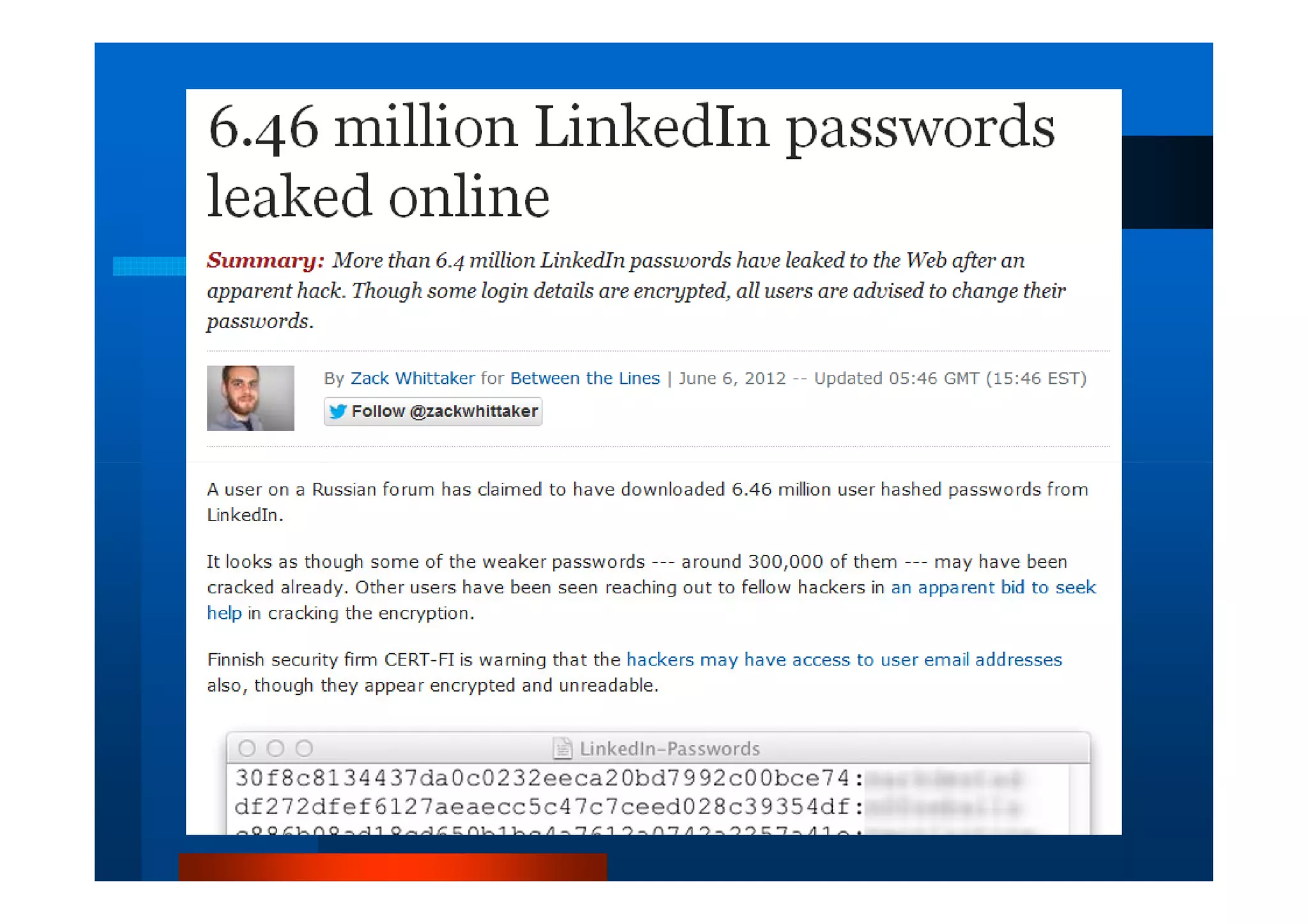
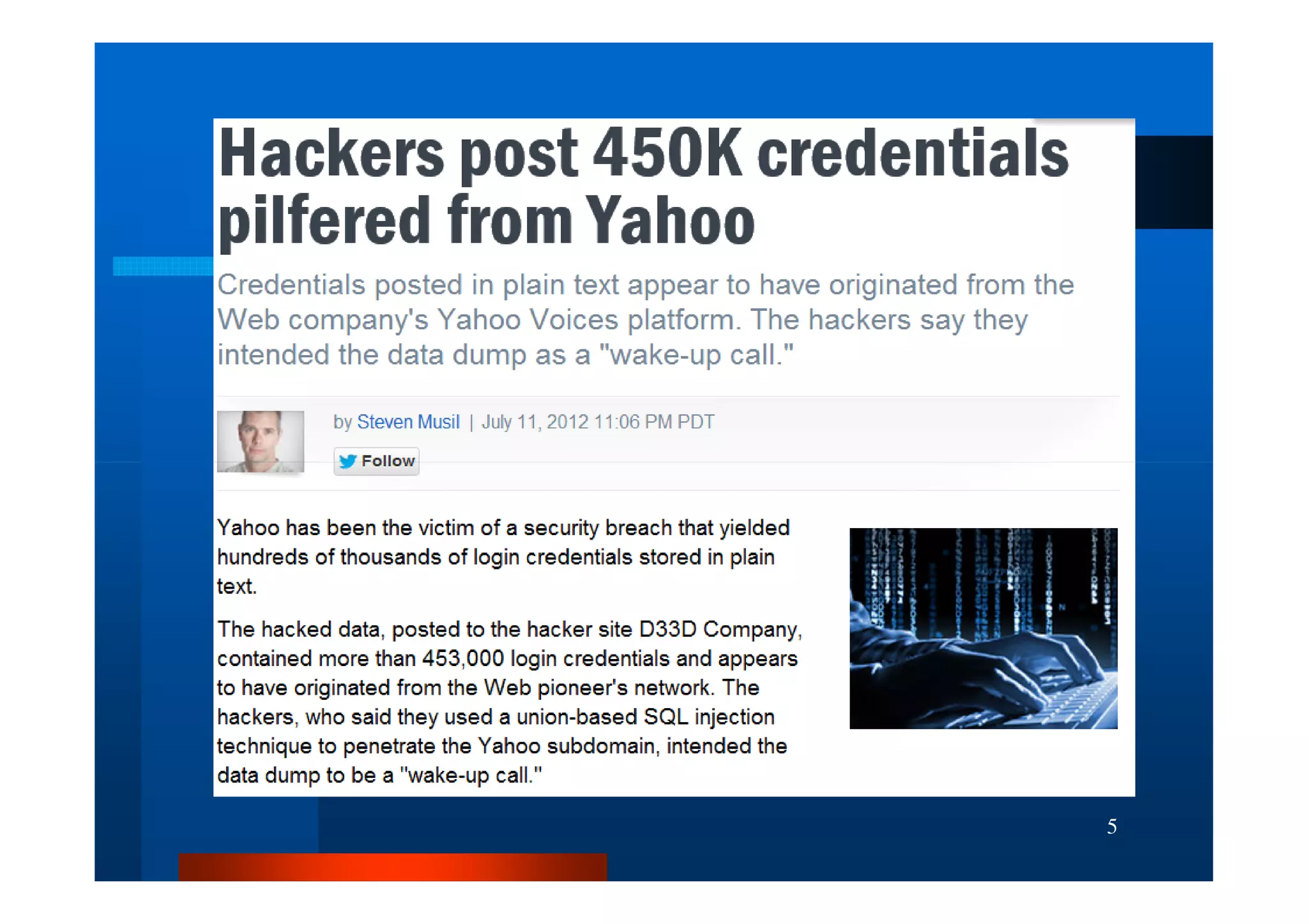
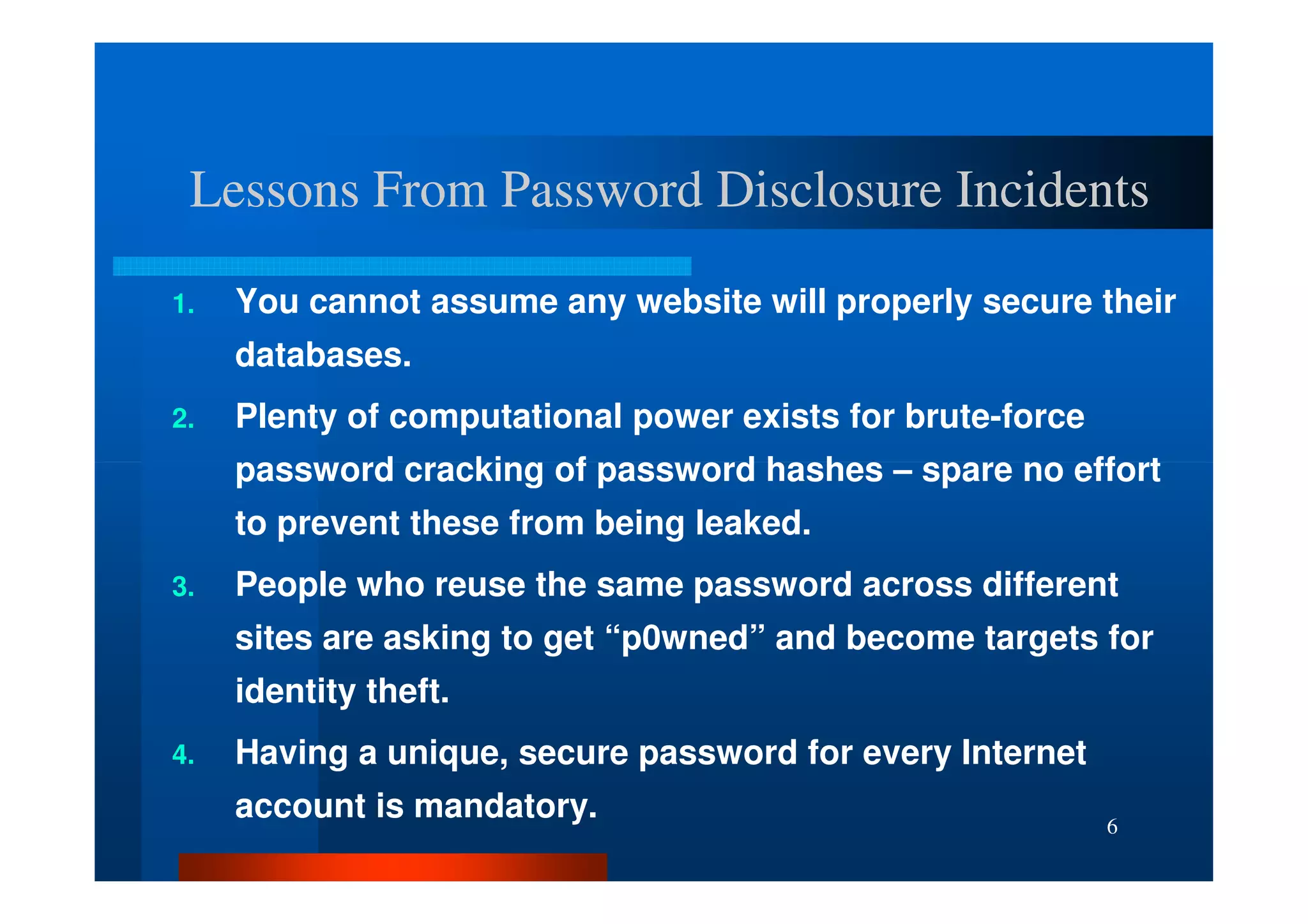
