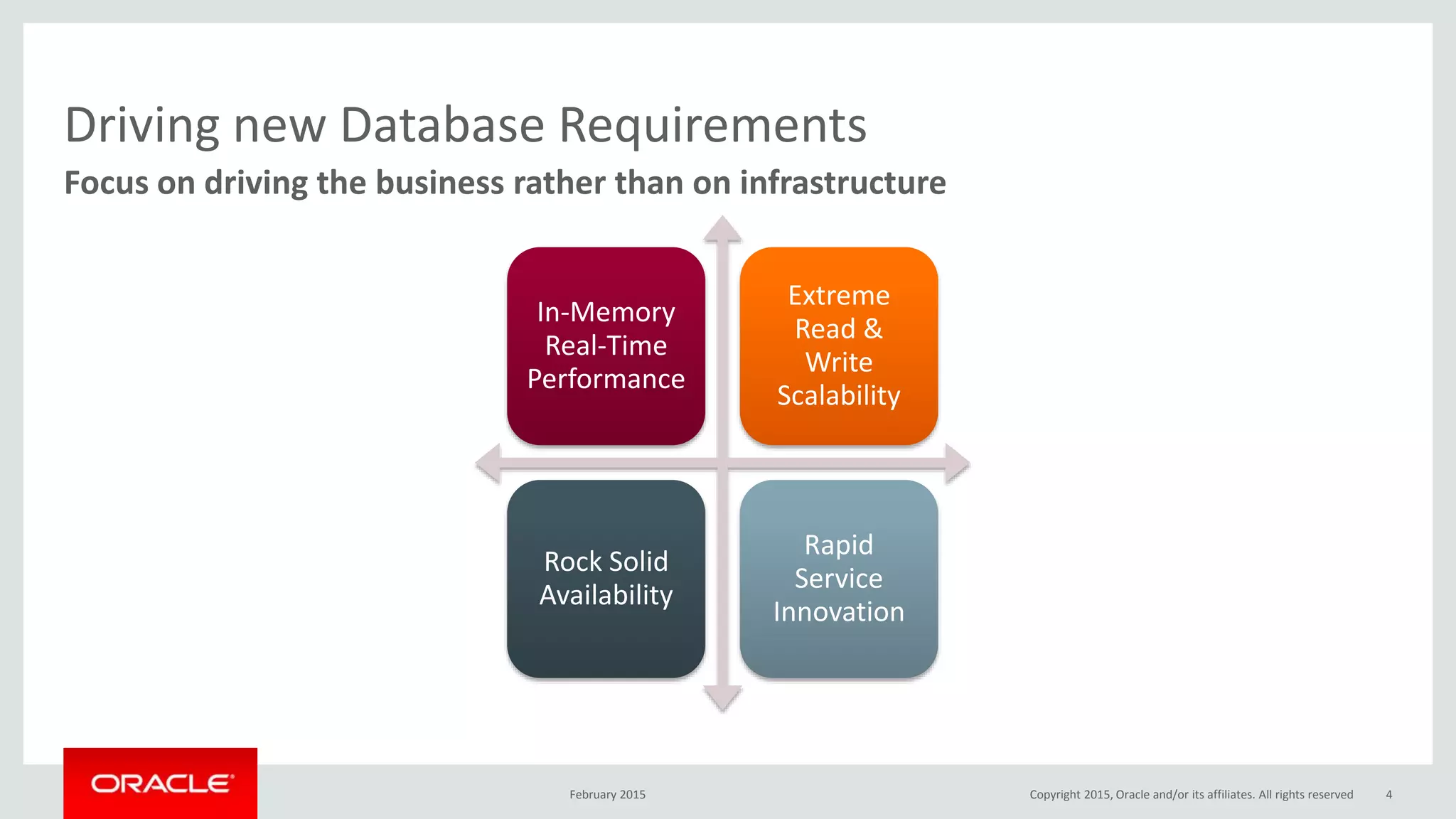
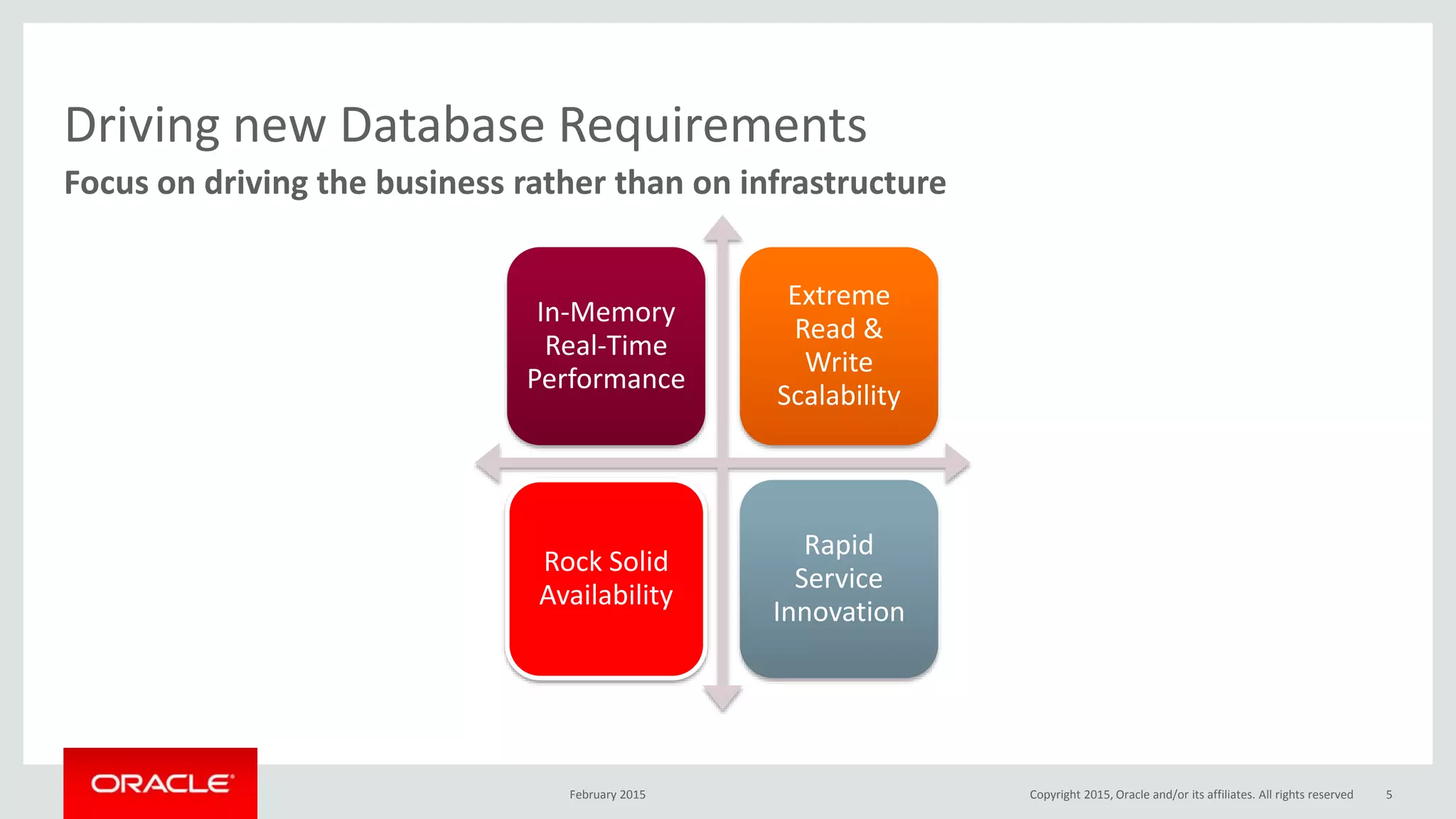
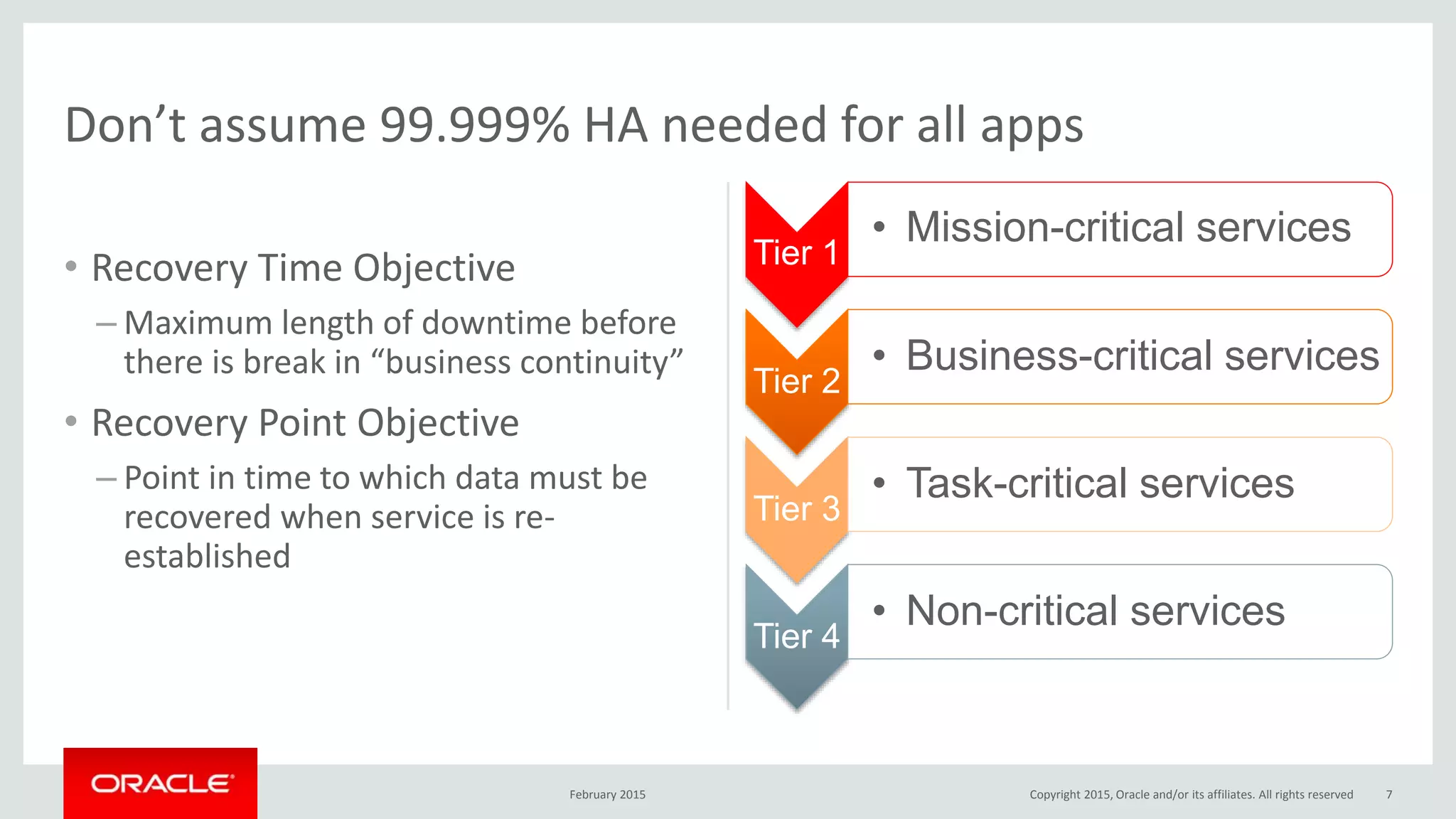
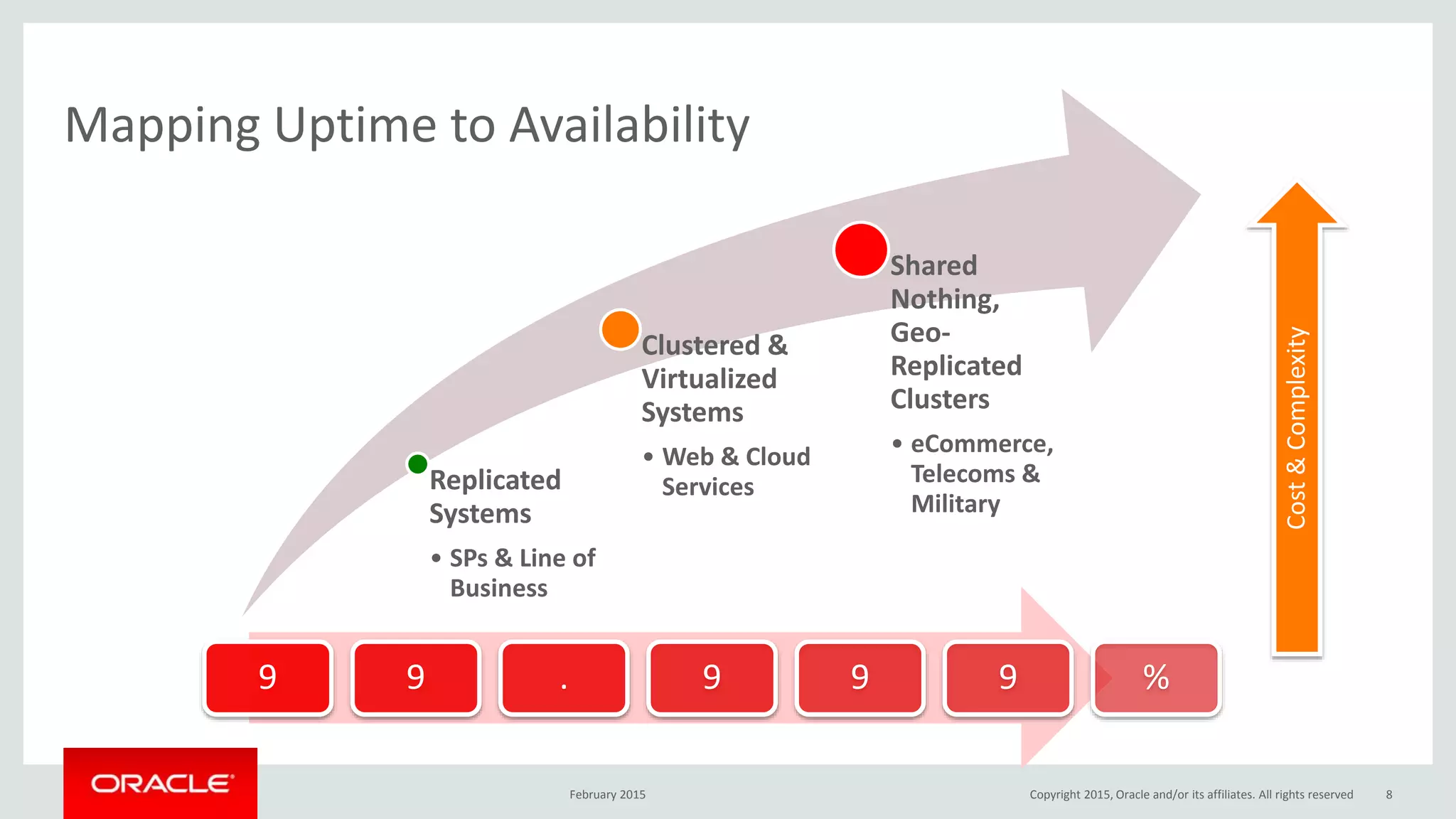
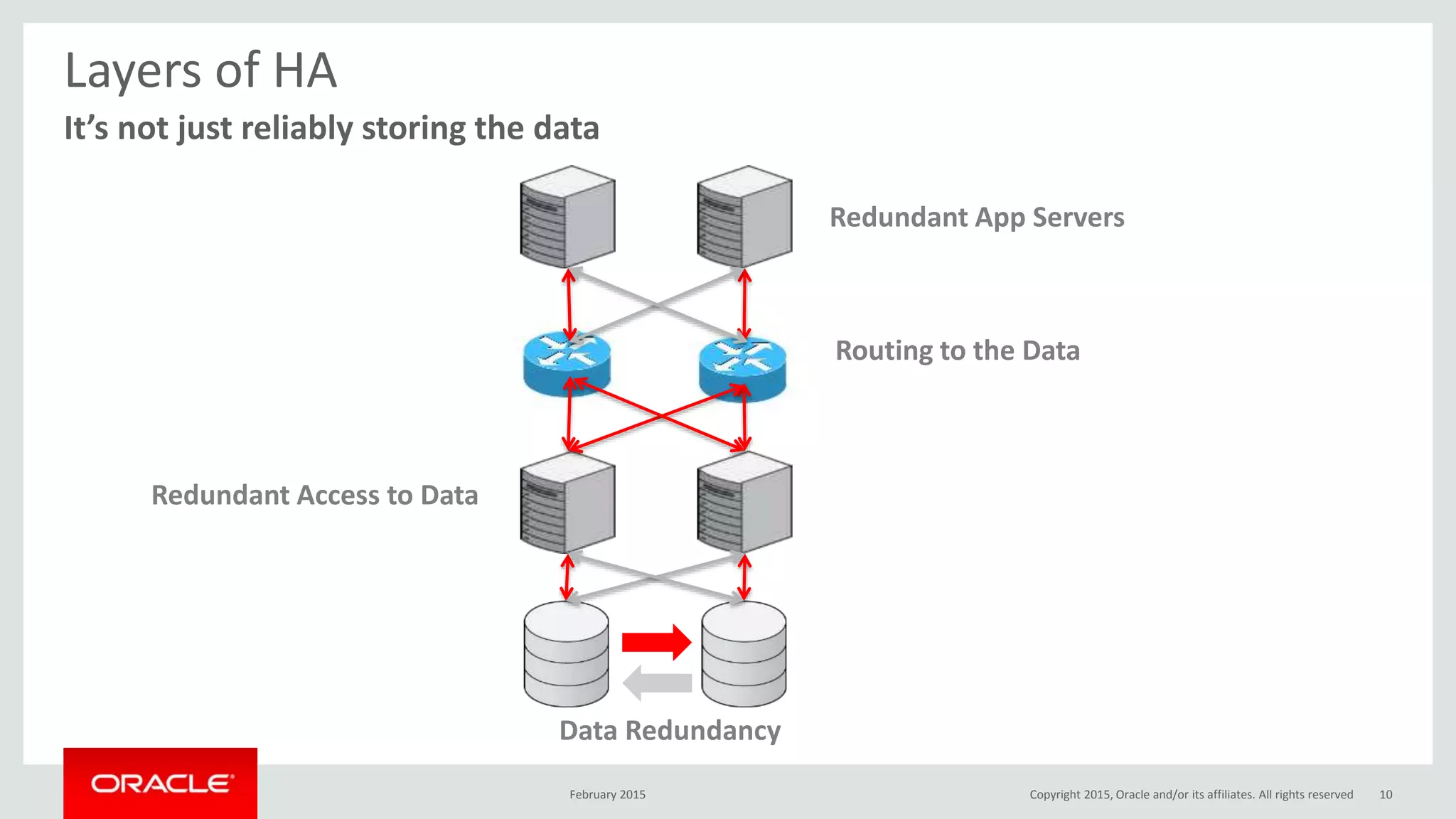
