The document discusses various topics related to network security including network layers, internet protocols like IPv4 and IPv6, network packet inspection, common attacks like spoofing, man-in-the-middle attacks, and denial of service attacks. It provides information on these topics and examples of hands-on exercises using tools like Wireshark to inspect network packets and demonstrate attacks. The document emphasizes the importance of network security defenses like IPsec, firewalls, intrusion detection systems, and security best practices.



![NETWORK LAYER
NO. 3 FROM OSI MODEL
PROVIDES THE FUNCTIONAL AND PROCEDURAL MEANS
OF TRANSFERING VARIABLE LENGTH DATA SEQUENCES
FROM SOURCE HOST TO A DESTINATION ON ONE
NETWORK TO ANOTHER, WHILE MAINTAINING THE QOS
REQUESTED BY TRANSPORT LAYER
FUCTION: PATH DETERMINATION AND LOGICAL
ADRESSING; DATA UNIT : PACKET/DATAGRAM
IP (IPV4, IPV6), ICMP, IPSEC, IGMP, IPX, APPLE TALK
[1]: WIKIPEDIA.ORG
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-5-2048.jpg)
![OSI 7 LAYER
[1]: WIKIPEDIA.ORG
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-6-2048.jpg)
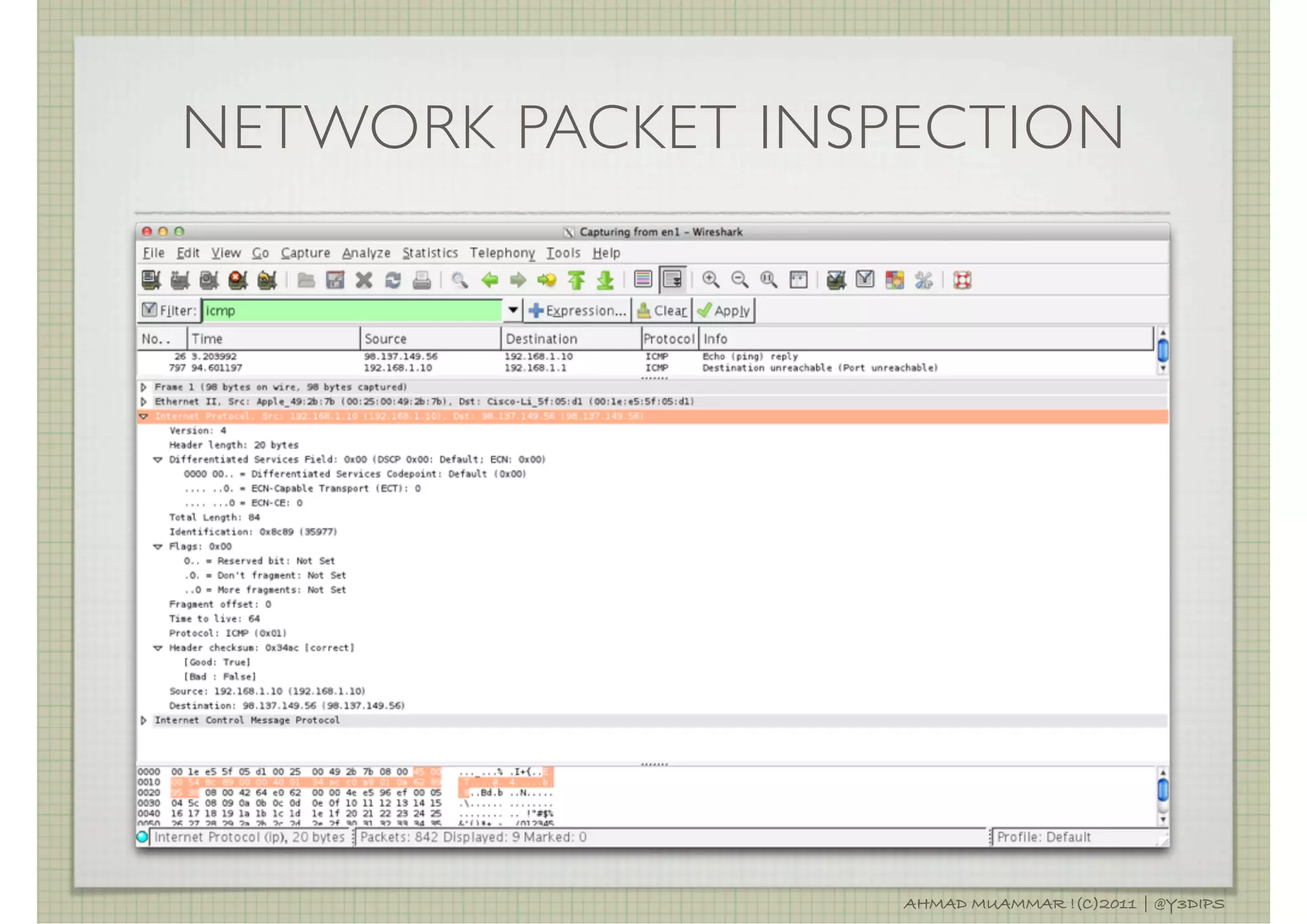
![INTERNET PROTOCOL
RESPONSIBLE FOR ADDRESSING HOSTS AND ROUTING
DATAGRAM (PACKETS) FROM A SOURCE HOST TO
DESTINATION HOST ACCROSS ONE OR MORE IP
NETWORK.
[1]: WIKIPEDIA.ORG
