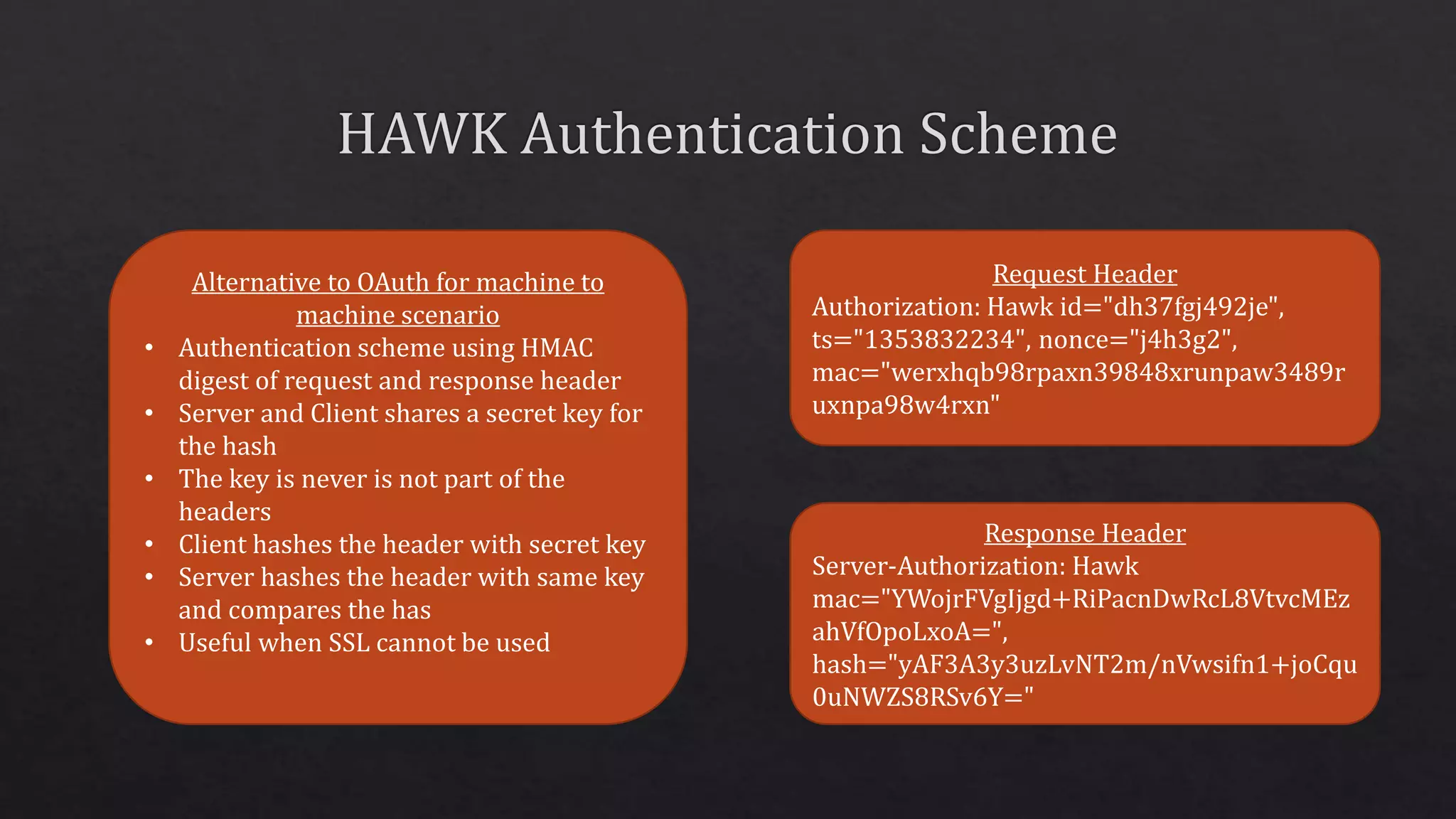
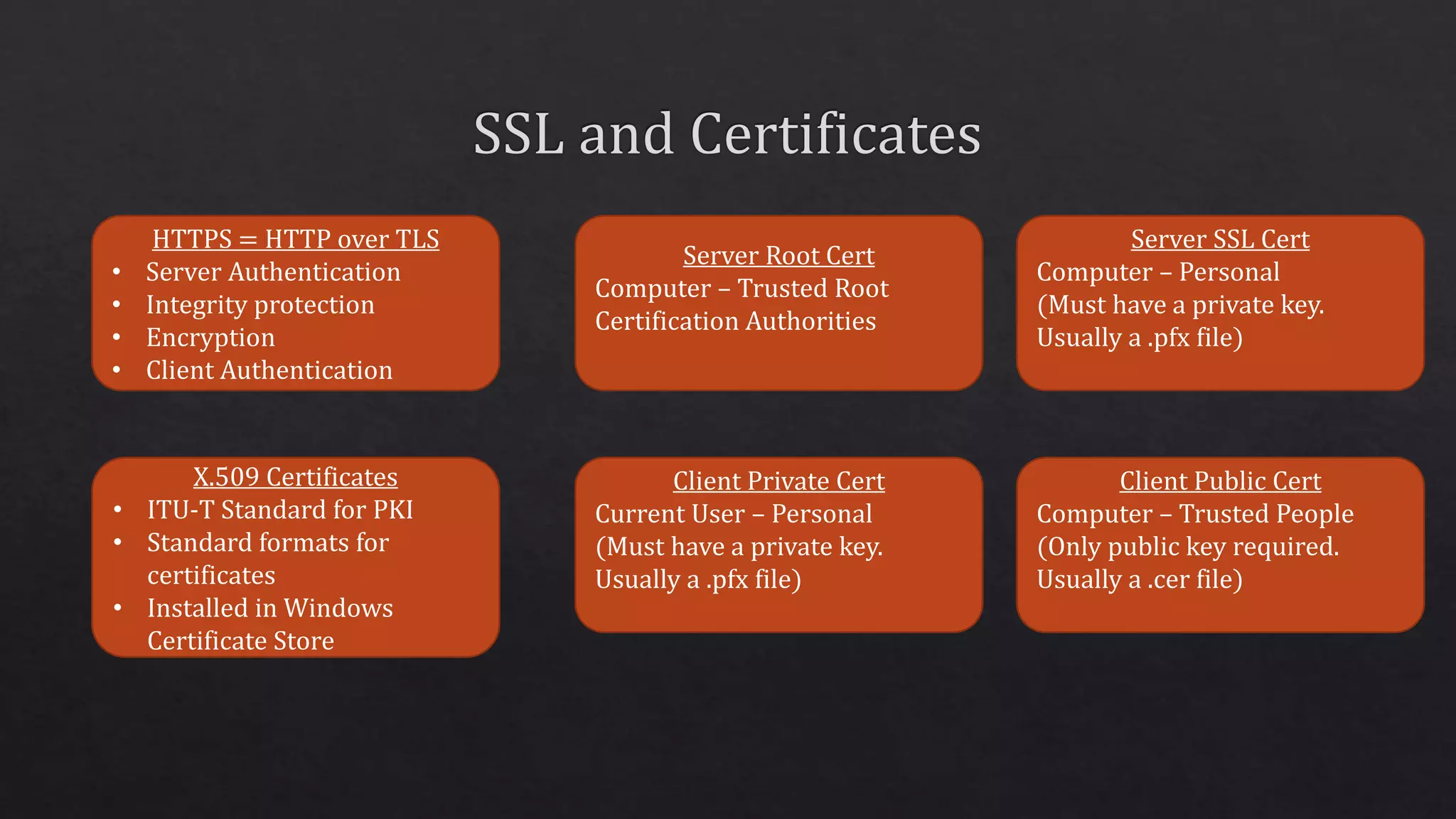
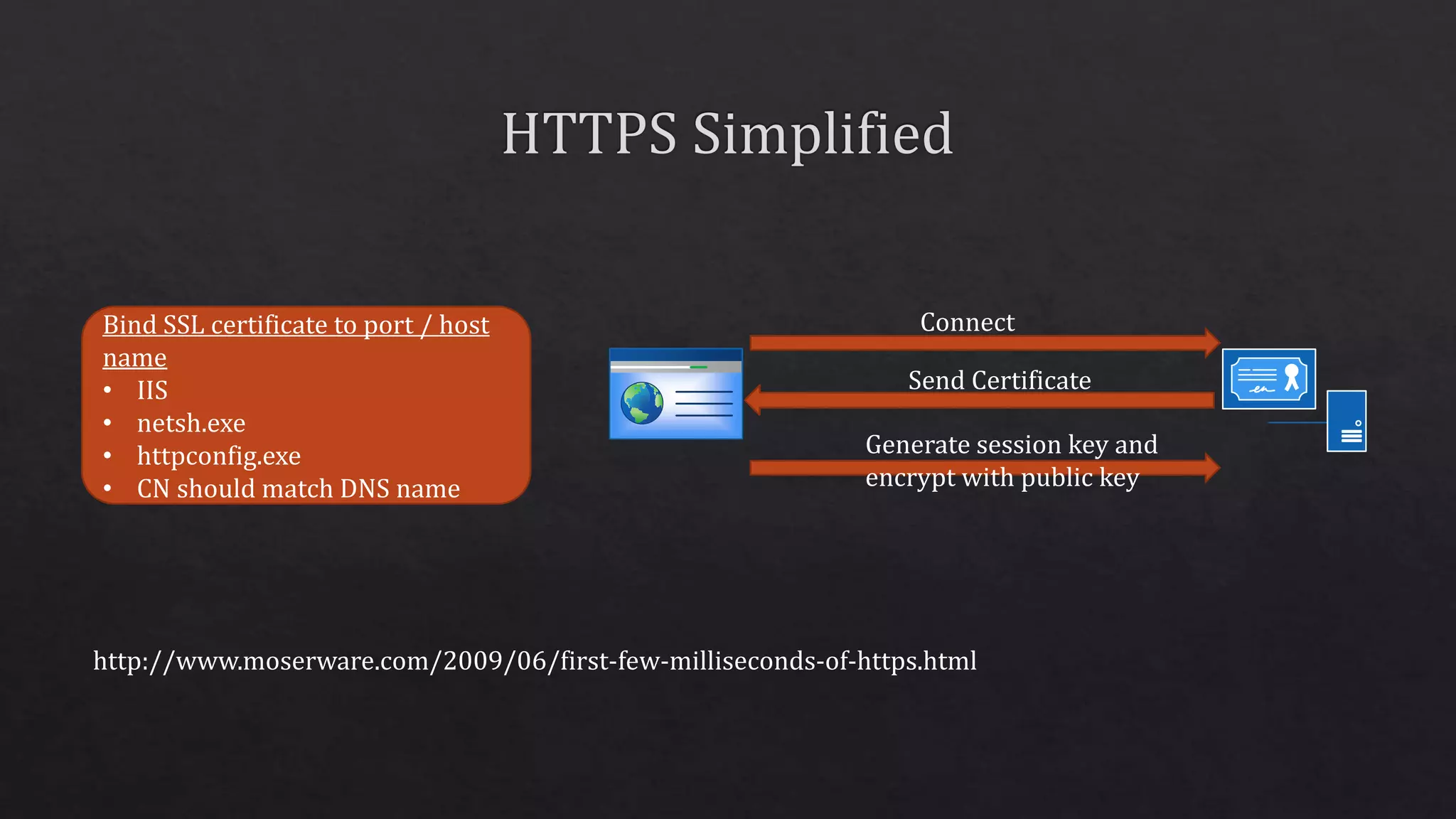
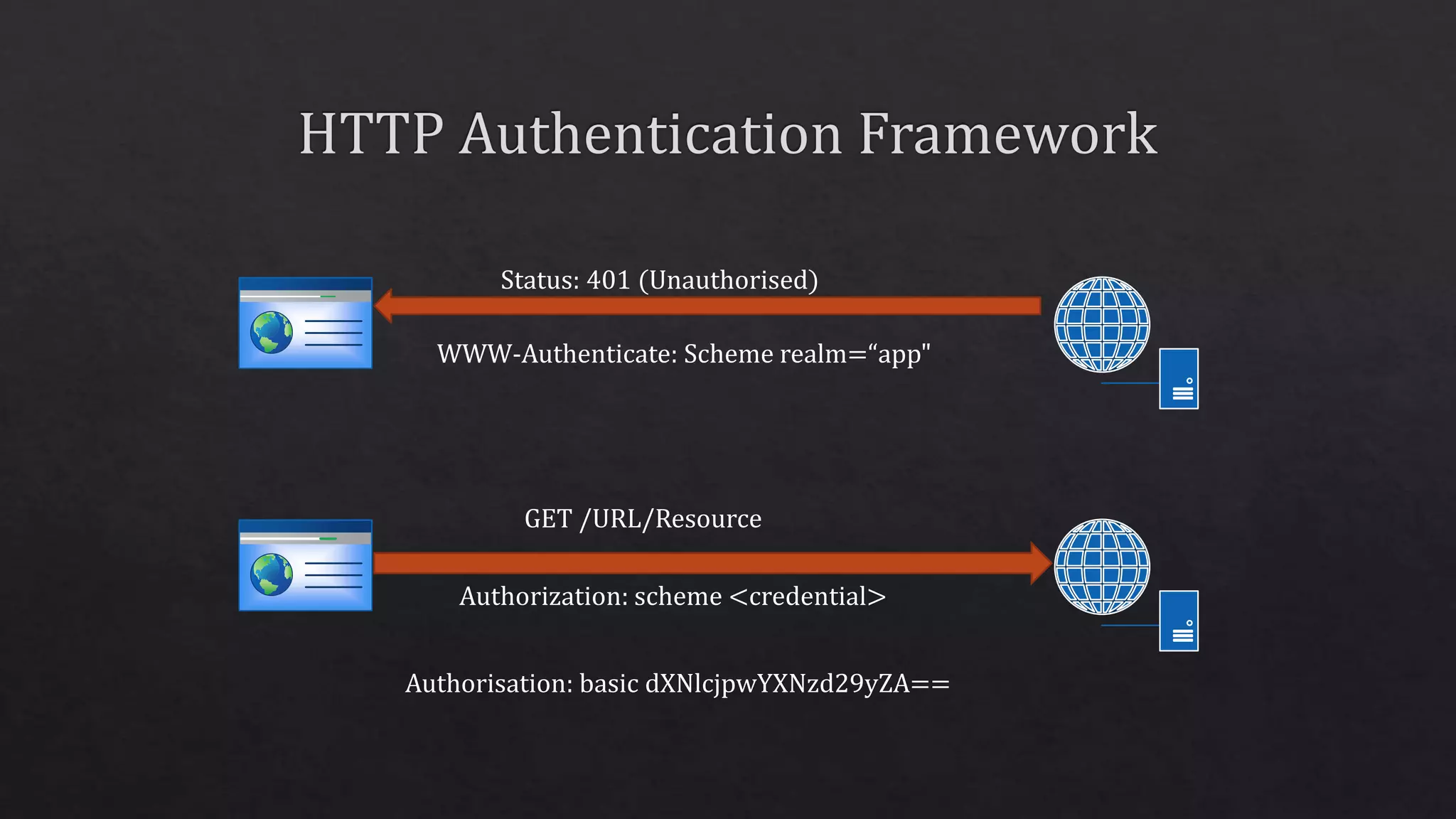
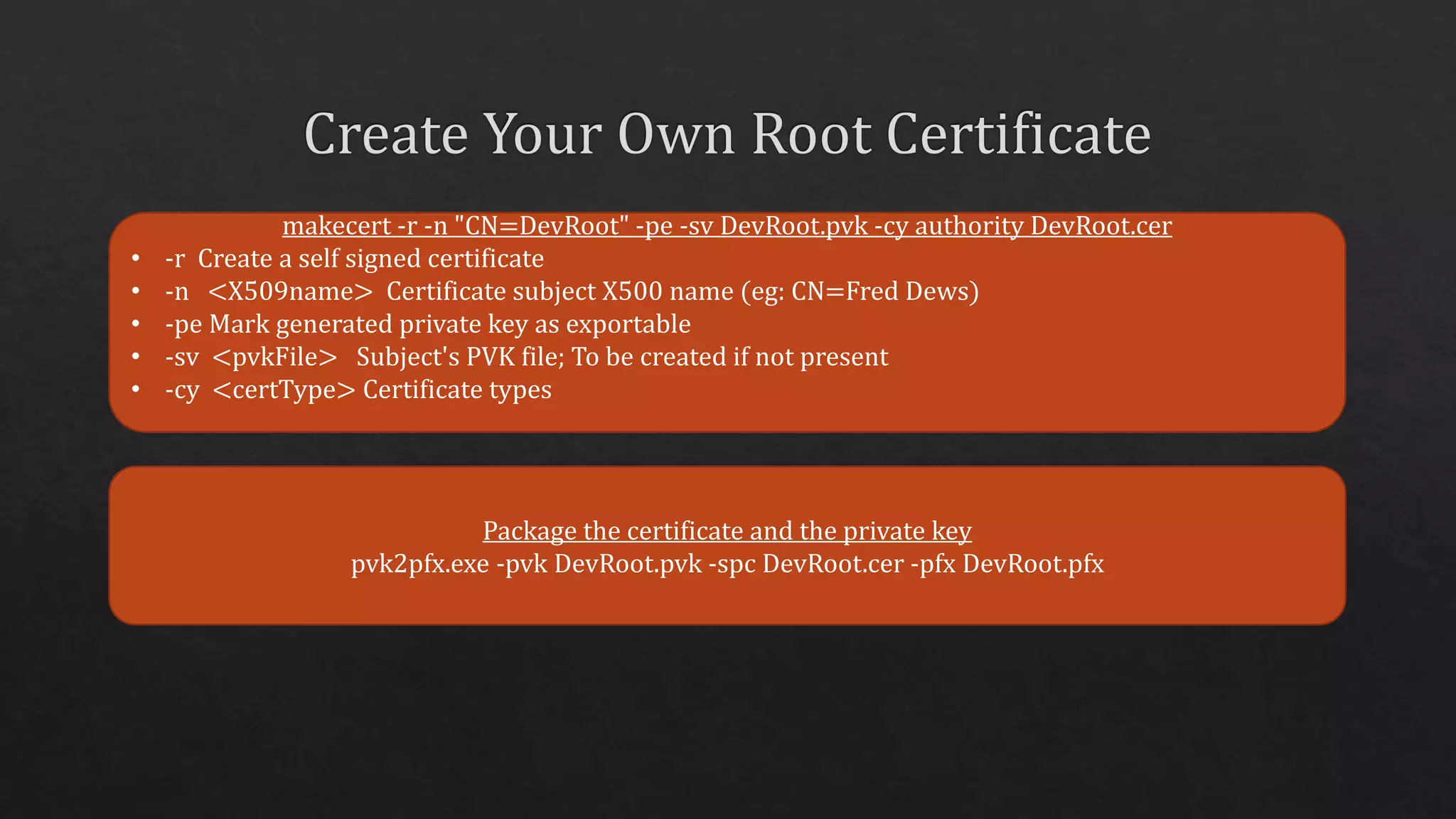
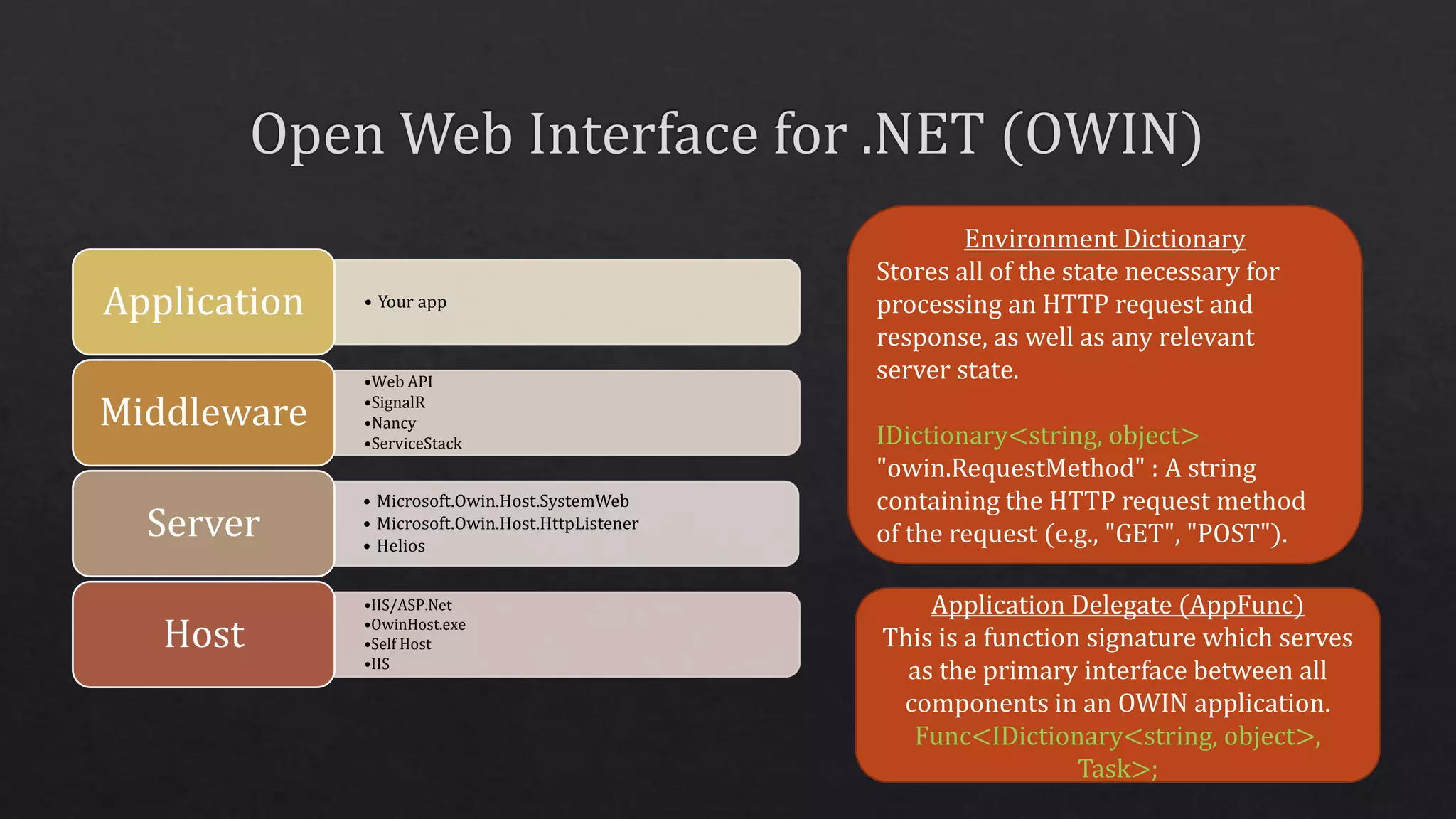
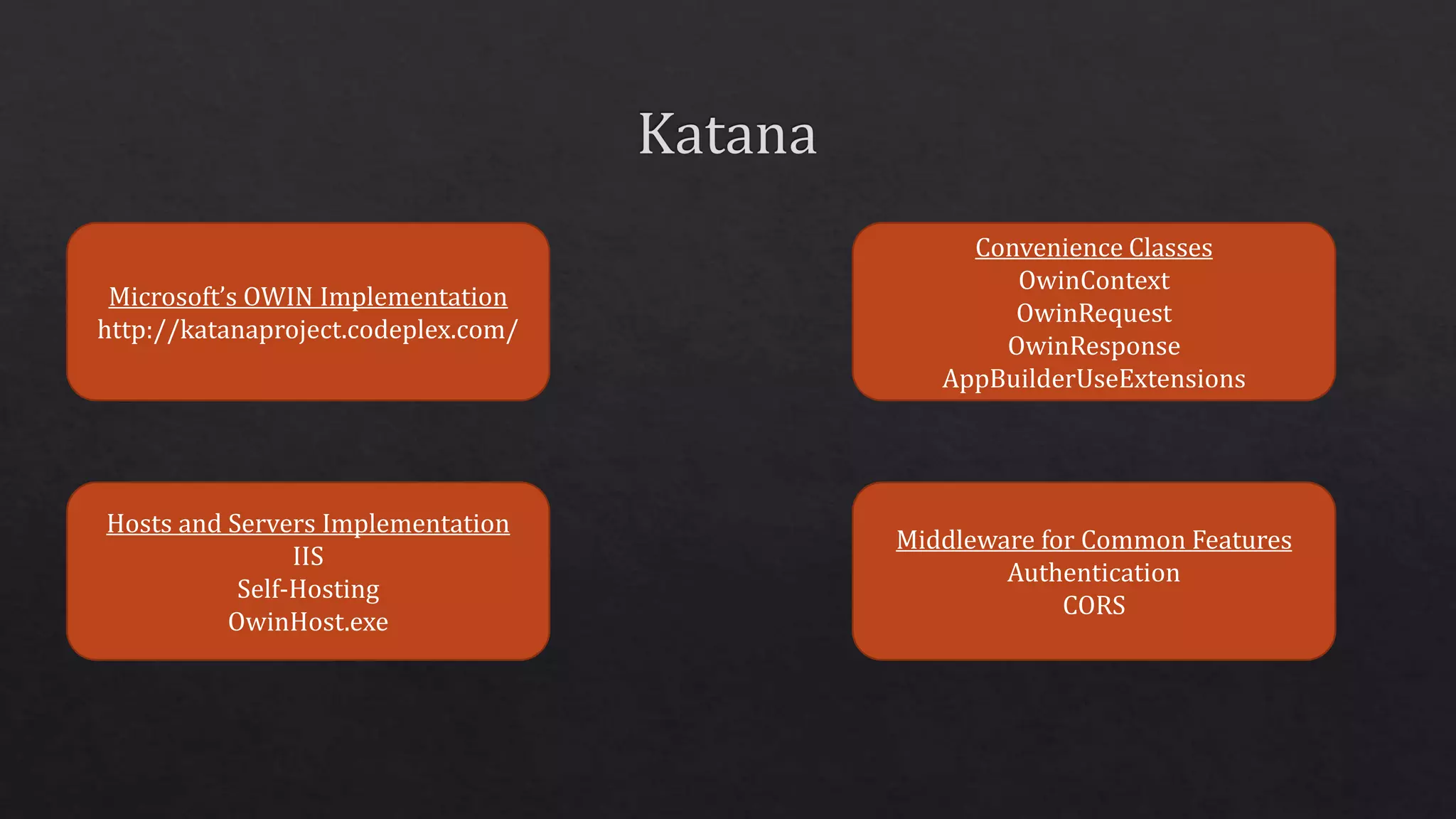
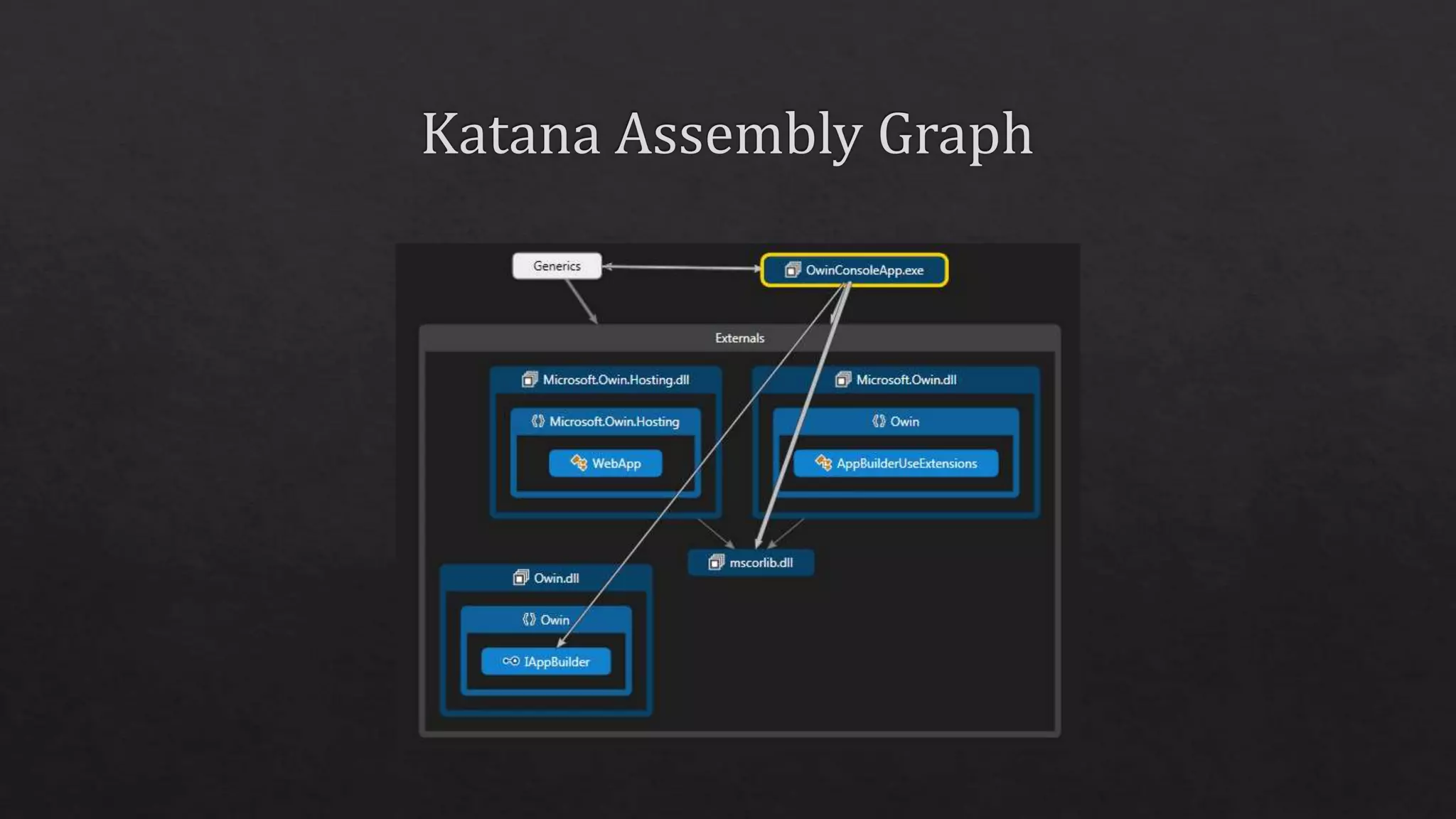
