Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9
•
0 likes•132 views
Laptop recovery story of How the Absolute recovery team recovered a stolen laptop from Virginia USA. Visit: http://www3.absolute.com/lojackforlaptops/ to recover and track your stolen laptops or mac.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (7)
United States Secret Service: Protecting the Nation's Leaders and Financial I...

United States Secret Service: Protecting the Nation's Leaders and Financial I...
Viewers also liked
Viewers also liked (15)
Presentatie vanbuurt ICT, Microsoft Office Specialist bijeenkomst 10 december...

Presentatie vanbuurt ICT, Microsoft Office Specialist bijeenkomst 10 december...
Bay Insulation Supply is now stocking Sikaflex 1A tubes!

Bay Insulation Supply is now stocking Sikaflex 1A tubes!
Toxic Stress! Childhood Roots of Health Inequities:

Toxic Stress! Childhood Roots of Health Inequities:
Similar to Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9
Similar to Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9 (9)
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6

Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9

Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9
Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0

Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0
Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2

Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2
Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5

Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5
Laptop Theft Recovery Cases from Absolute Software – Case Number 7I5B2

Laptop Theft Recovery Cases from Absolute Software – Case Number 7I5B2
Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7

Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7
Recently uploaded
Recently uploaded (20)
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024

New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
Artificial intelligence in the post-deep learning era

Artificial intelligence in the post-deep learning era
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9
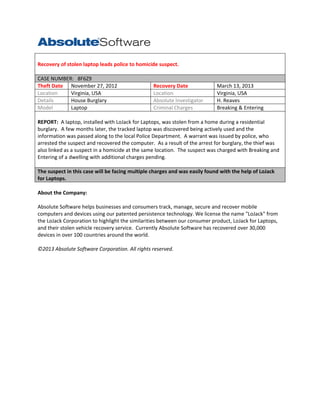
- 1. Recovery of stolen laptop leads police to homicide suspect. CASE NUMBER: 8F6Z9 Theft Date November 27, 2012 Location Virginia, USA Details House Burglary Model Laptop Recovery Date Location Absolute Investigator Criminal Charges March 13, 2013 Virginia, USA H. Reaves Breaking & Entering REPORT: A laptop, installed with LoJack for Laptops, was stolen from a home during a residential burglary. A few months later, the tracked laptop was discovered being actively used and the information was passed along to the local Police Department. A warrant was issued by police, who arrested the suspect and recovered the computer. As a result of the arrest for burglary, the thief was also linked as a suspect in a homicide at the same location. The suspect was charged with Breaking and Entering of a dwelling with additional charges pending. The suspect in this case will be facing multiple charges and was easily found with the help of LoJack for Laptops. About the Company: Absolute Software helps businesses and consumers track, manage, secure and recover mobile computers and devices using our patented persistence technology. We license the name "LoJack" from the LoJack Corporation to highlight the similarities between our consumer product, LoJack for Laptops, and their stolen vehicle recovery service. Currently Absolute Software has recovered over 30,000 devices in over 100 countries around the world. ©2013 Absolute Software Corporation. All rights reserved.
