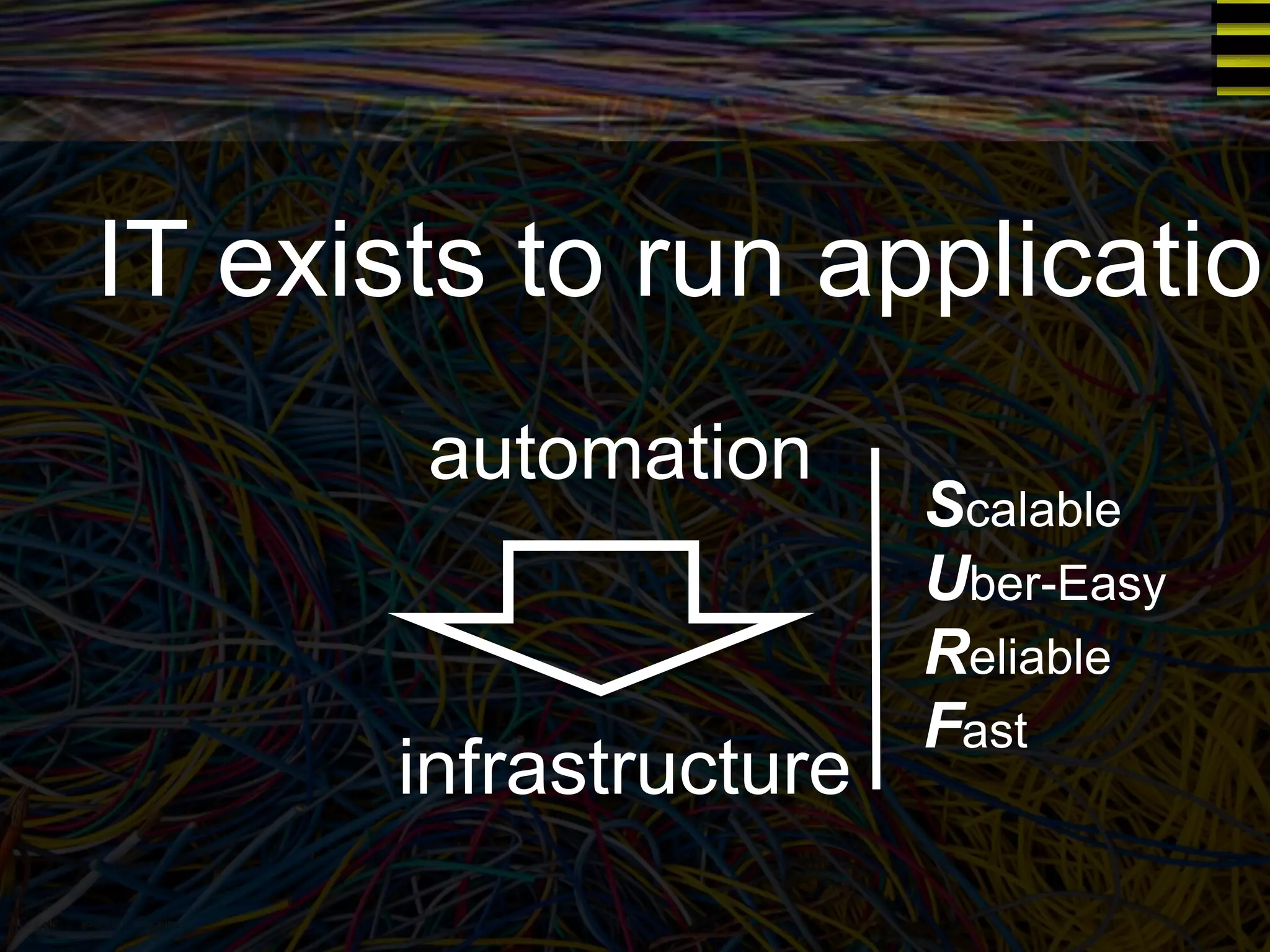
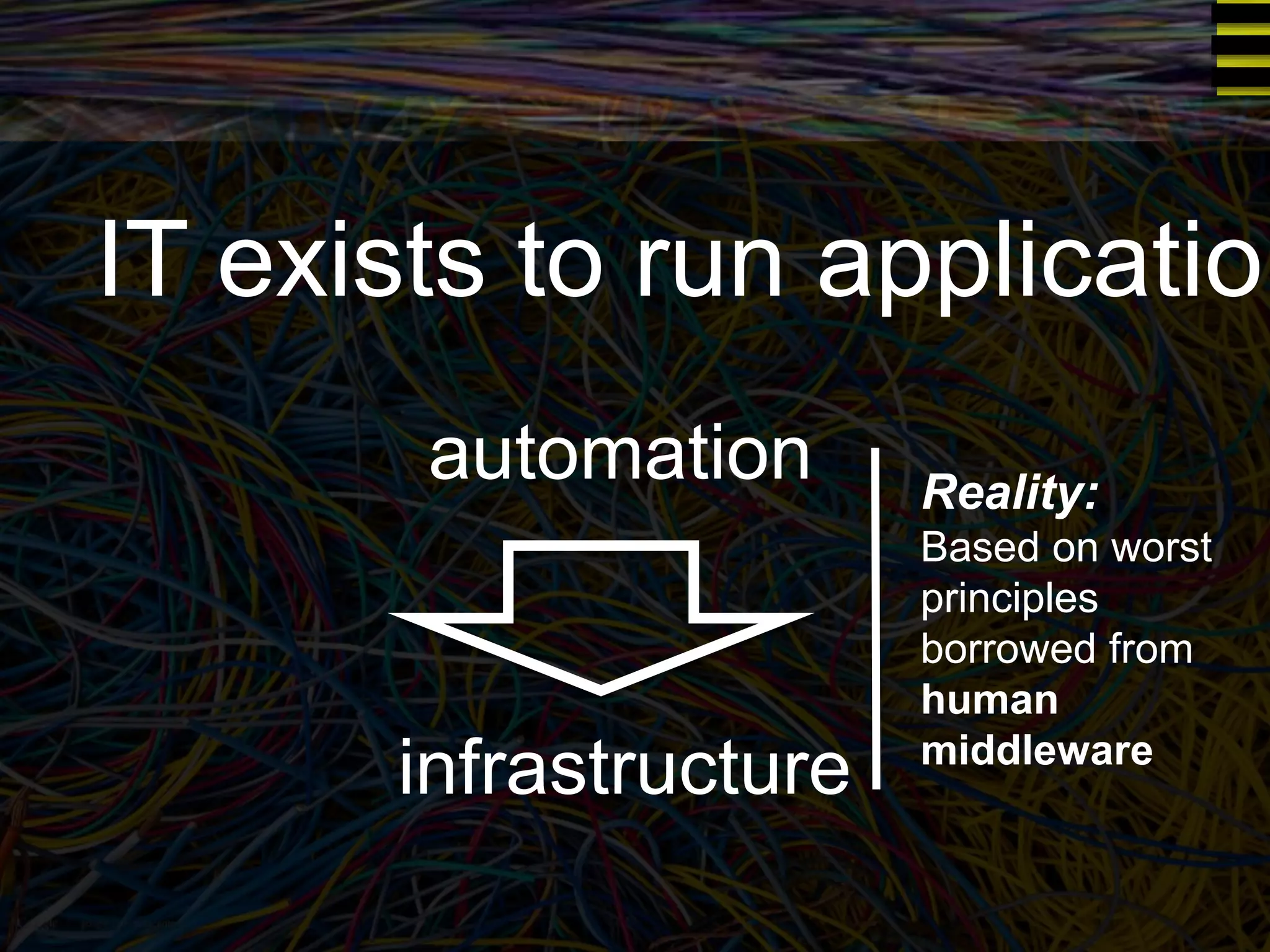
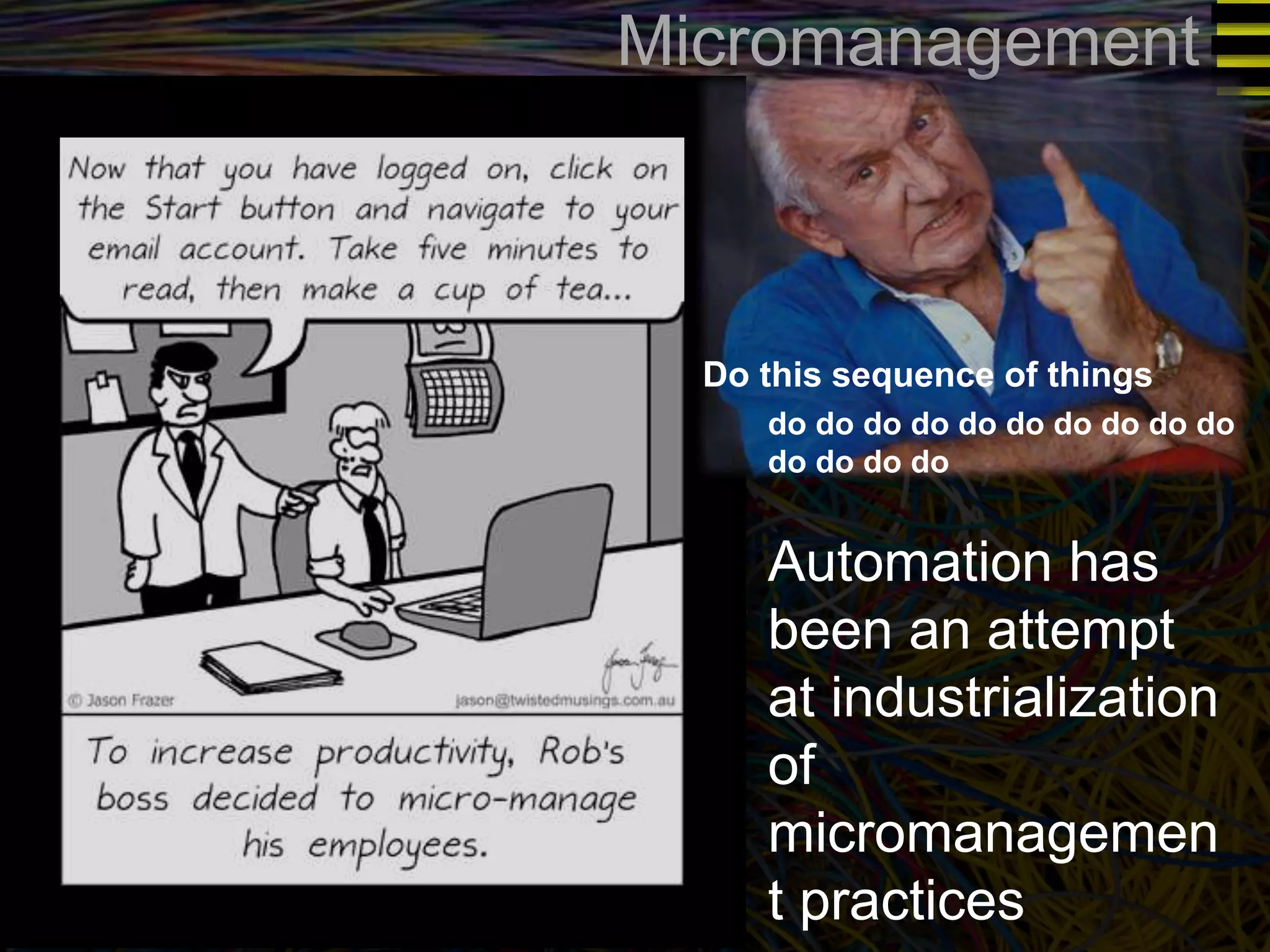
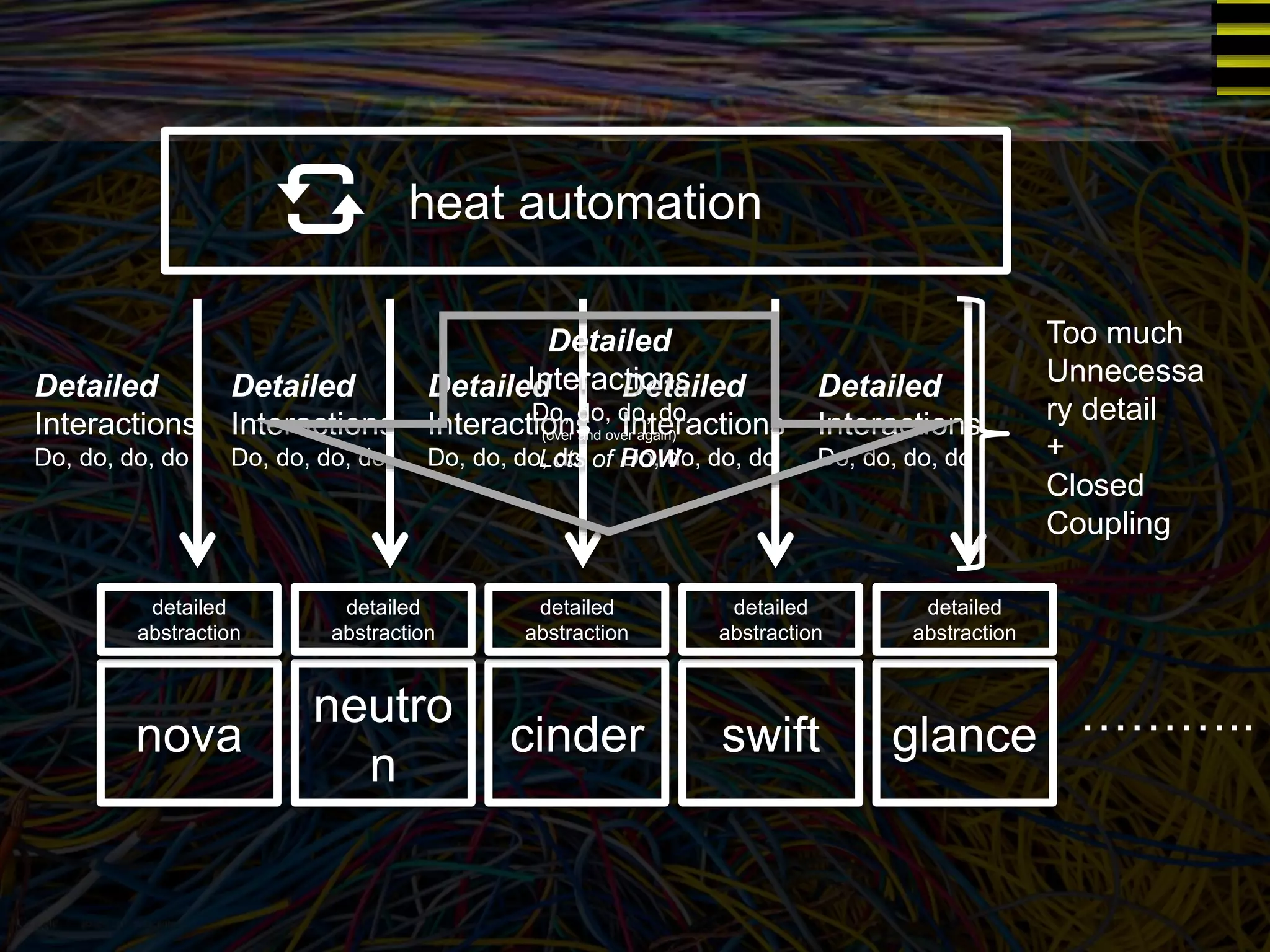
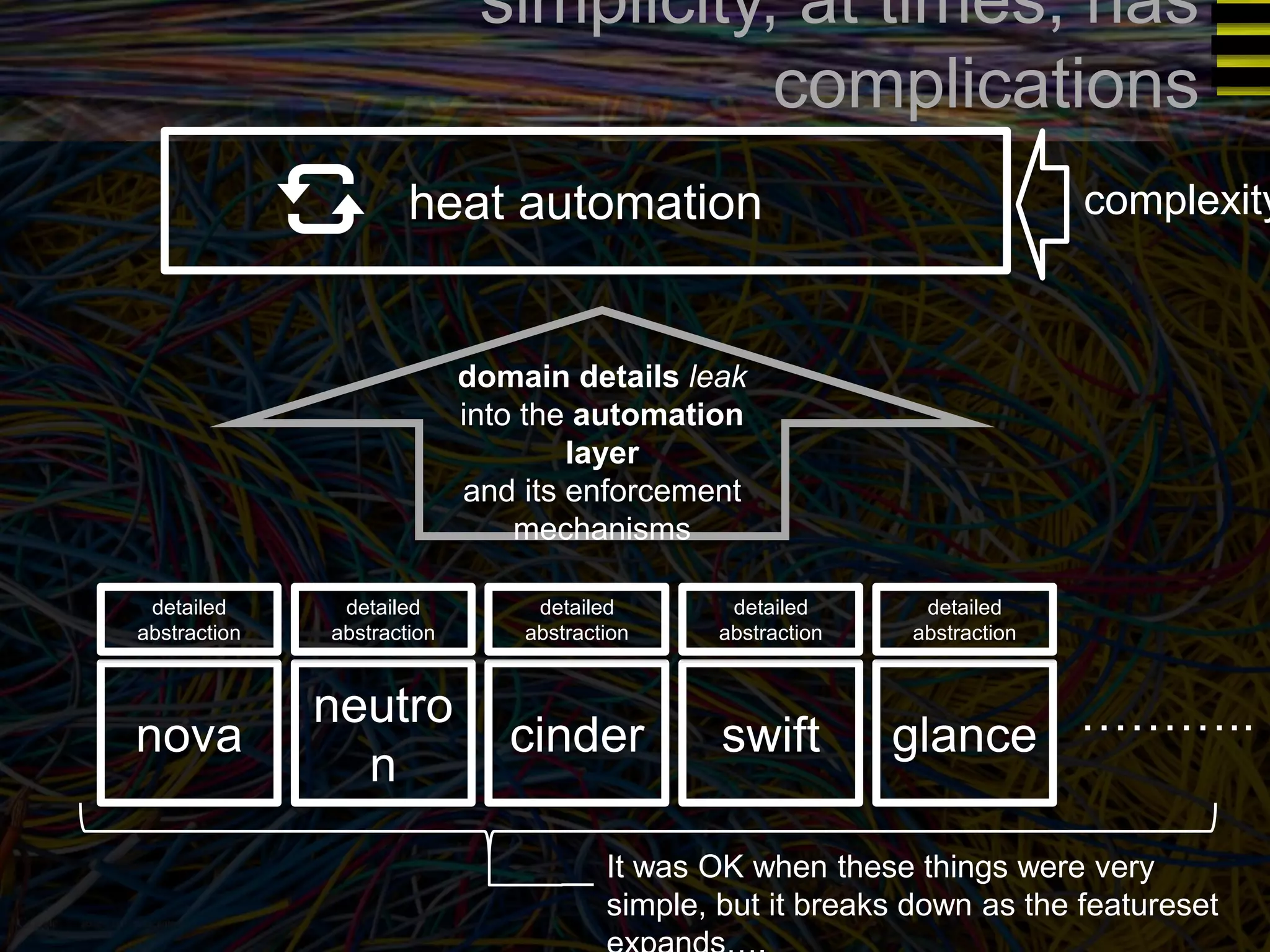