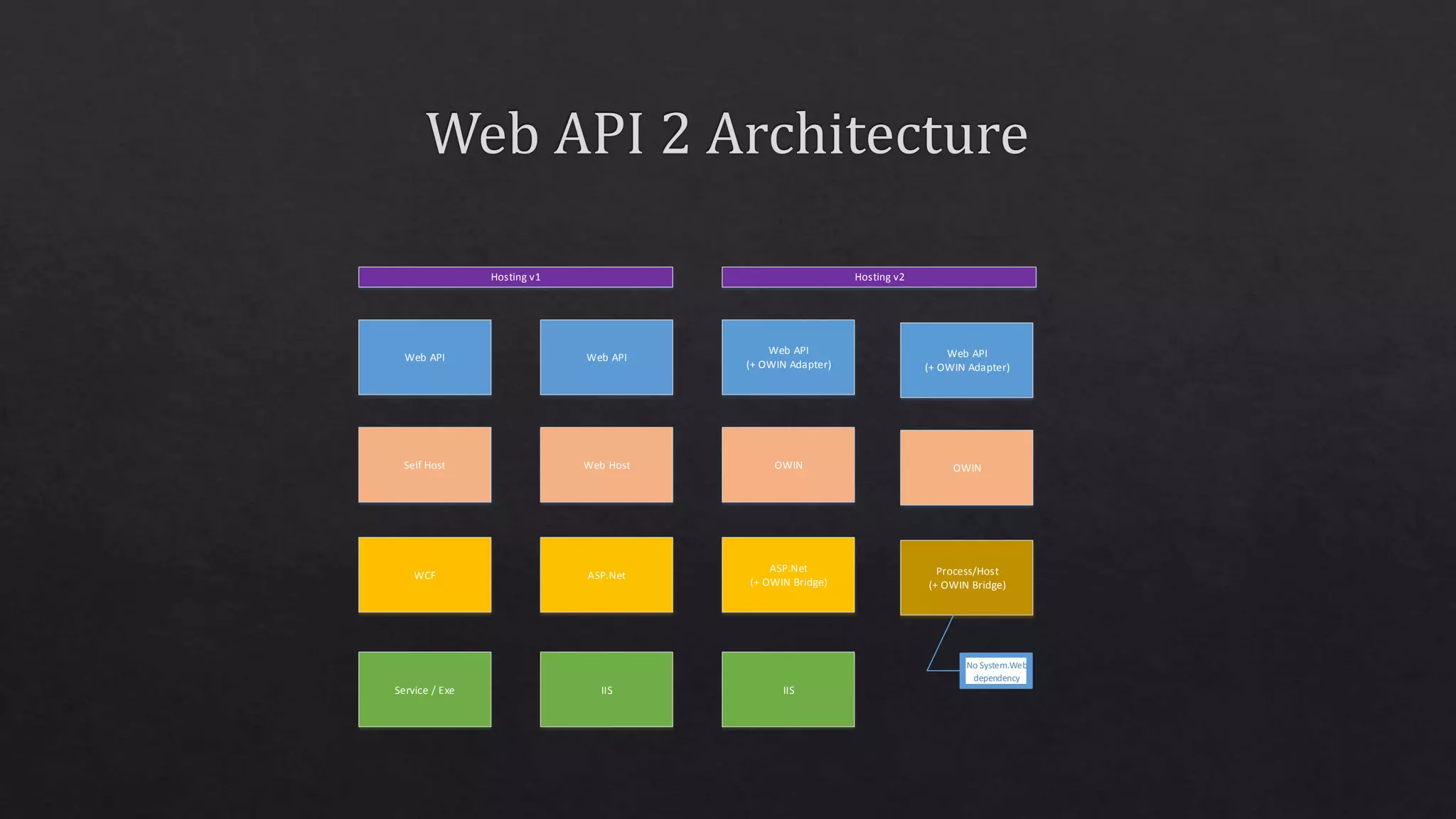
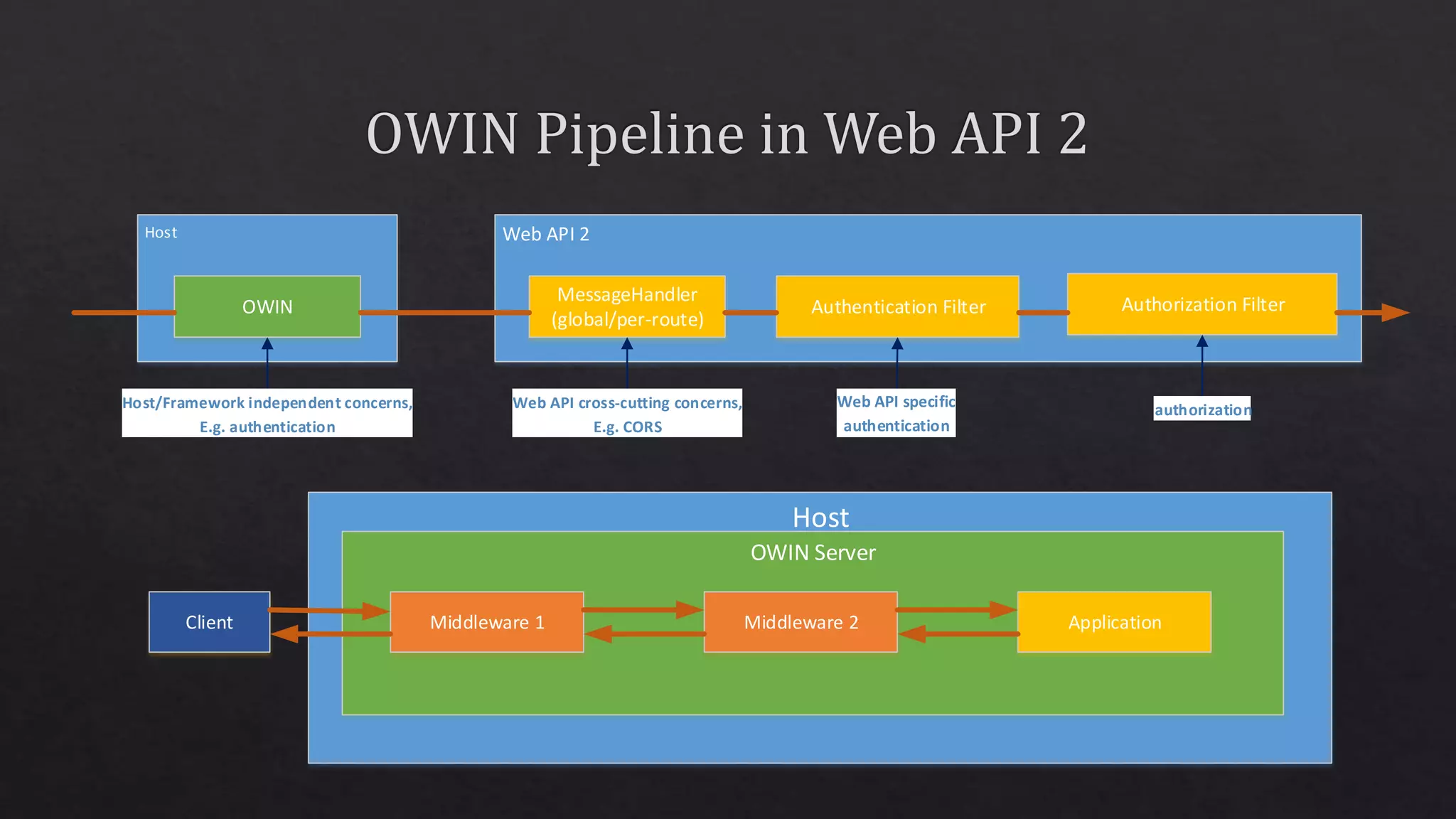
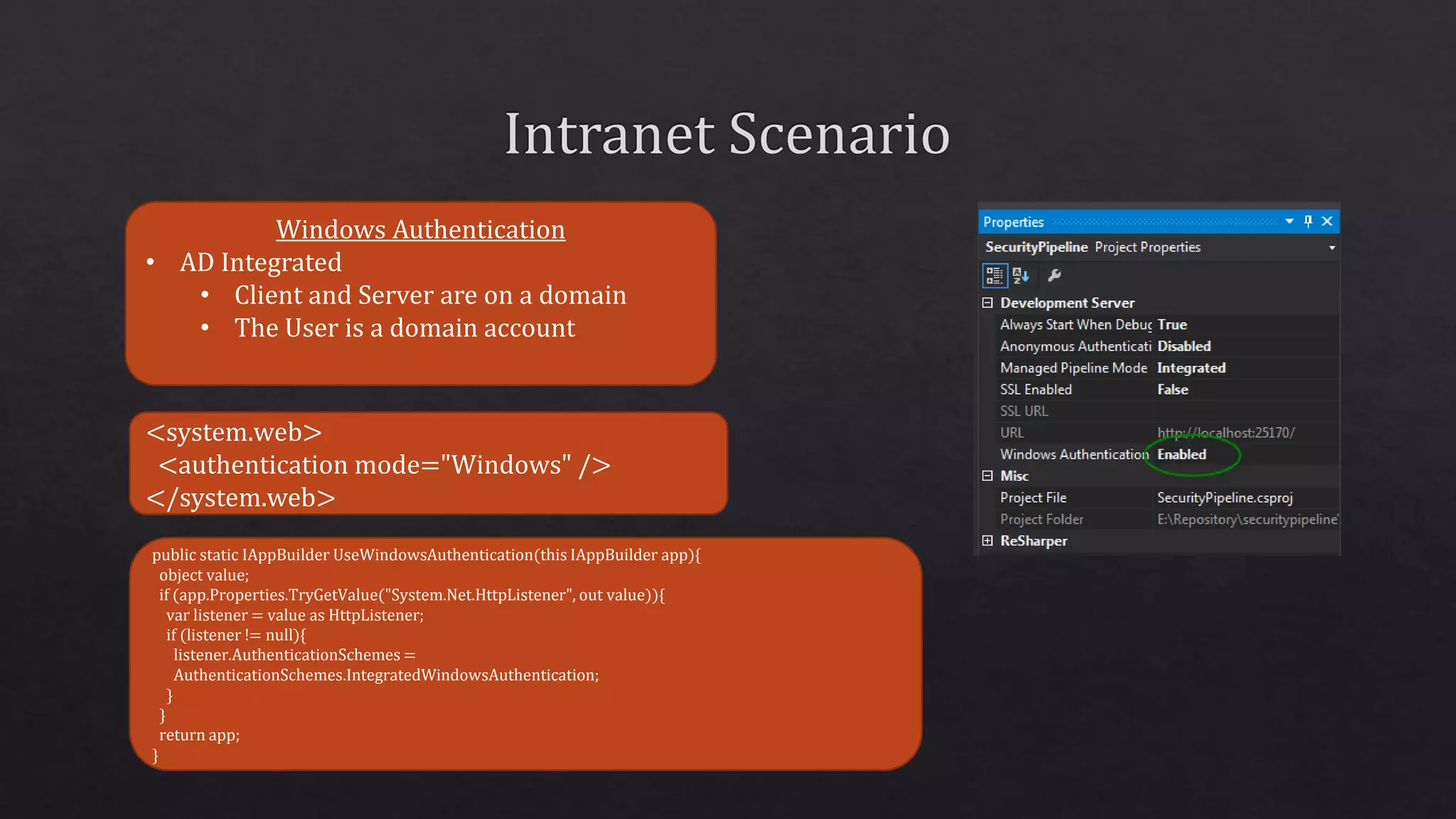
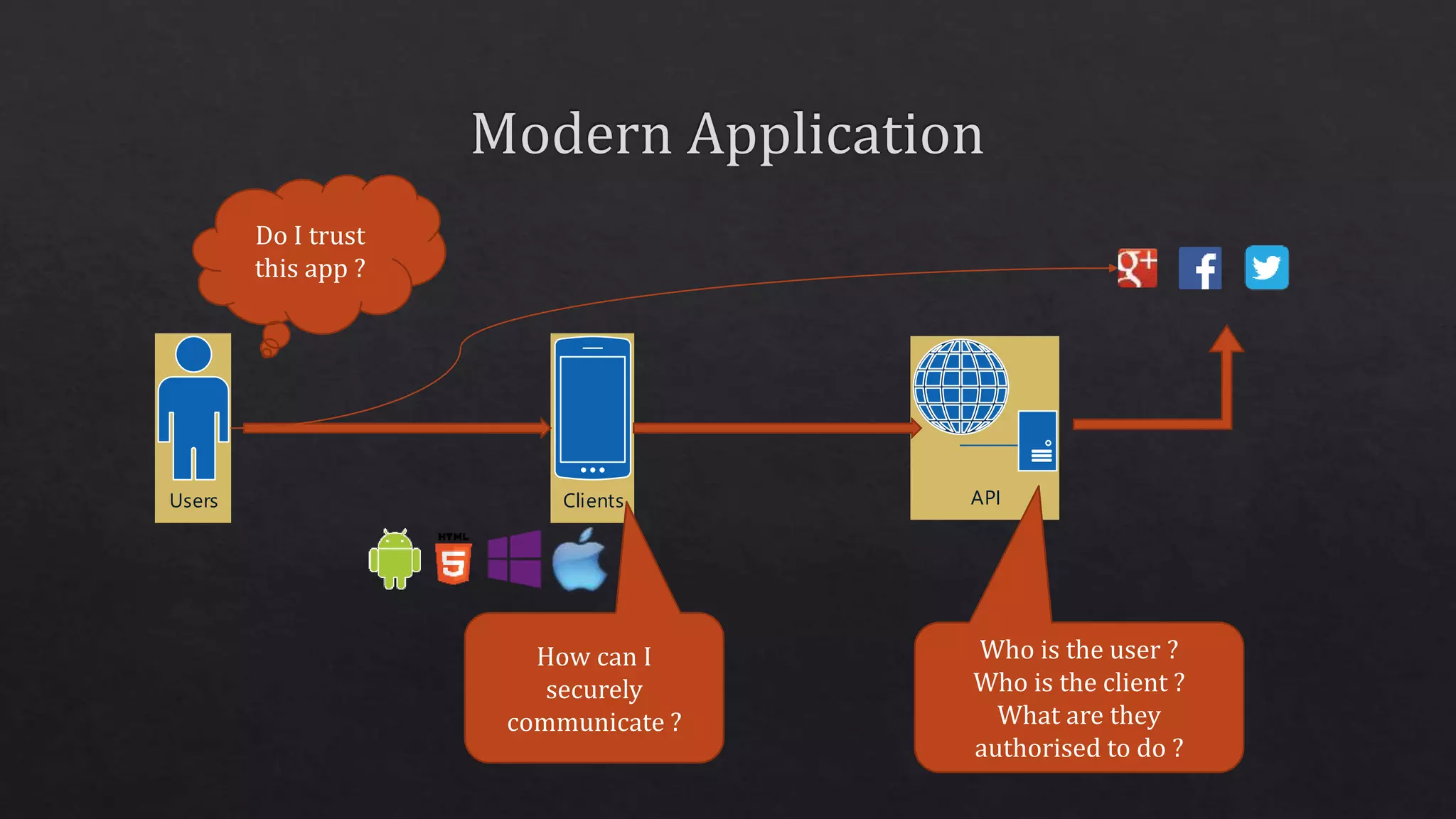
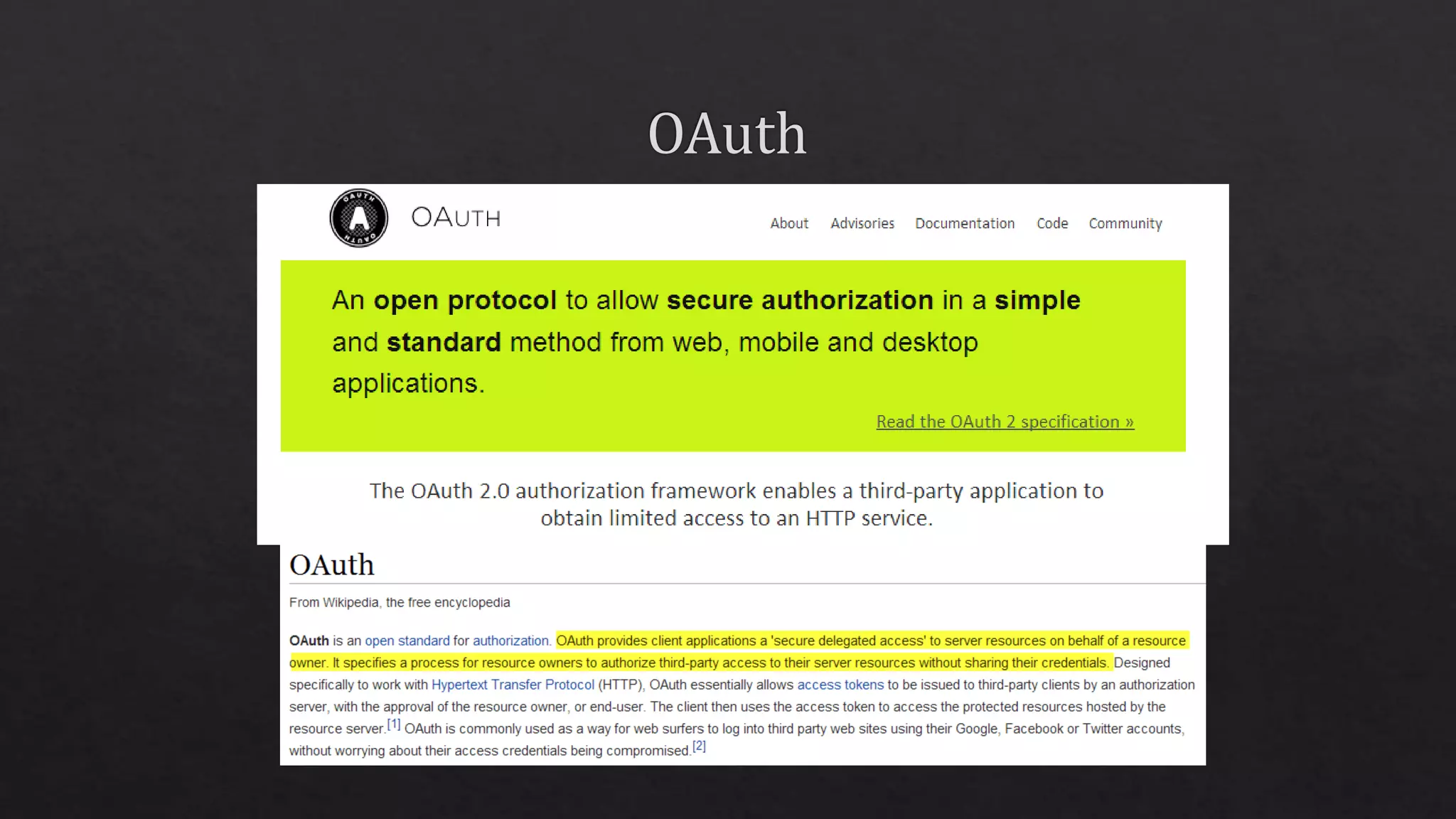
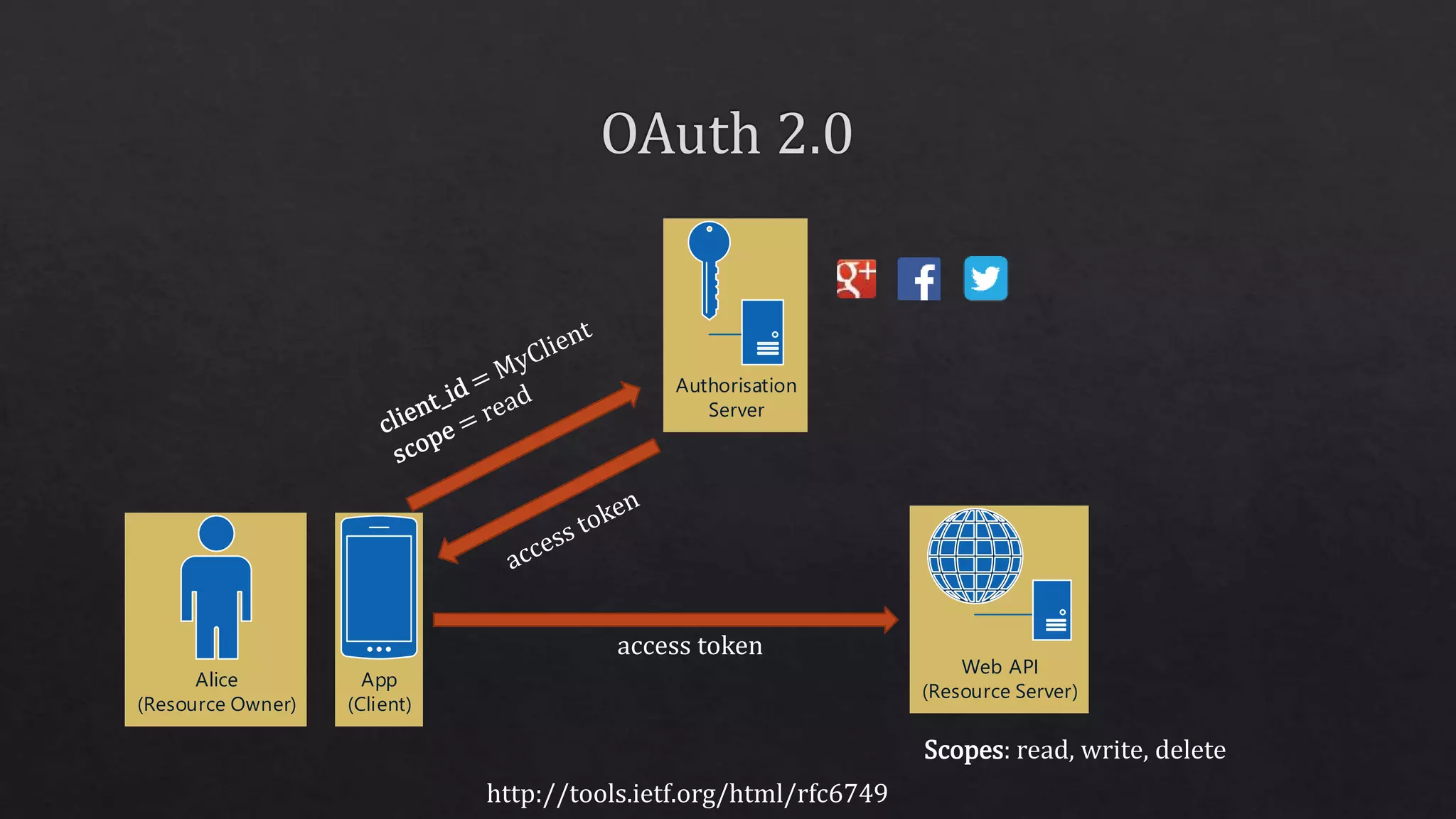
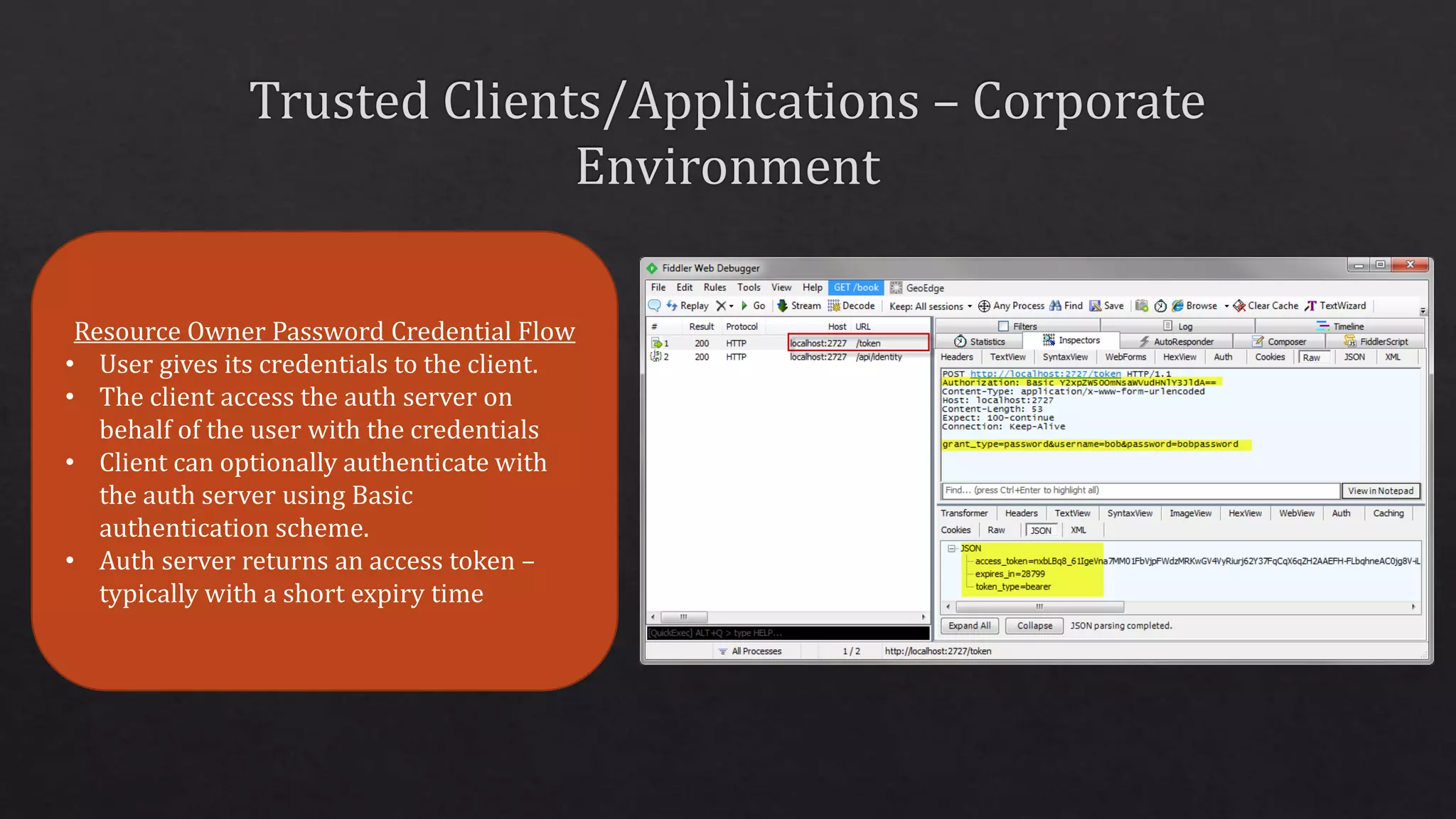
