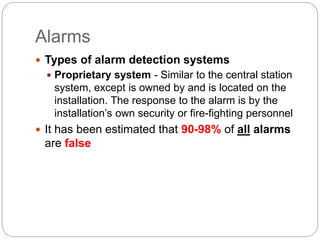
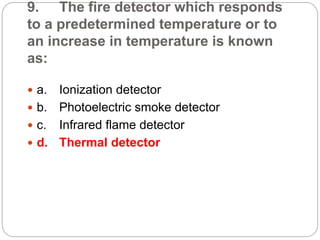
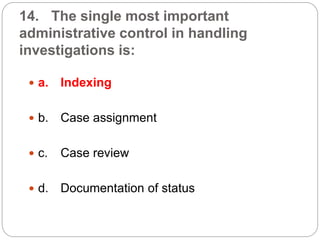
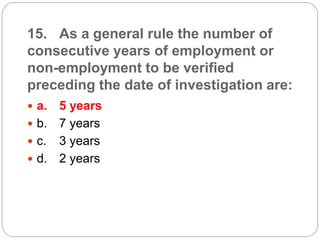
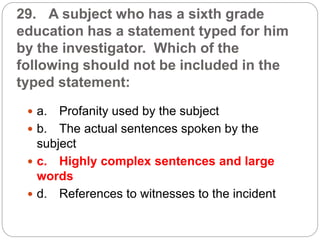
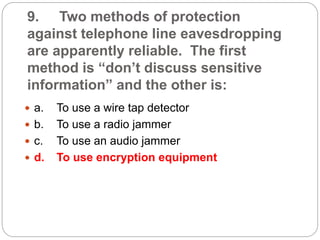
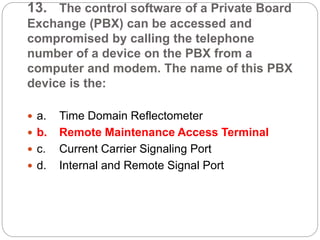
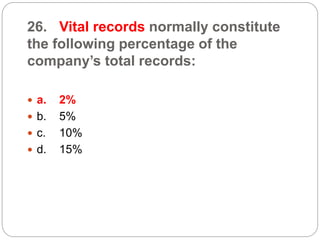
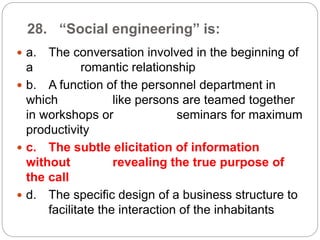
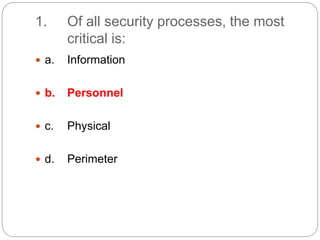
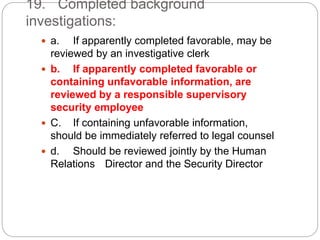
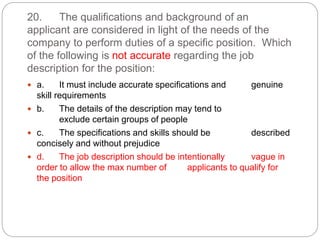
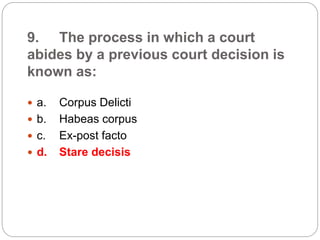
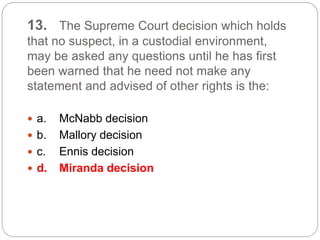
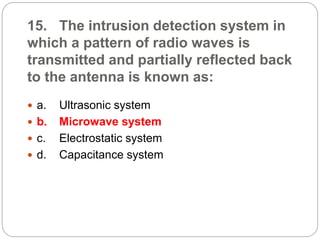
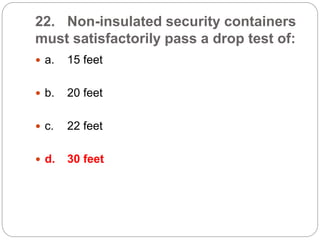
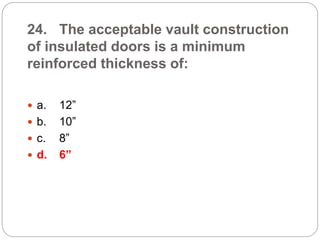
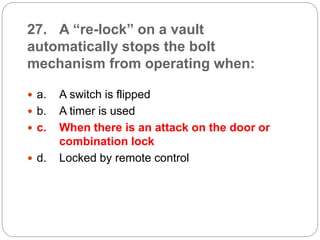
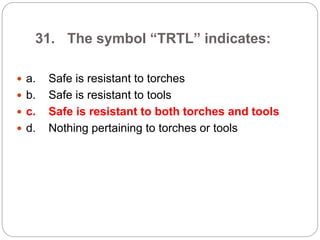
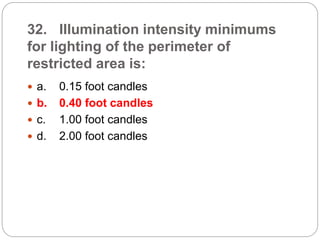
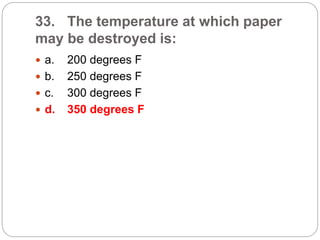
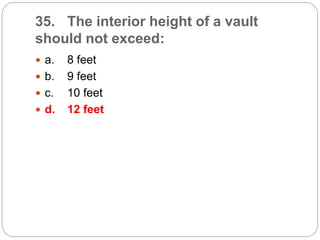
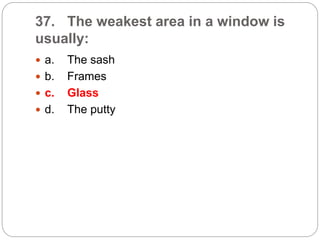
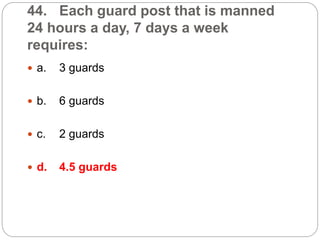
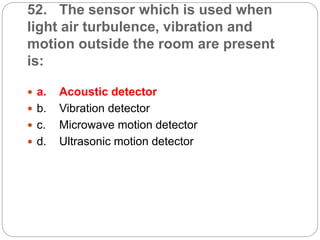
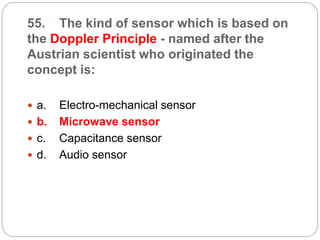
This document provides a study guide for the Certified Protection Professional (CPP) exam. It recommends reading over 500 slides and deleting slides already known, using 300 practice quizzes for testing, and purchasing "The Complete Guide of the CPP Exam" book. The guide was created by collecting open source CPP study materials online. Test takers are advised to repeat the process and then take the CPP exam, notifying the creator upon passing.