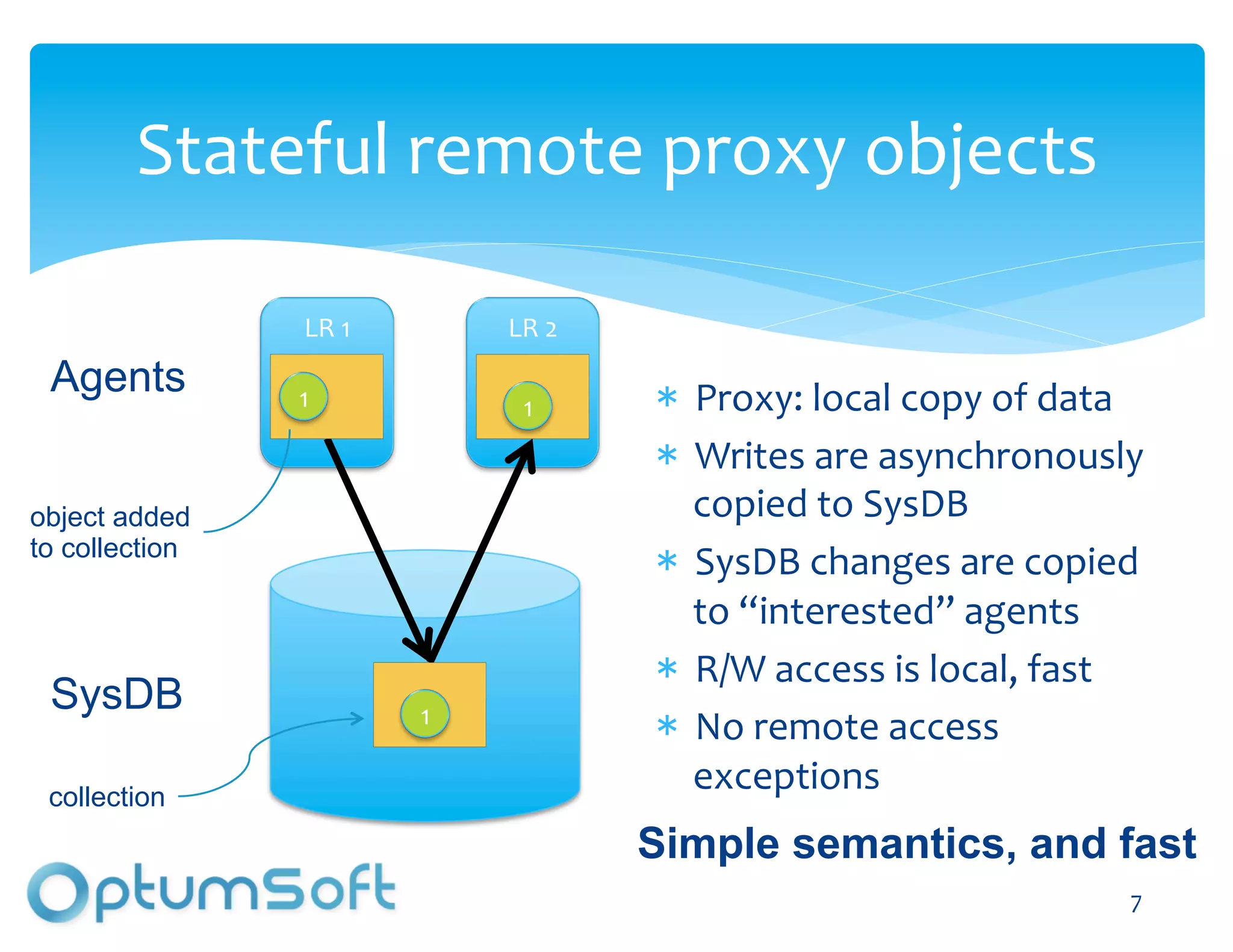
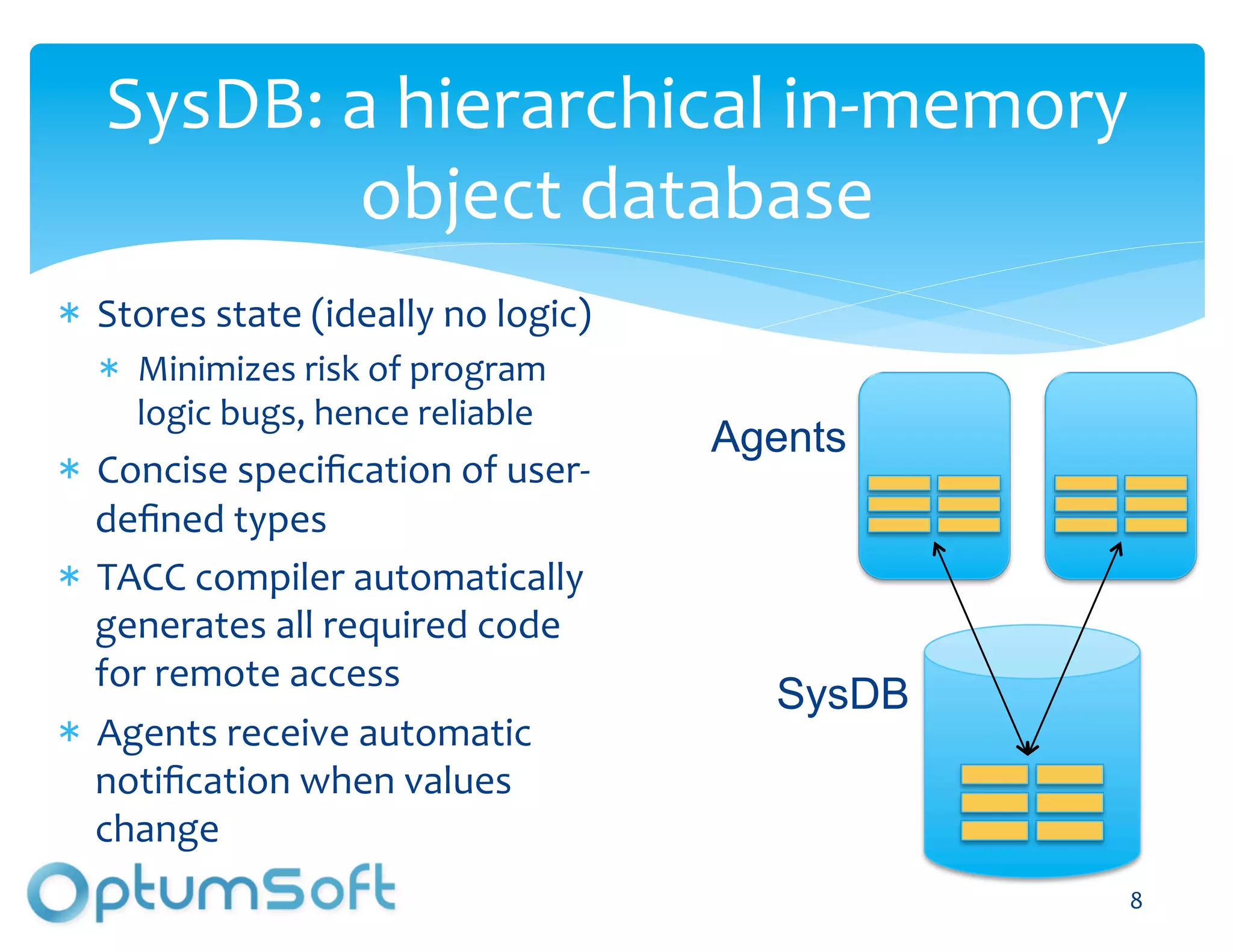
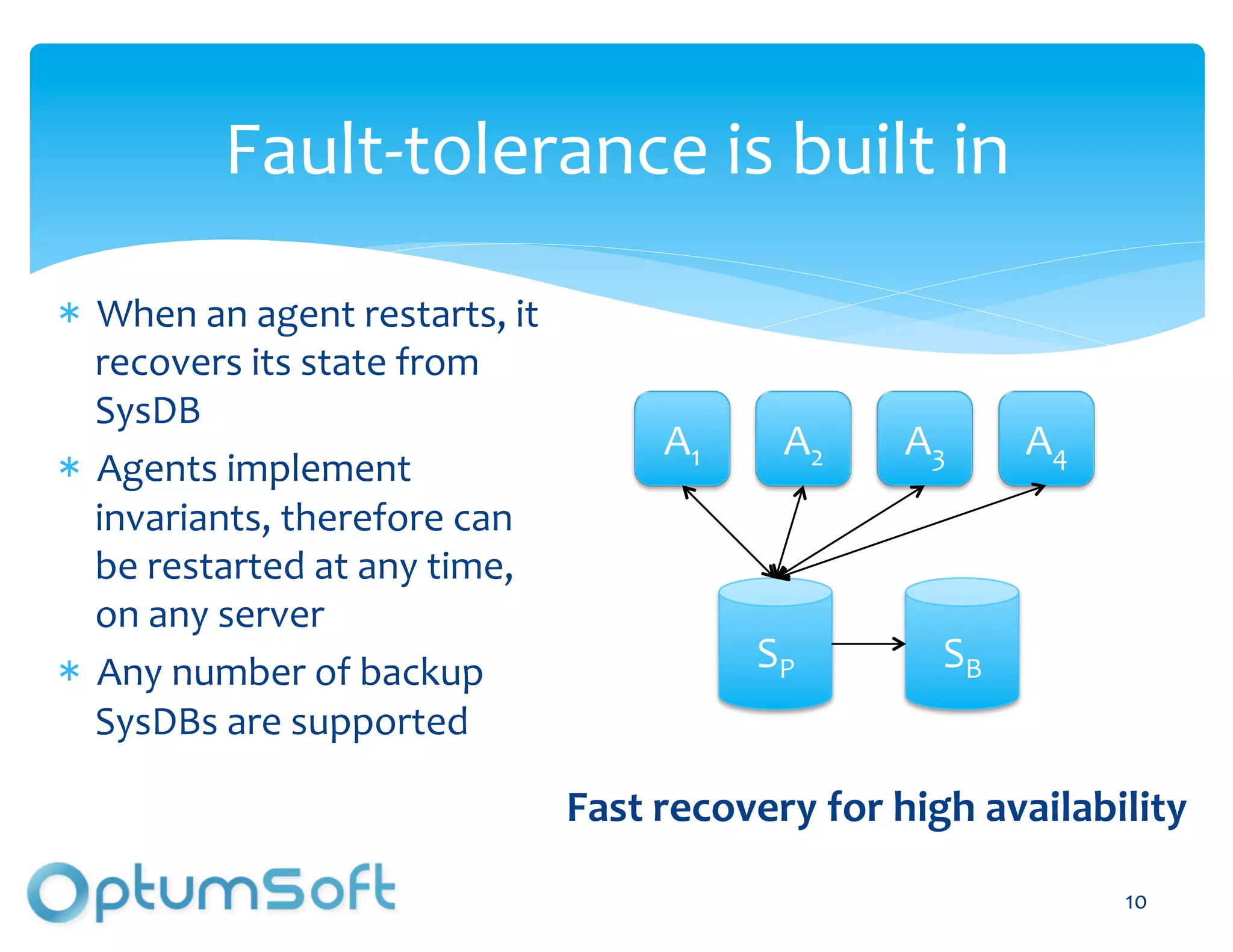