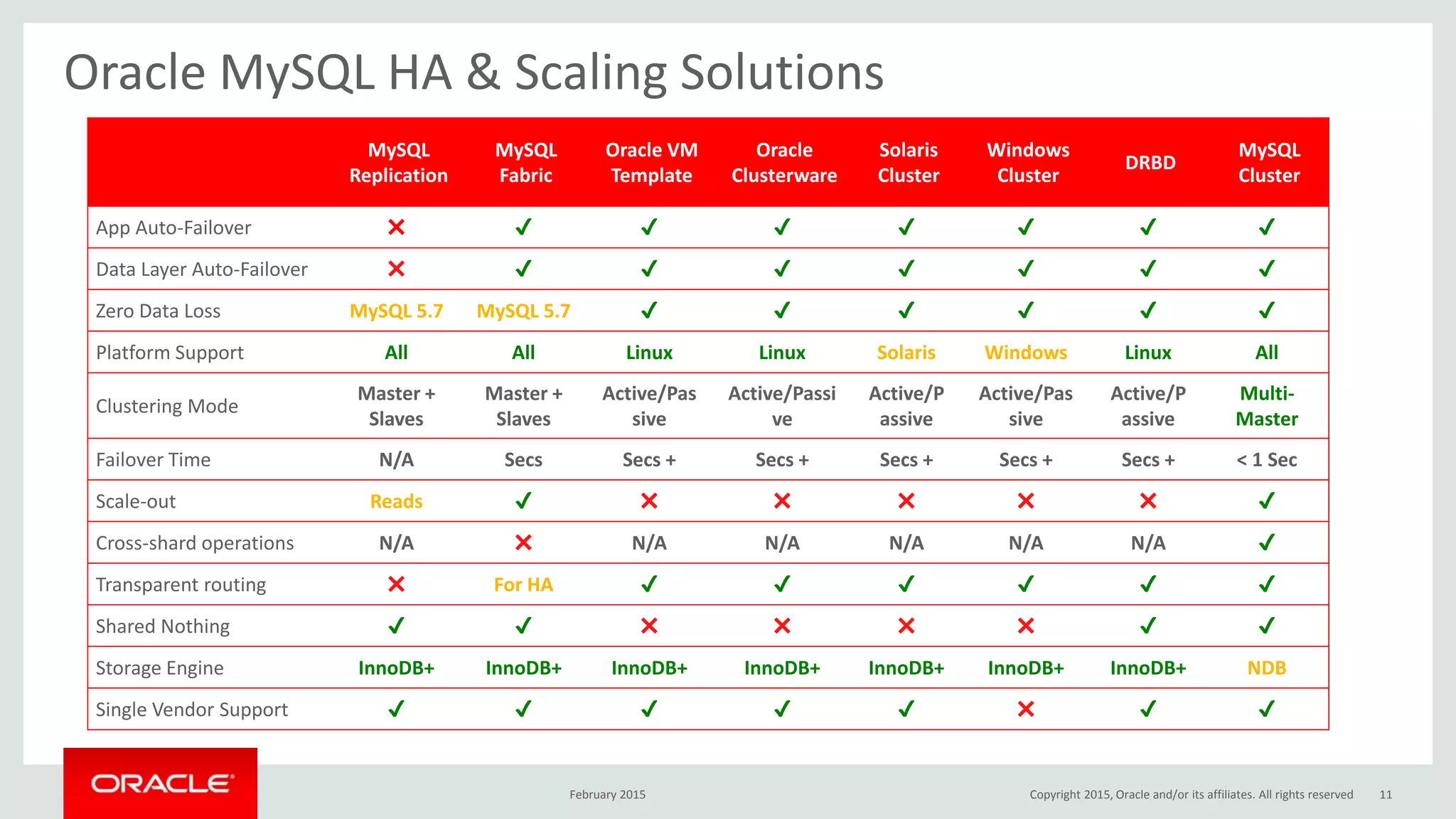
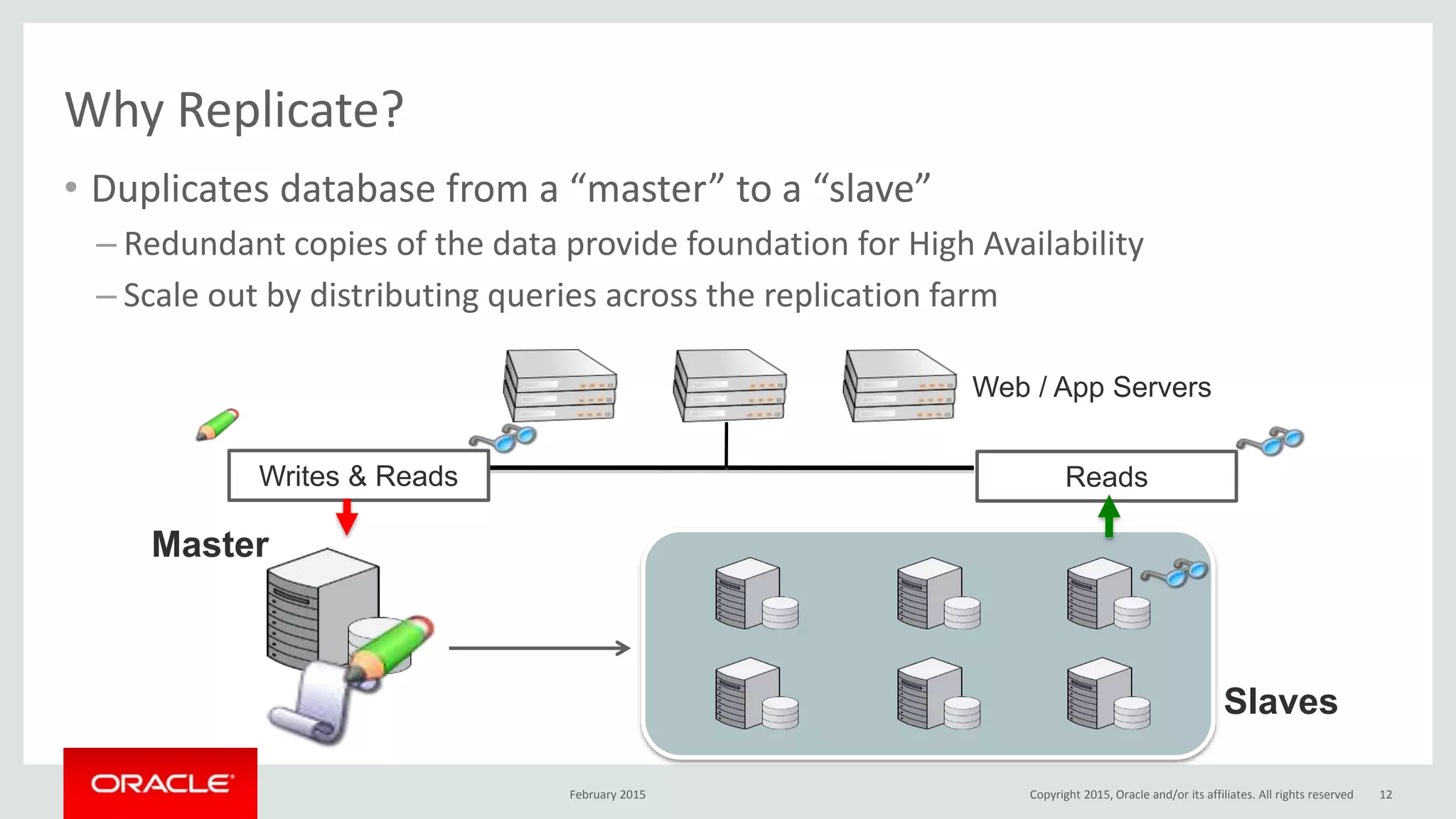
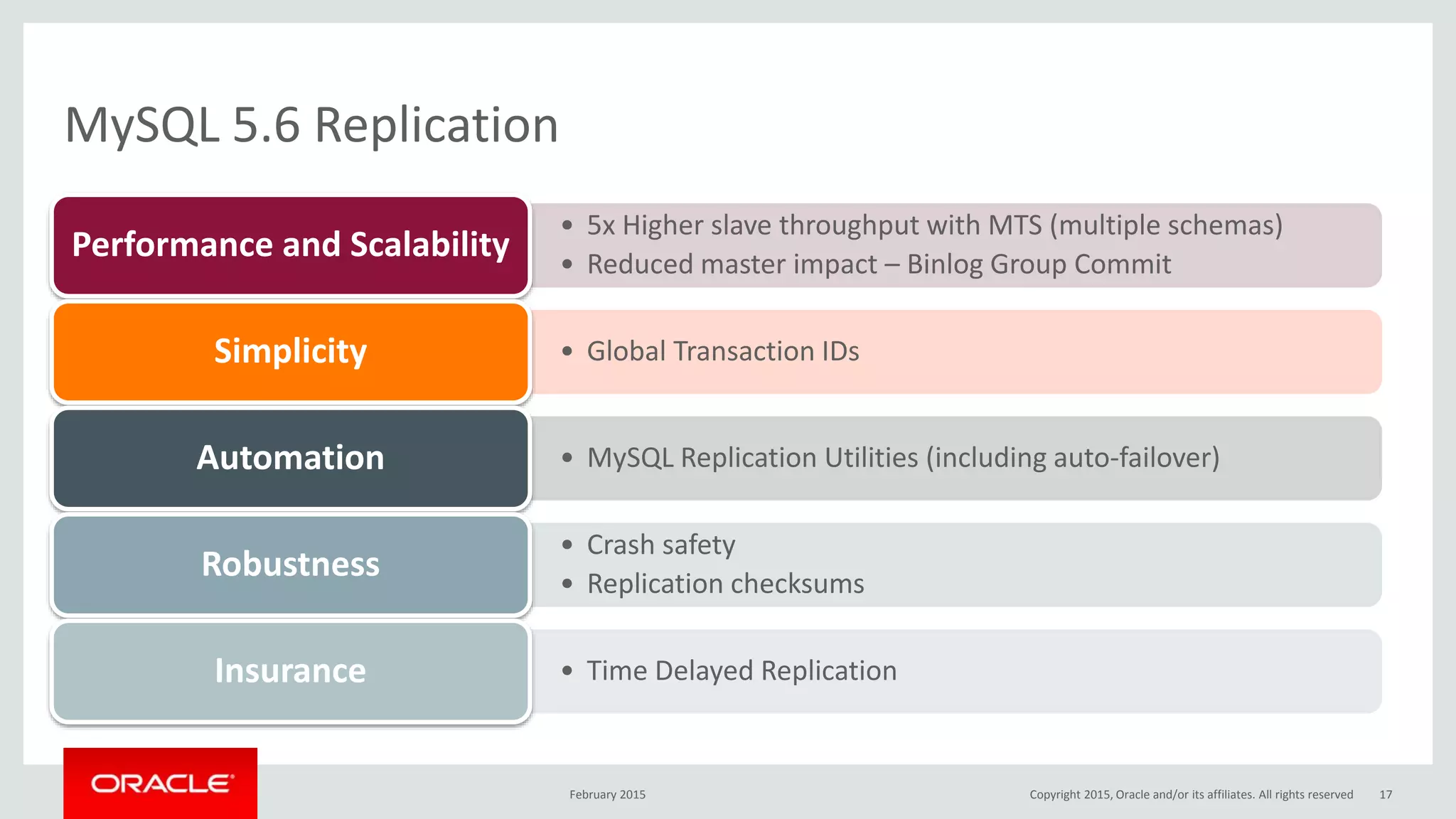
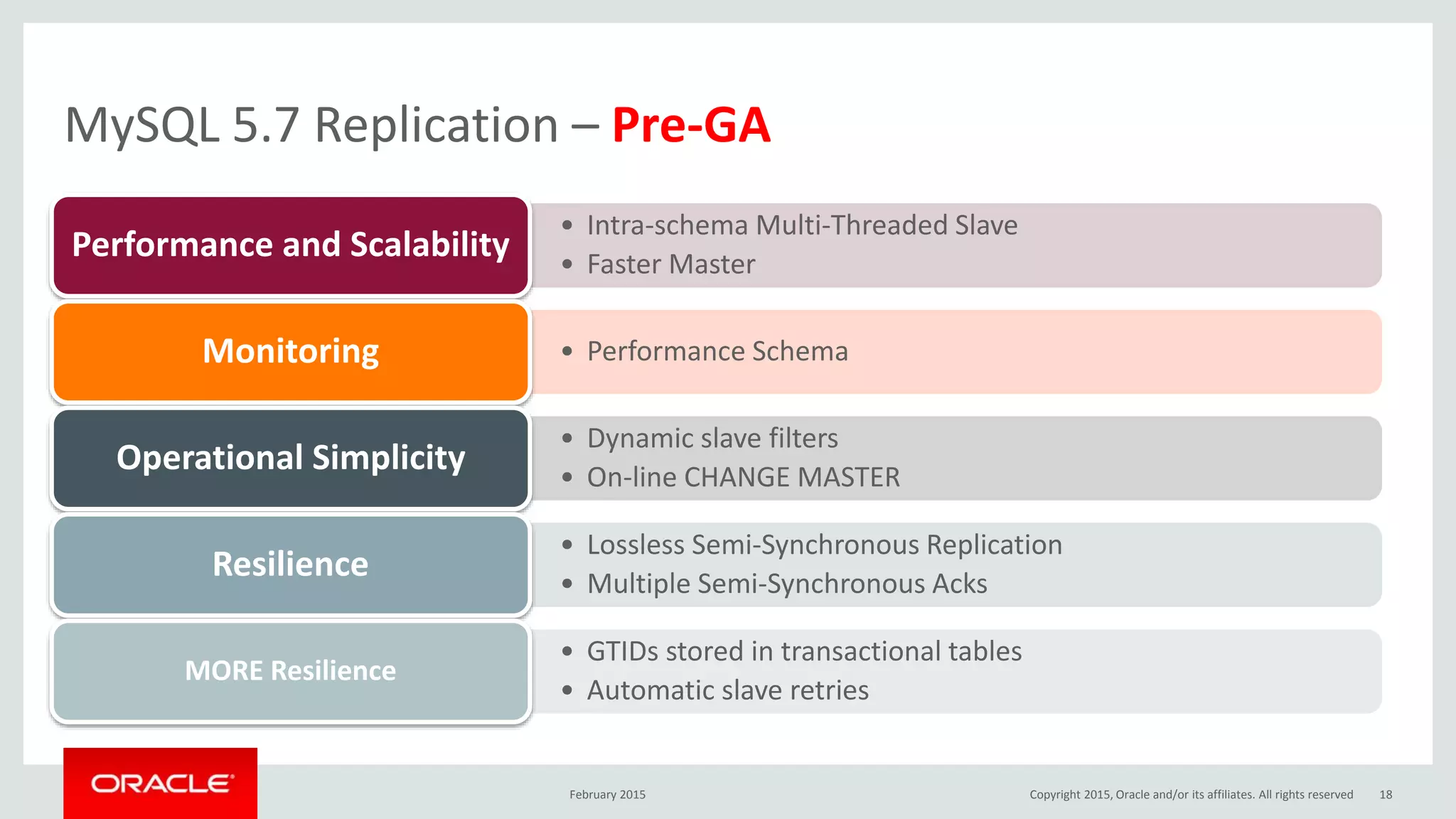
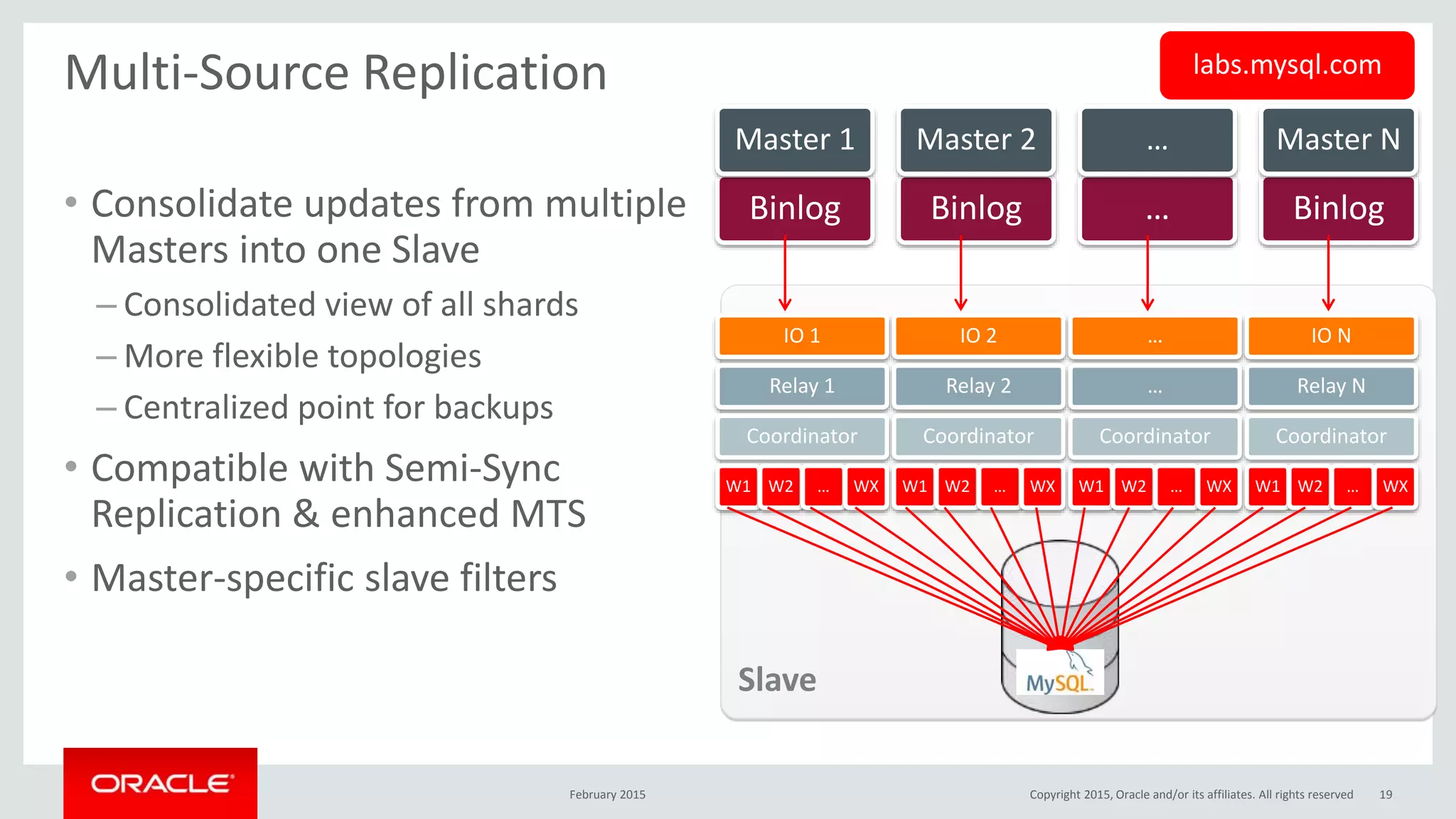
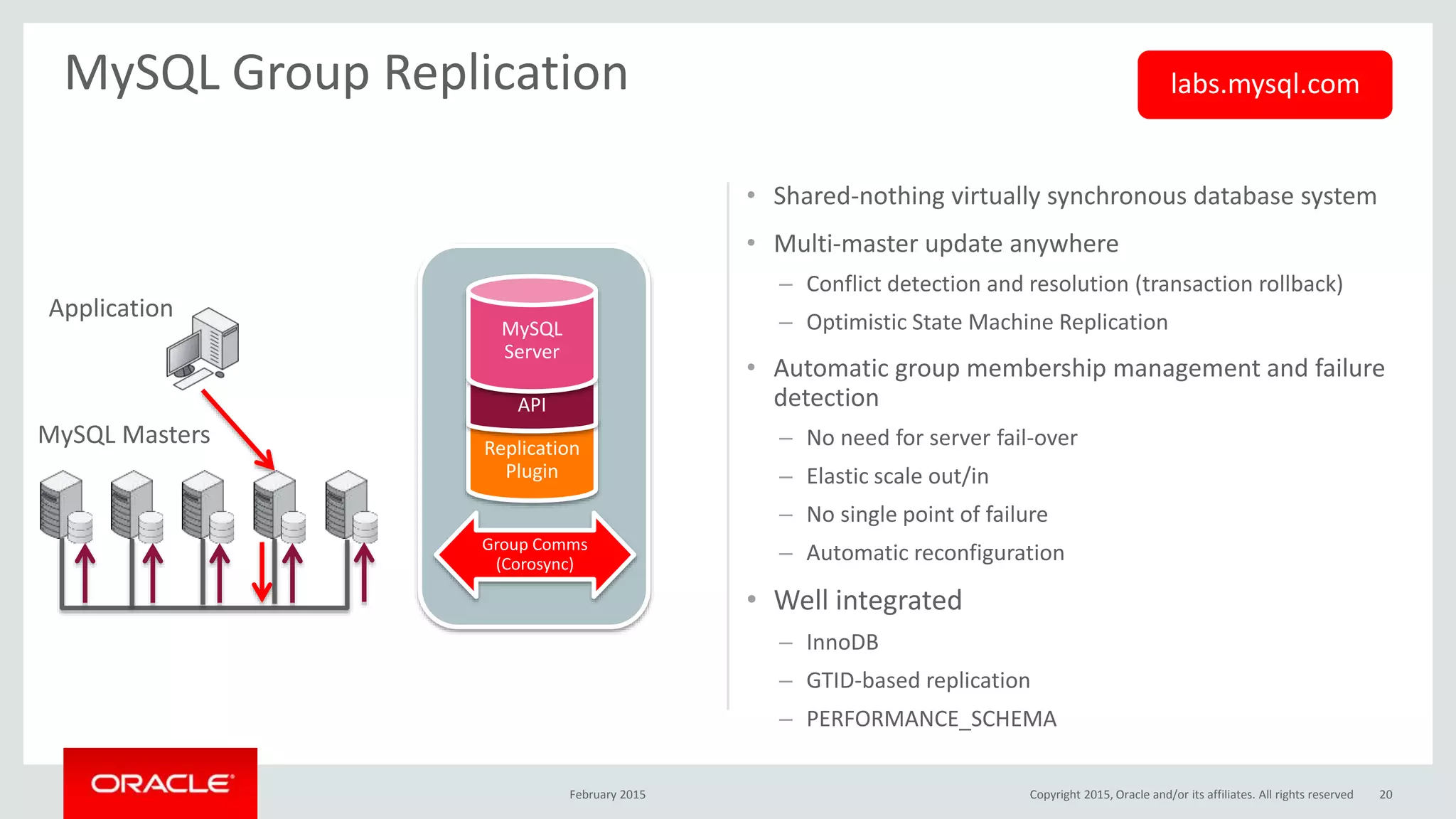
