IP tables,Filtering.pptx
•Download as PPTX, PDF•
0 likes•125 views
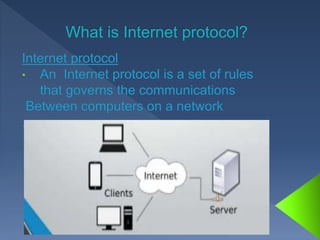
ip address
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (20)
Topic # 12 of outline Configuring Local Services.pptx

Topic # 12 of outline Configuring Local Services.pptx
System Administration: Introduction to system administration

System Administration: Introduction to system administration
System and network administration network services

System and network administration network services
Similar to IP tables,Filtering.pptx
Similar to IP tables,Filtering.pptx (20)
Lecture 2 -_understanding_networks_with_presenter_notes

Lecture 2 -_understanding_networks_with_presenter_notes
Geometric efficient matching algorithm for firewalls

Geometric efficient matching algorithm for firewalls
Geometric efficient matching algorithm for firewalls

Geometric efficient matching algorithm for firewalls
Simple Network Management Protocol by vikas jagtap

Simple Network Management Protocol by vikas jagtap
More from AyeCS11
More from AyeCS11 (10)
Topic # 14 of outline Administer Local Users and Groups.pptx

Topic # 14 of outline Administer Local Users and Groups.pptx
Topic # 16 of outline Managing Network Services.pptx

Topic # 16 of outline Managing Network Services.pptx
Recently uploaded
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptxnull - The Open Security Community
Recently uploaded (20)
Designing IA for AI - Information Architecture Conference 2024

Designing IA for AI - Information Architecture Conference 2024
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
"Federated learning: out of reach no matter how close",Oleksandr Lapshyn

"Federated learning: out of reach no matter how close",Oleksandr Lapshyn
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx
IP tables,Filtering.pptx
- 2. An internet protocol address is a numerical Label assigned to each device connected network that use the internet protocol for communication. The address is made of 32 binary bits which can be divisible into network portion and host portion with the help of a subnet mask.
- 3. The basic firewall software used in Linux is called IP tables. IP tables is a command –line firewall utility that uses policy chain allow .when a connection established itself on the system the IP tables looks for a rule in its list match it . if don’t find it show default action. We can call basic firewalls for Linux . The firewall system is normally installed and shoe the input and output packets.
- 4. o The default structure of IP Tables is like: “Tables which has chains and the chains which contain rules” o Table Chains Rules o The rules are defined to control the packets for input/output.
- 5. o The kernel has the ability to filter packets and decide based on the rules what to do with each packet. o IP filtering is simply mechanism that decides which types of IP datagram will be processed normally which will be discarded o Packet filtering uses a list of rules for filtering.
- 6. The three built-in tables with chain rules. They are follows: o Filter: The default tables for handling network packets. o Nat: Used to alter packets that create a new connection. o Mangle: used for specific types of packet alteration.