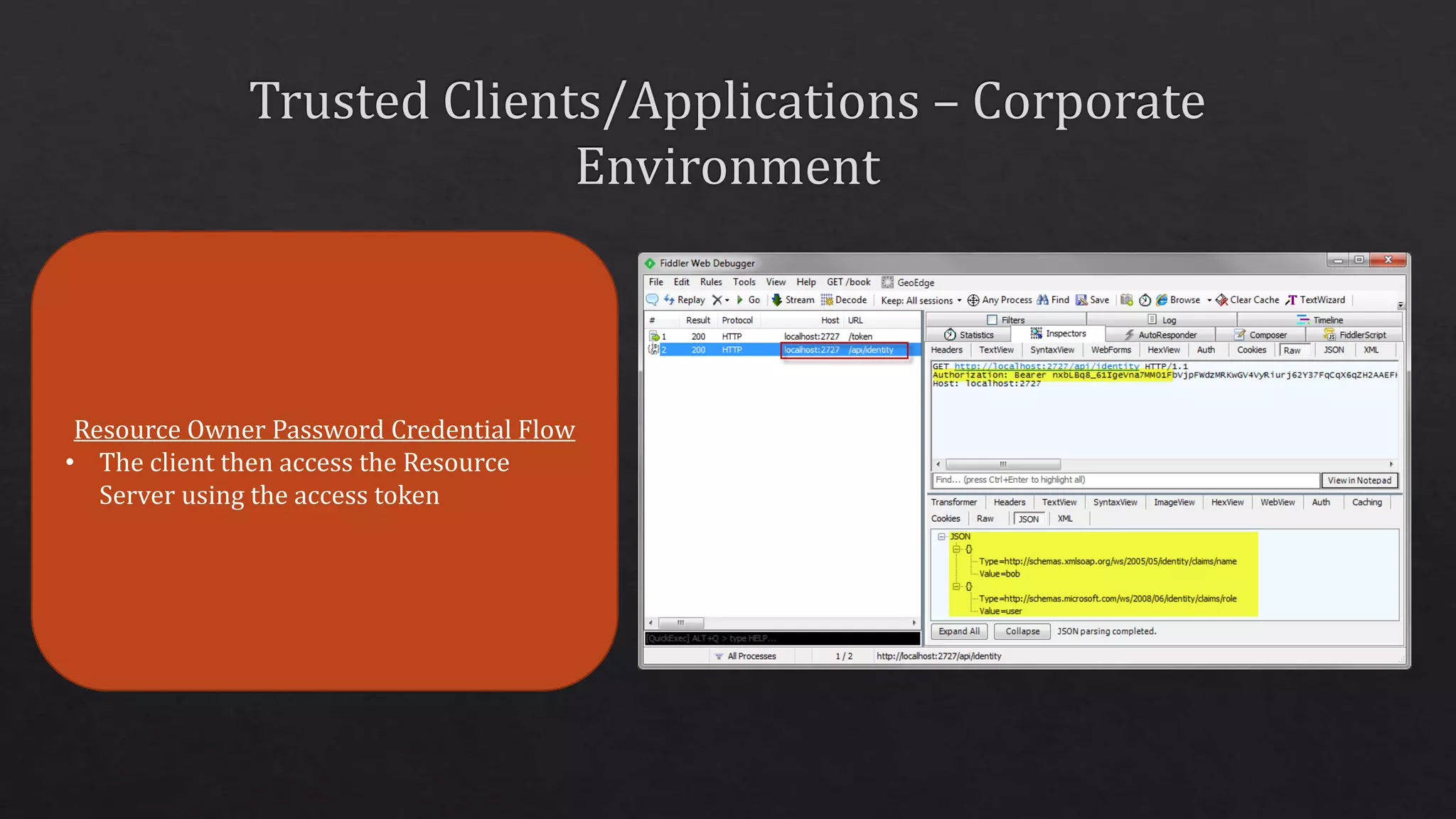
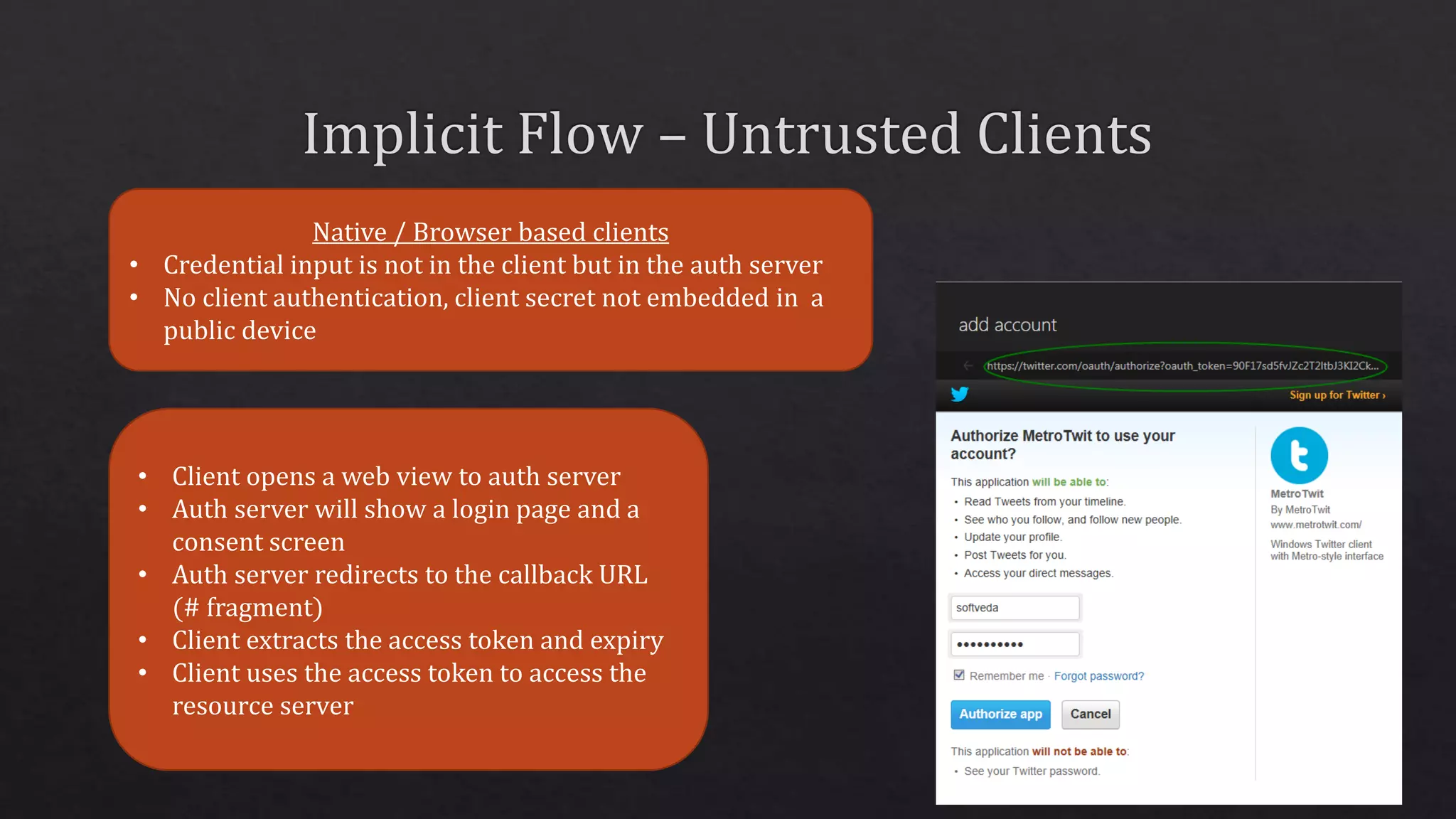
The document outlines the use of HTTP over TLS, covering server and client authentication, SSL certificates, and the creation of self-signed certificates. It also discusses the OWIN implementation for hosting applications, including middleware for