Test Table for Wireless NIC
•Download as DOCX, PDF•
0 likes•338 views
This is a test table that was created when testing the wireless NIC. It can also be used as a guide, to show how to test a Wi-Fi connection. It includes a number different tests which include ping, ipconfig,and drivers. This document is part of my IT coursework*
Report
Share
Report
Share
Recommended
Recommended
More Related Content
Viewers also liked
Viewers also liked (8)
Similar to Test Table for Wireless NIC
Similar to Test Table for Wireless NIC (20)
IT Essentials (Version 7.0) - ITE Chapter 6 Exam Answers

IT Essentials (Version 7.0) - ITE Chapter 6 Exam Answers
Commands used in Assessing Network layout & Security

Commands used in Assessing Network layout & Security
Positive Hack Days. Pavlov. Network Infrastructure Security Assessment

Positive Hack Days. Pavlov. Network Infrastructure Security Assessment
More from Ajay Jassi
More from Ajay Jassi (20)
Hardware Documentation and Benefits of Hardware Provider

Hardware Documentation and Benefits of Hardware Provider
IT job role description for Technical Support Engineer

IT job role description for Technical Support Engineer
Reasons why Hardware is Installed and Potential Problems and the Precautions

Reasons why Hardware is Installed and Potential Problems and the Precautions
Potential problems that occur during hardware installation

Potential problems that occur during hardware installation
Health and safety requirements for computer maintenance

Health and safety requirements for computer maintenance
Recently uploaded
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Test Table for Wireless NIC
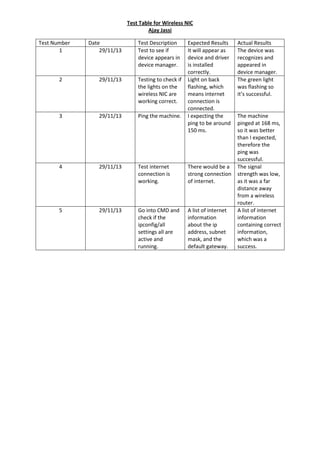
- 1. Test Table for Wireless NIC Ajay Jassi Test Number 1 Date 29/11/13 Test Description Test to see if device appears in device manager. Expected Results It will appear as device and driver is installed correctly. Light on back flashing, which means internet connection is connected. I expecting the ping to be around 150 ms. 2 29/11/13 Testing to check if the lights on the wireless NIC are working correct. 3 29/11/13 Ping the machine. 4 29/11/13 Test internet connection is working. There would be a strong connection of internet. 5 29/11/13 Go into CMD and check if the ipconfig/all settings all are active and running. A list of internet information about the ip address, subnet mask, and the default gateway. Actual Results The device was recognizes and appeared in device manager. The green light was flashing so it’s successful. The machine pinged at 168 ms, so it was better than I expected, therefore the ping was successful. The signal strength was low, as it was a far distance away from a wireless router. A list of internet information containing correct information, which was a success.