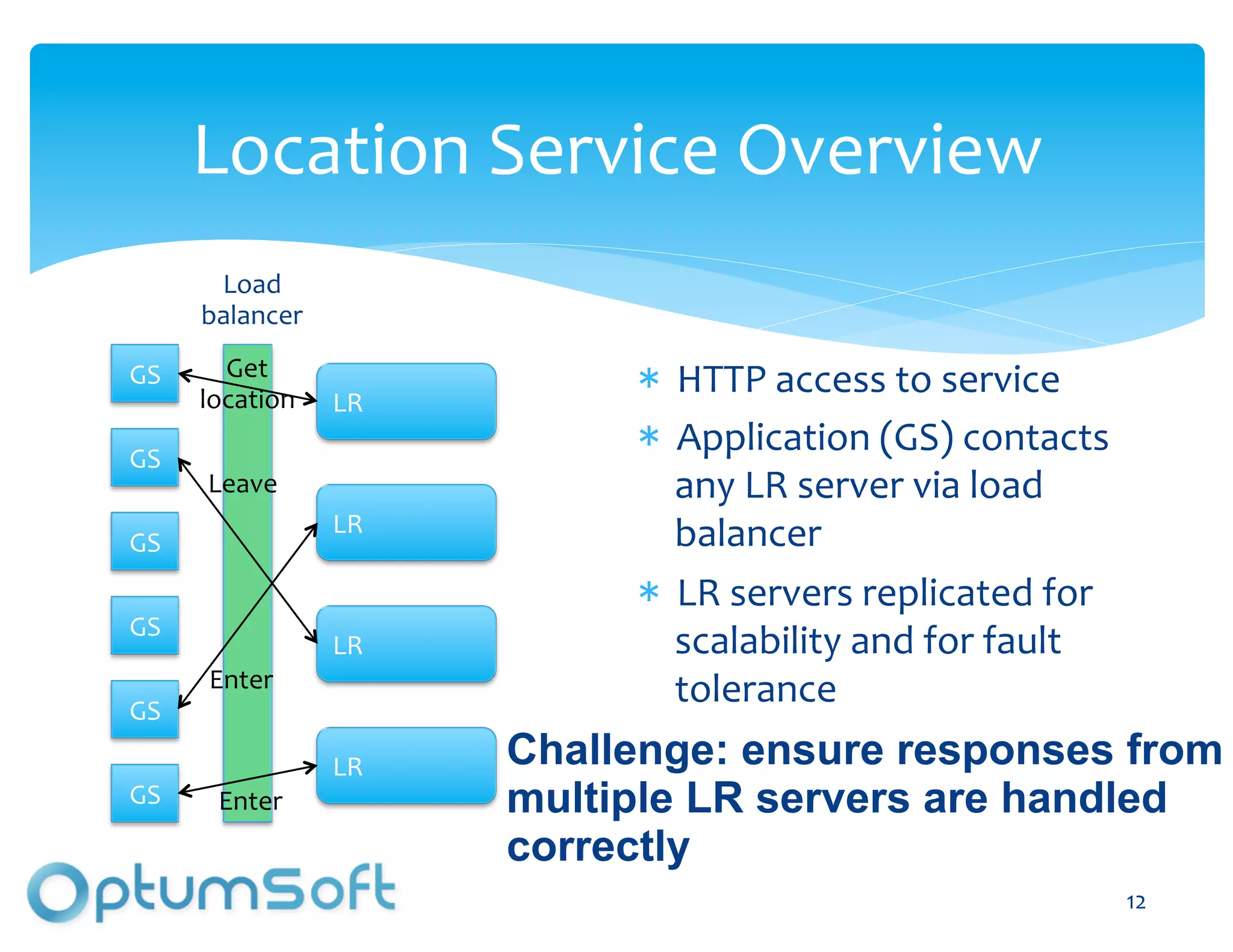
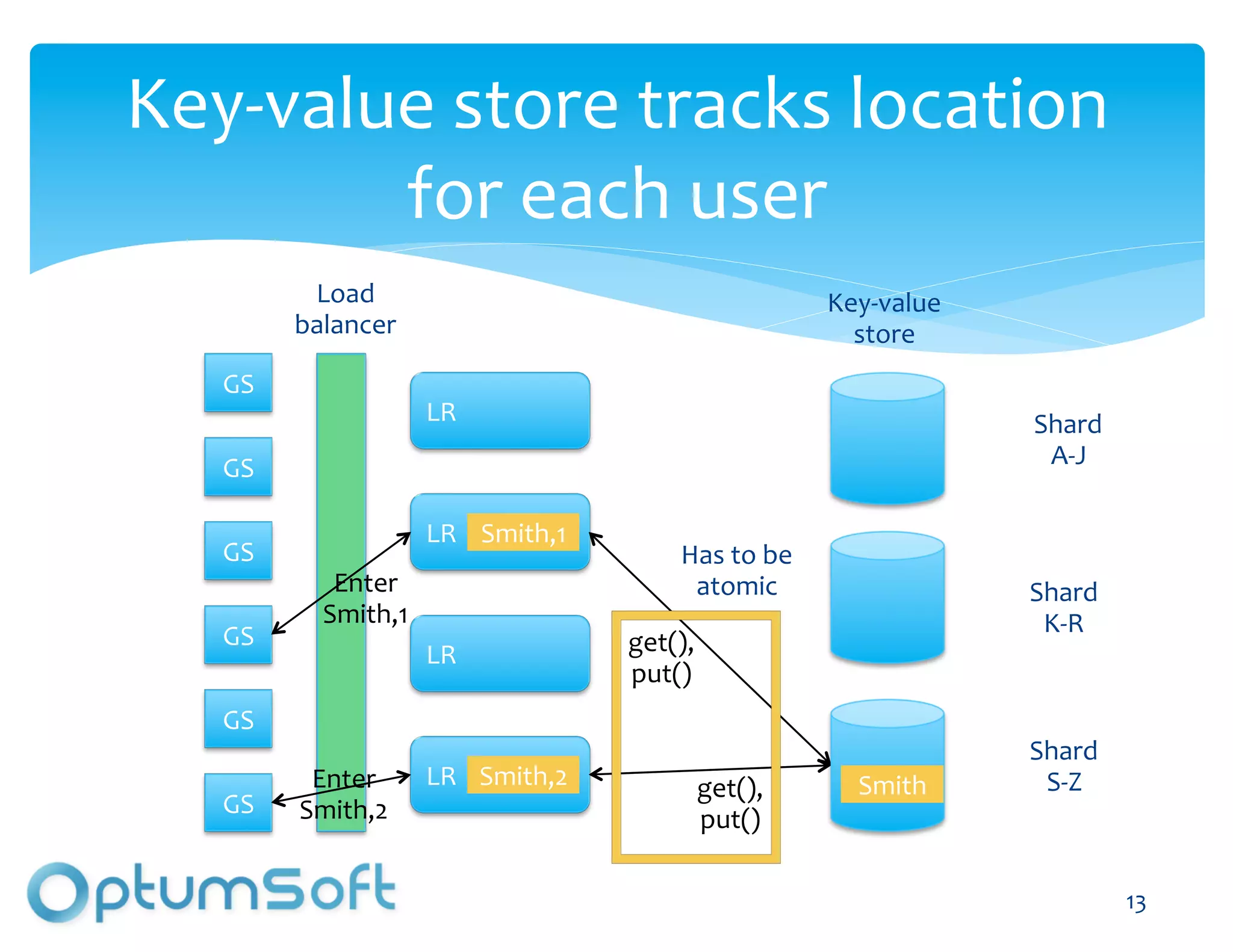
