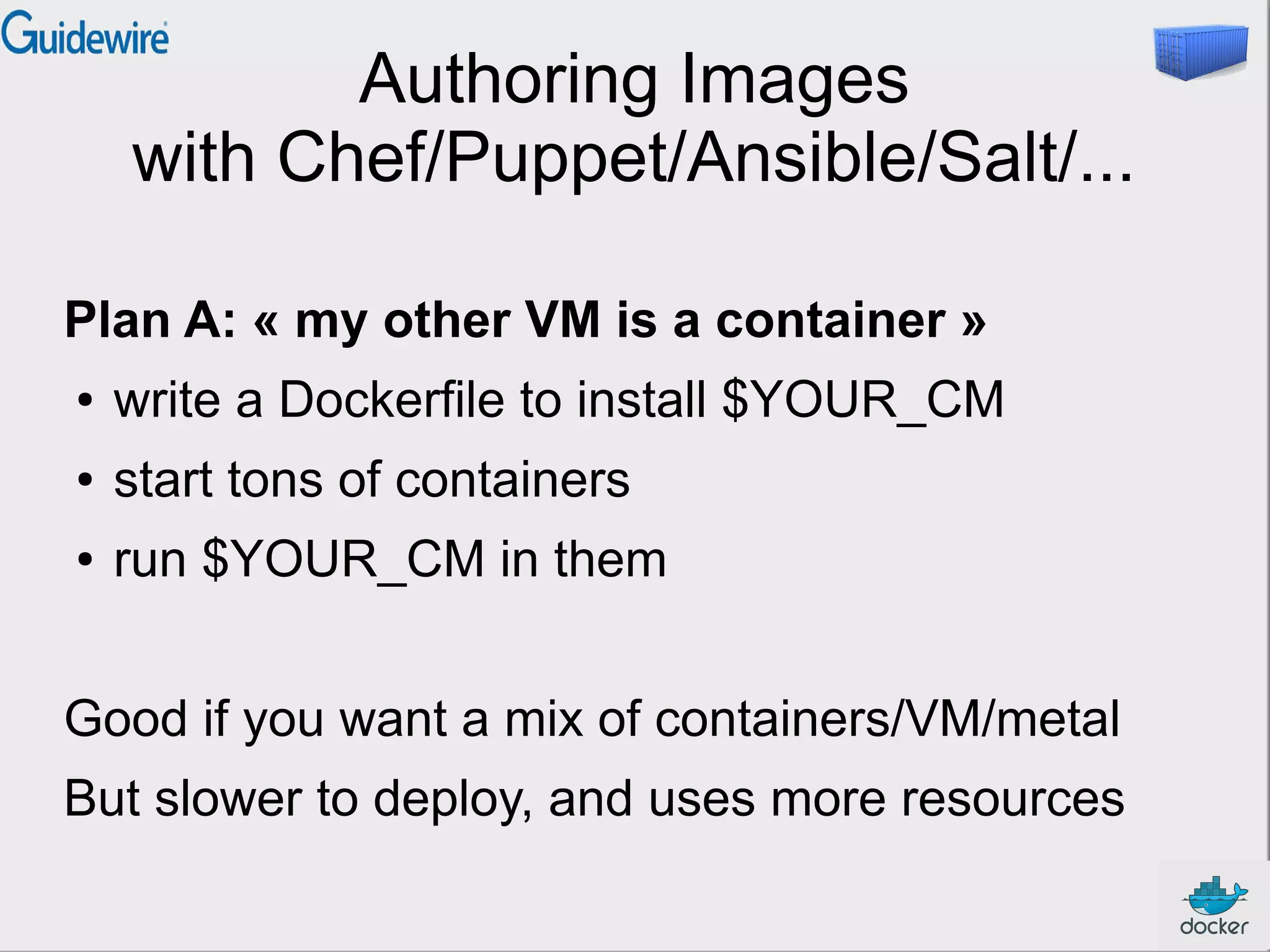
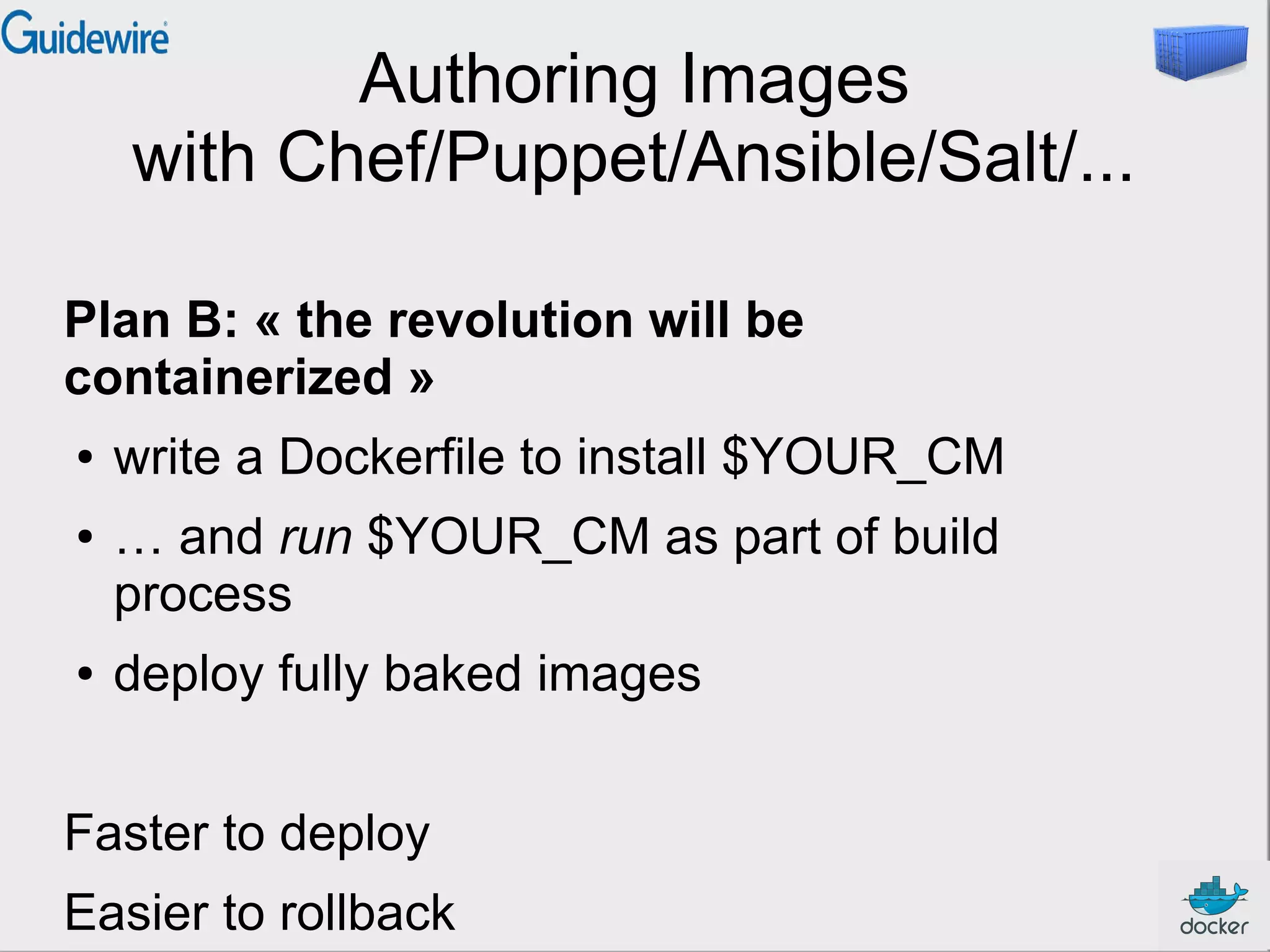
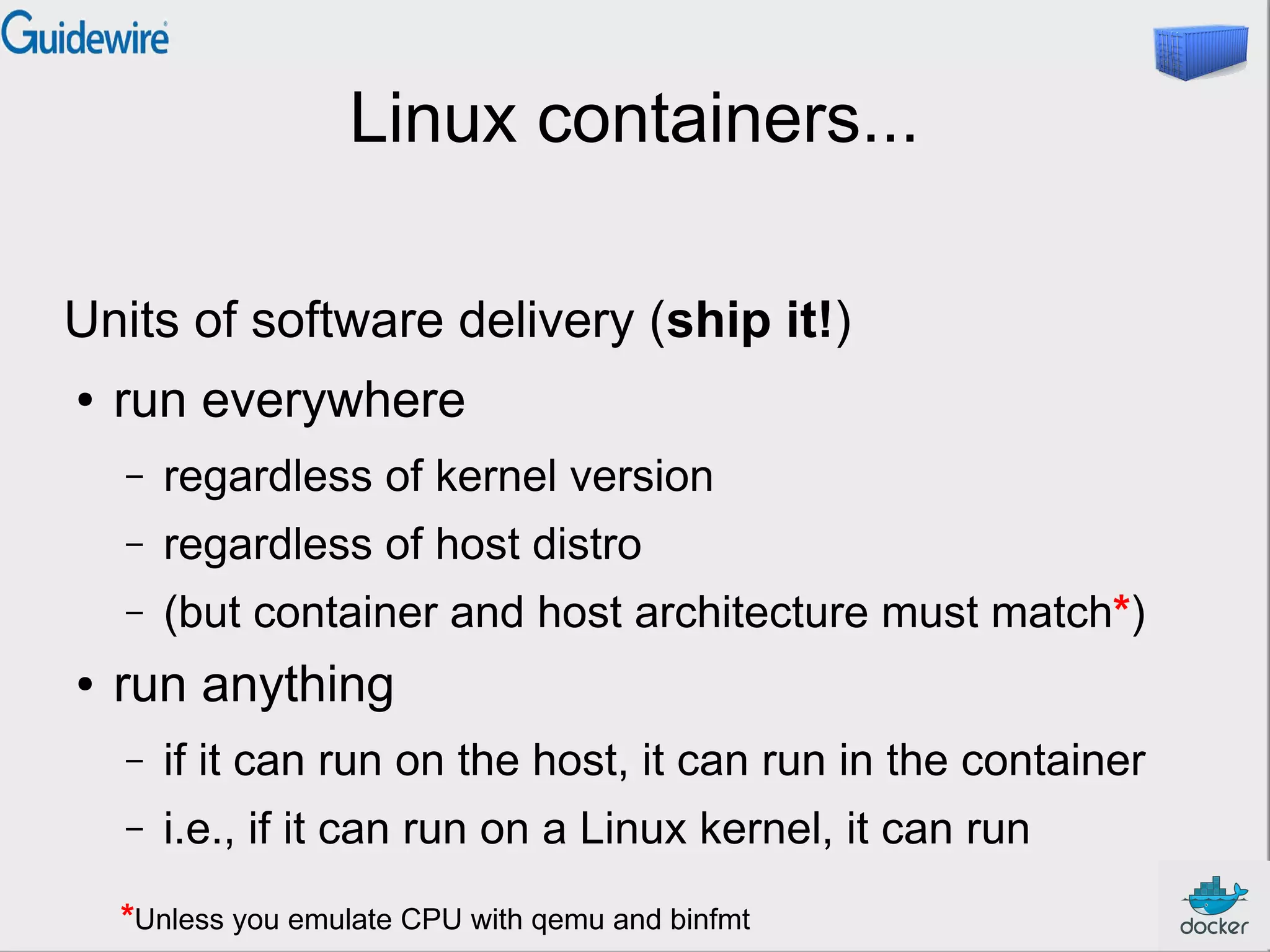
