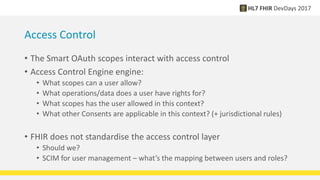
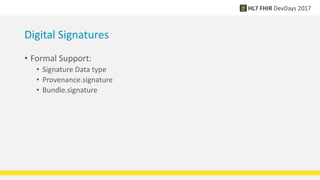
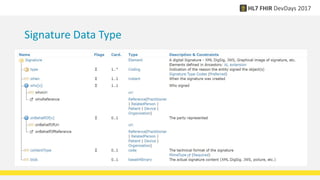
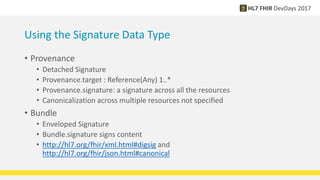
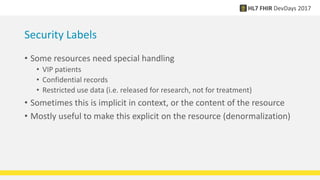
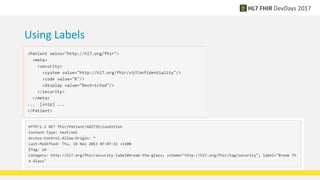
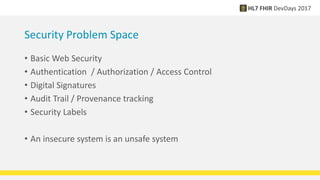
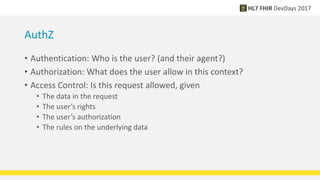
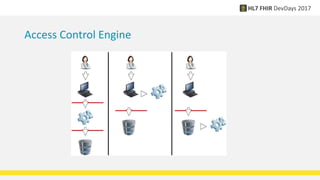
FHIR provides standards for security including authentication, authorization, access control, digital signatures, audit trails, and security labels. Authentication verifies a user's identity, while authorization determines what resources a user can access. Access control engines enforce authorization and other rules. Digital signatures can be applied to resources and bundles to ensure integrity. Audit trails and provenance track access. Security labels make access restrictions like confidentiality explicit. Ongoing work continues on authorization models and how to apply signatures to RESTful resources.


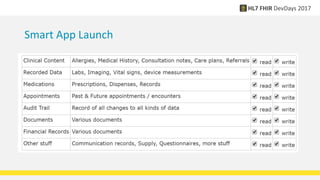
![Smart App Launch Scopes
• [class]/[type].[mode]
• Class = patient | user | system
• Type = * or a FHIR resource type
• Mode = * | read | write
• Examples: patient/*.read user/*.* system/Communication.write
• Also: openid profile launch offline_access online_access](https://image.slidesharecdn.com/securityoverviewgrahame-171117082036/85/Security-overview-grahame-11-320.jpg)