Host Card Emulation - the ability to emulate payment card on a mobile device without dependency on special Secure Element hardware - opens a whole new chapter for mobile payment applications, which are recently springing out like mushrooms after the rain of HCE. But will these "mushrooms" turn out to be delicious, barely edible, or maybe rather poisonous? Does the security assured by vendor always reflect actual implementation? What could possibly go wrong? How these applications could be attacked? Based on several assessments, we will answer these questions, and leave the audience with best practices on how to mitigate the risks.
Understand what Host Card Emulation is, how the technology works and what the limitations are
Determine what security features are ensured by OS level, and what is left for the mobile application developers
Identify possibilities to attack mobile payment applications, attack conditions and risks
Analyse implementation shortcomings captured during assessments
Identify security mechanisms possible to implement in order to mitigate the risk, guidelines and best practice






























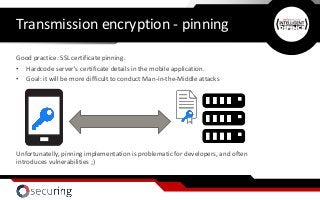
![Transmission encryption - pinning
SSL vulnerability example #1 – empty trustManager
sslcontext = SSLContext.getInstance("TLS");
atrustmanager = new TrustManager[1];
atrustmanager[0] = new EasyX509TrustManager(null);
sslcontext.init(null, atrustmanager, null);
The application accepts ALL the possible certificates ;)](https://image.slidesharecdn.com/demystifyinghostcardemulationsecurity-bestpracticesforimplementingsecuremobilepayments-160627112508/85/Demystifying-Host-Card-Emulation-Security-Best-Practices-for-Implementing-Secure-Mobile-Payments-36-320.jpg?cb=1467027833)