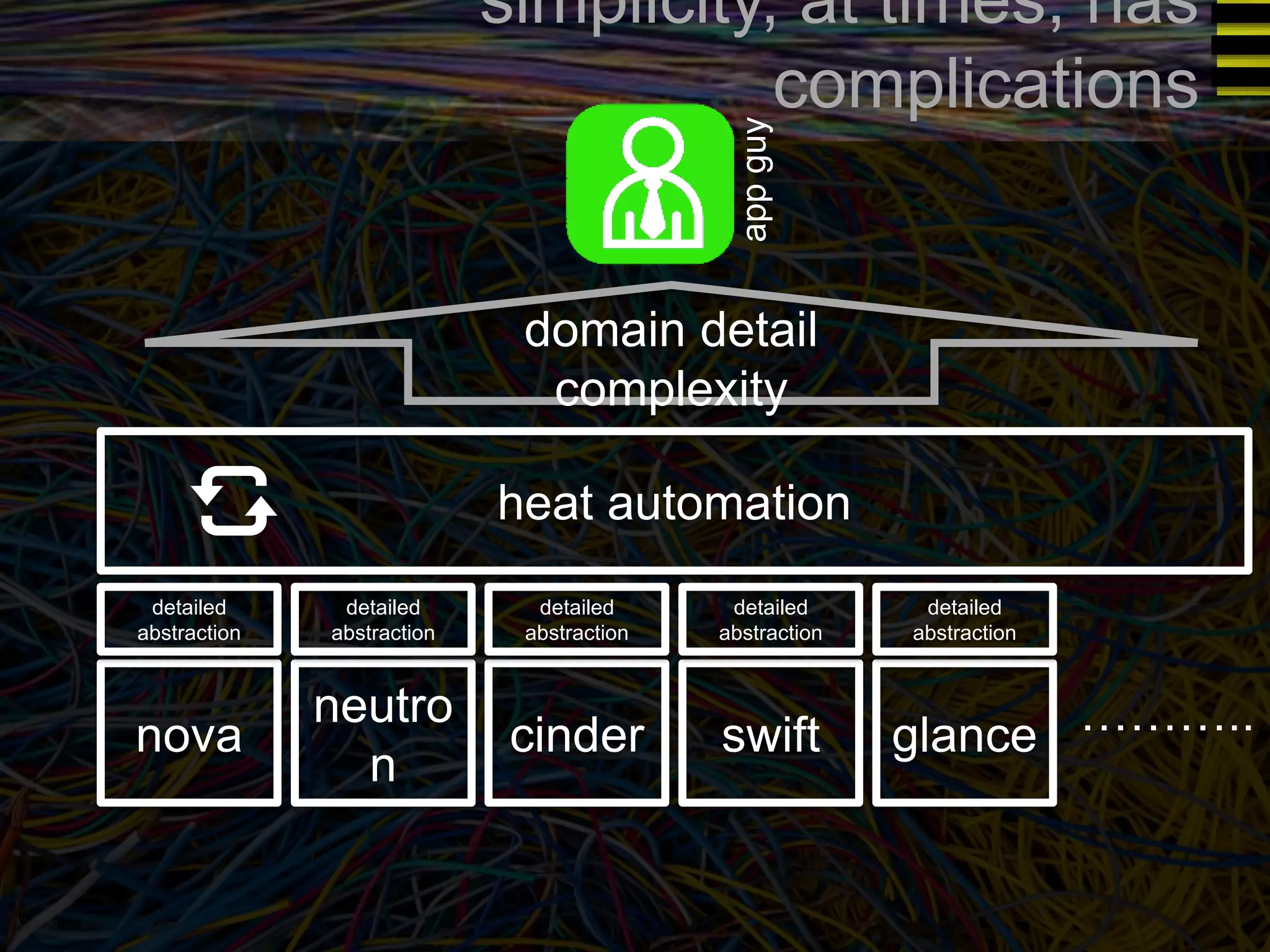
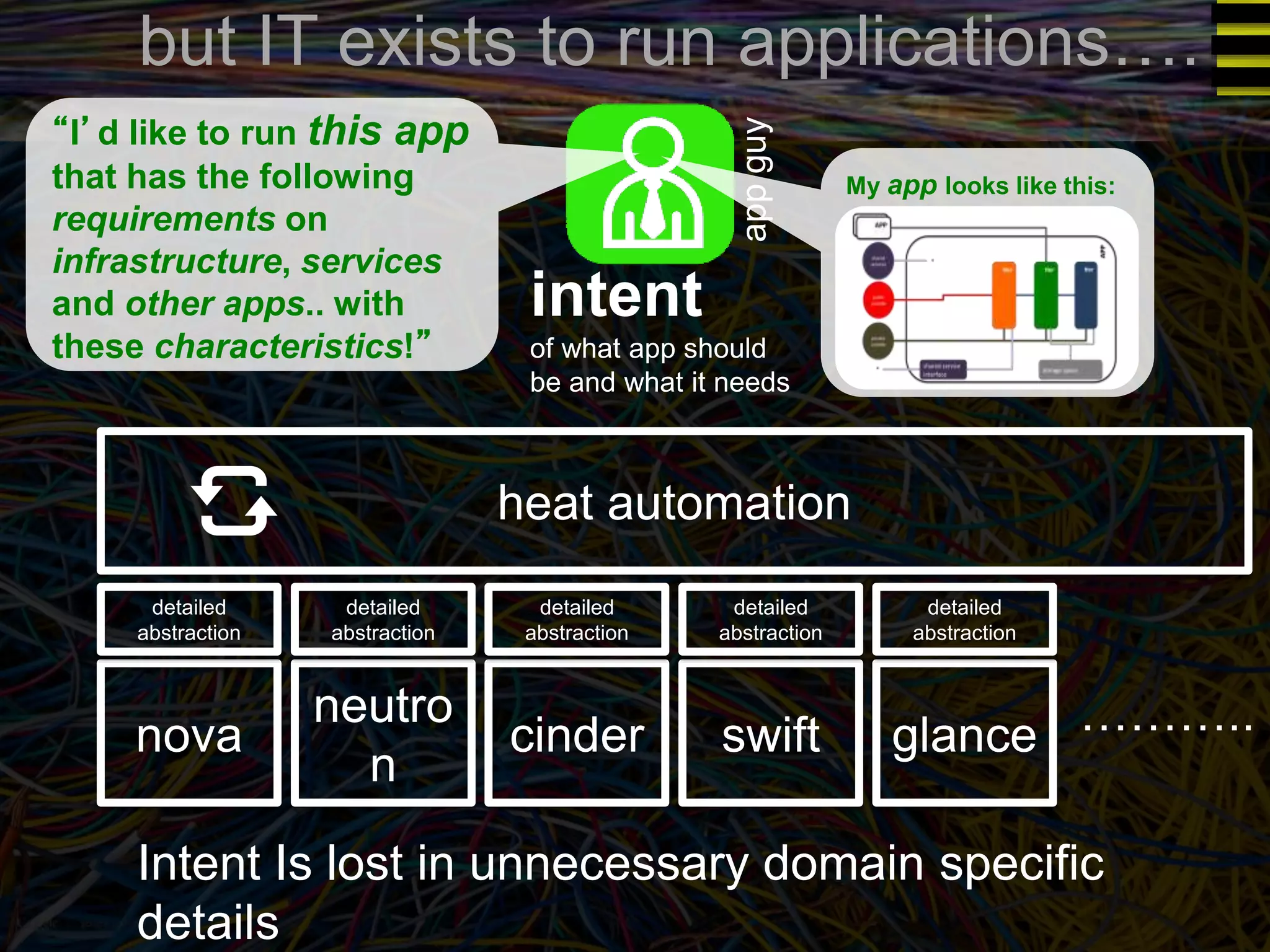
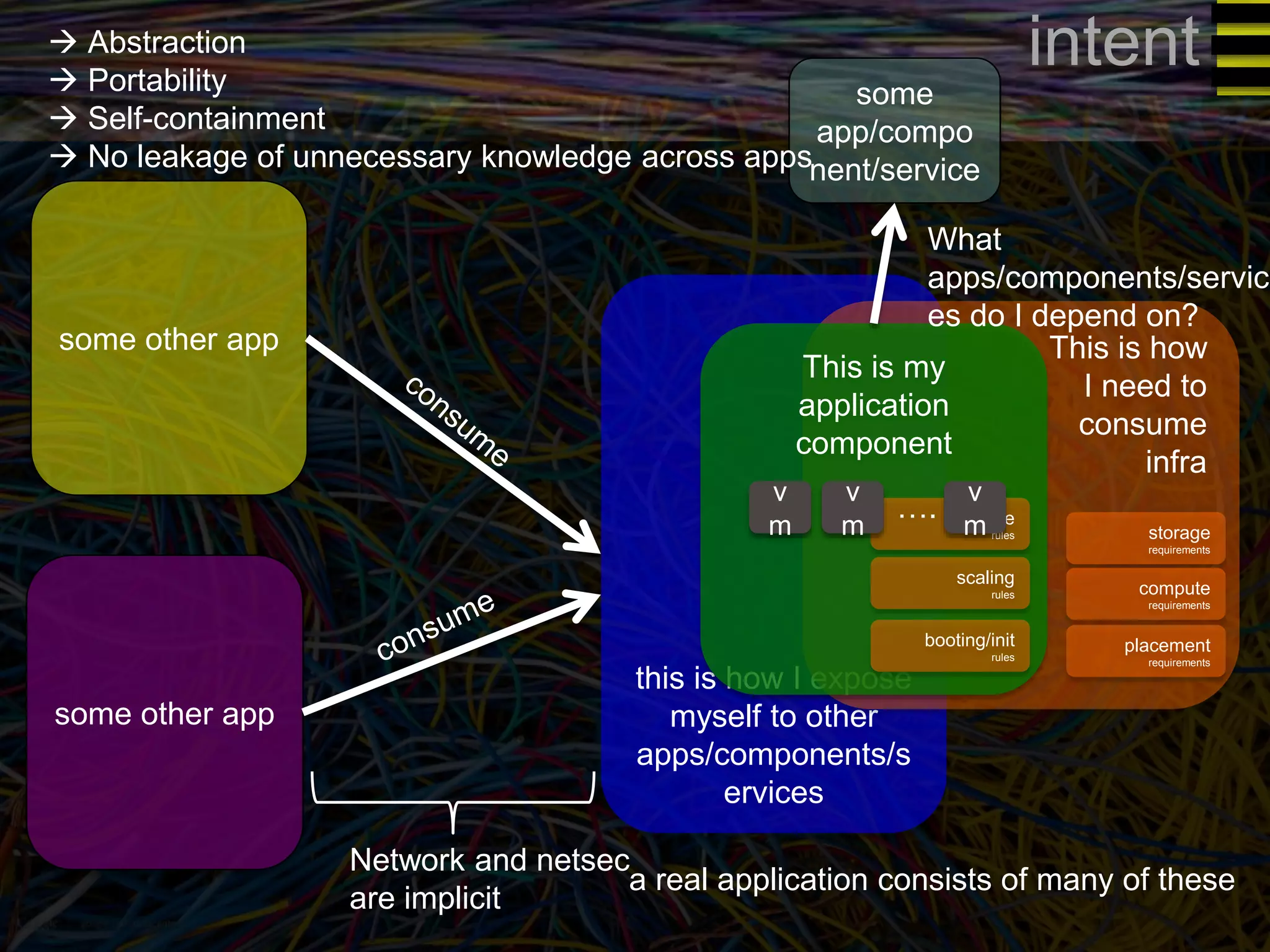
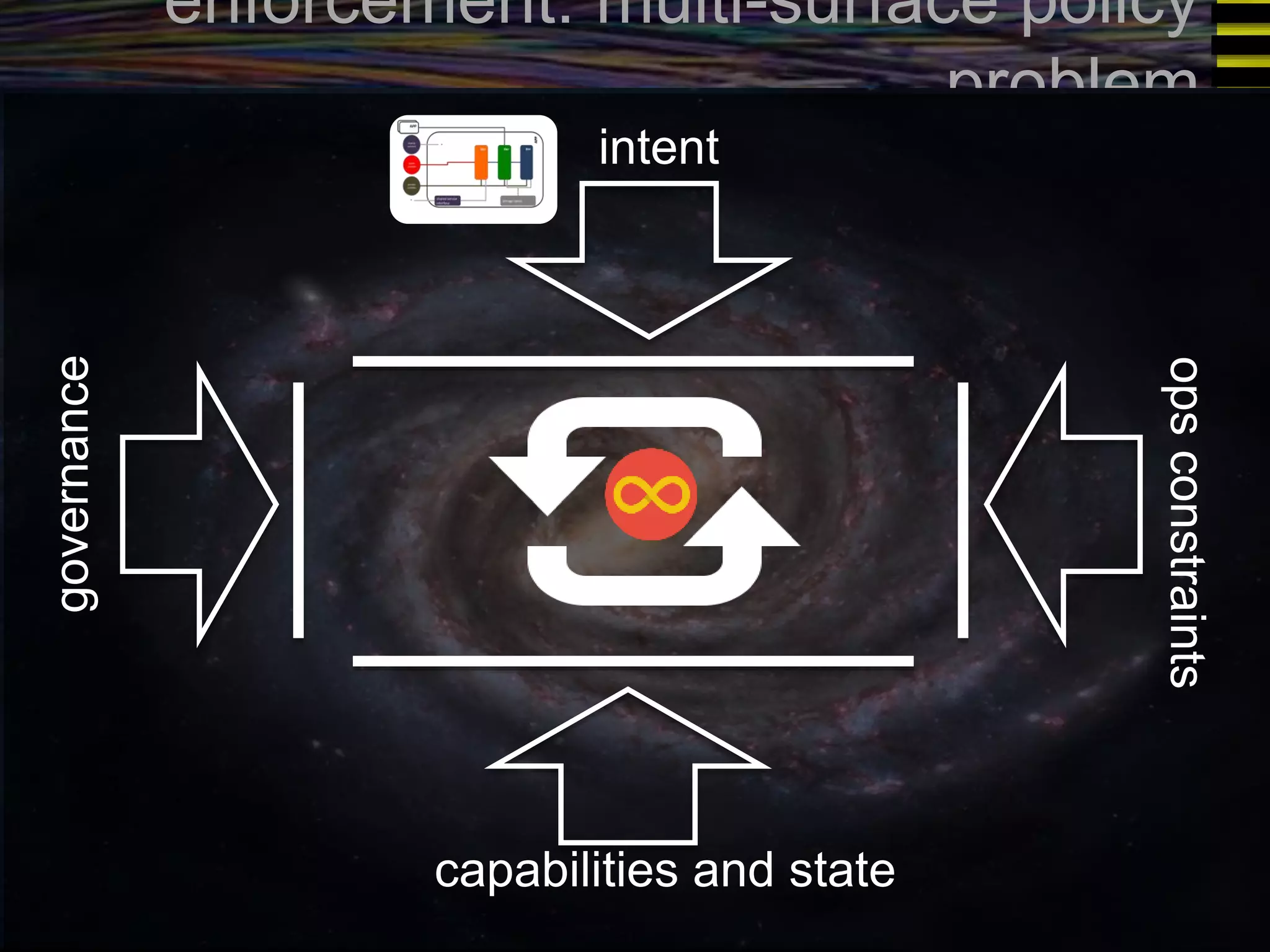