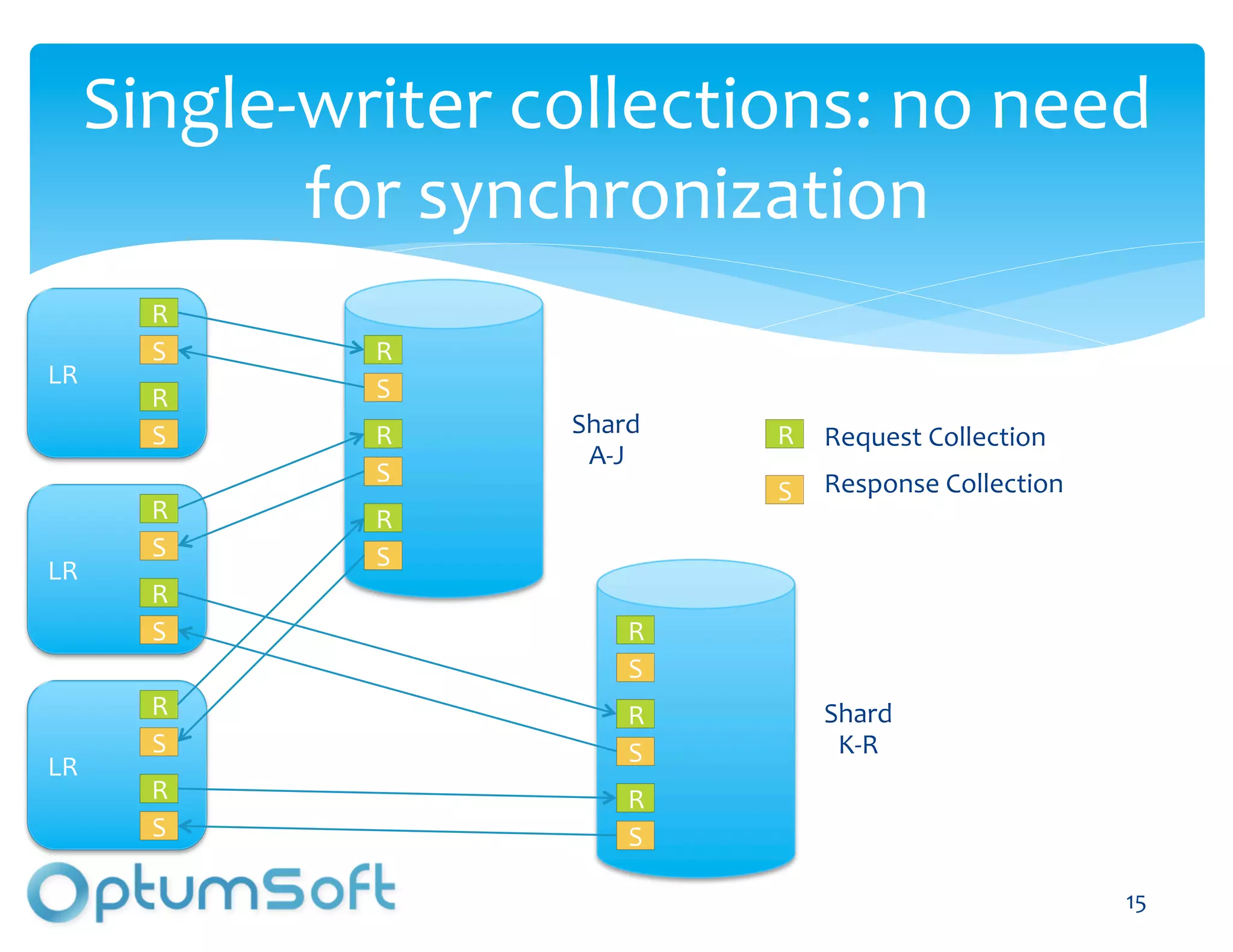
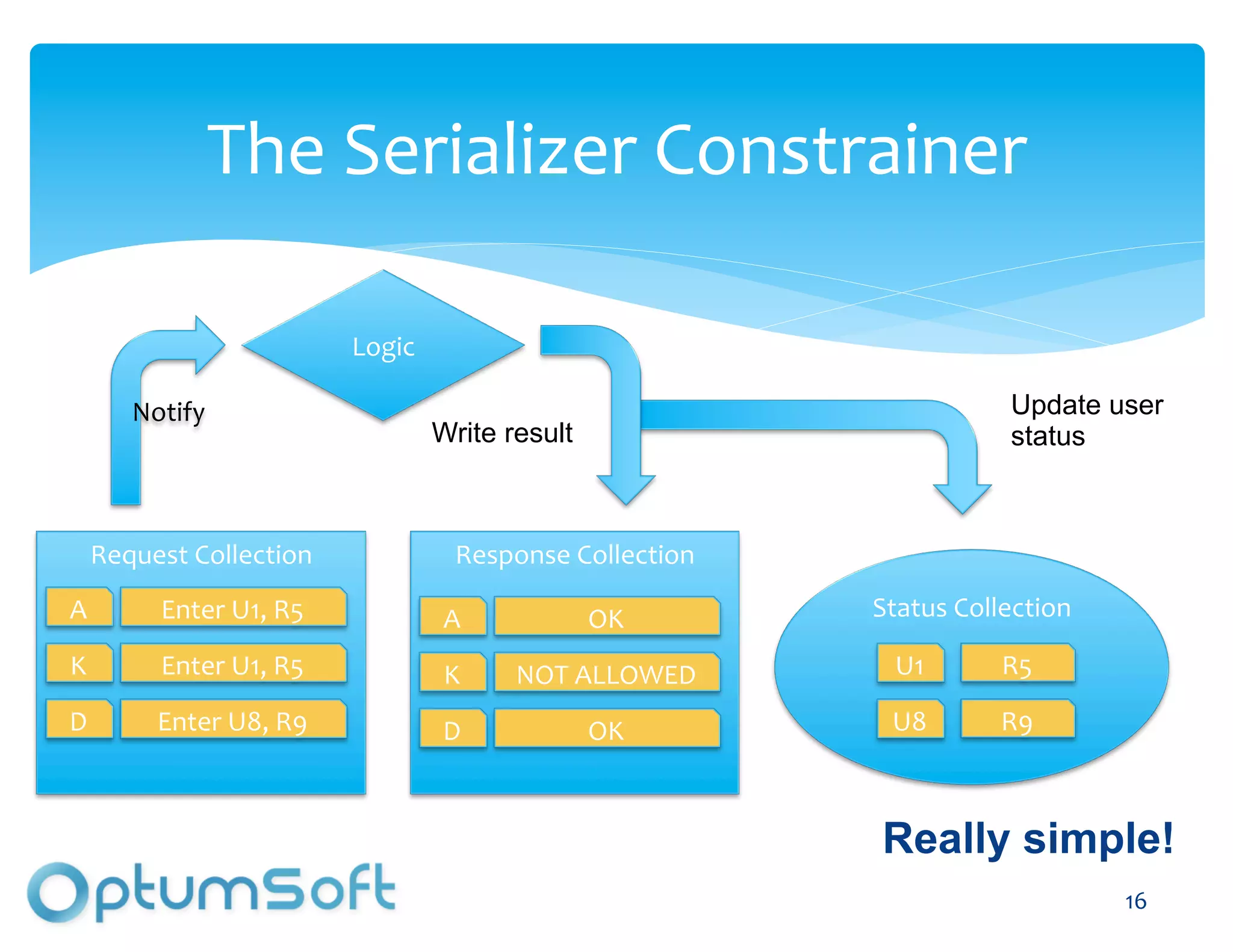
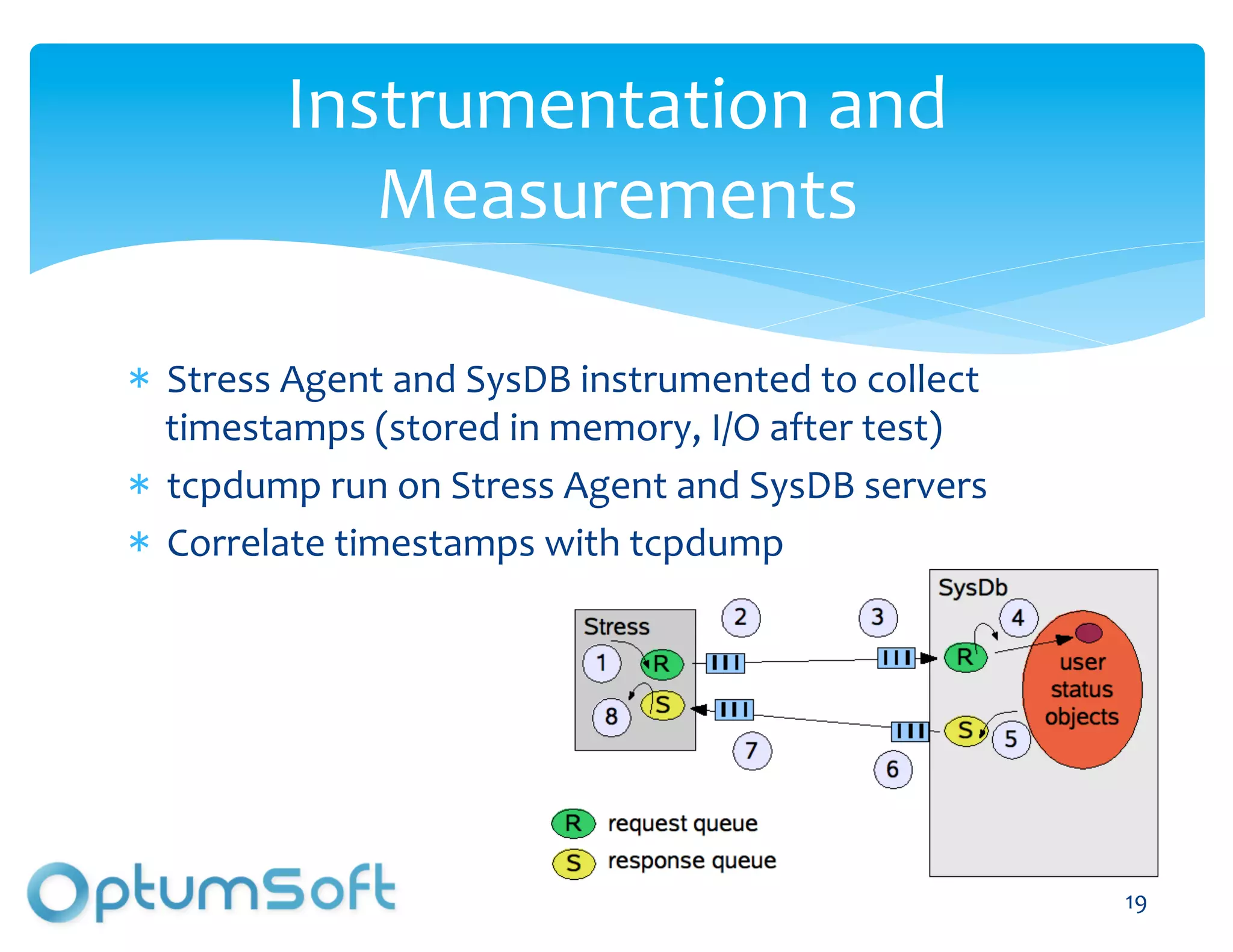