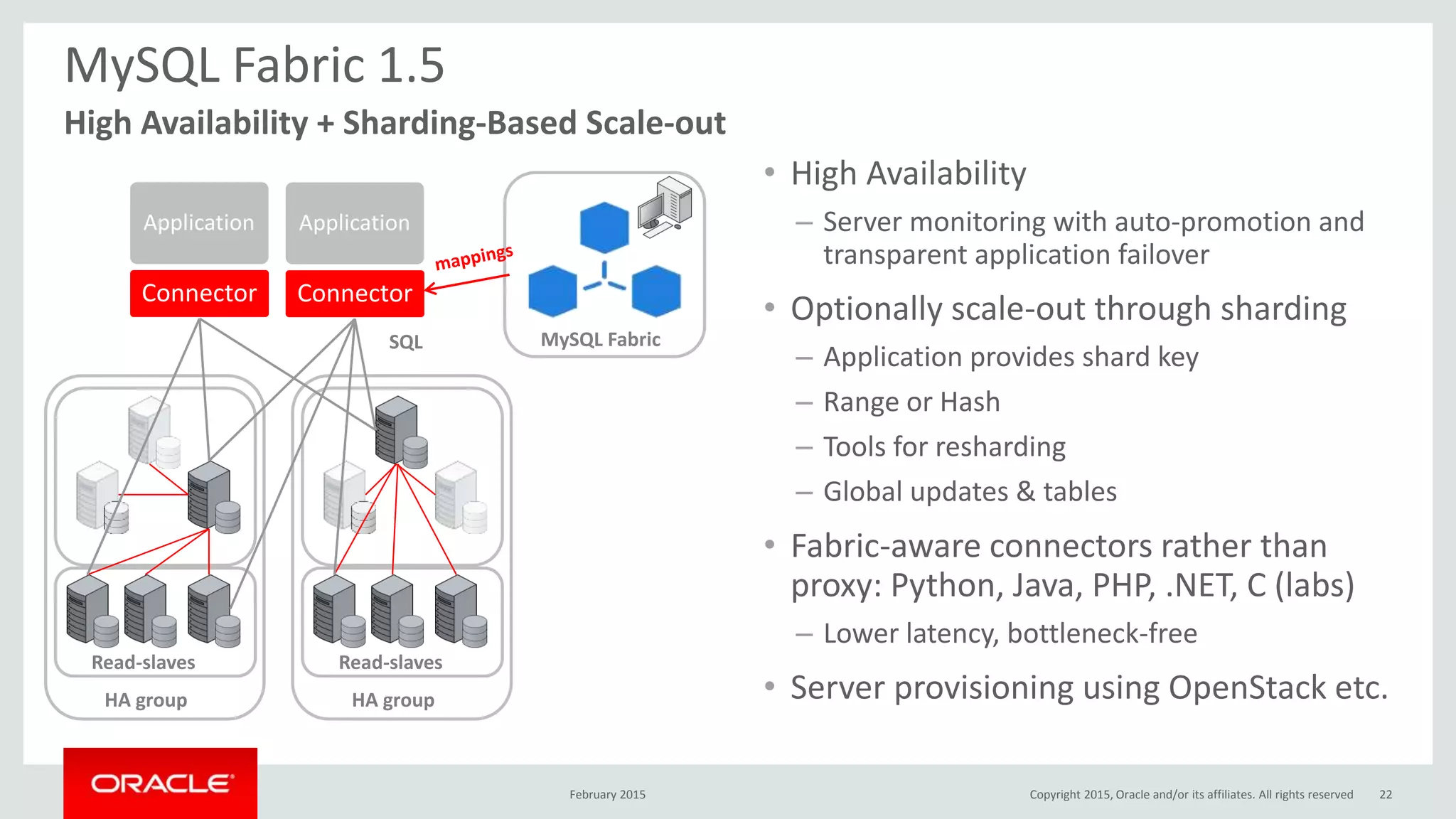
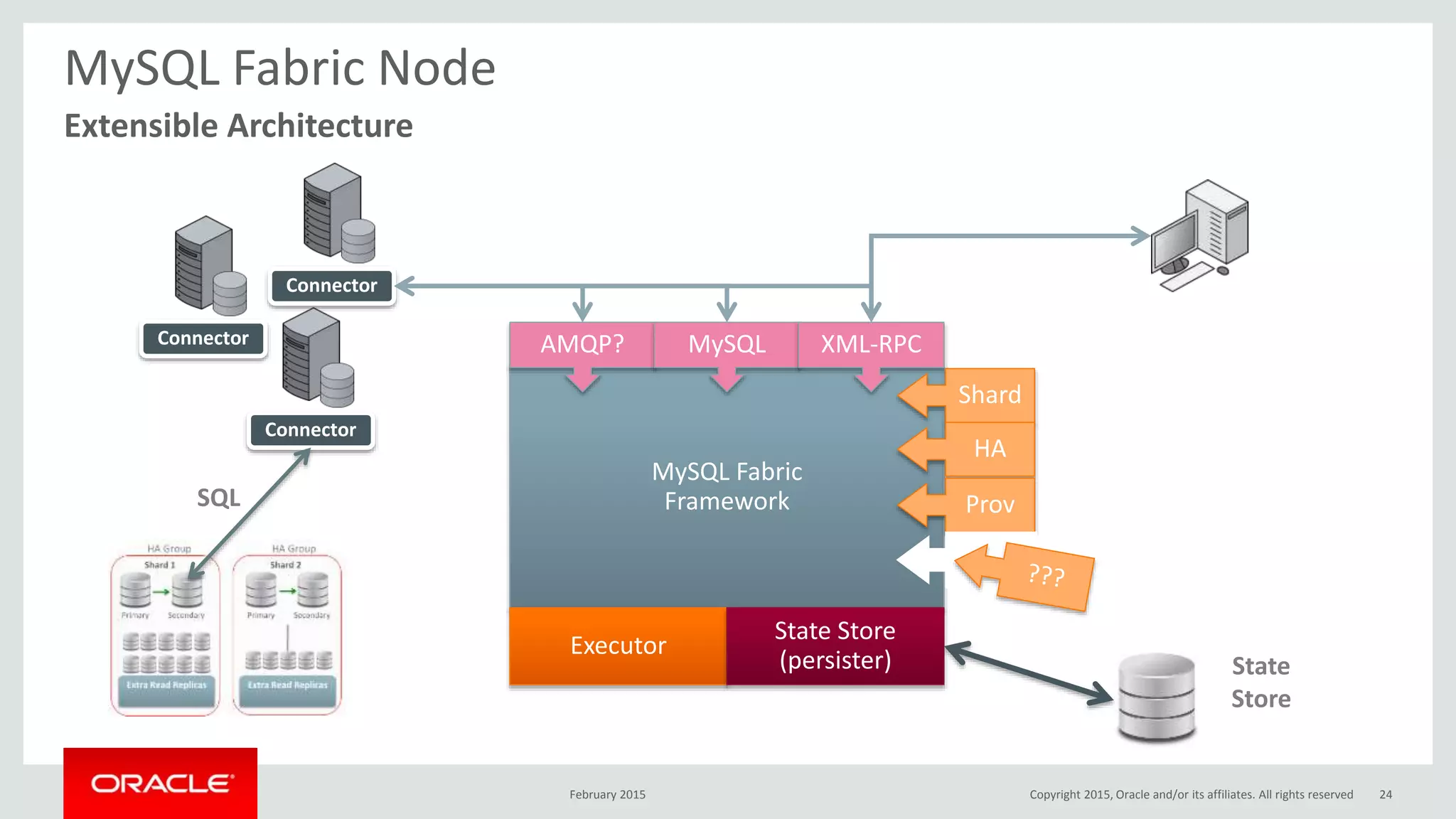
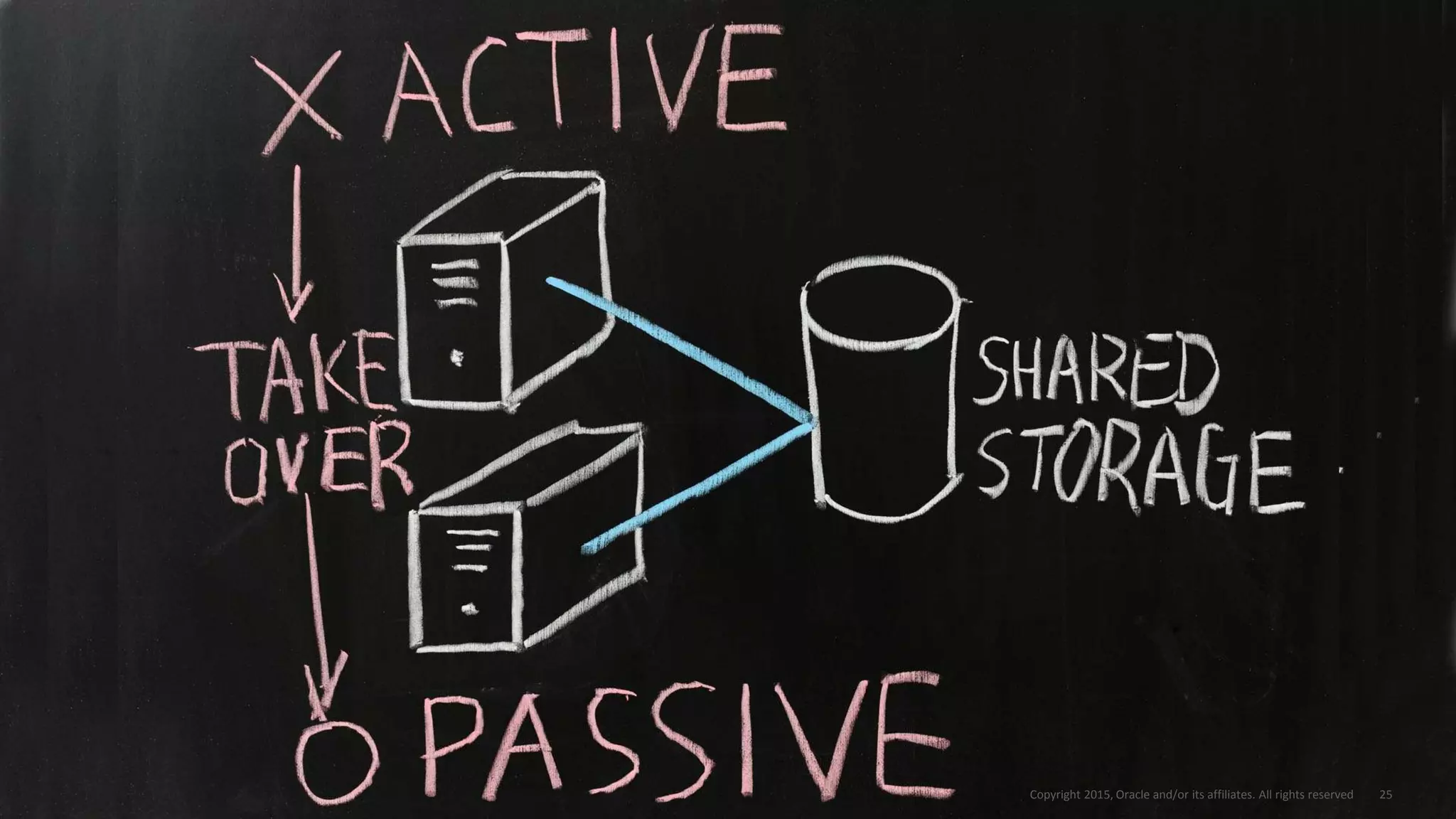
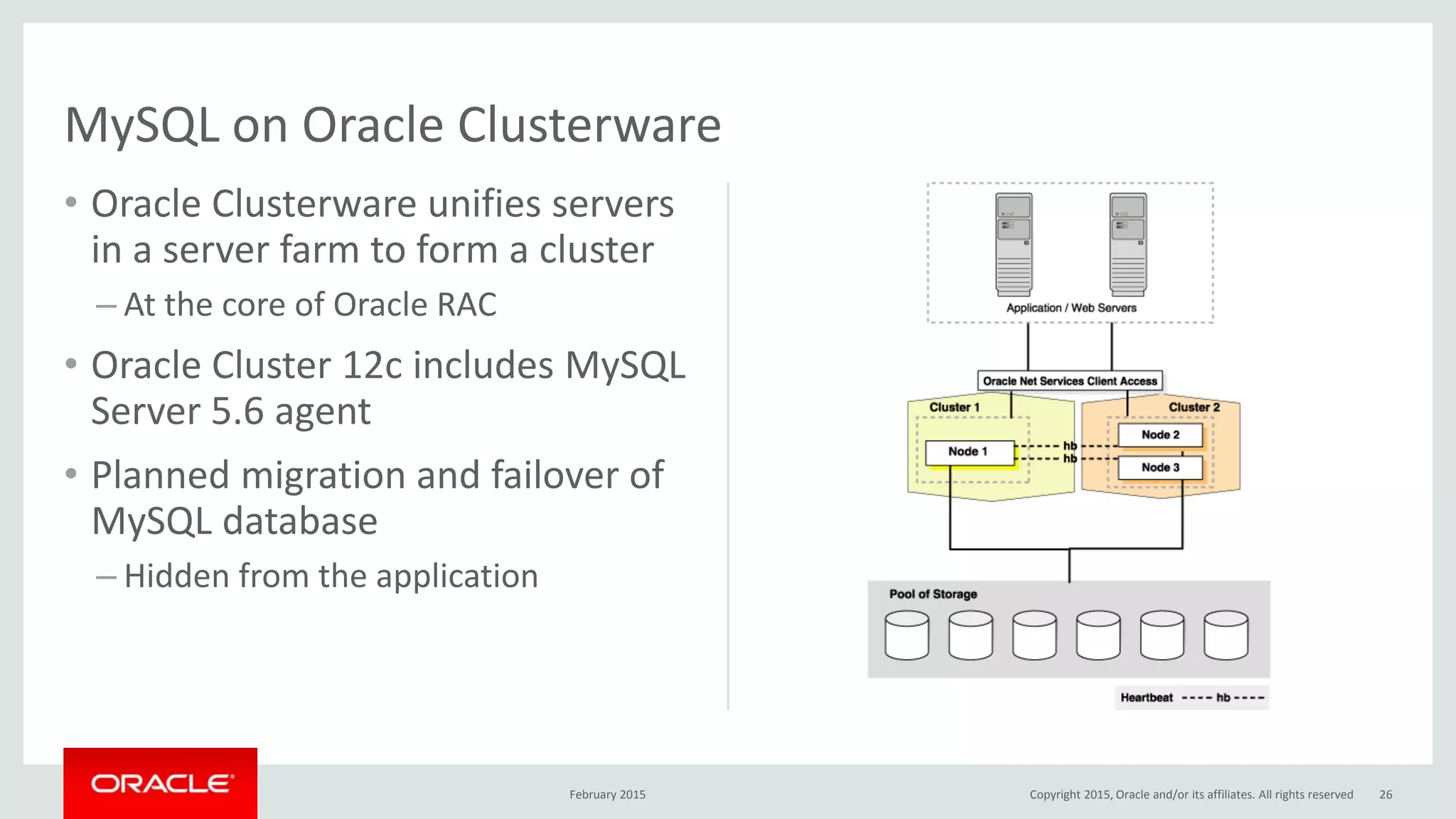
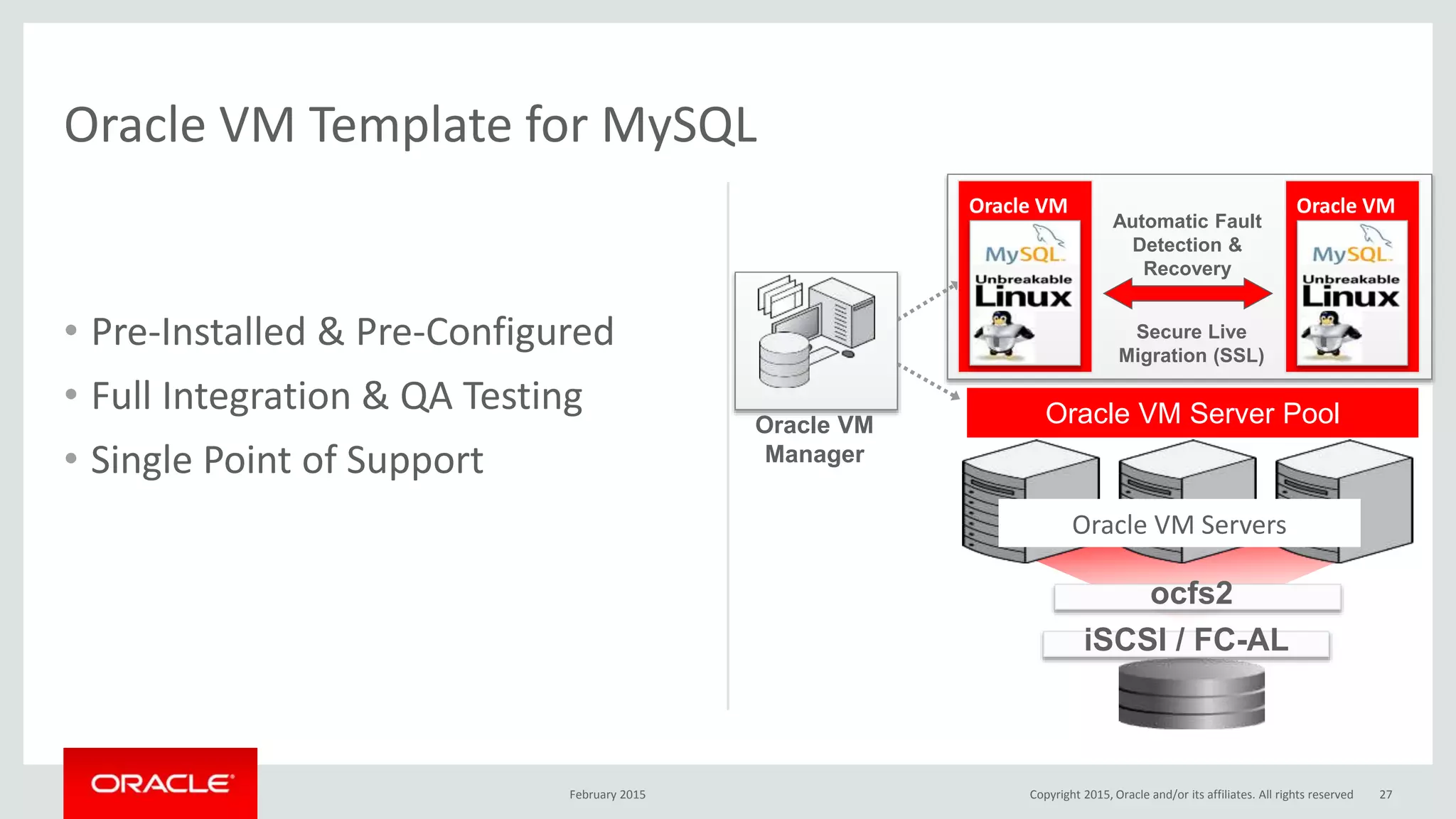
