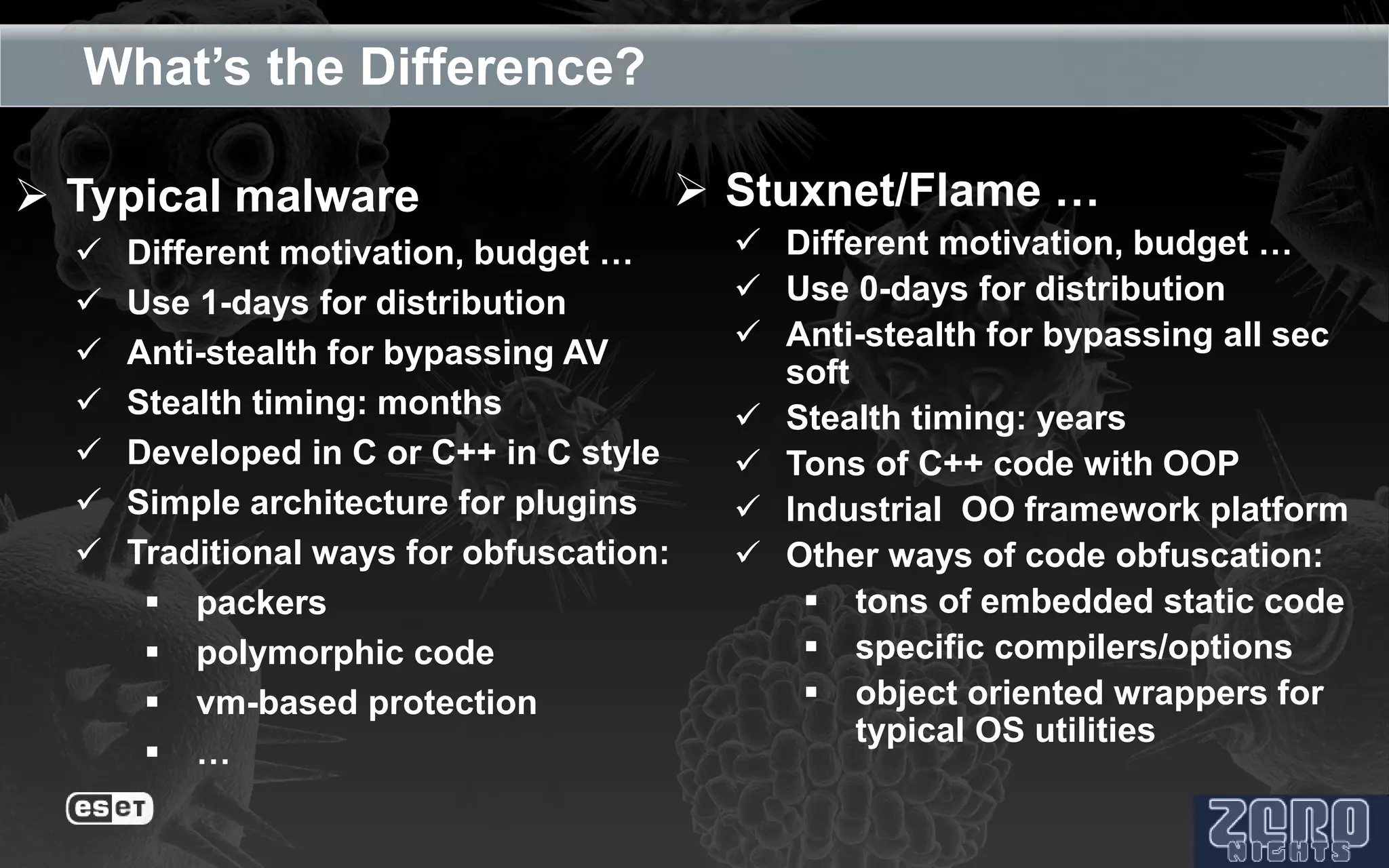