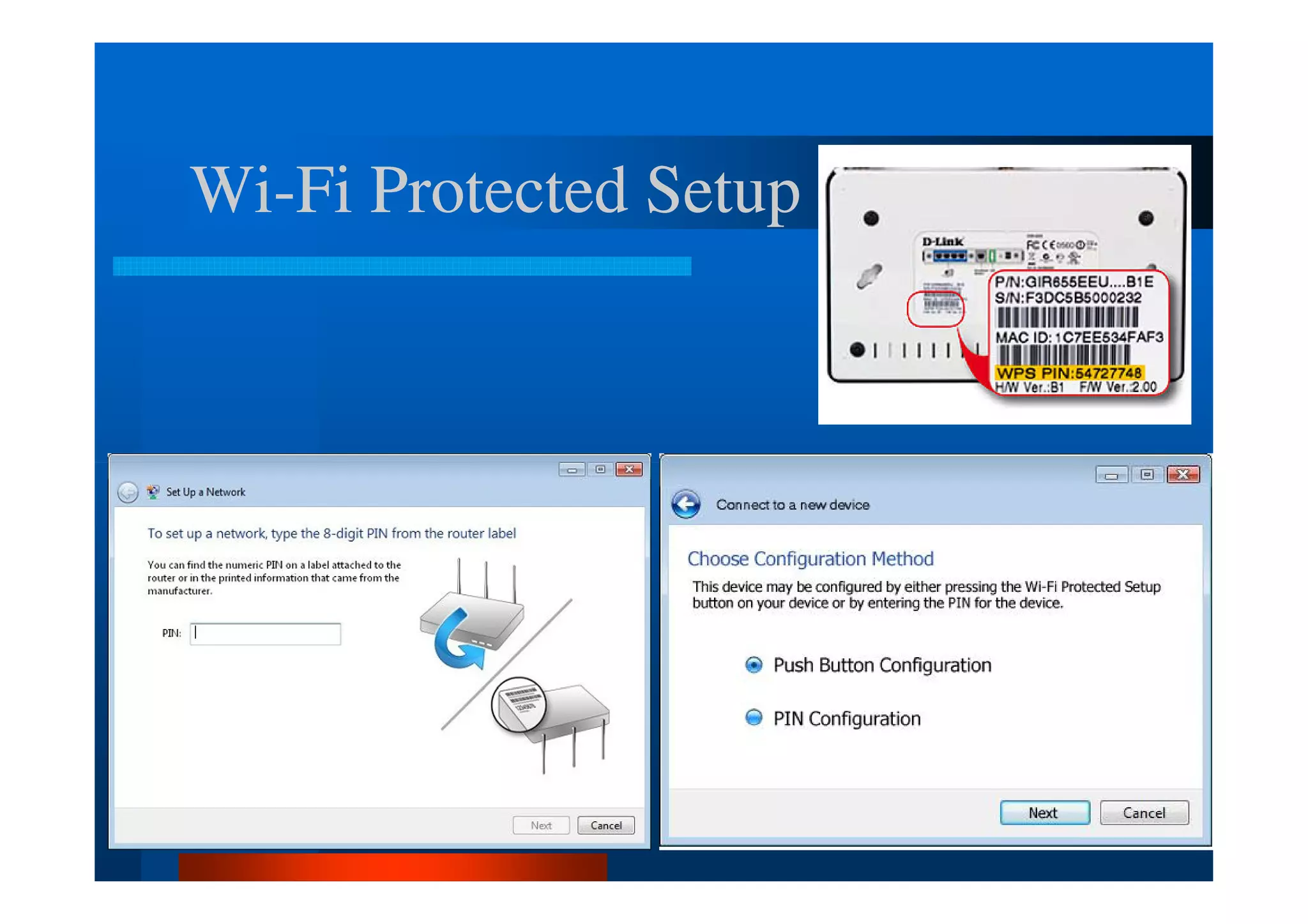
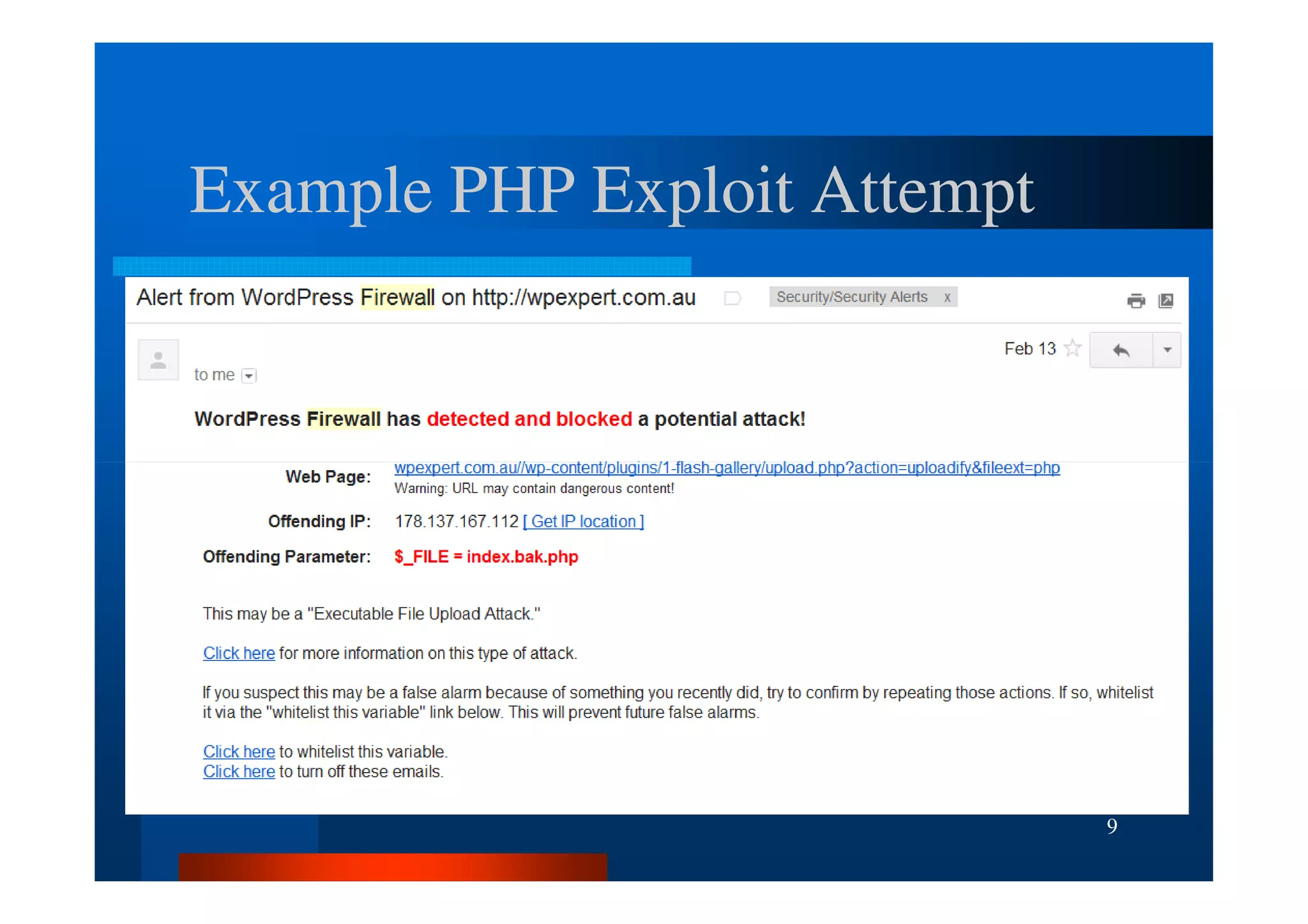
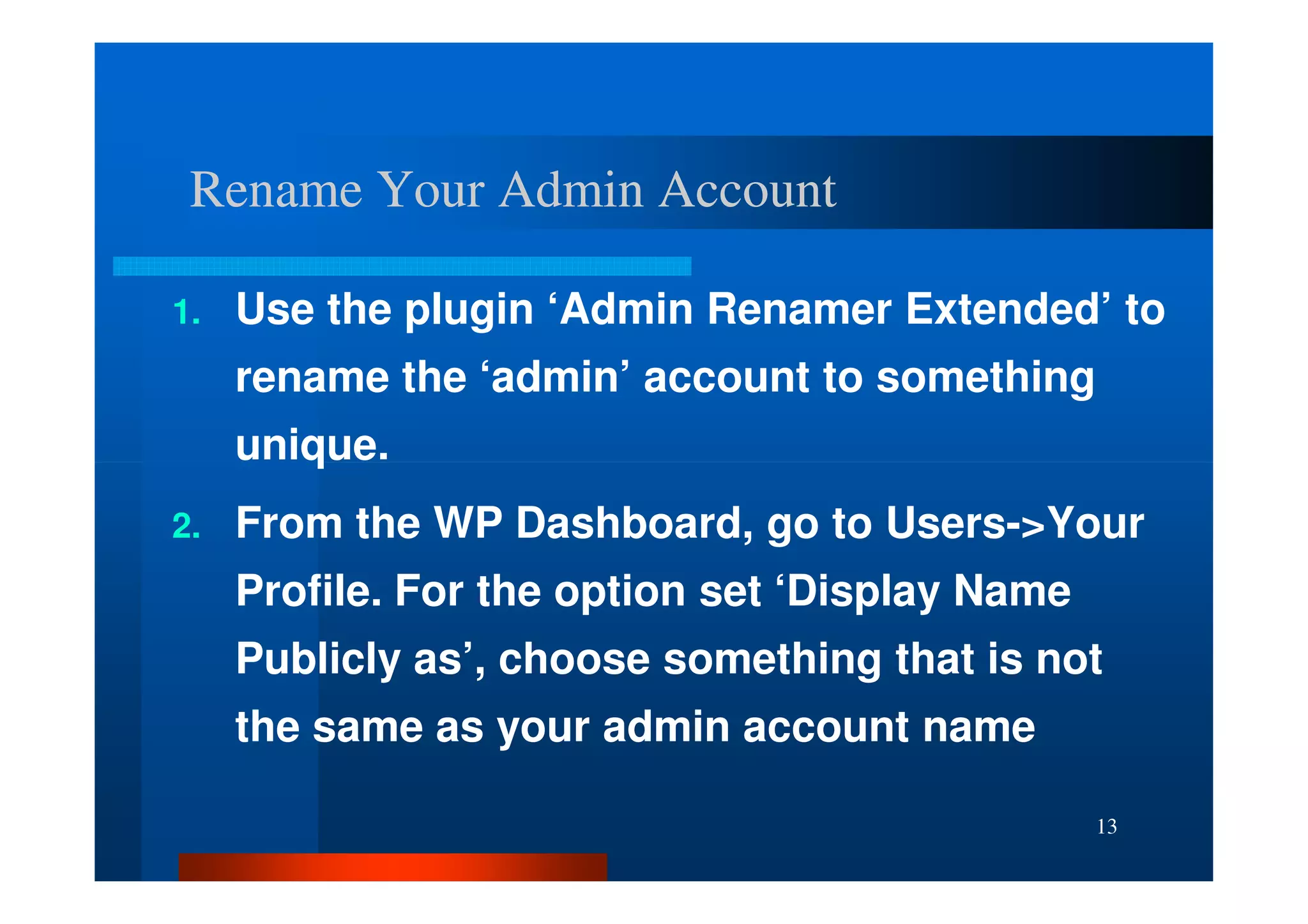