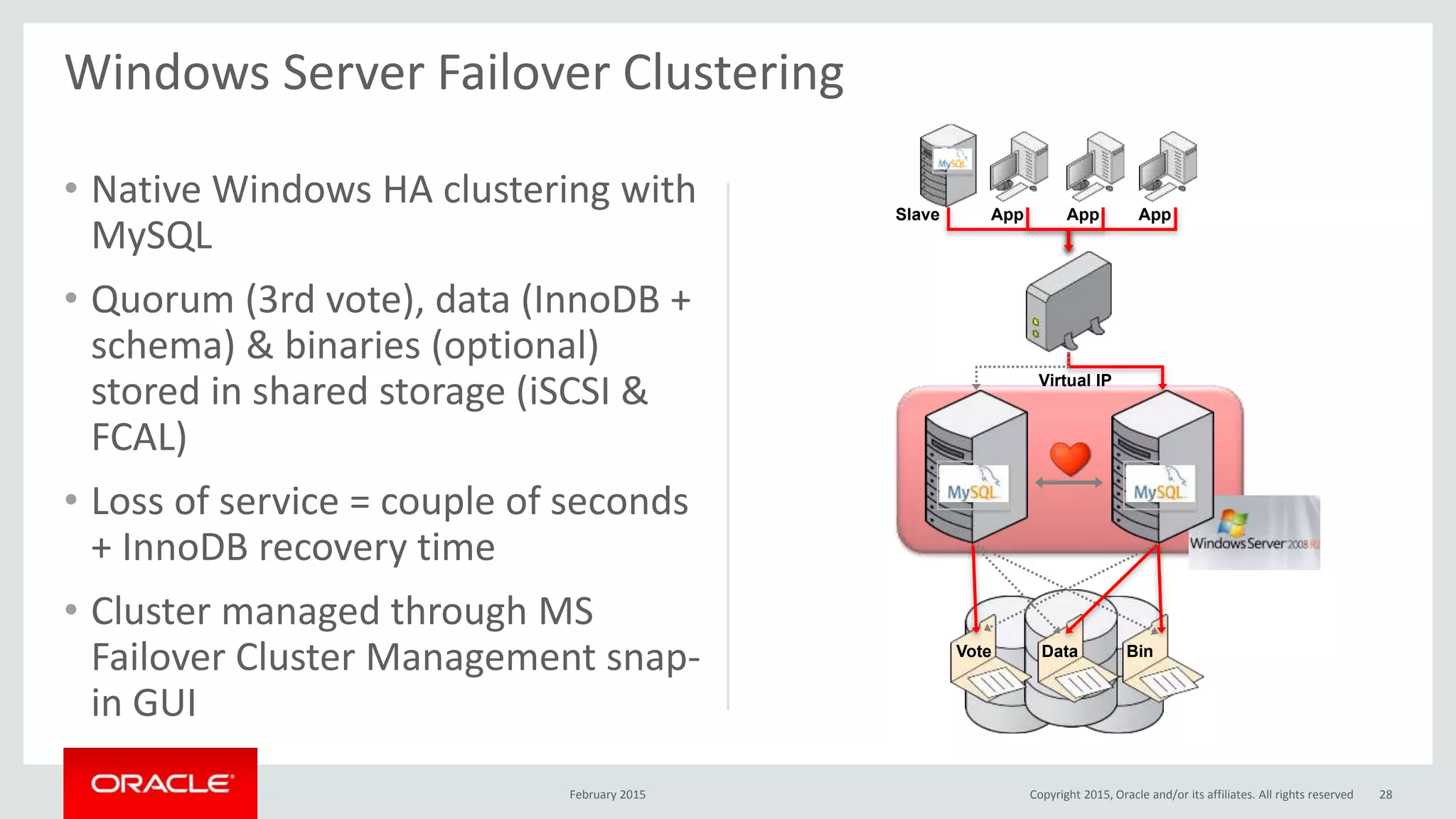
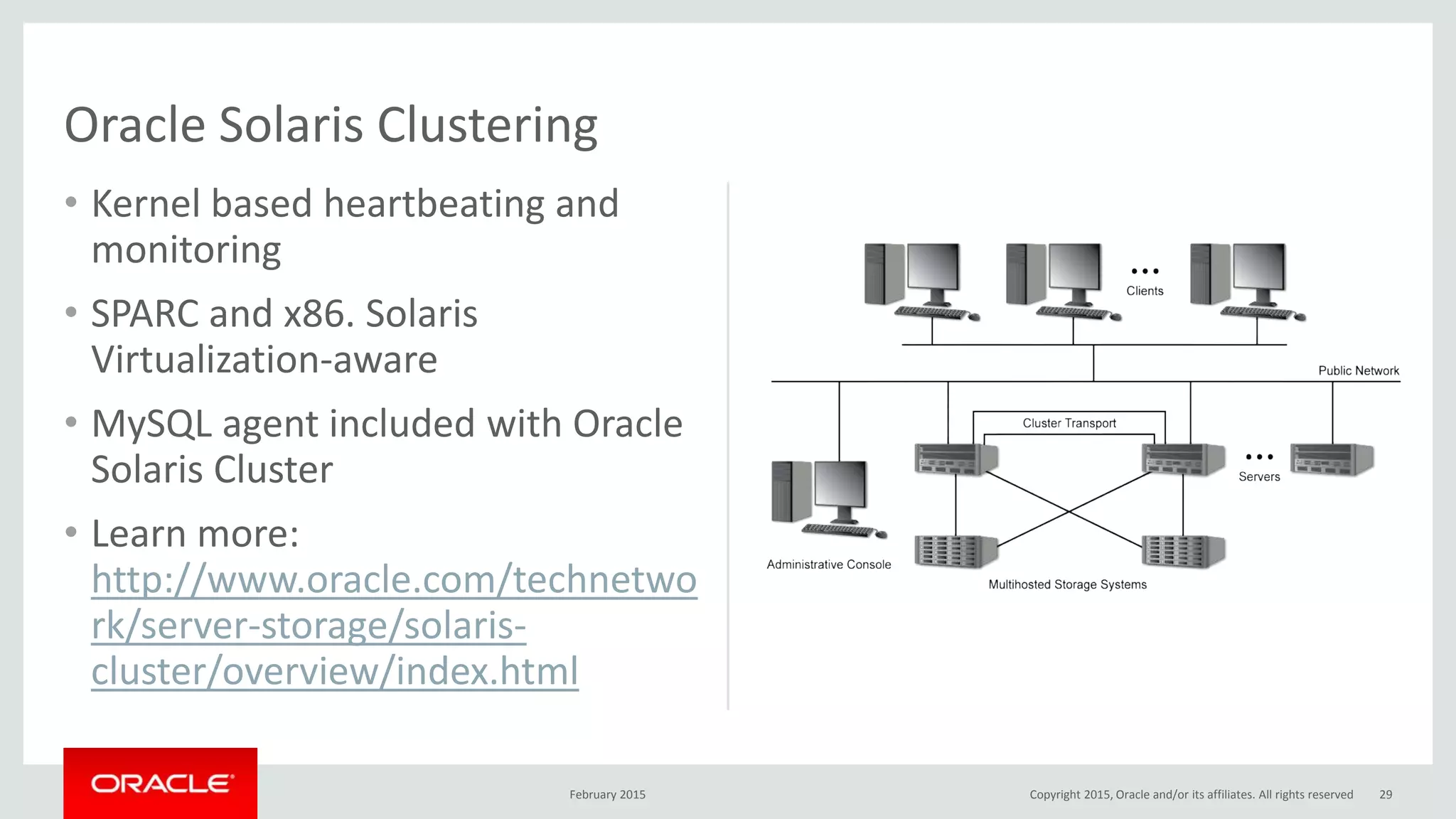
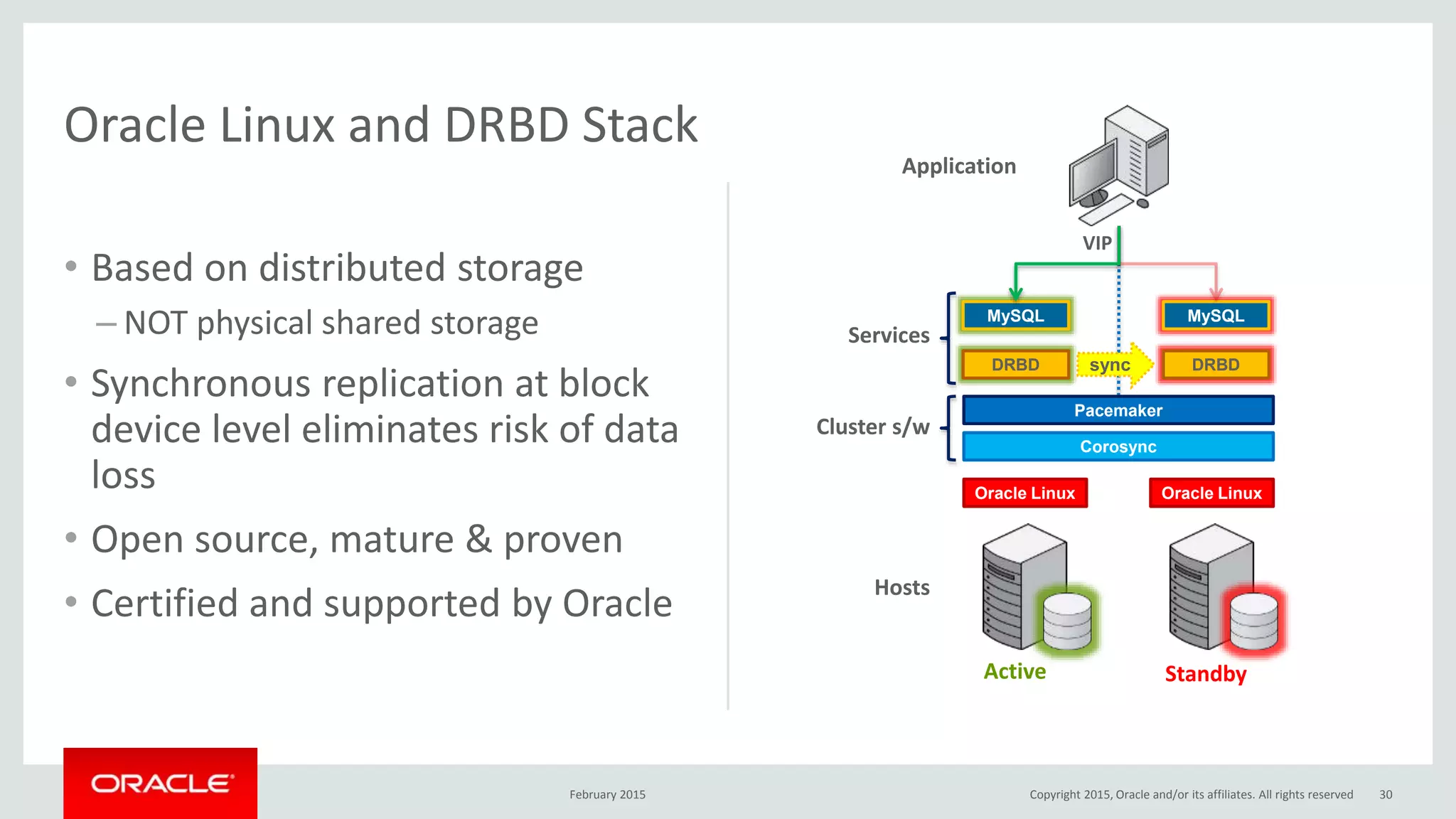
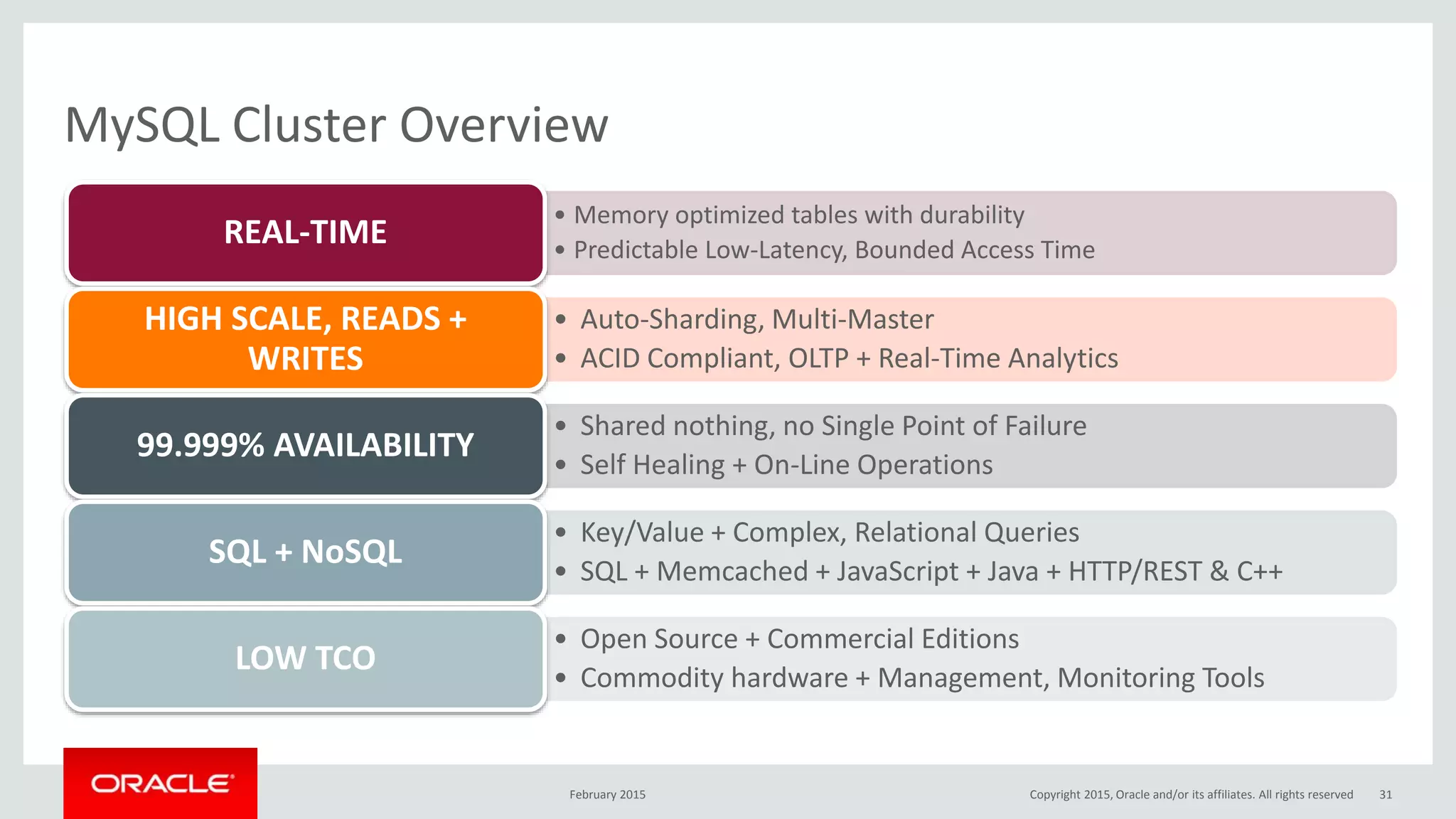
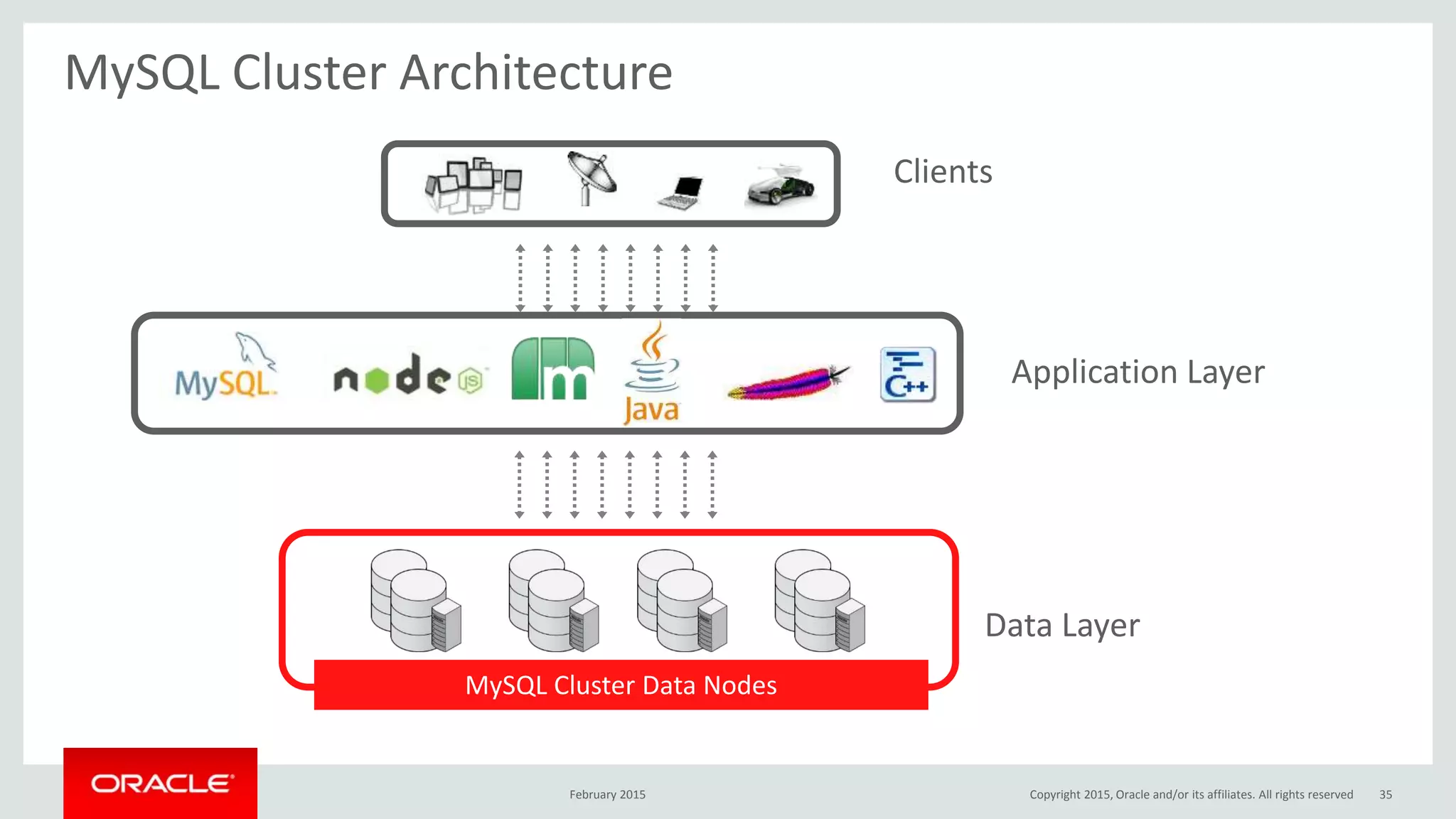
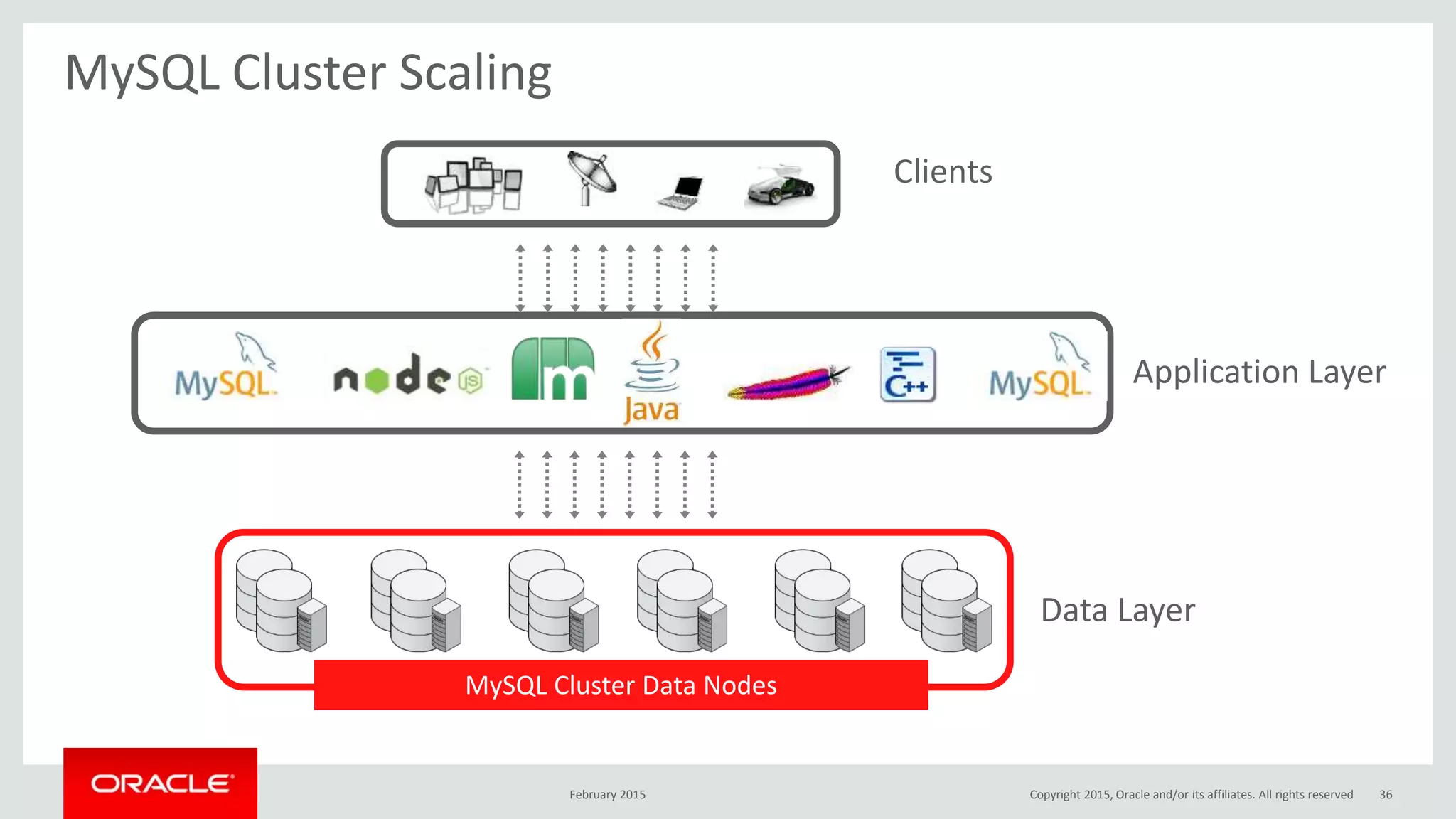