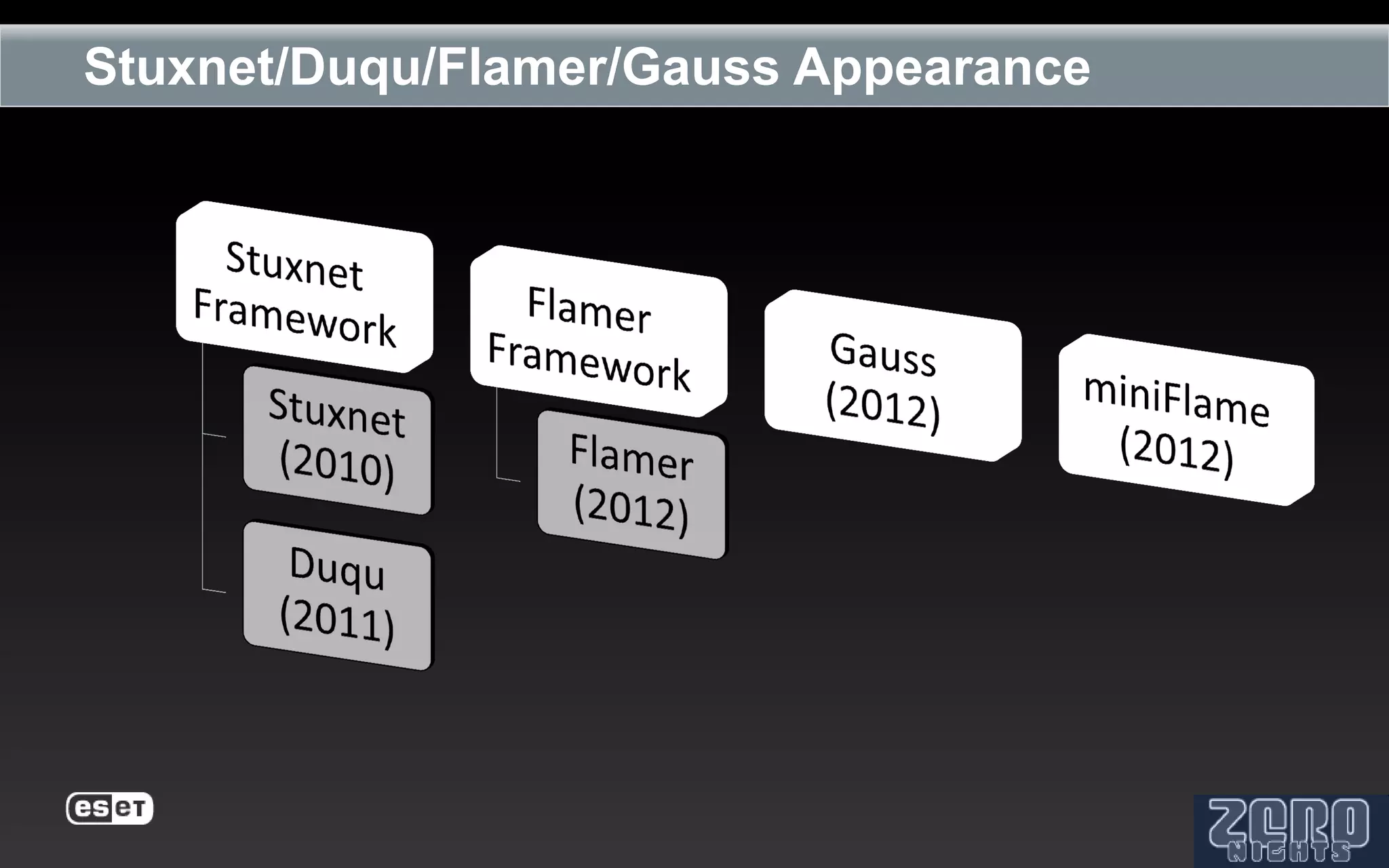