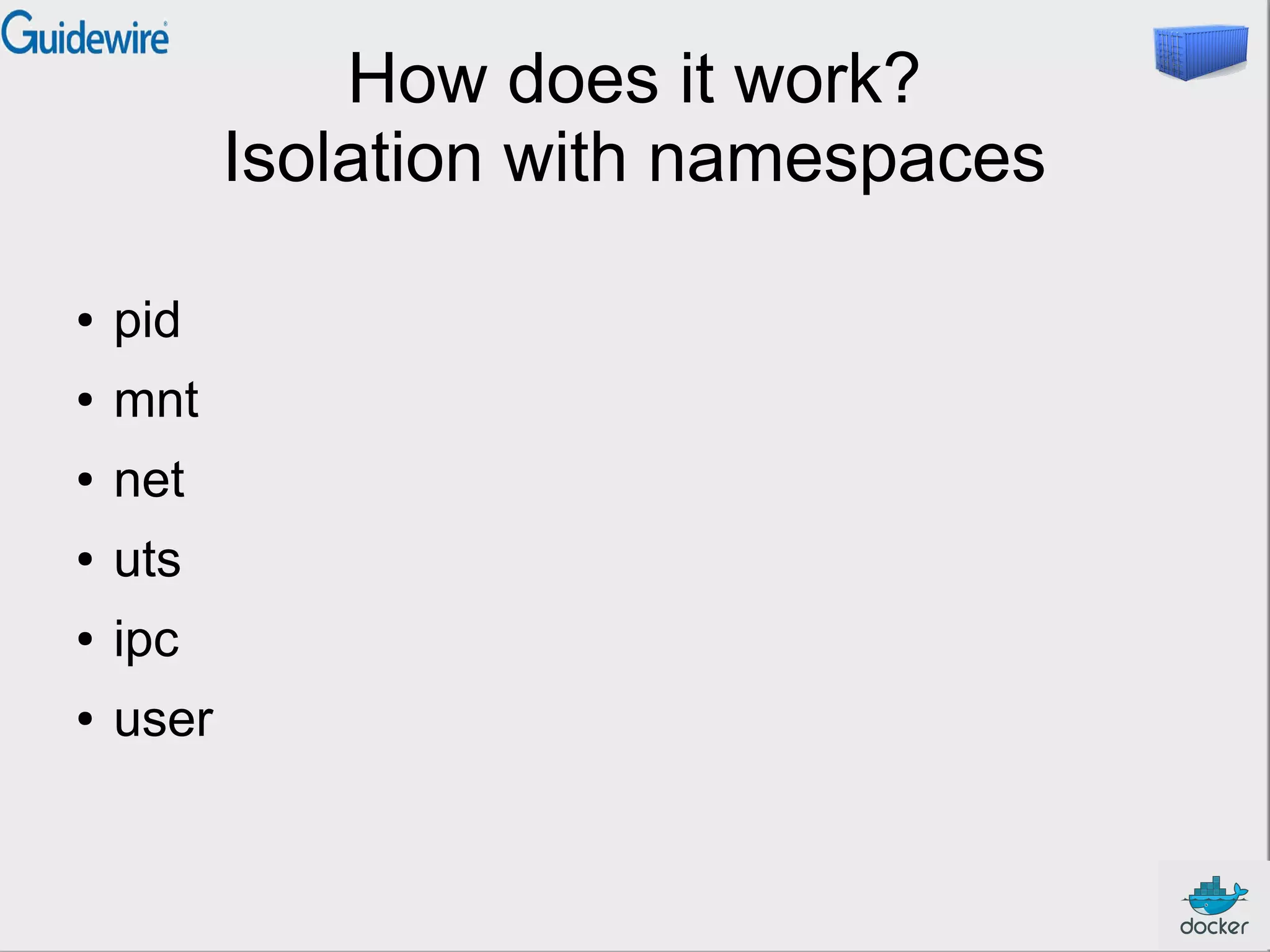
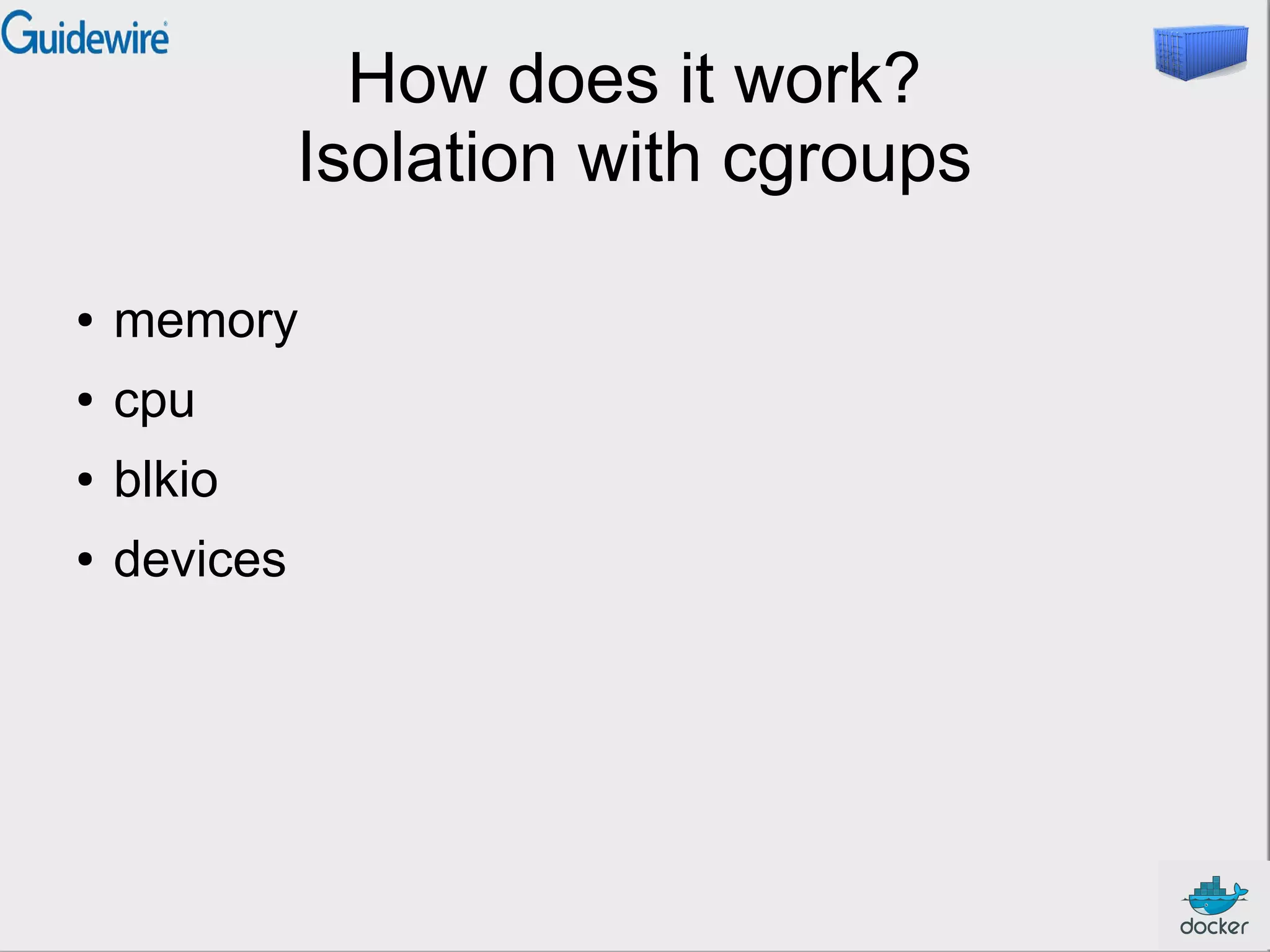
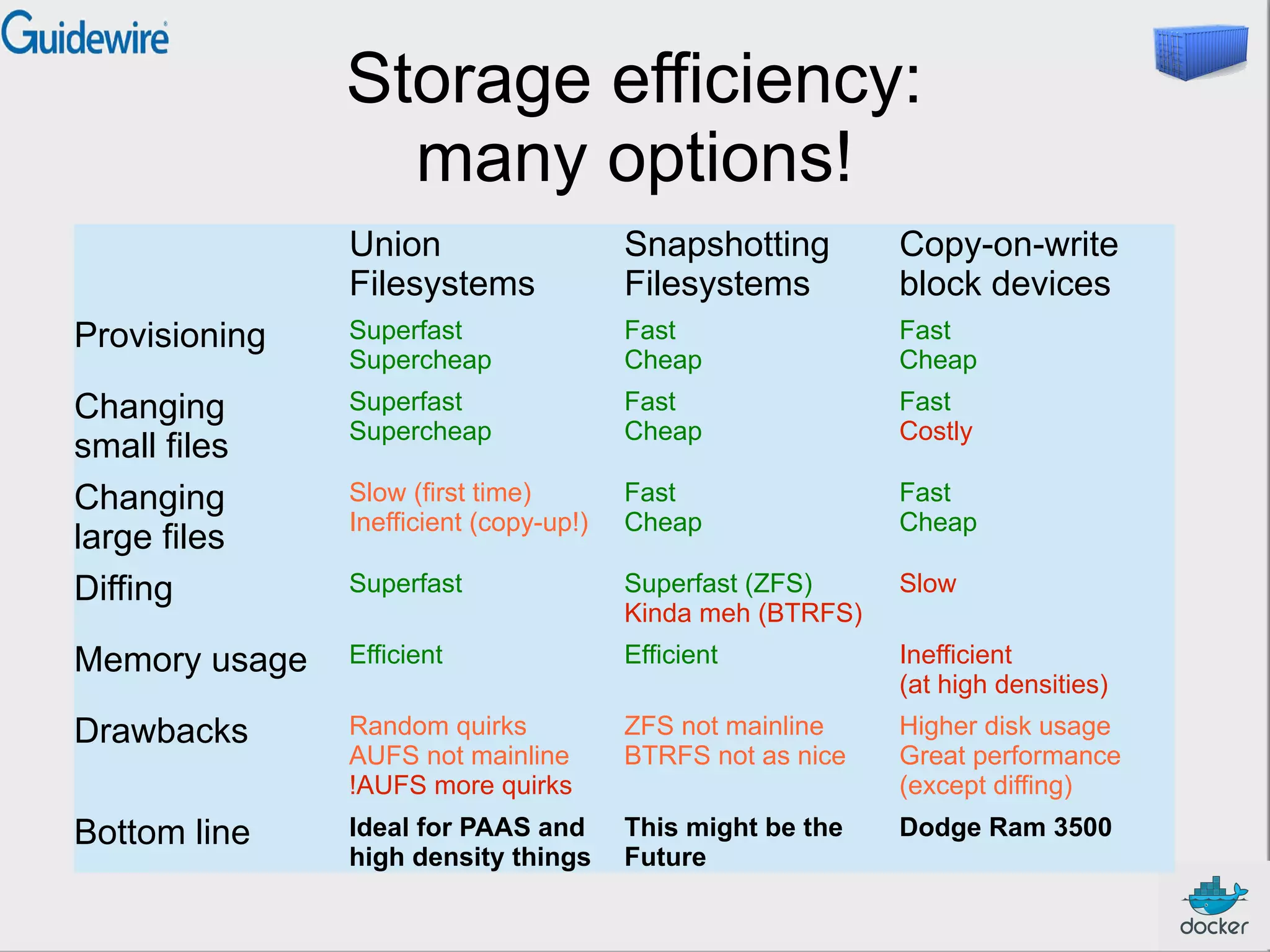
This document provides an introduction and overview of Docker and containers. It discusses that Docker is an open source tool that allows applications to be packaged with all their dependencies and run as isolated processes on any machine. Containers provide lightweight virtualization that improves efficiency by sharing resources but still isolating processes. The document outlines how Docker uses containers powered by Linux namespaces and cgroups to package and deploy applications easily and consistently across environments.