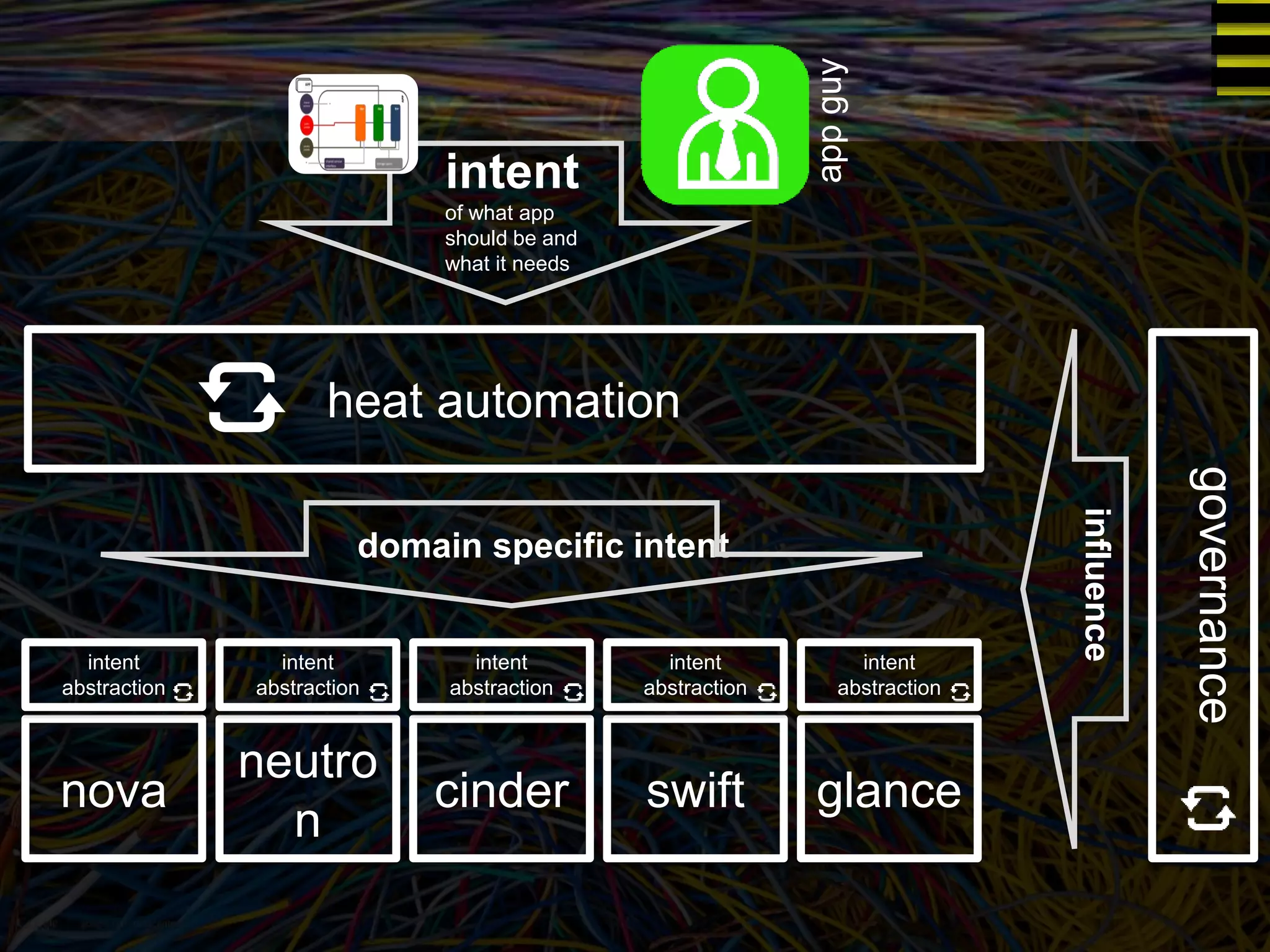
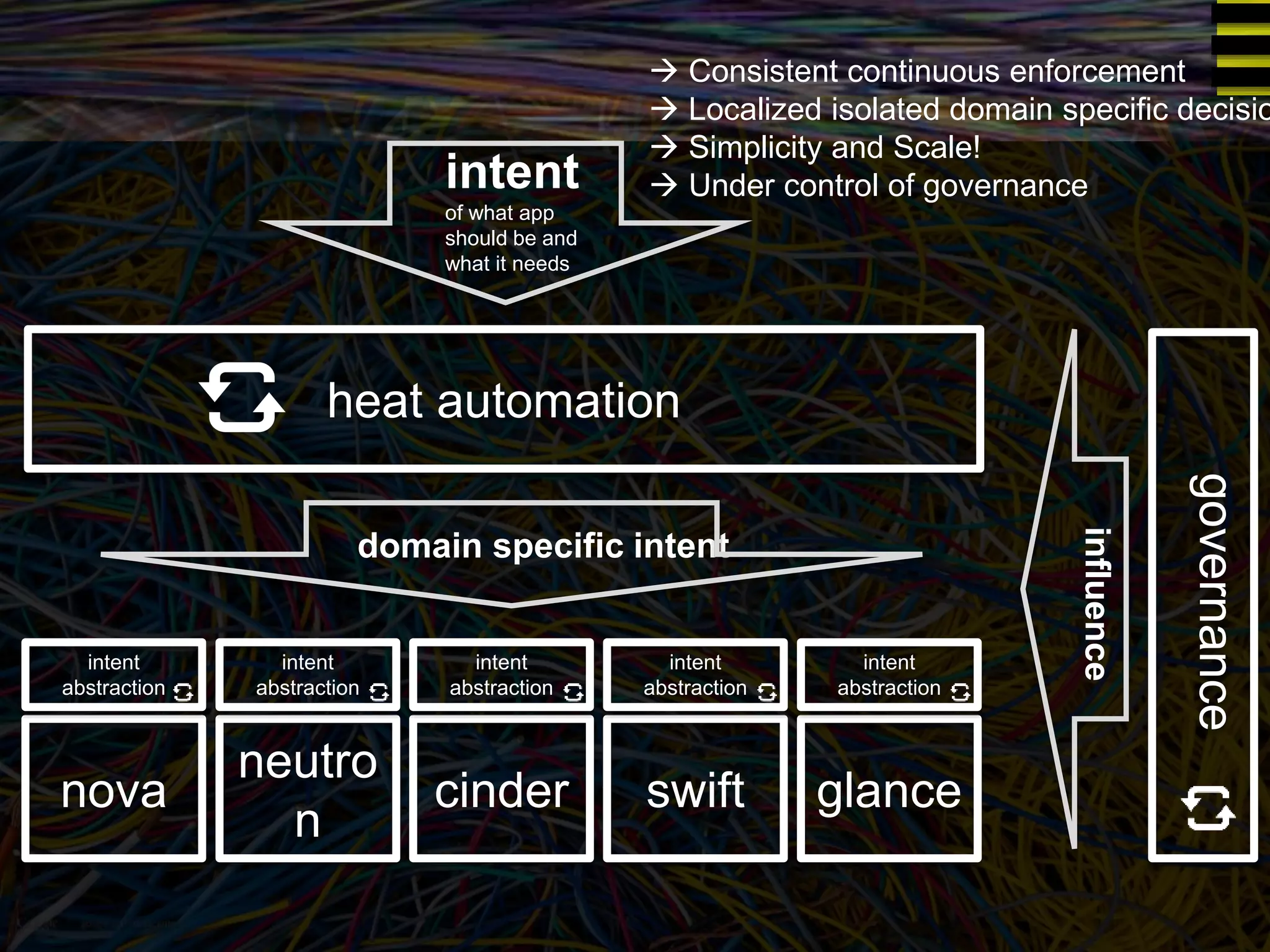
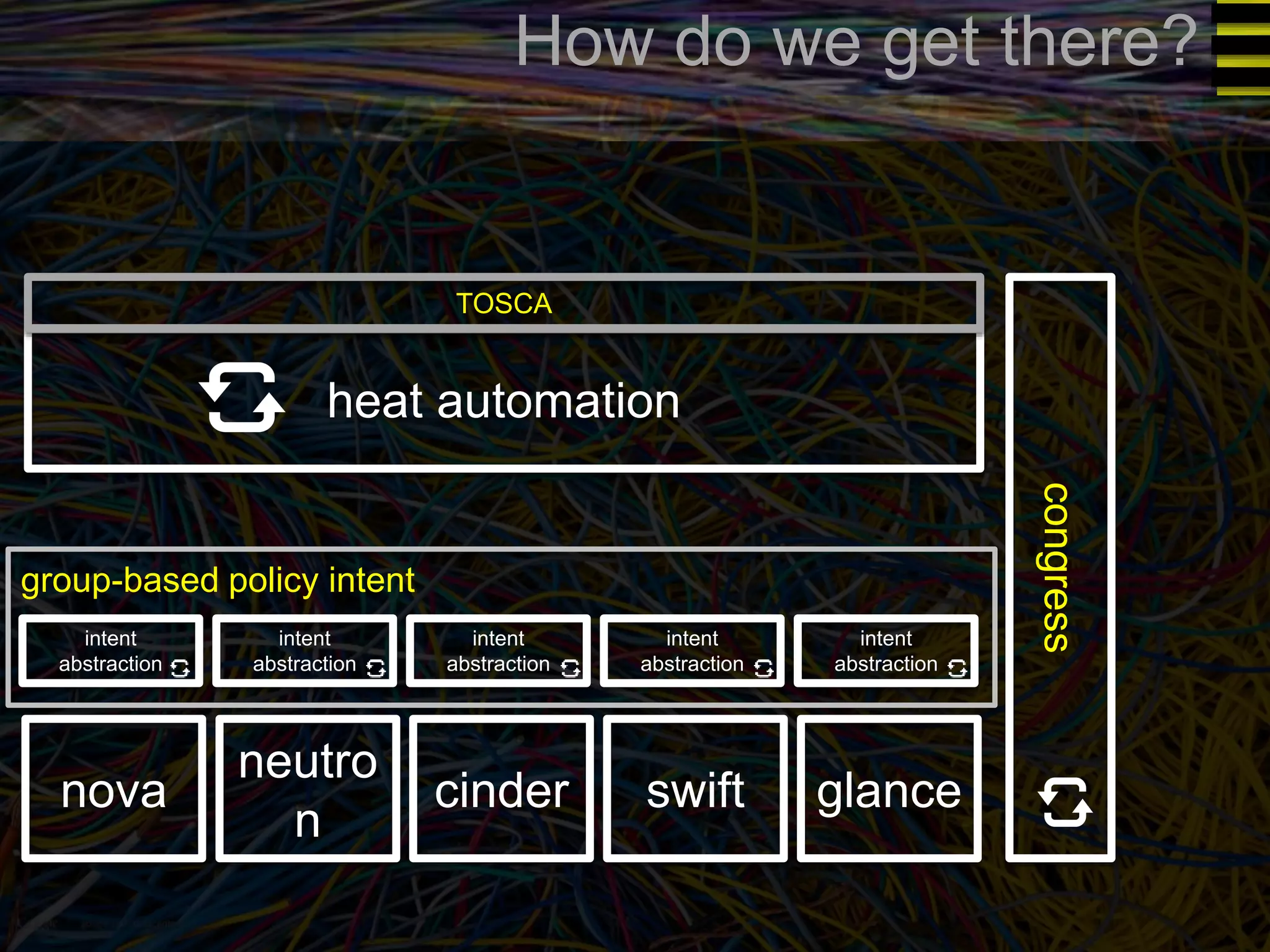
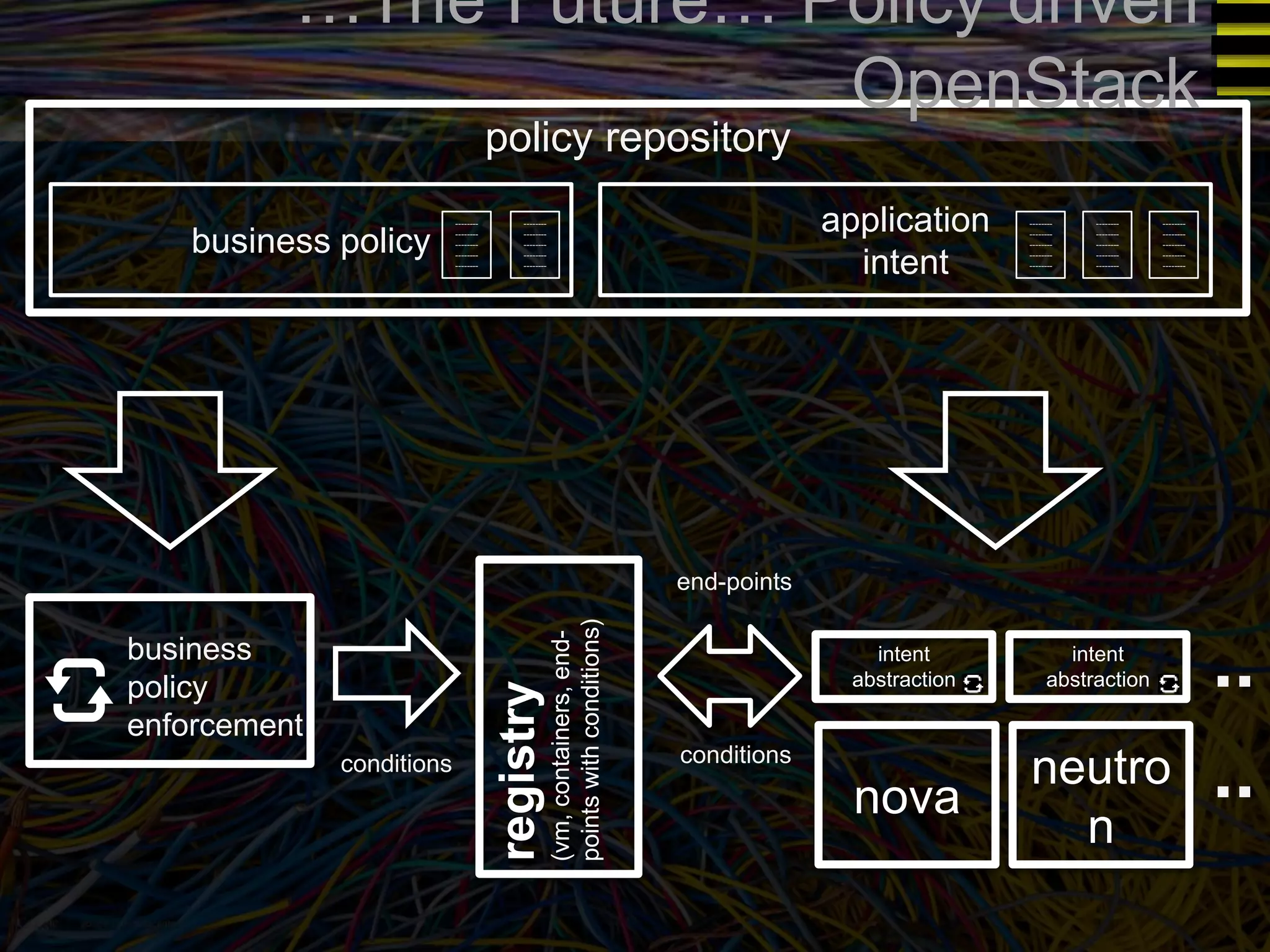
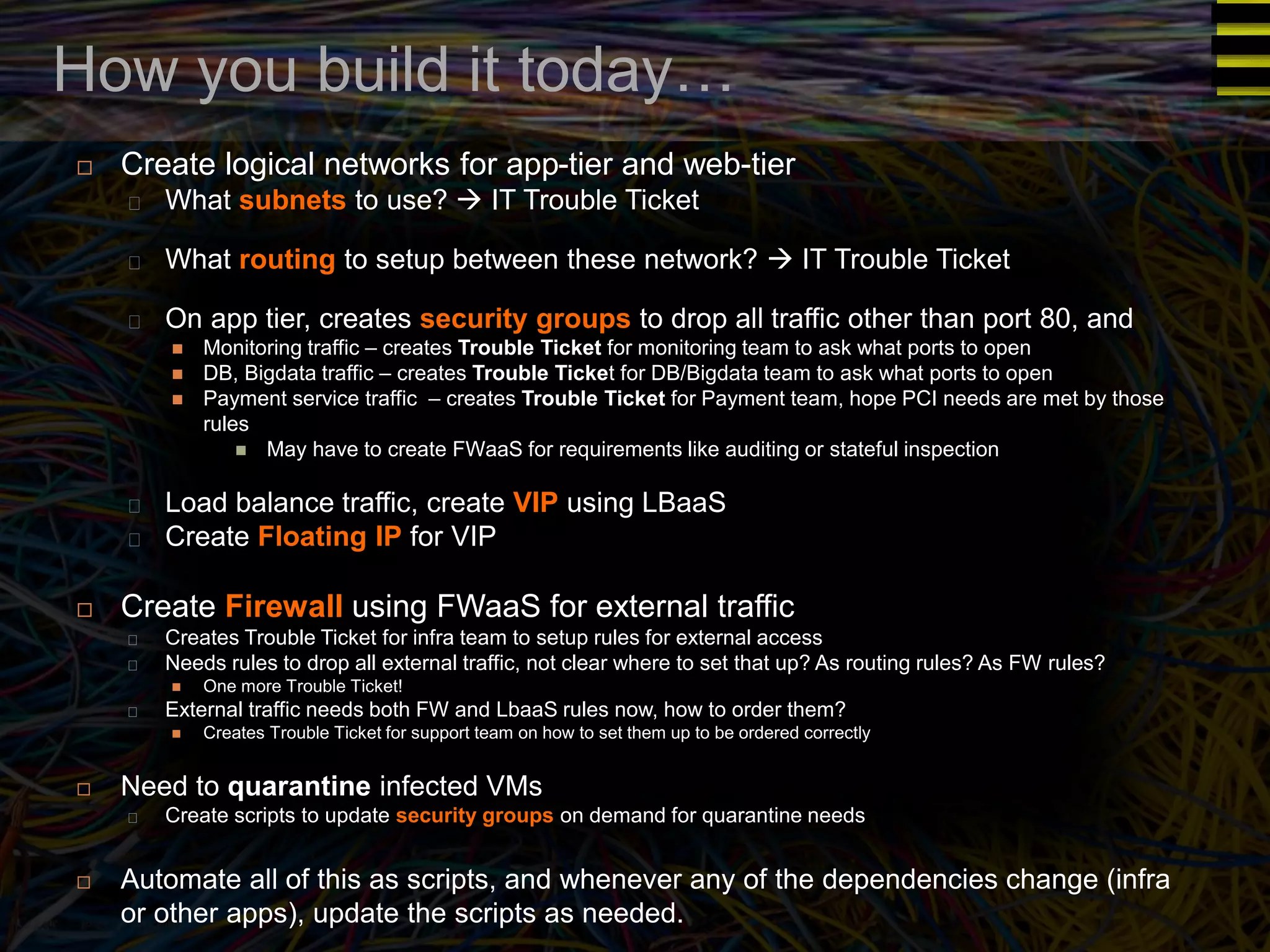