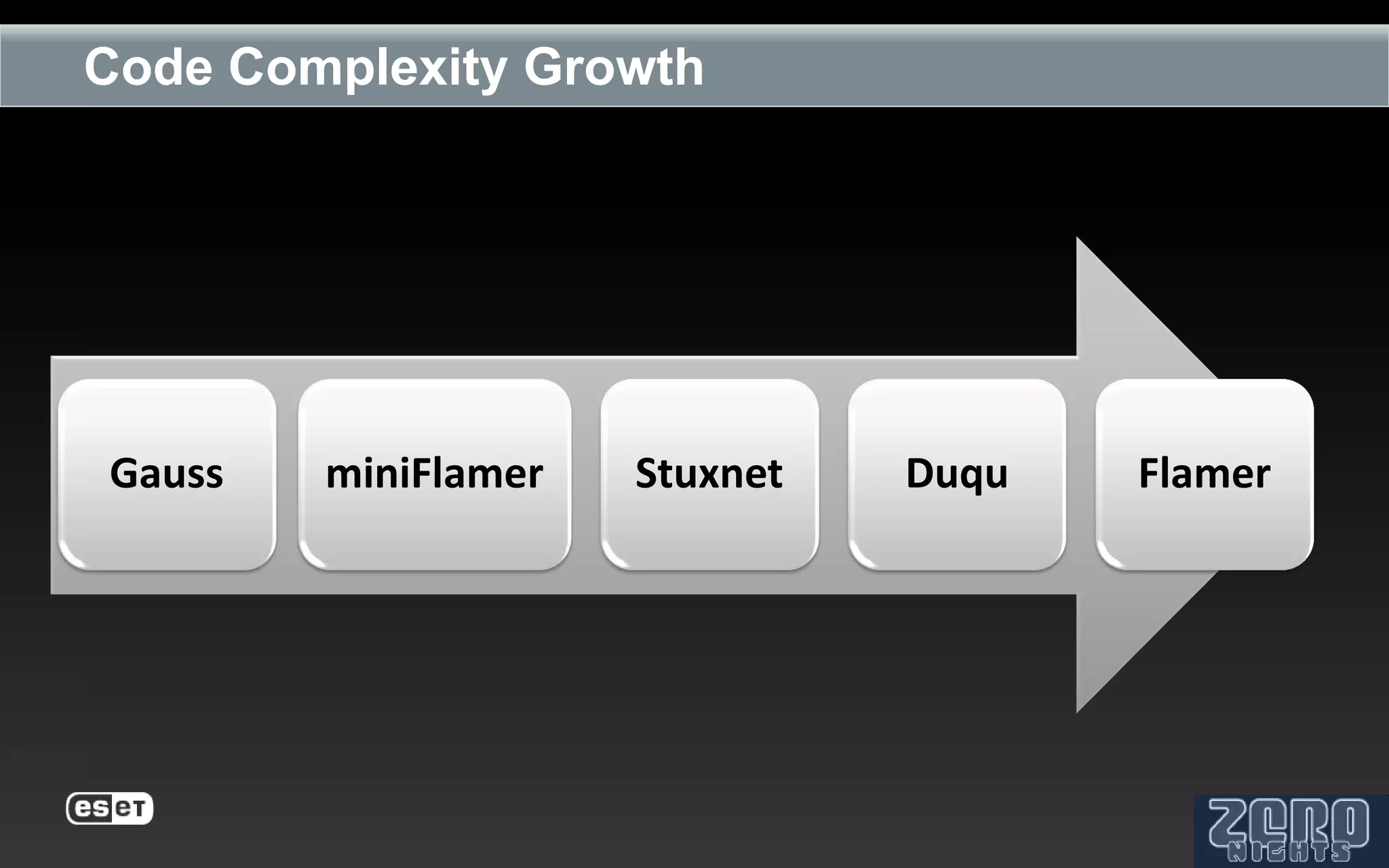
