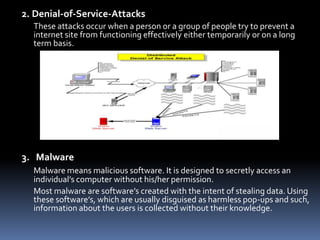
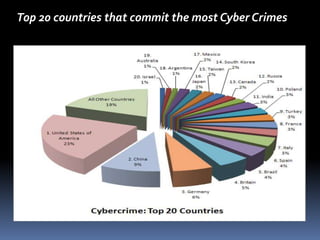
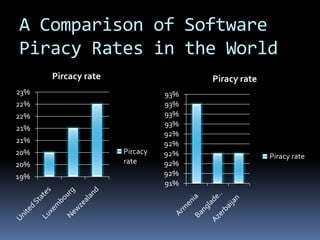
This document summarizes different types of computer crimes and cybercrimes. It discusses 12 types of cybercrimes including viruses/worms, denial of service attacks, malware, hacking, software piracy, fraud, cyber stalking, obscene content, harassment, trafficking, computer vandalism, and spam. It also provides information on countries that commit the most cybercrimes globally and issues related to software piracy in Bangladesh. While Bangladesh has experienced little cybercrime to date, the document predicts it will likely see rising crimes as internet usage increases.