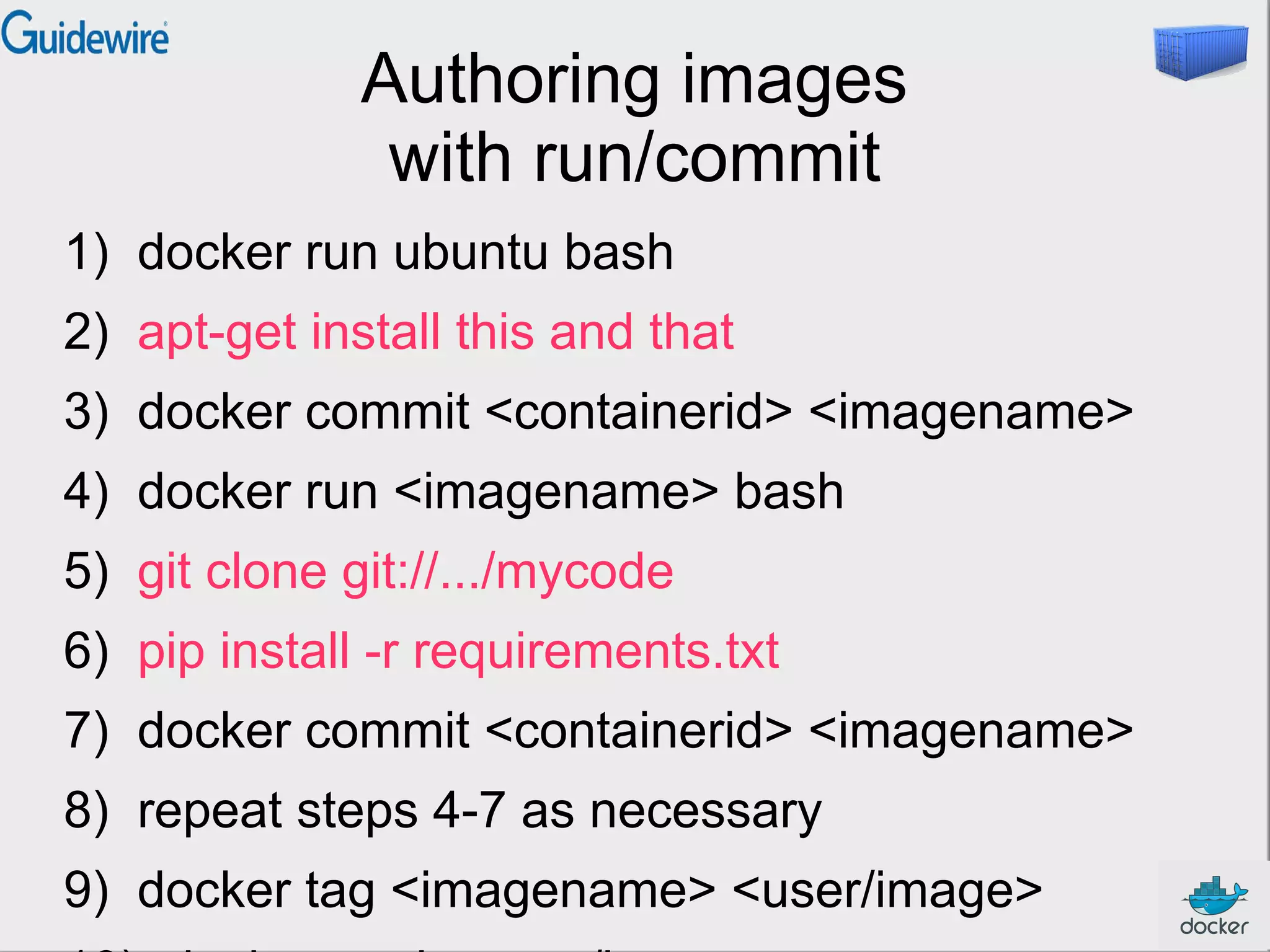
![Authoring images
with a Dockerfile
FROM ubuntu
RUN apt-get -y update
RUN apt-get install -y
RUN apt-get install -y
erlang-base-hipe ...
RUN apt-get install -y
libtool ...
RUN apt-get install -y
g++
erlang-dev erlang-manpages
libmozjs185-dev libicu-dev
make wget
RUN wget http://.../apache-couchdb-1.3.1.tar.gz | tar
-C /tmp -zxfRUN cd /tmp/apache-couchdb-* && ./configure && make
install
RUN printf "[httpd]nport = 8101nbind_address =
0.0.0.0" >](https://image.slidesharecdn.com/guidewire-2013-maintalk-131120112908-phpapp01/75/Introduction-to-Docker-at-SF-Peninsula-Software-Development-Meetup-Guidewire-37-2048.jpg)