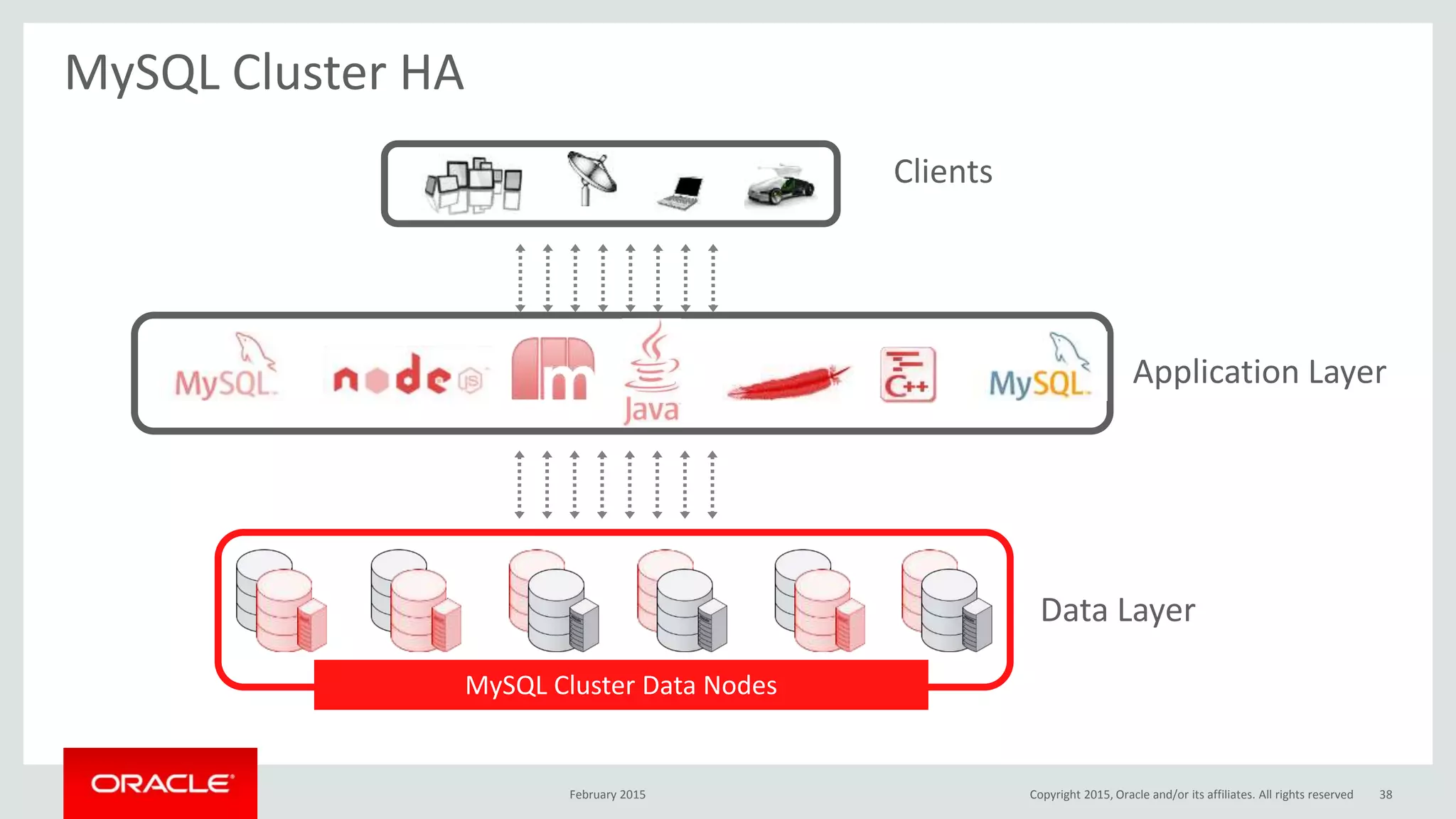
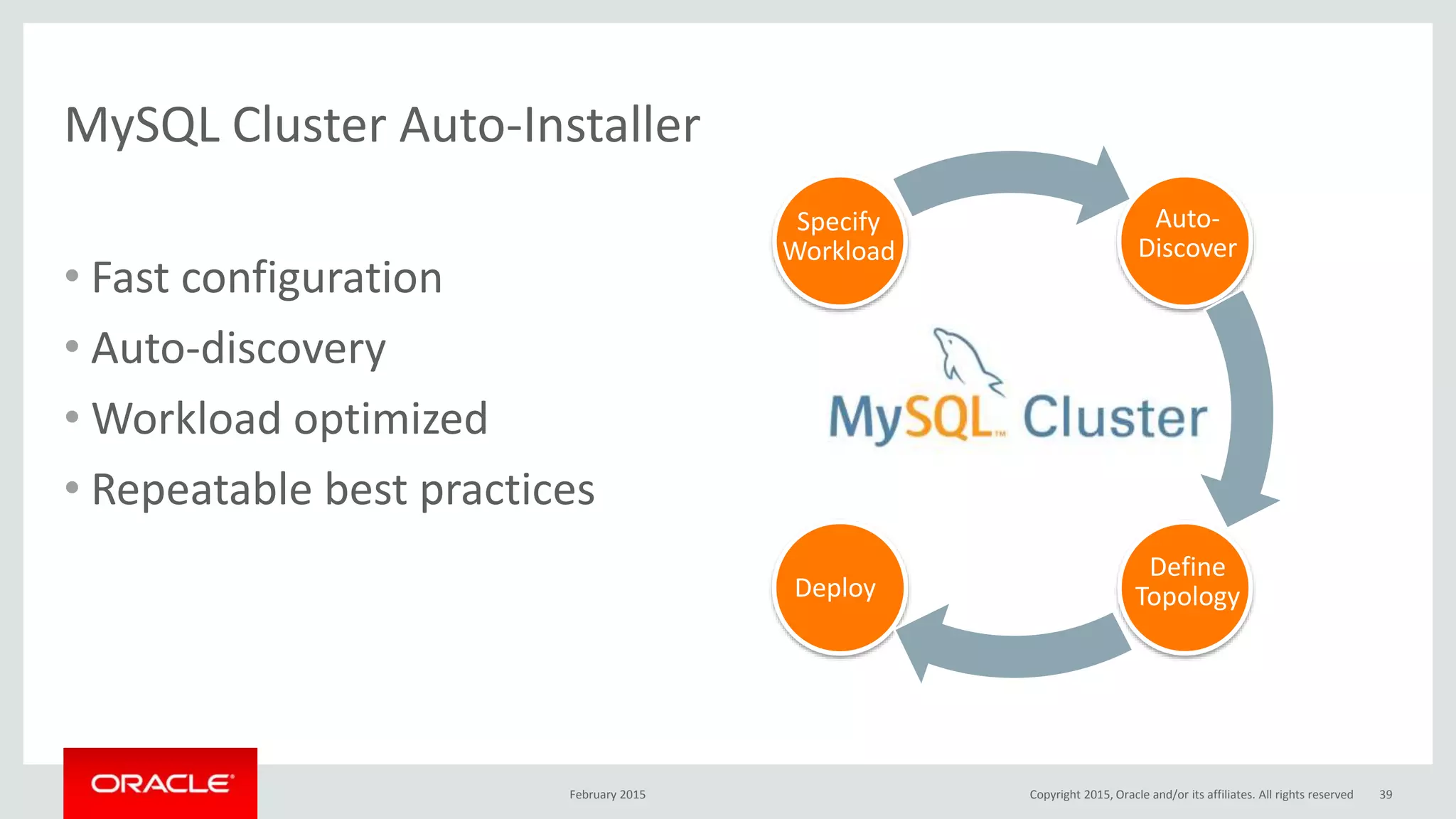
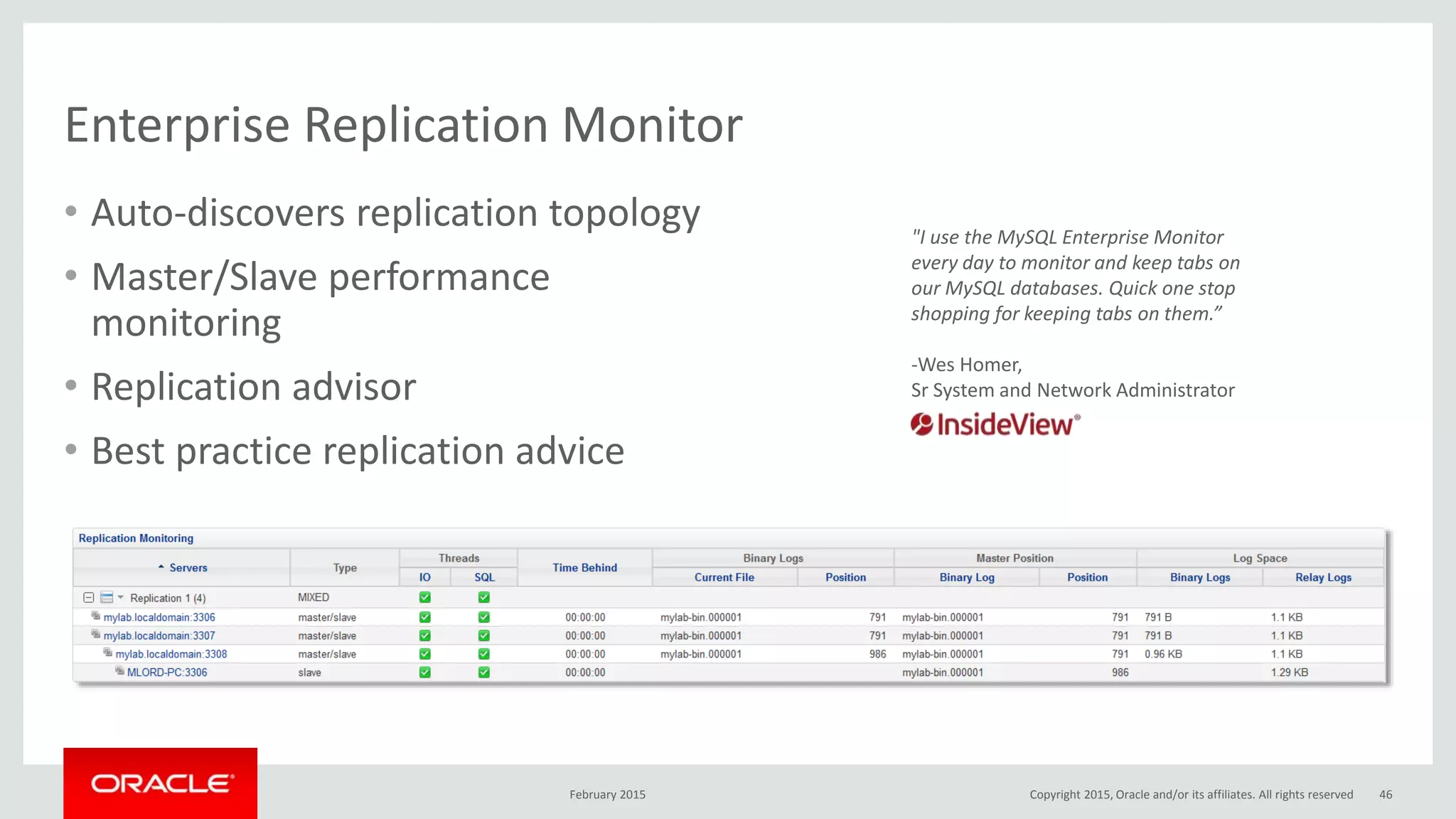
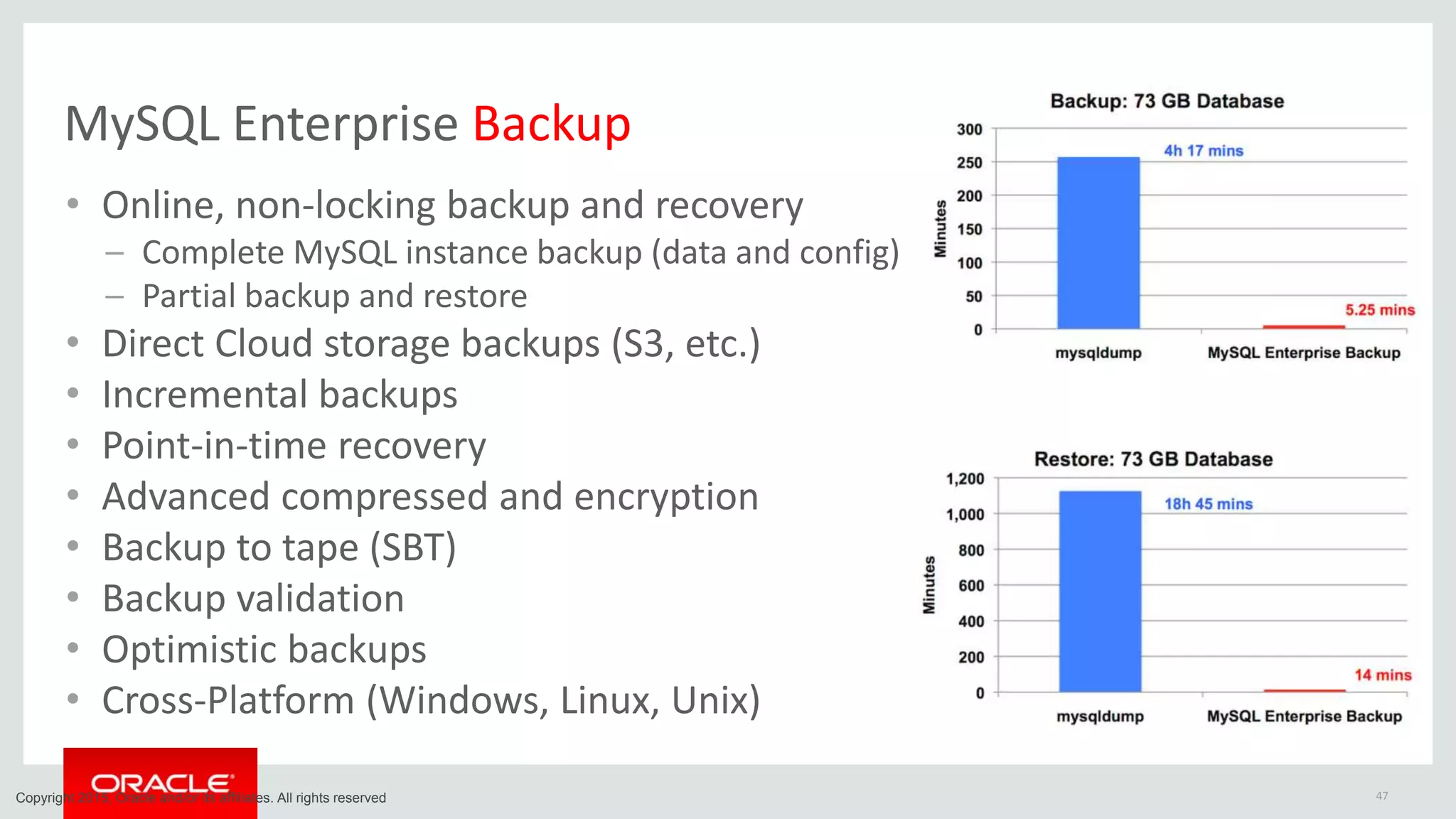
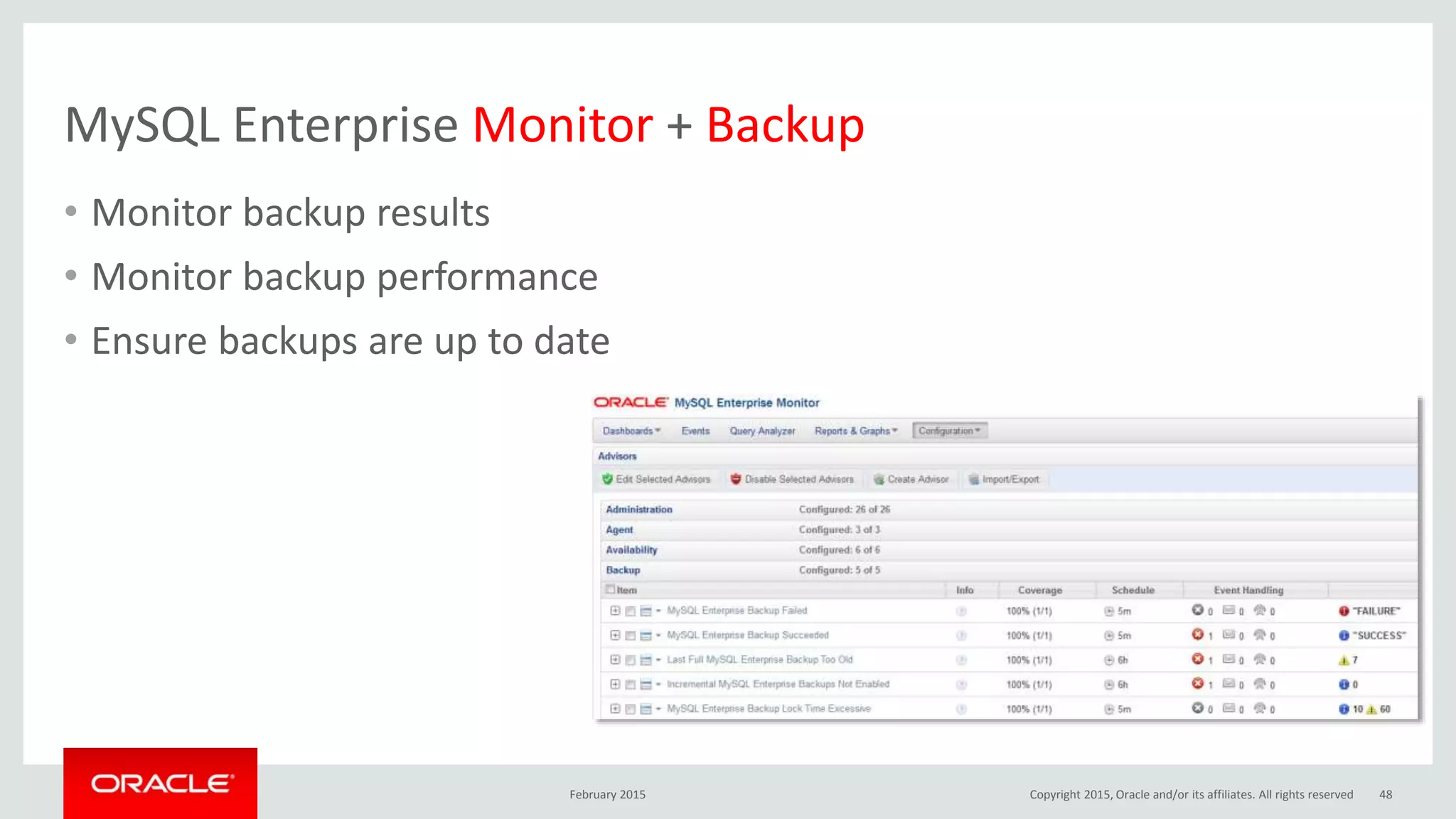