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-7-2048.jpg)
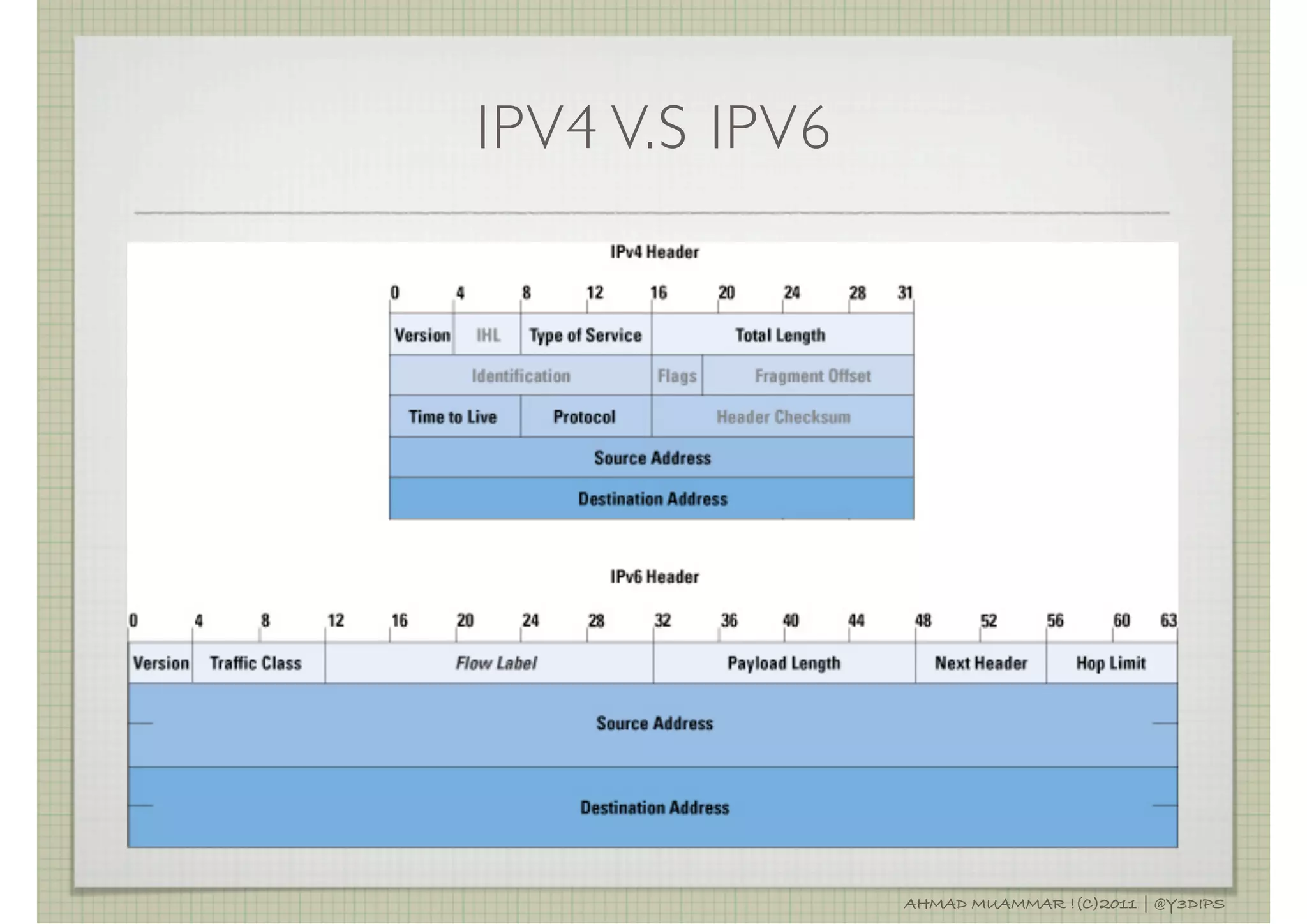
![IPV4
FOURTH REVISION IN THE DEVELOPMENT OF IP AND THE
FIRST VERSION OF THE PROTOCOL WIDELY DEPLOYED
CONNECTIONLESS, NOT GUARANTEE DELIVERY, NOT
ASSURING PROPER SEQUENCE OR AVOIDANCE OF
DUPLICATE DELIVERY,
32 BIT = 192.168.0.1
IPSEC IS OPTIONAL
[1]: WIKIPEDIA.ORG
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-8-2048.jpg)







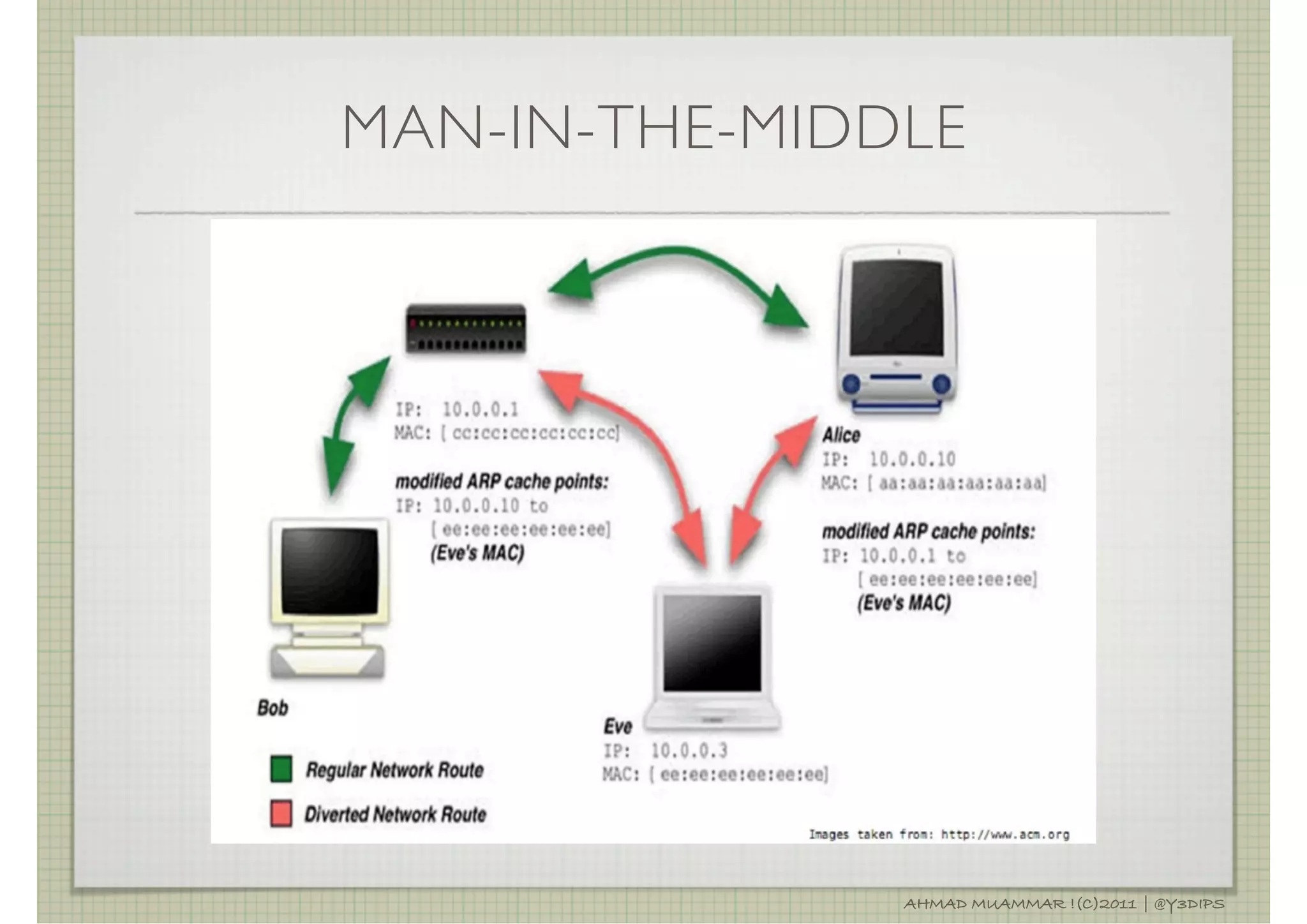
![SPOOFING
SPOOF = MASQUEARADE[1]
IS A SITUATION IN WHICH A PROGRAM SUCCESSFULLY
MASQUARADES AS ANOTHER BY FALSIFYING DATA AND
THEREBY GAINING AN ILLEGITIMATE ADVANTAGE[2]