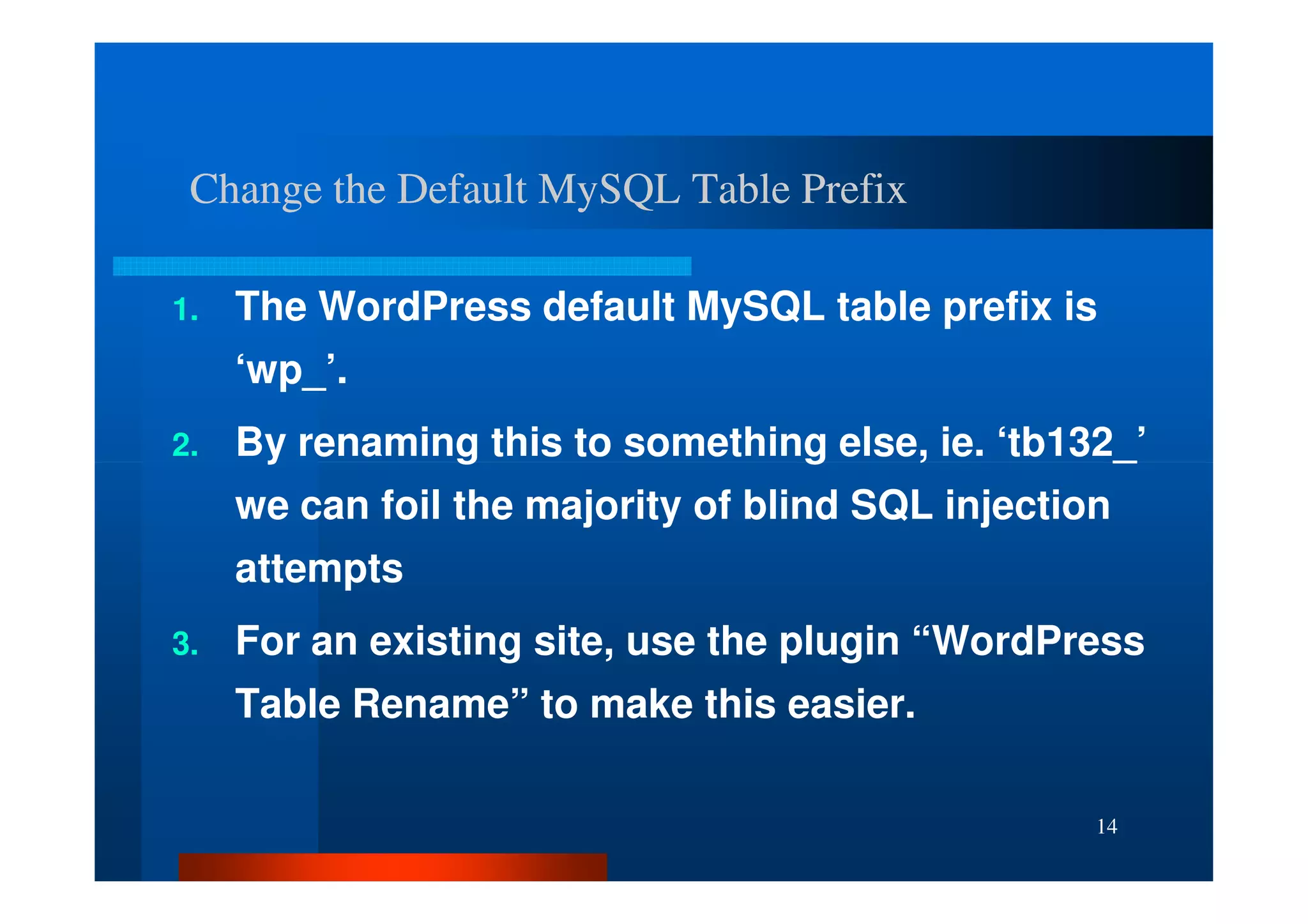
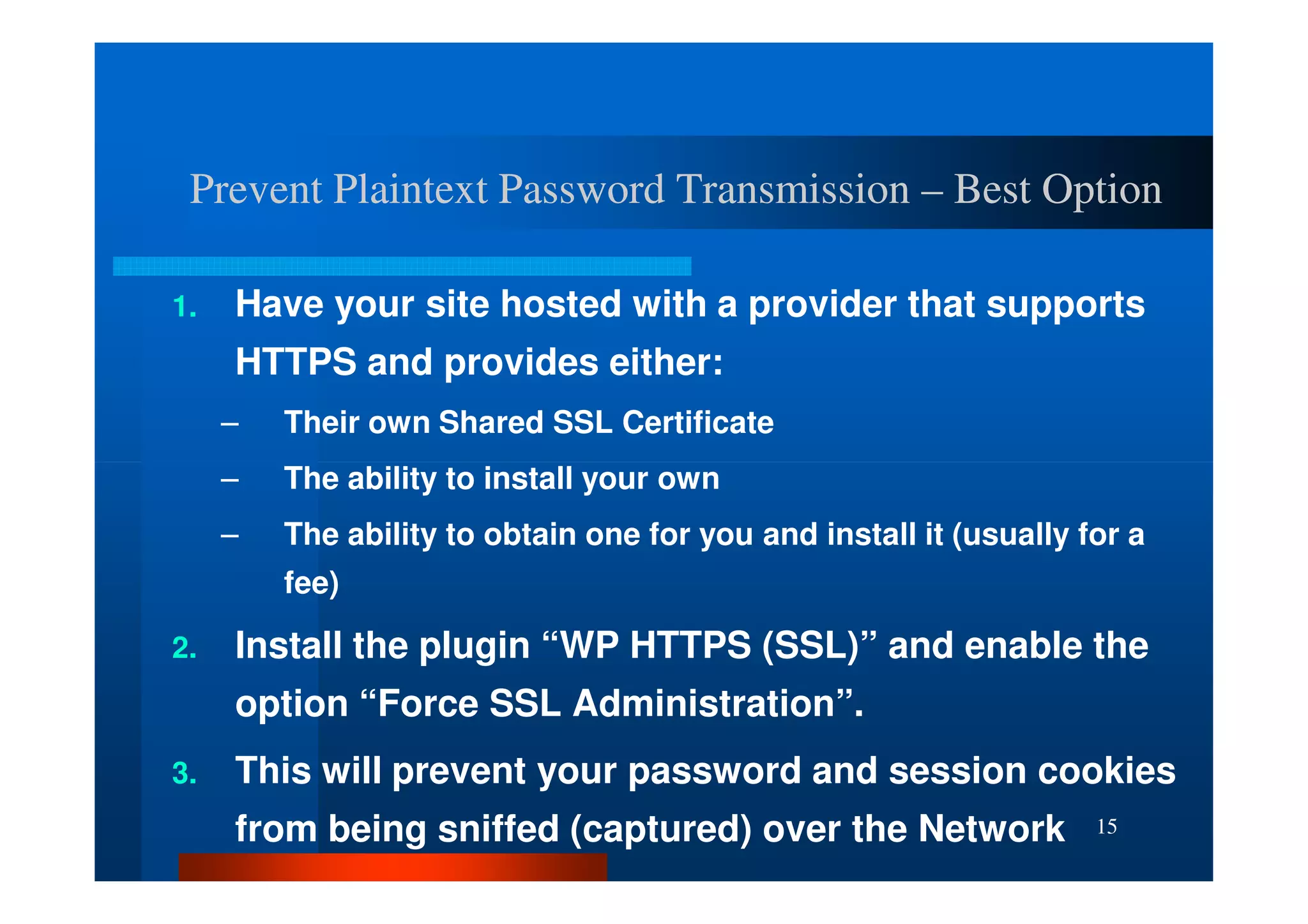
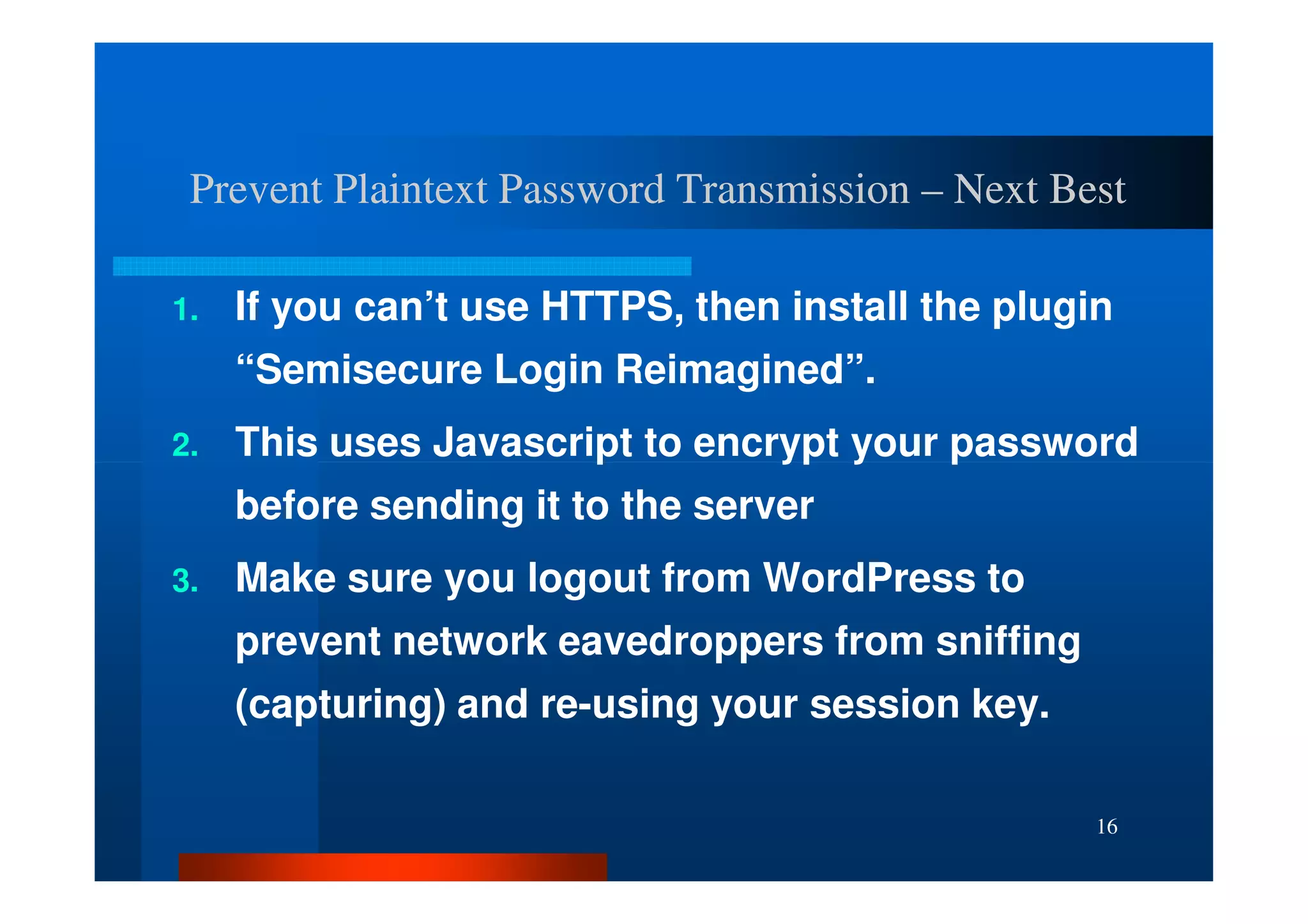