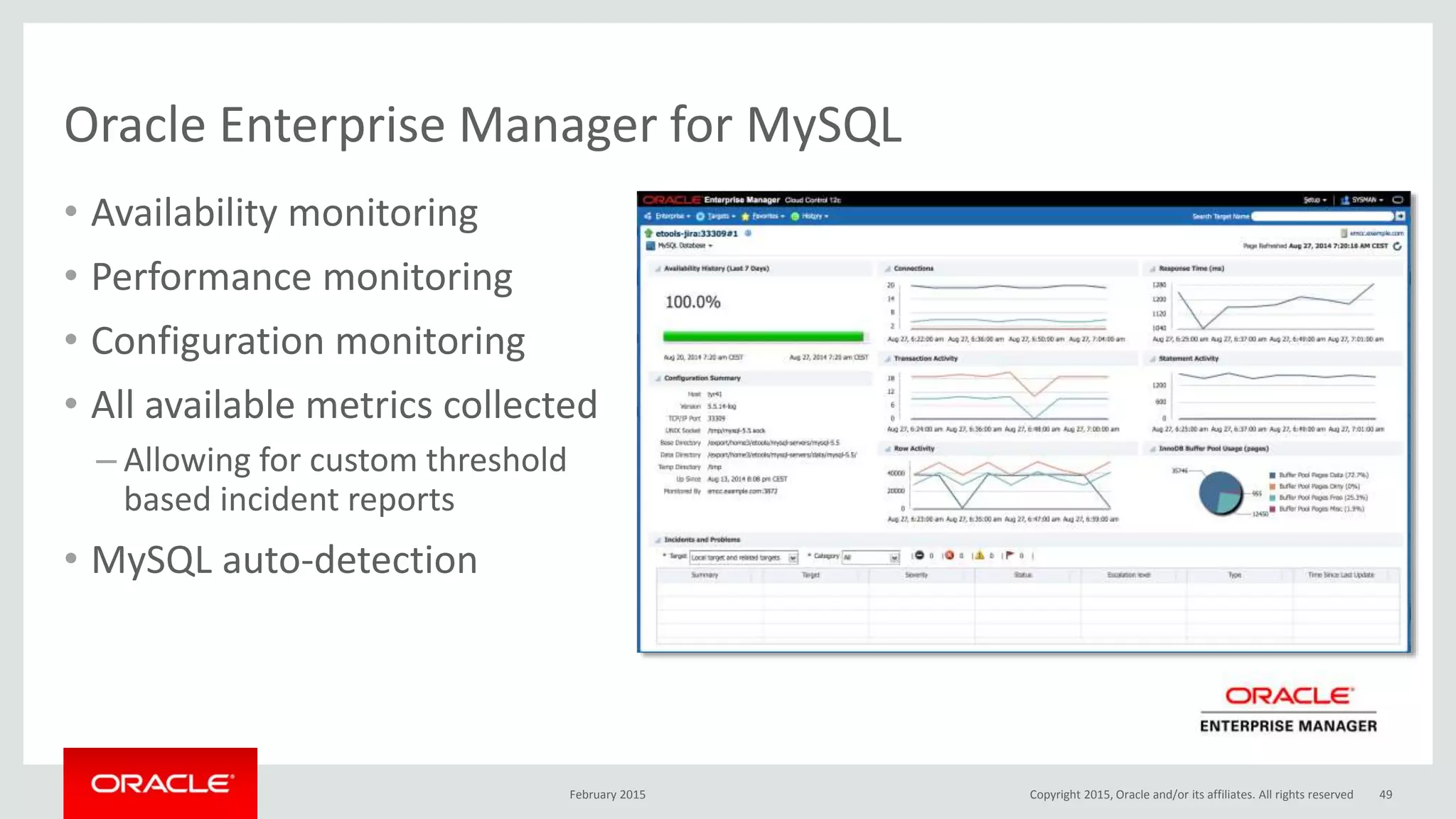
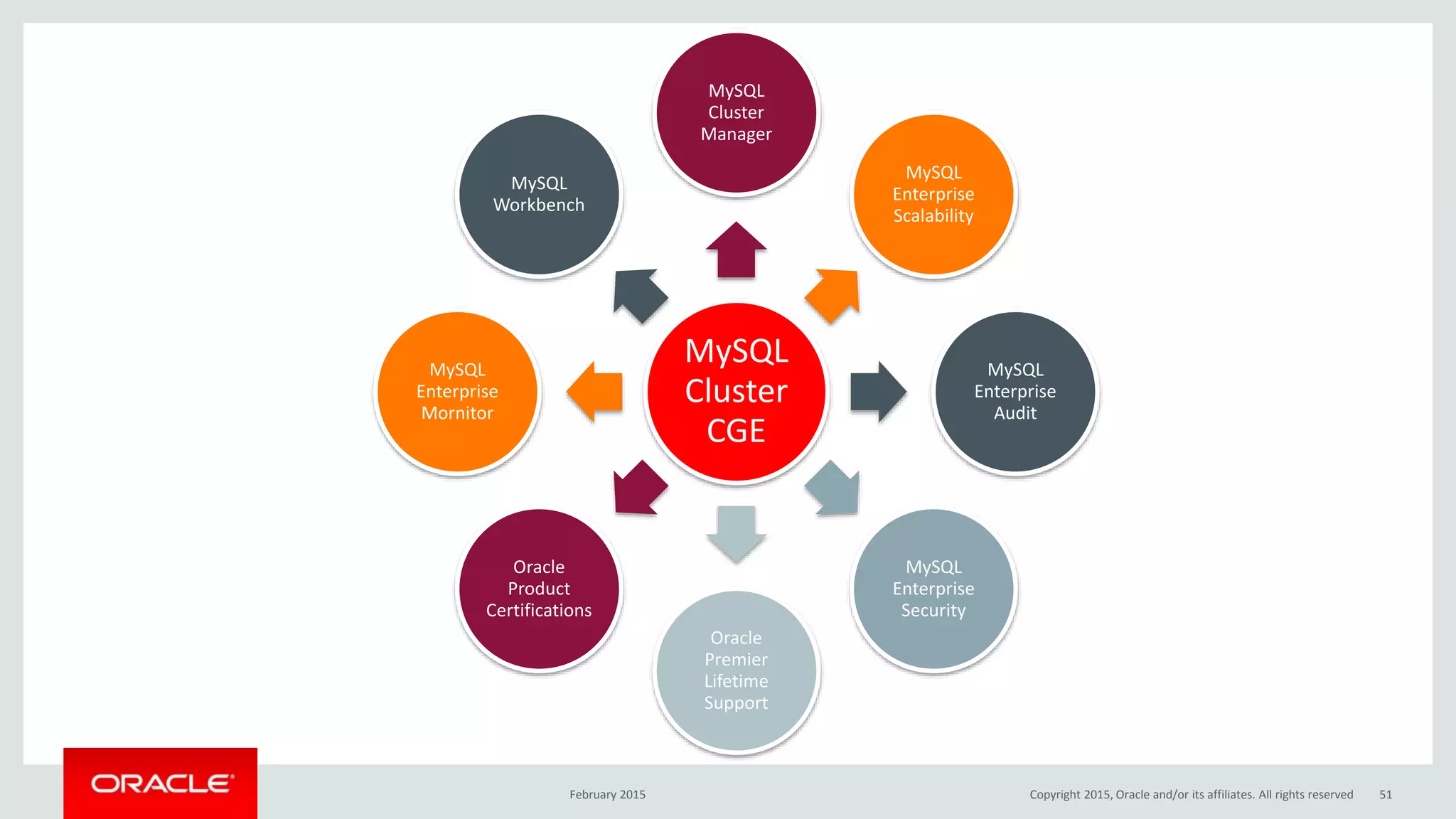
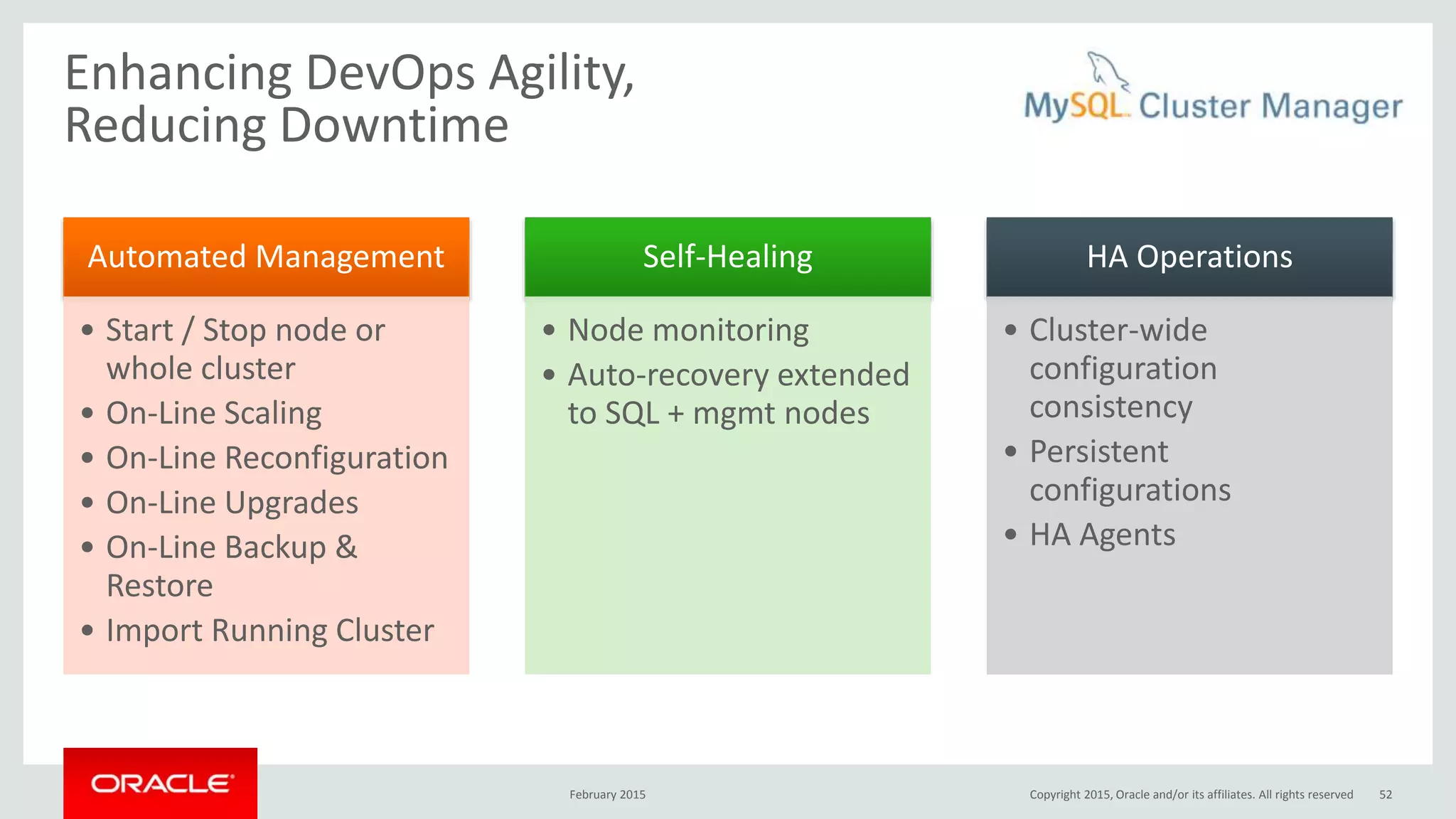
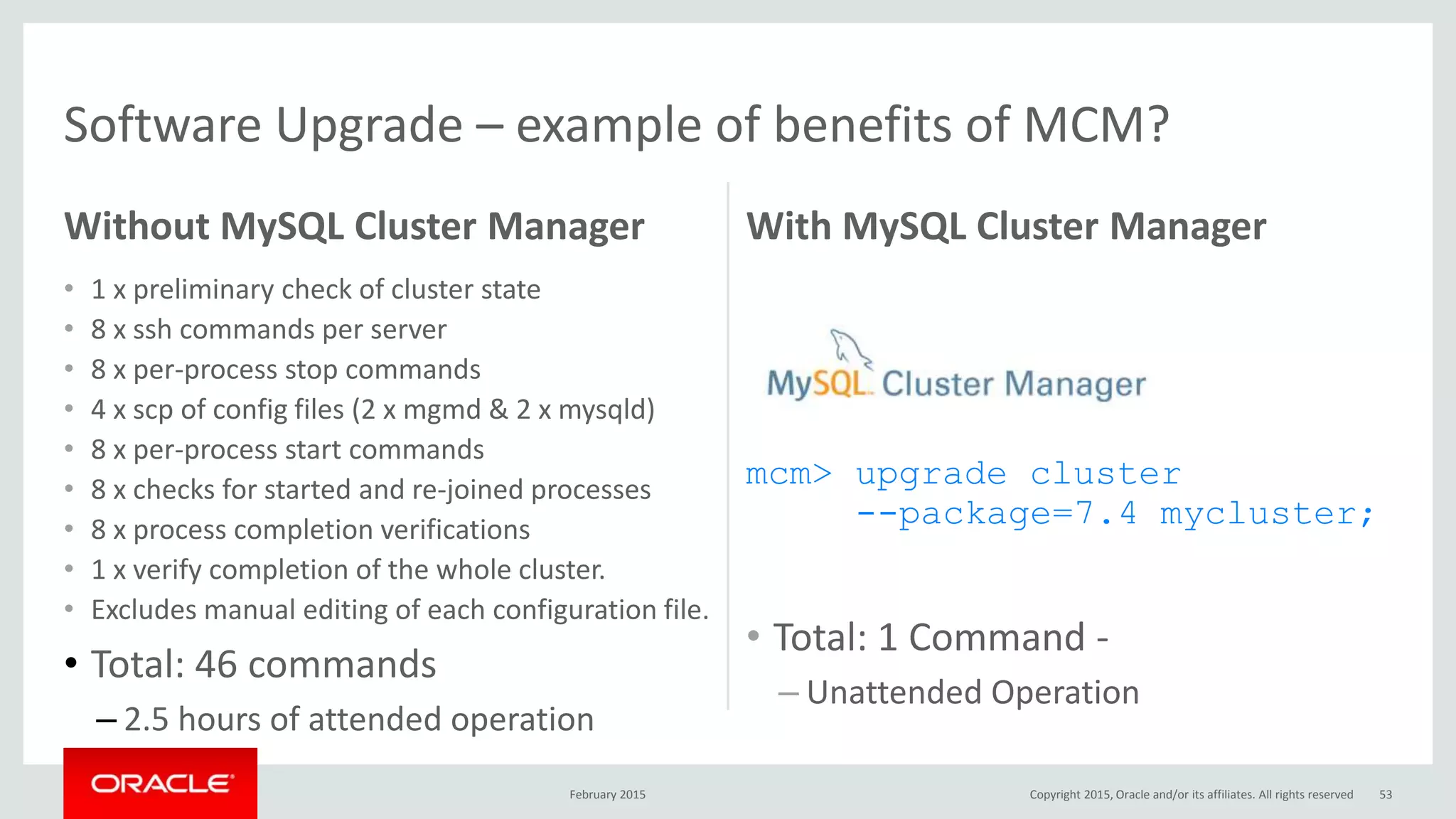
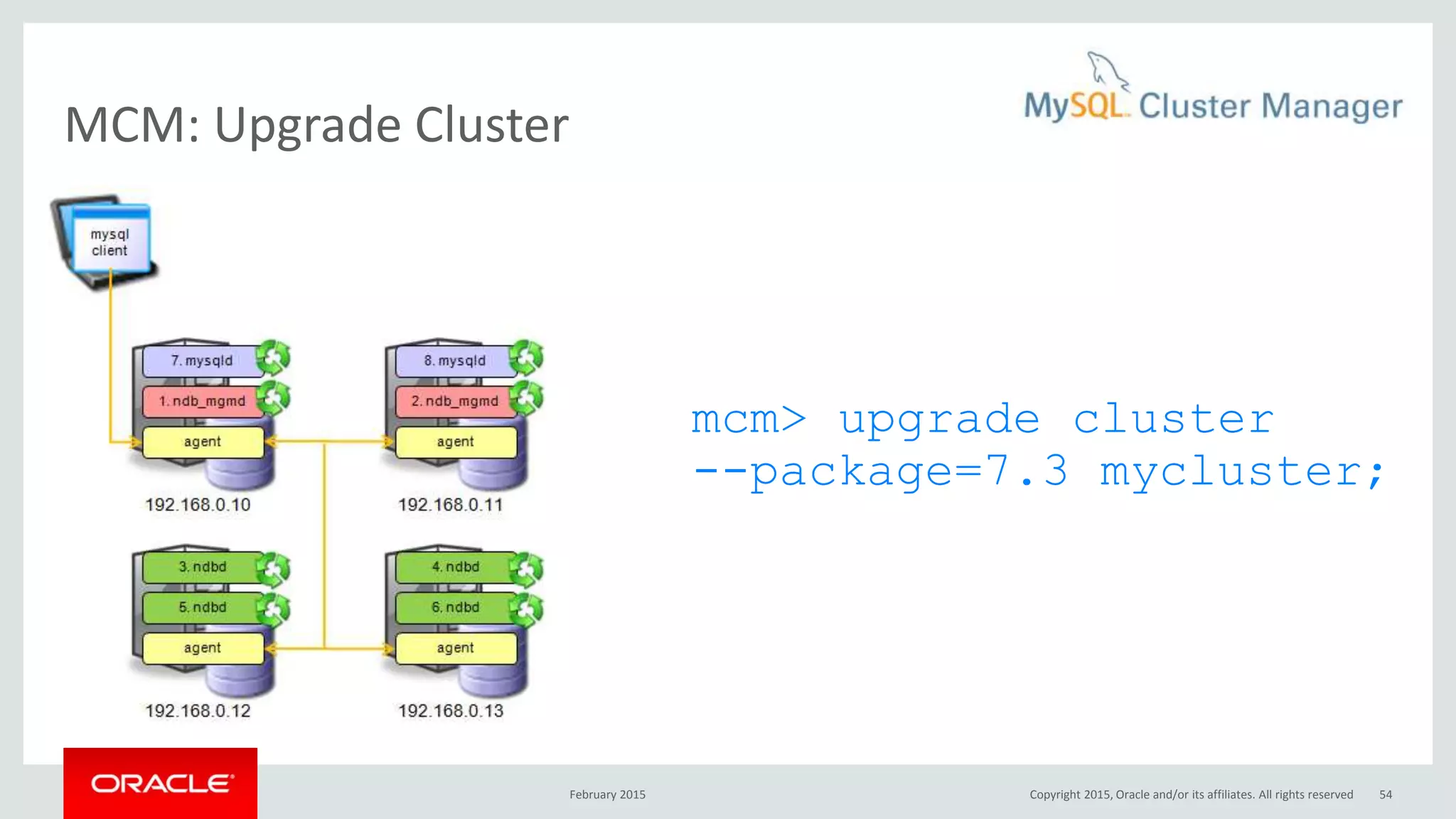
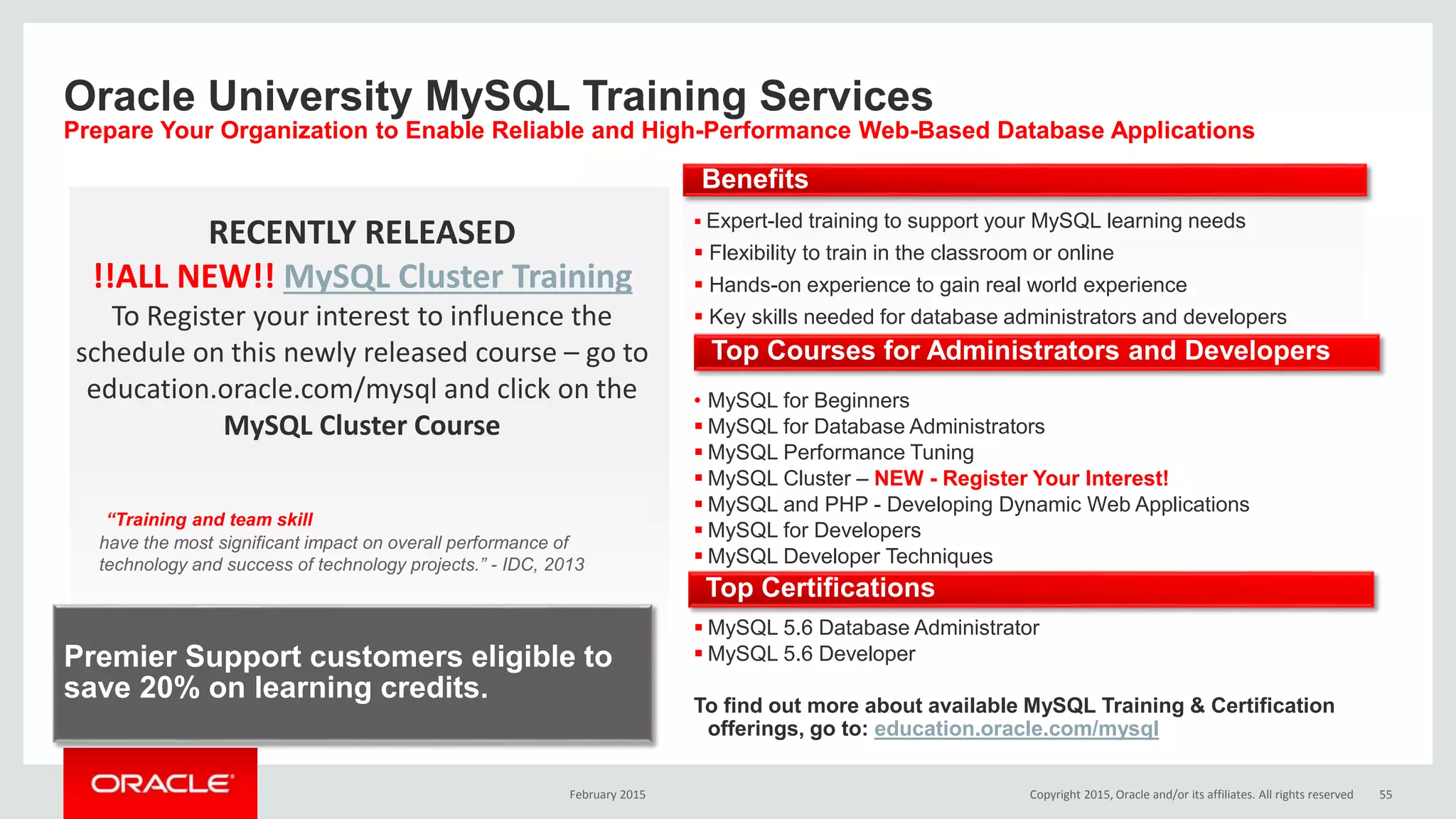
The document discusses MySQL high availability (HA) solutions and their approaches to ensure data access protection. It outlines various replication methods, their configurations, and the suitability of different solutions for mission-critical databases. The content emphasizes the need for assessing business requirements, operational capabilities, and budgetary constraints when choosing the appropriate database architecture.