[1]: RFC4949
[2]: WIKIPEDIA.ORG
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-20-2048.jpg)
![SPOOFING
IPSPOOFING, E.G: MODIFY SOURCE ADDRESS
A COMMON MISCONCEPTION: IP SPOOFING CAN BE USED
TO HIDE IP ADDRESS WHILE SURFING THE INTERNET,
CHATTING, ON-LINE, AND SO FORTH. THIS IS GENERALLY
NOT TRUE. FORGING THE SOURCES IP ADDRESS CAUSES
THE RESPONSES TO BE MISDIRECTED, MEANING CANNOT
CREATE NORMAL NETWORK CONNECTION.[1]
USUALLY COMBINE WITH NETWORK DOS/DDOS ATTACK
[1]: ISS.NET
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-21-2048.jpg)

![TUNNELING
TUNNEL IS A COMMUNICATION CHANNEL CREATED IN A
COMPUTER NETWORK BY ENCAPSULATING (I.E.,
LAYERING) A COMMUNICATION PROTOCOL’S DATA
PACKETS IN (I.E., ABOVE) A SECOND PROTOCOL THAT
NORMALLY WOULD BE CARRIED ABOVE, OR AT THE SAME
LAYER AS, THE FIRST ONE. [1]
HTTP, SSH, DNS, ICMP
SSH FOO@DOO -D PORT
[1]: RFC4949
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-23-2048.jpg)

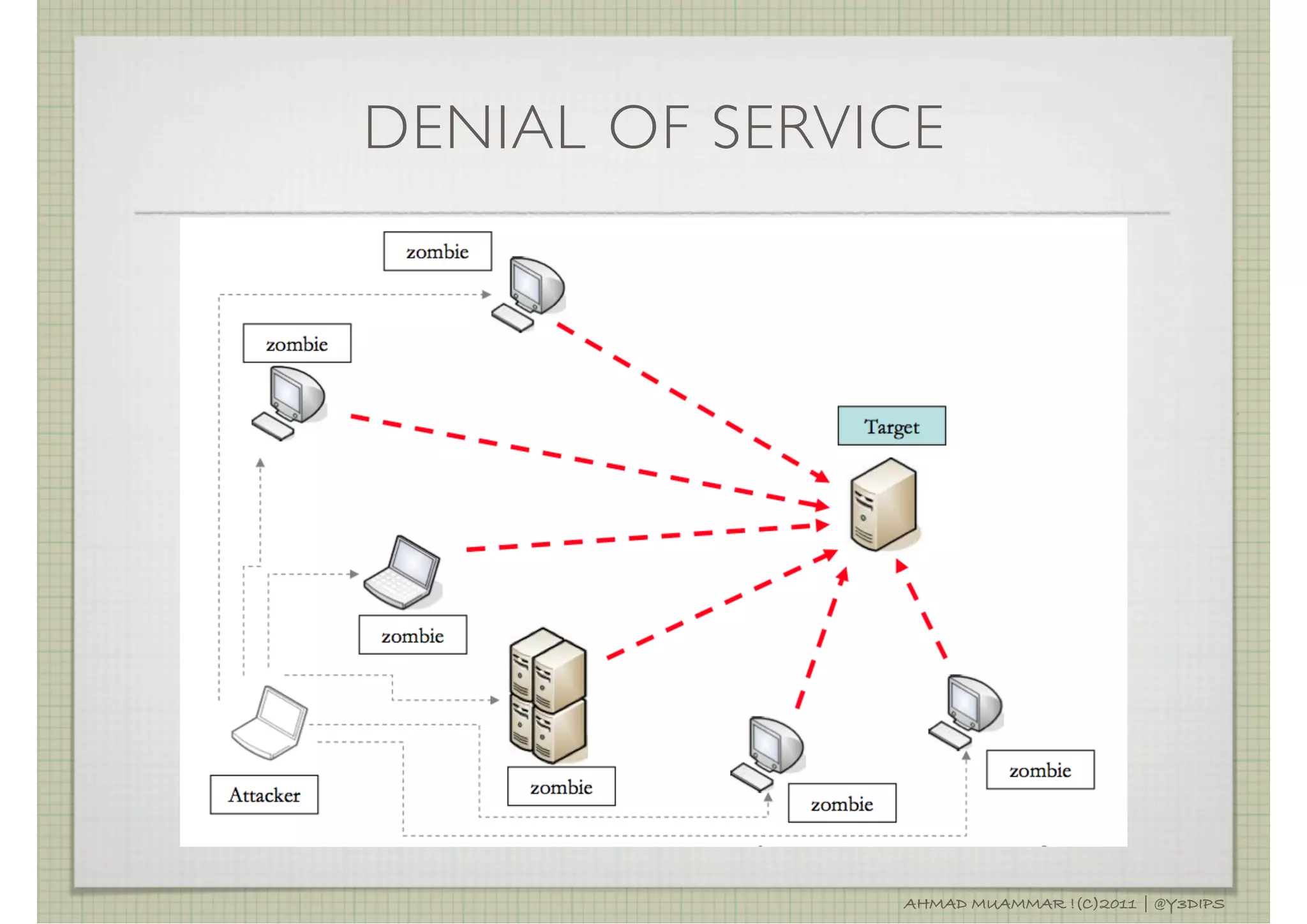
![DENIAL OF SERVICE
THE PREVENTION OF AUTHORIZED ACCESS TO A SYSTEM
RESOURCE OR THE DELAYING OF SYSTEM OPERATIONS
AND FUNCTION. [1]
PING OF DEATH (ICMP FLOODING), SYNFLOOD
DISTRIBUTED DOS, BOT NET
[1]: RFC4949
AHMAD MUAMMAR !(C)2011 | @Y3DIPS](https://image.slidesharecdn.com/networksecurity-120108234214-phpapp02/75/Network-security-28-2048.jpg)