various features like authentication and CORS. Additionally, it explains authorization flows, such as resource owner password credentials, and the importance of secure communication methods between clients and servers.


![makecert -iv DevRoot.pvk -ic DevRoot.cer -n "CN=site.local" -pe -sv %1.pvk -sky exchange
site.local.cer -eku 1.3.6.1.5.5.7.3.1
• -iv <pvkFile> Issuer's PVK file
• -ic <file> Issuer's certificate file
• -n <X509name> Certificate subject X500 name (eg: CN=Fred Dews)
• -pe Mark generated private key as exportable
• -sv <pvkFile> Subject's PVK file; To be created if not present
• -sky <keytype> Subject key type
• -eku <oid[<,oid>]> Comma separated enhanced key usage OIDs](https://image.slidesharecdn.com/dddmelbourne2014securityinasp-140803072648-phpapp01/75/DDD-Melbourne-2014-security-in-ASP-Net-Web-API-2-7-2048.jpg)


![Same Origin Policy in Browsers
• AJAX requests to a different host, port or protocol
will fails
• CORS is a W3C standard that allows cross origin
http requests
• The request itself succeeds but the browser
returns an error
• Supported in modern browsers only, IE 10+
CORS support in Web API
• Install-Package
Microsoft.AspNet.WebApi.Cors
• WebApiConfig.cs –
config.EnableCors();
• Controller.cs –
[EnableCors("origin", "headers", "verbs")]
public class MyController : ApiController
{
}
Request Header
Origin: http://cors.local/
Response Header
Access-Control-Allow-Origin: *](https://image.slidesharecdn.com/dddmelbourne2014securityinasp-140803072648-phpapp01/75/DDD-Melbourne-2014-security-in-ASP-Net-Web-API-2-24-2048.jpg)