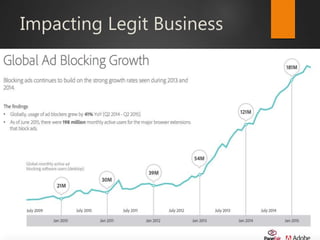
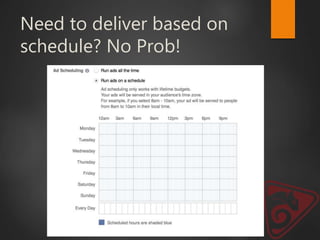
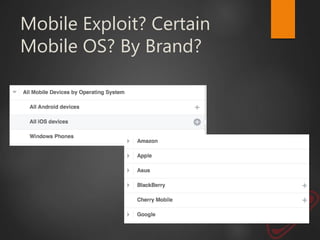
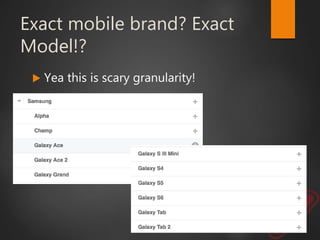
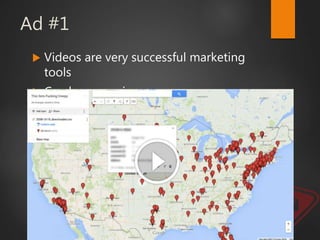
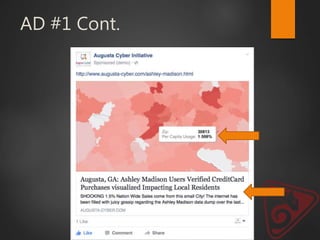
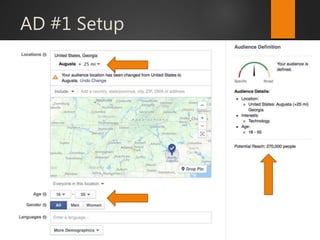
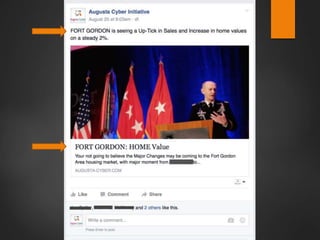
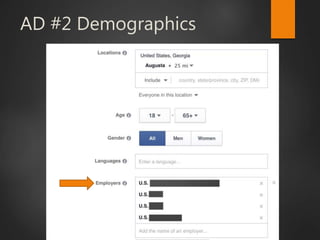
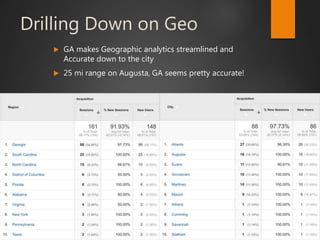
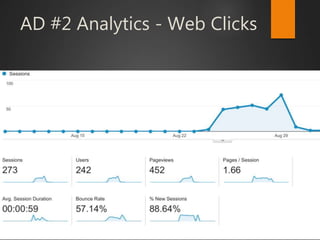
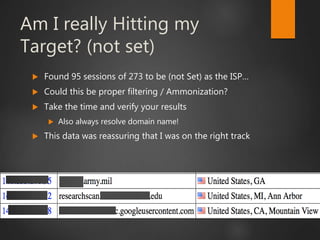
This document discusses strategic malvertising techniques. It begins with an introduction to malvertising and an overview of how ad-based malware works. It then discusses targeting methods like using open source intelligence and big data analytics to precisely target ads. The document outlines one individual's one-week experiment conducting malvertising campaigns on Facebook. It found the ad review process was ineffective and the campaigns successfully reached the targeted locations and demographics. The document concludes by arguing large, well-funded campaigns could have significant impact and questions whether ad agencies adequately protect users.