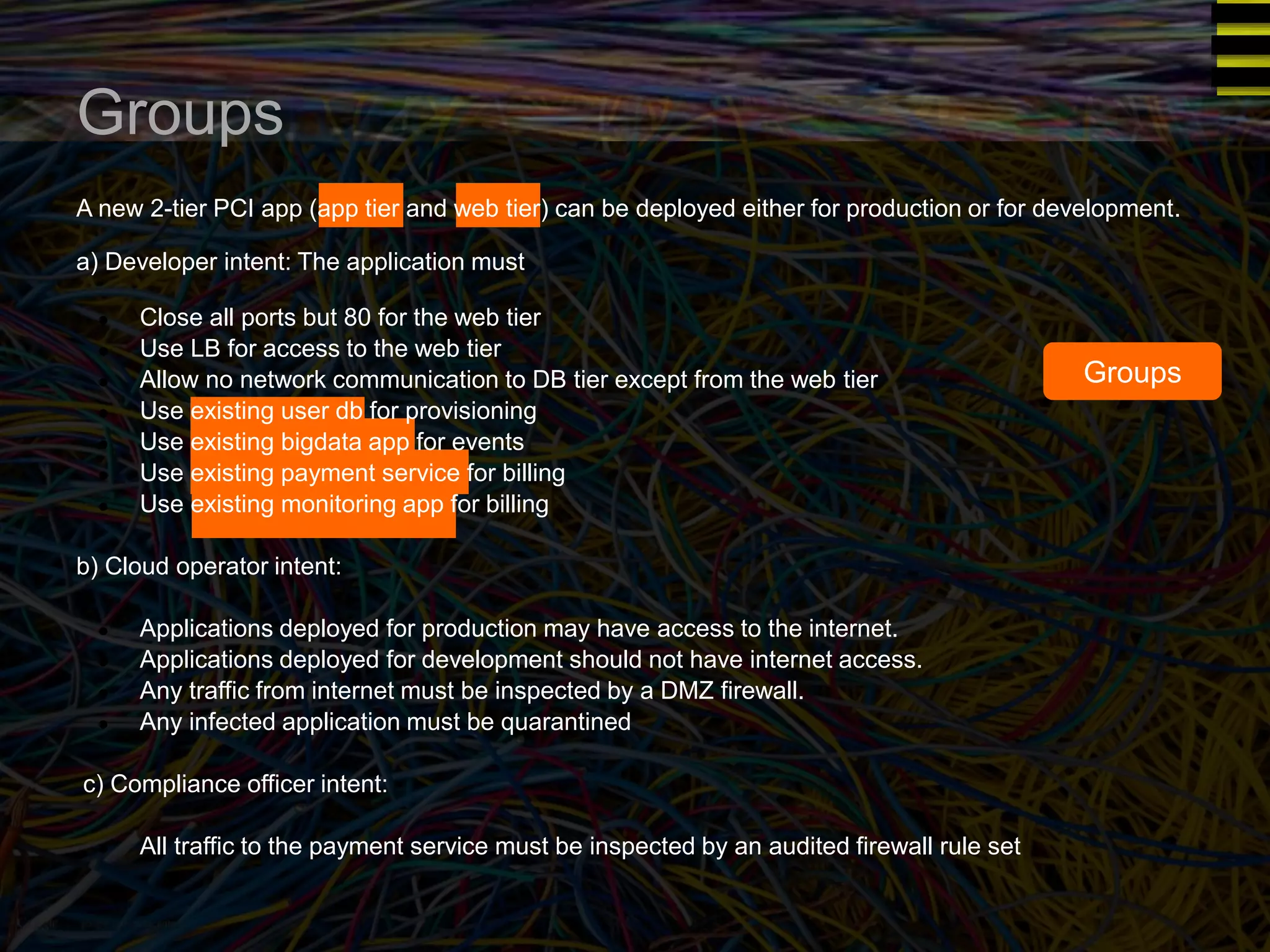
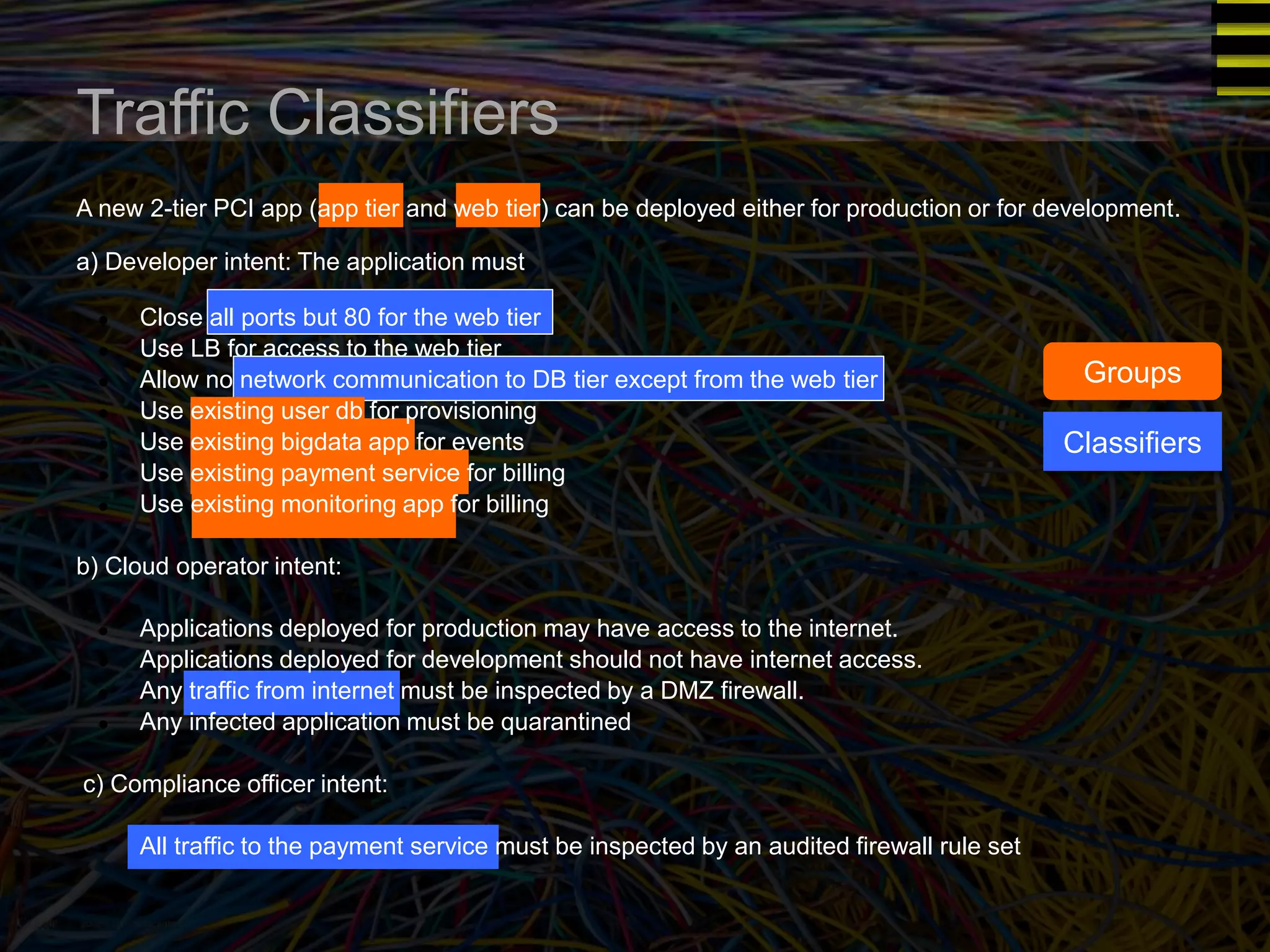
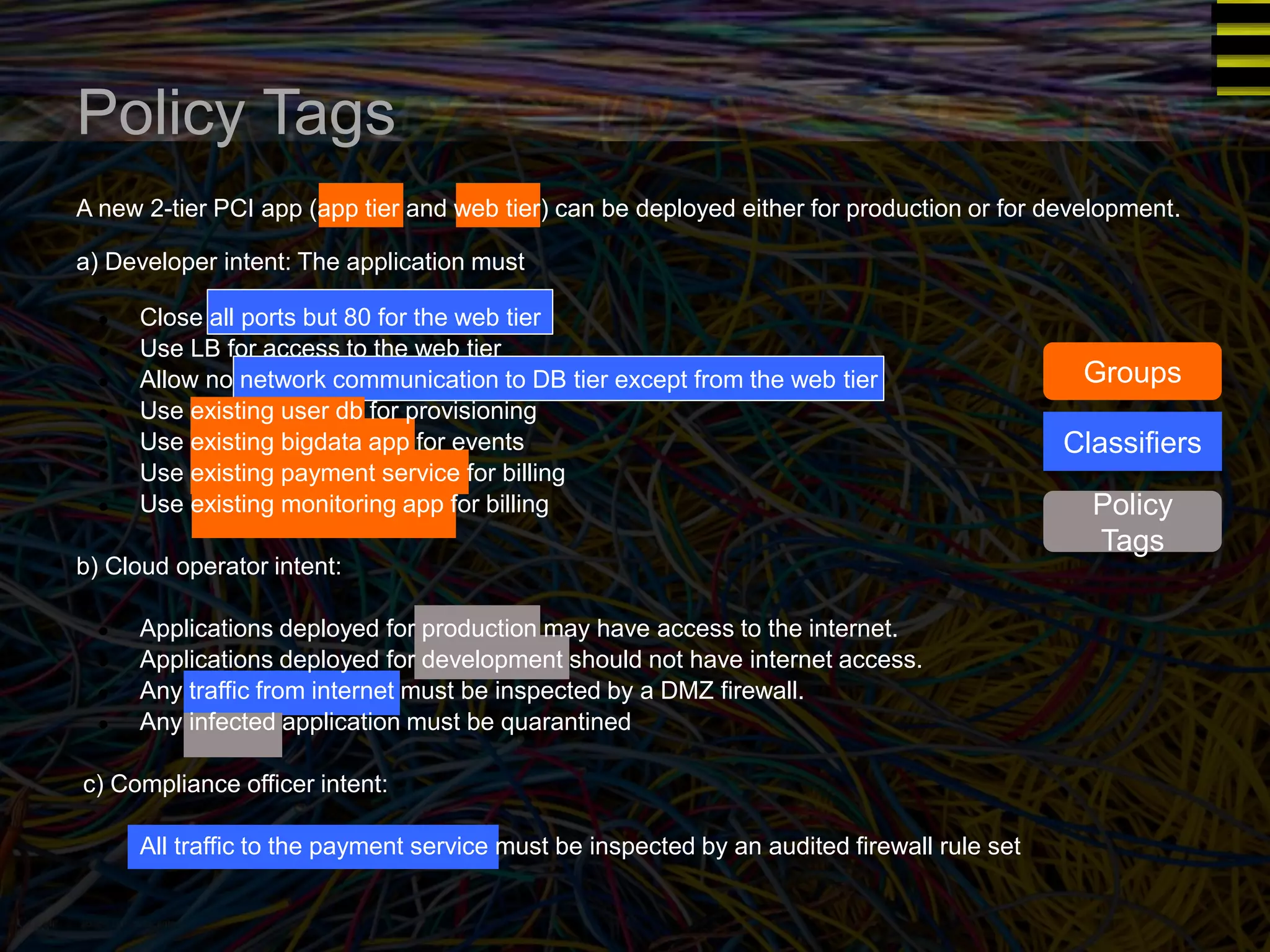
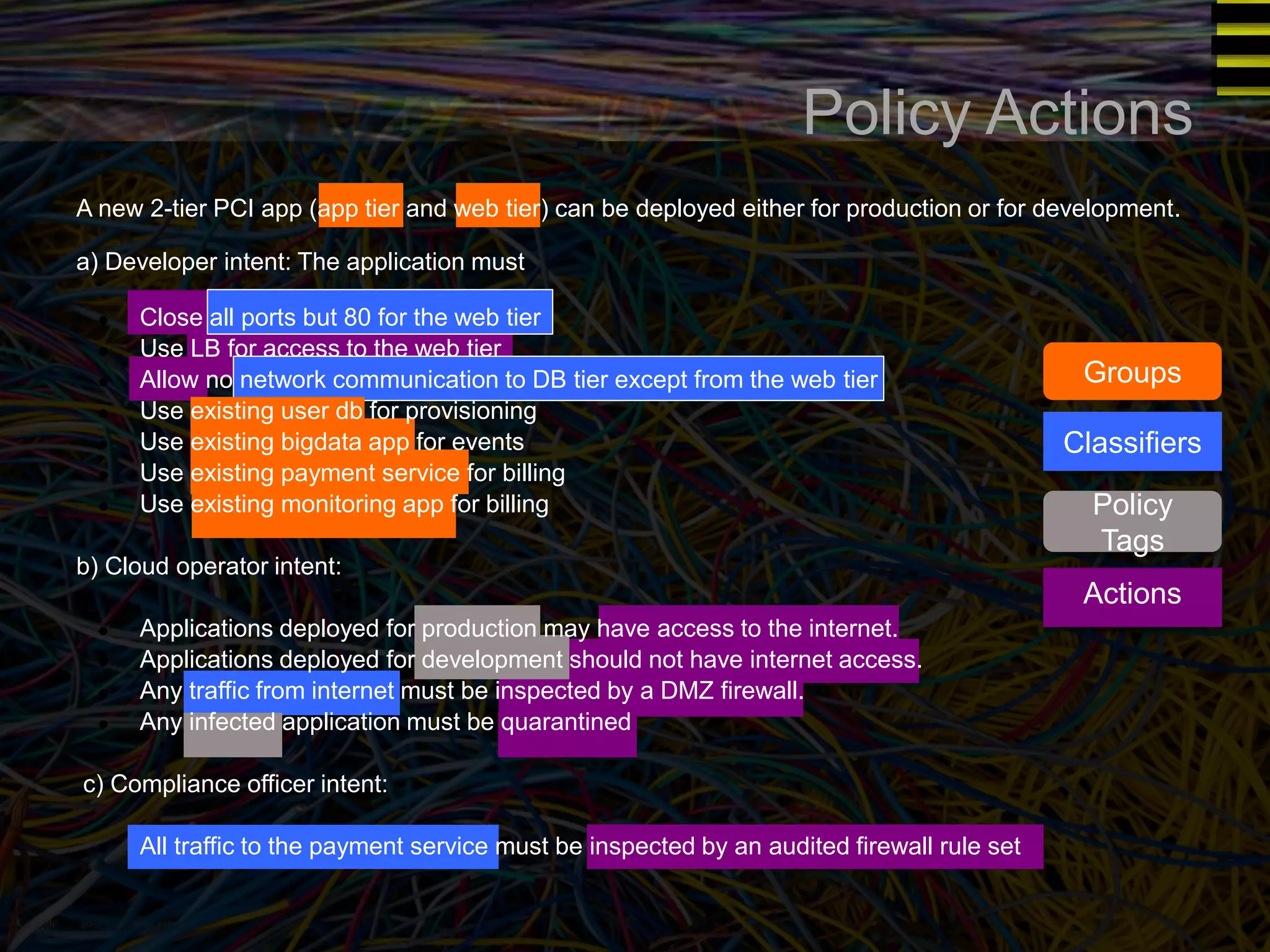