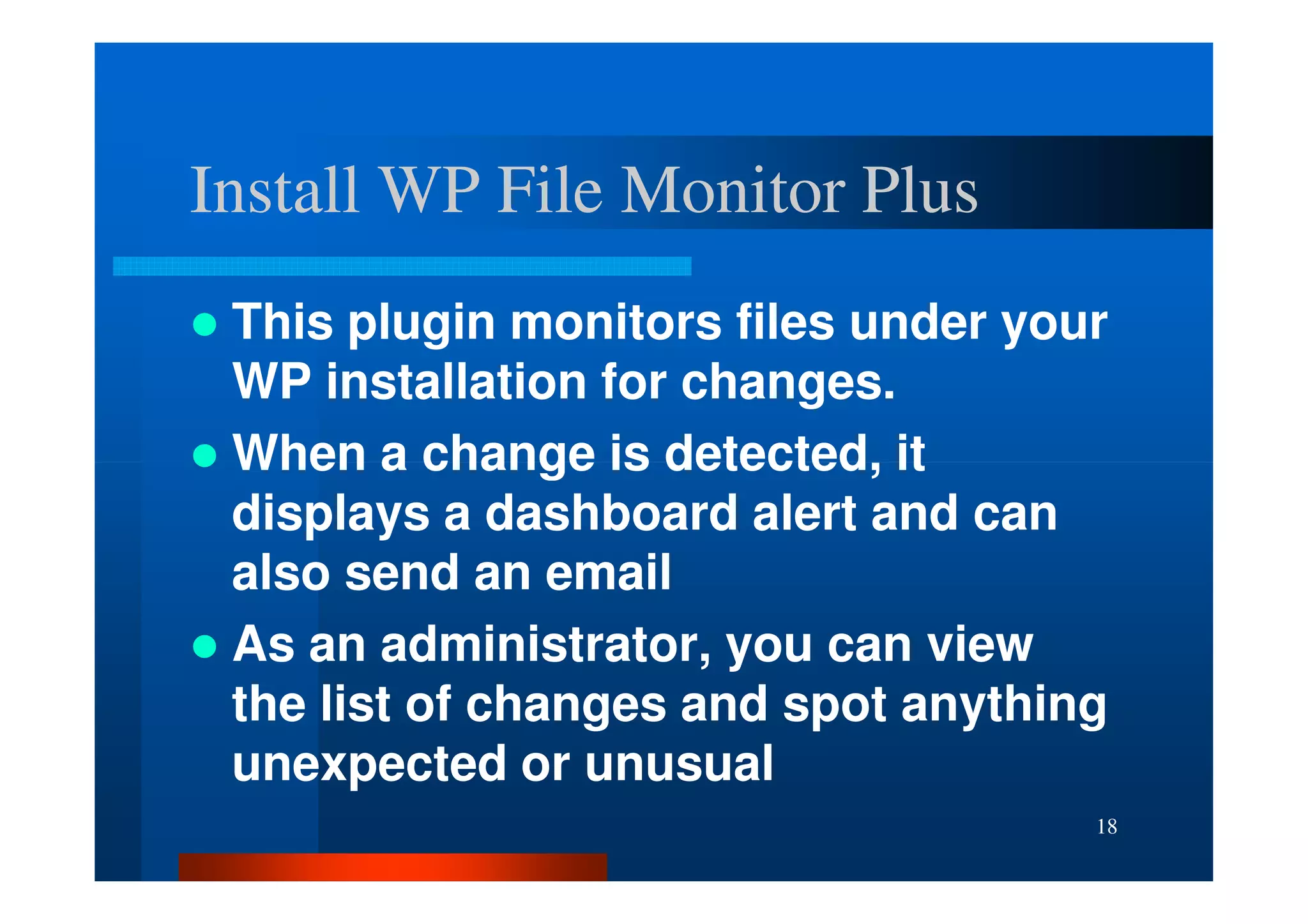
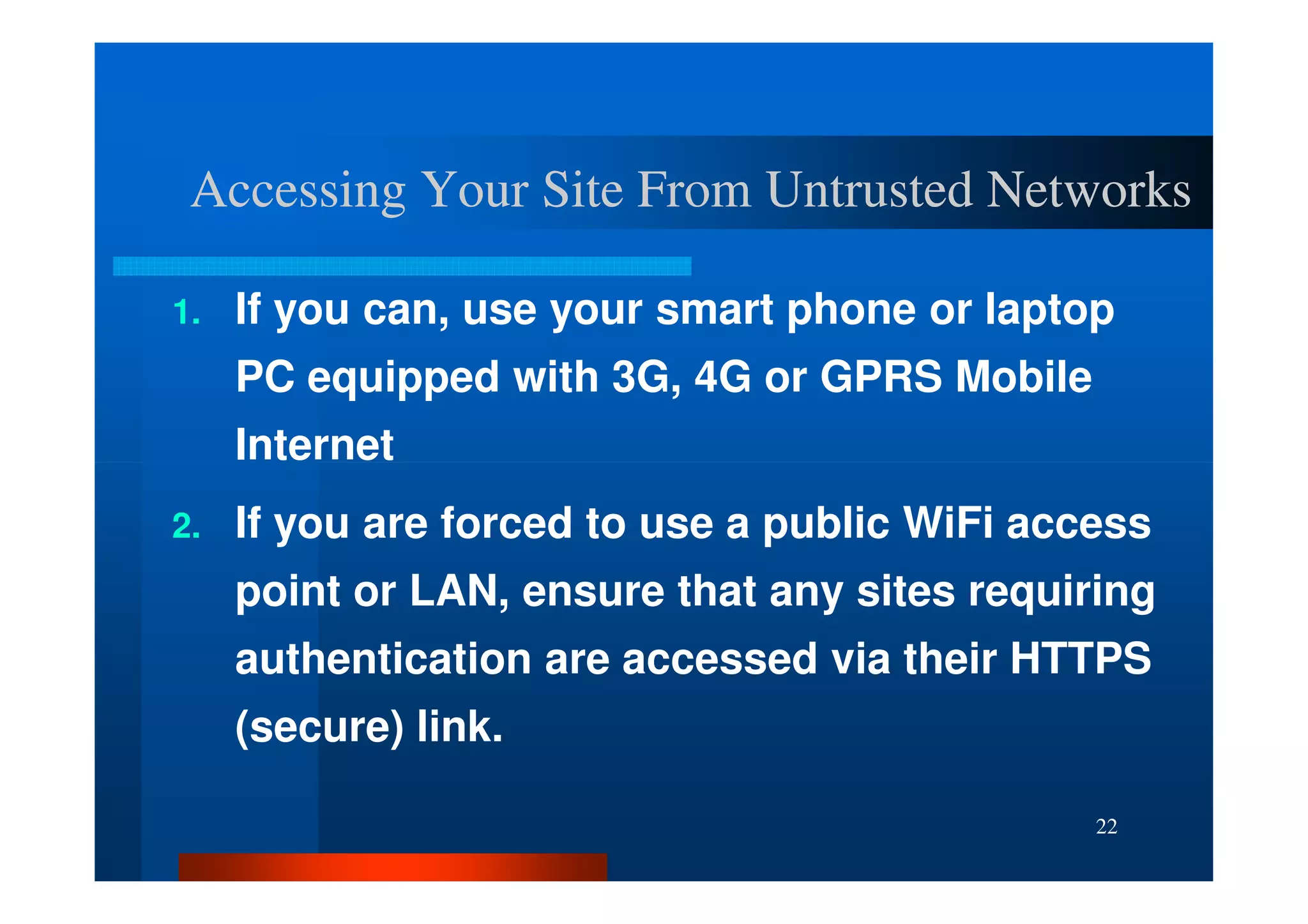
The document outlines security threats and best practices for securing WordPress websites, highlighting incidents from 2012 and common vulnerabilities such as password leaks and PHP exploits. It emphasizes critical steps to harden installations, including setting up firewalls, renaming admin accounts, changing database prefixes, and employing secure password practices. Additionally, it stresses the importance of regular updates, two-factor authentication, and using secure connections when accessing sites from untrusted networks.