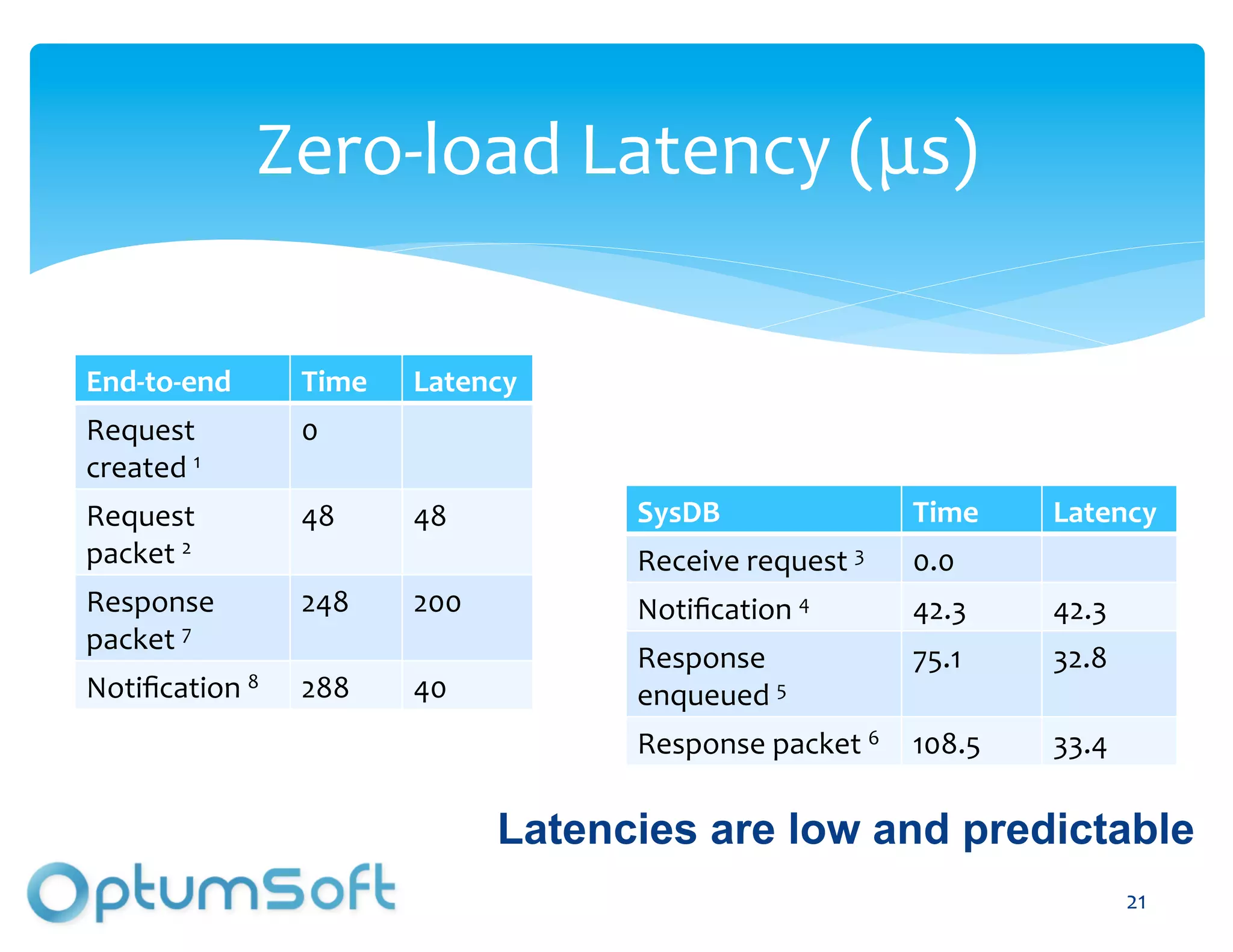
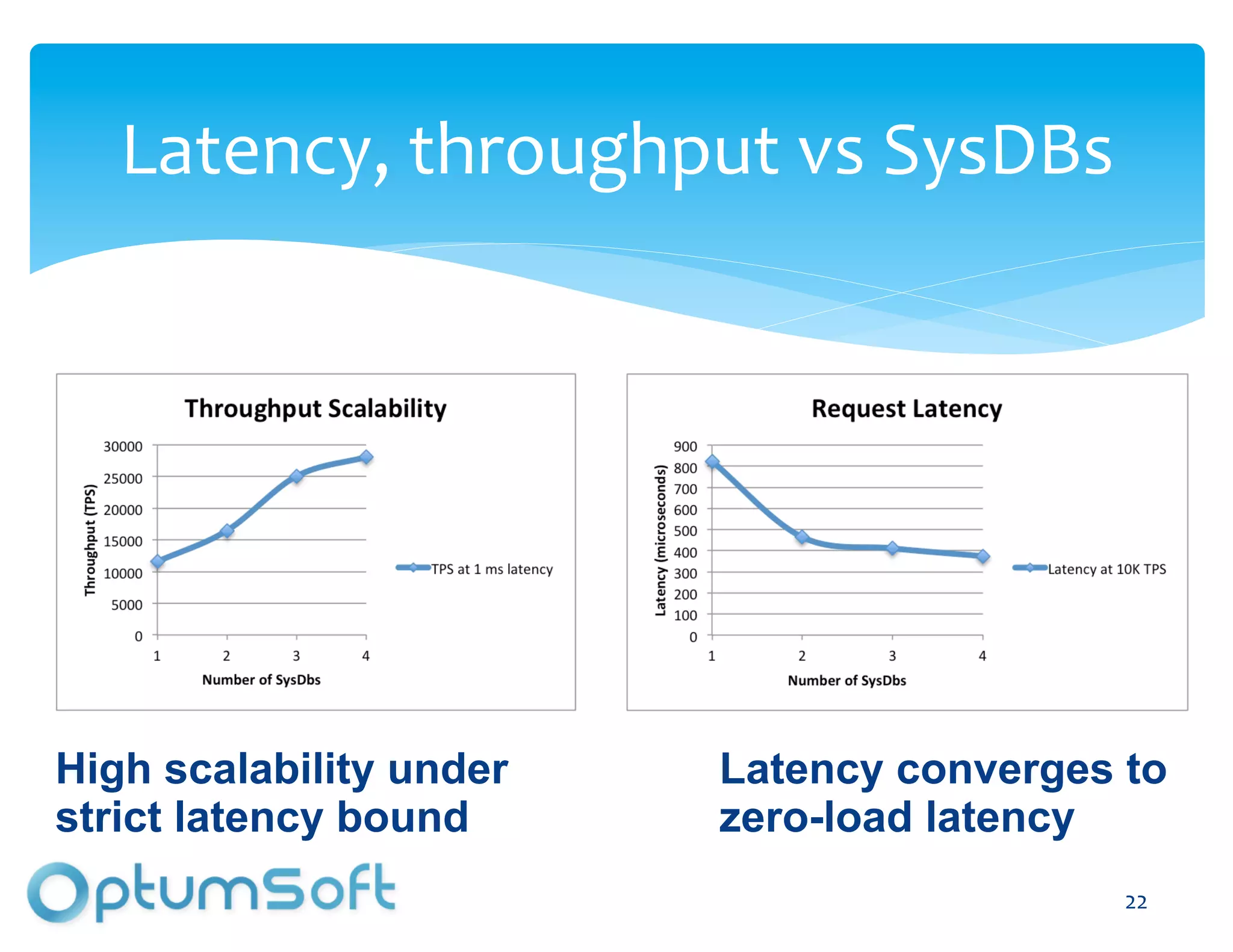
The document discusses TACC, a high-level programming language designed to enhance the development of scalable and fault-tolerant key-value stores. It emphasizes how TACC simplifies application logic, improves performance, and minimizes synchronization issues, leading to faster development times and increased reliability. An example of a location service demonstrates TACC's ability to efficiently handle real-time user location tracking with high throughput and low latency.