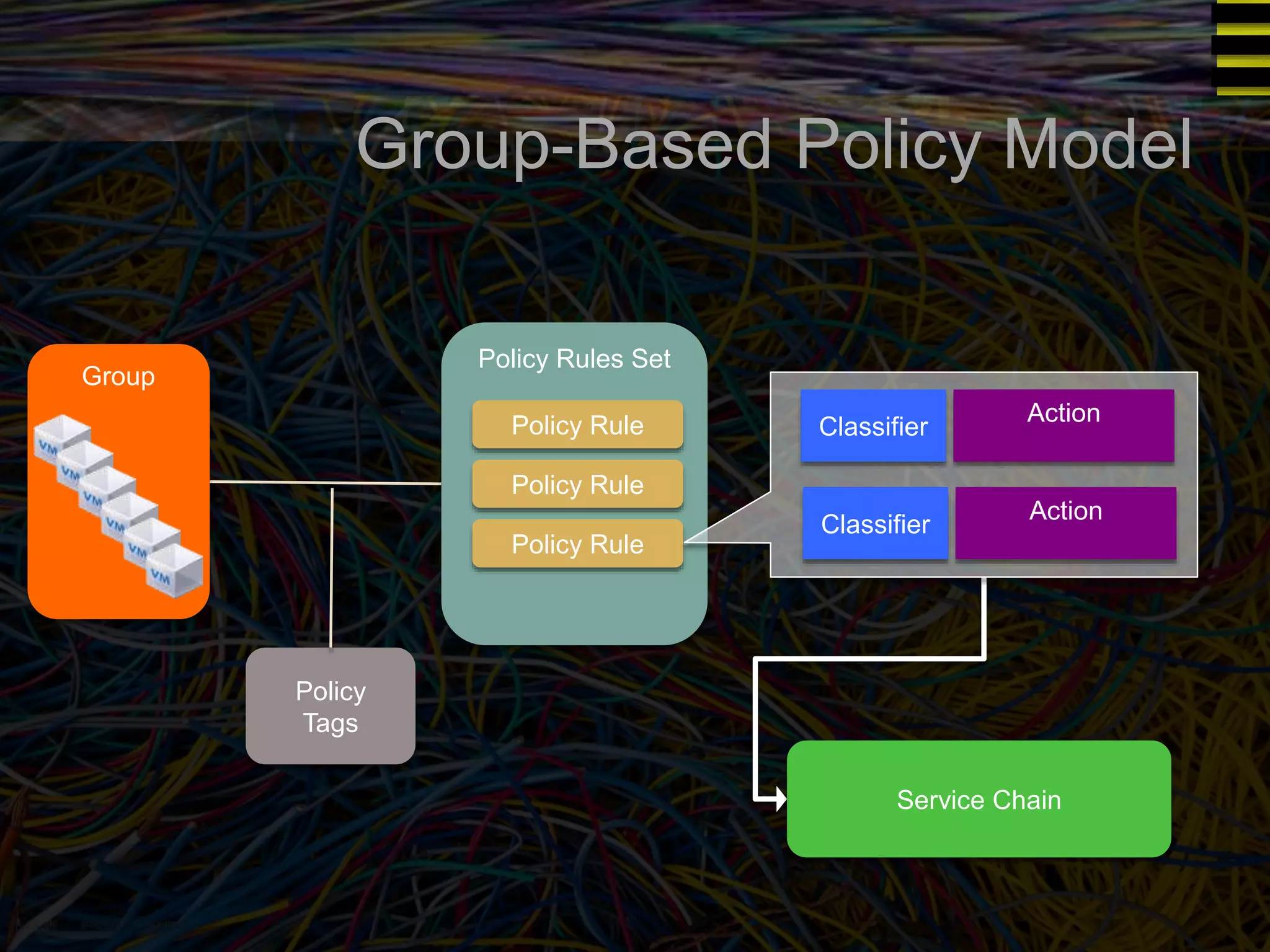
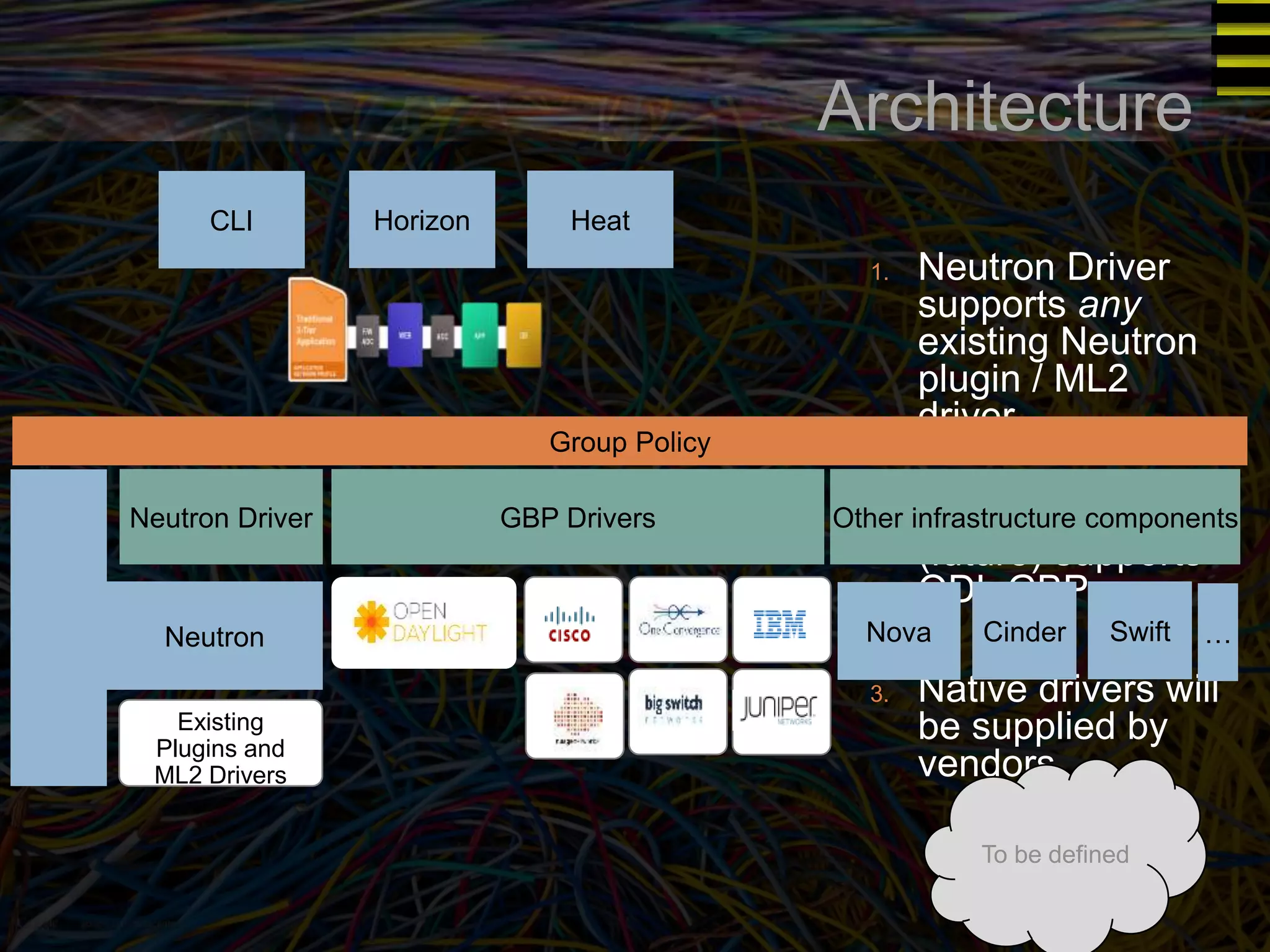
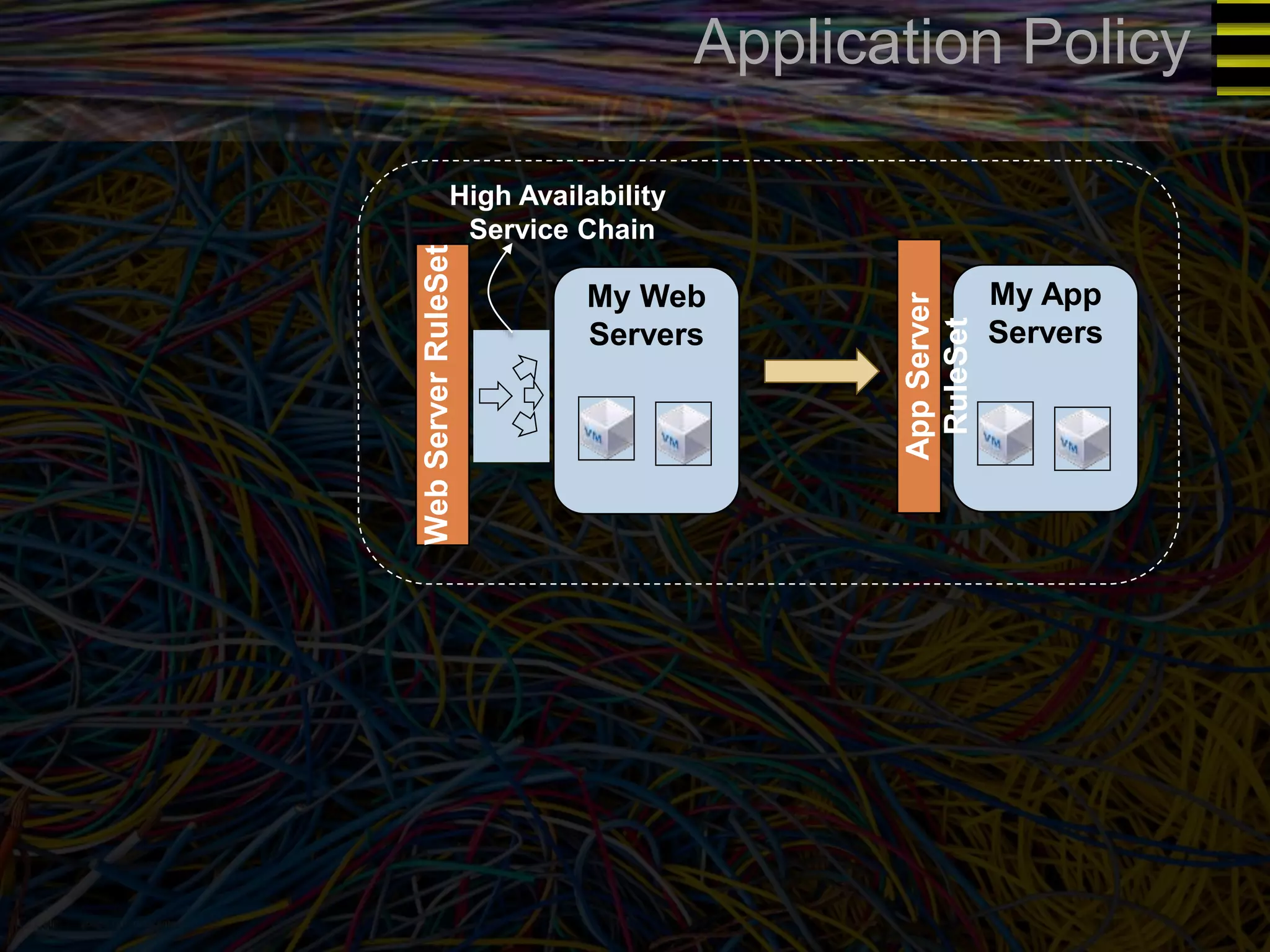
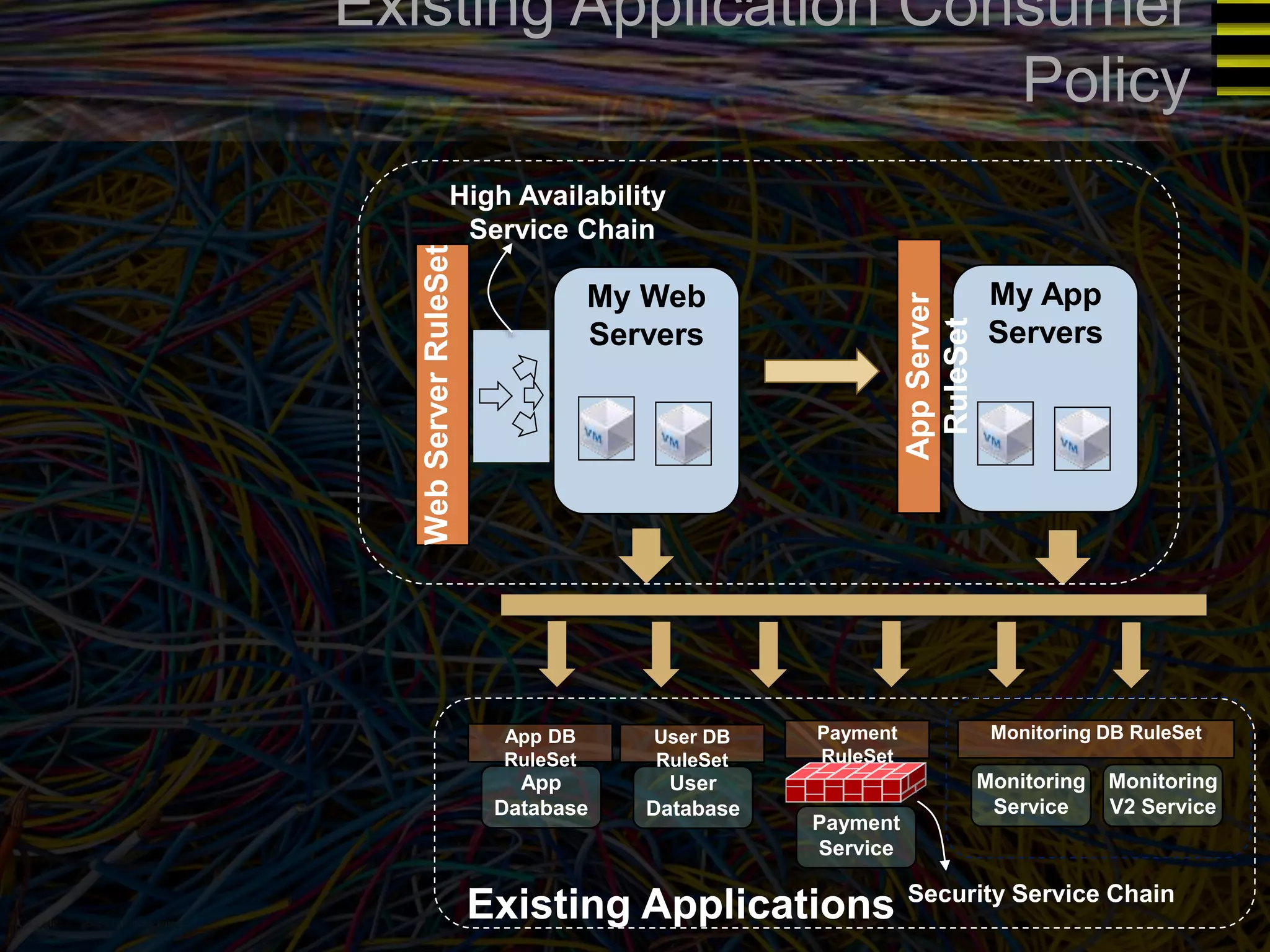
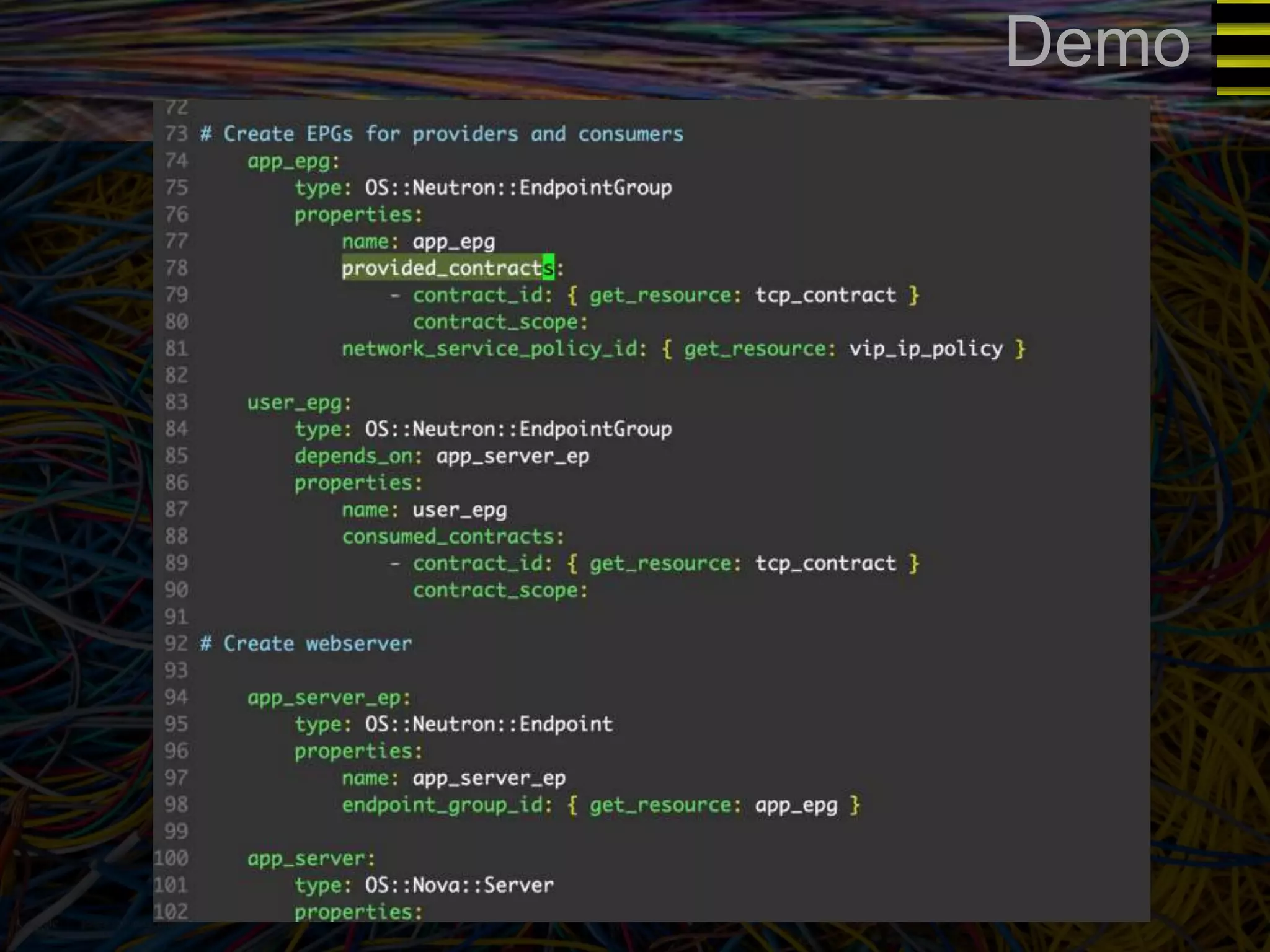
The document discusses a new approach to OpenStack automation called Group-Based Policy (GBP). GBP aims to capture an application's infrastructure needs at a higher level of abstraction, independent of the underlying implementation details. It introduces several new concepts, including groups to organize resources, traffic classifiers to define network traffic, and policy tags to apply governance rules. The goal is for applications to simply describe their requirements and dependencies rather than having to specify low-level configuration details.