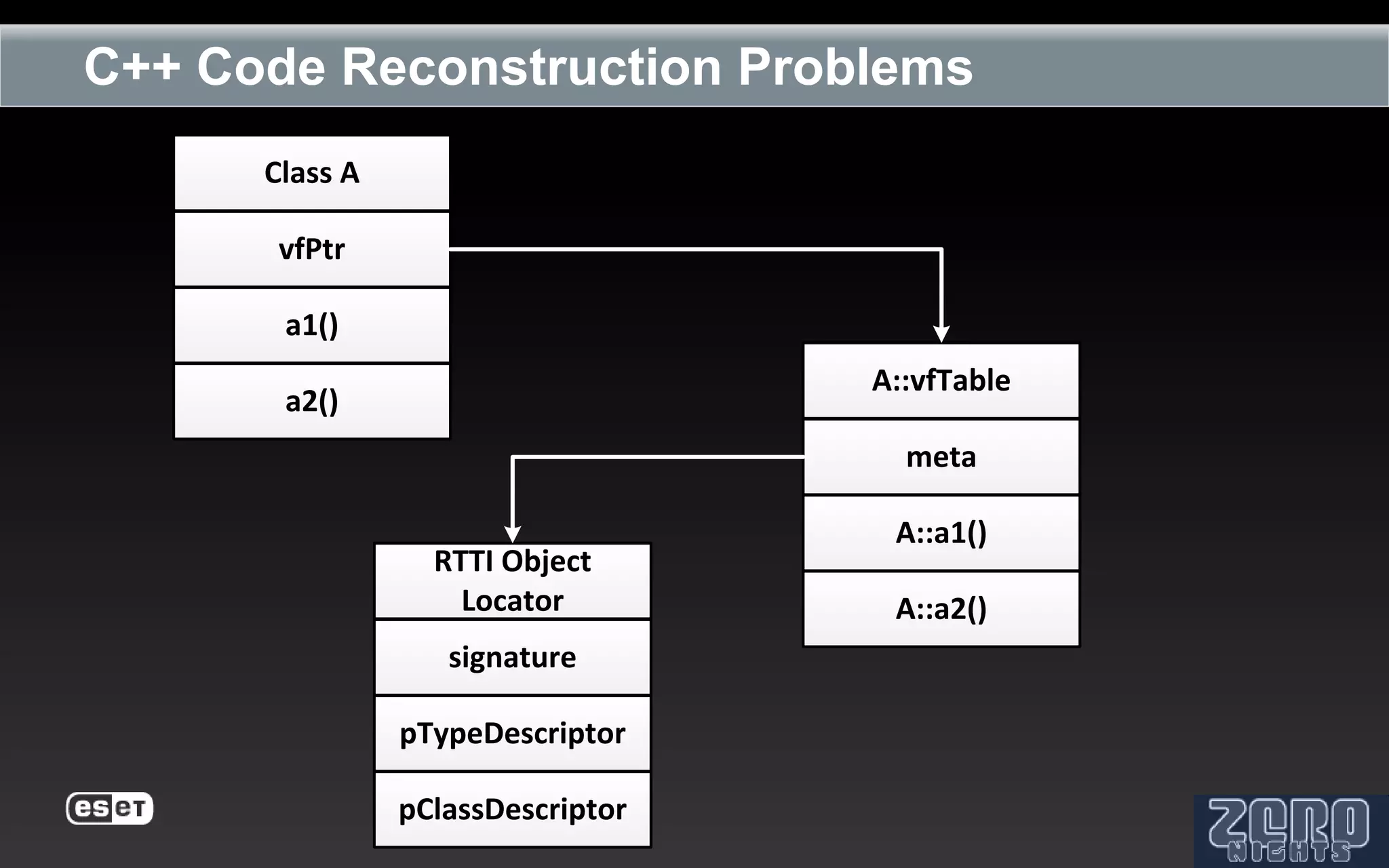
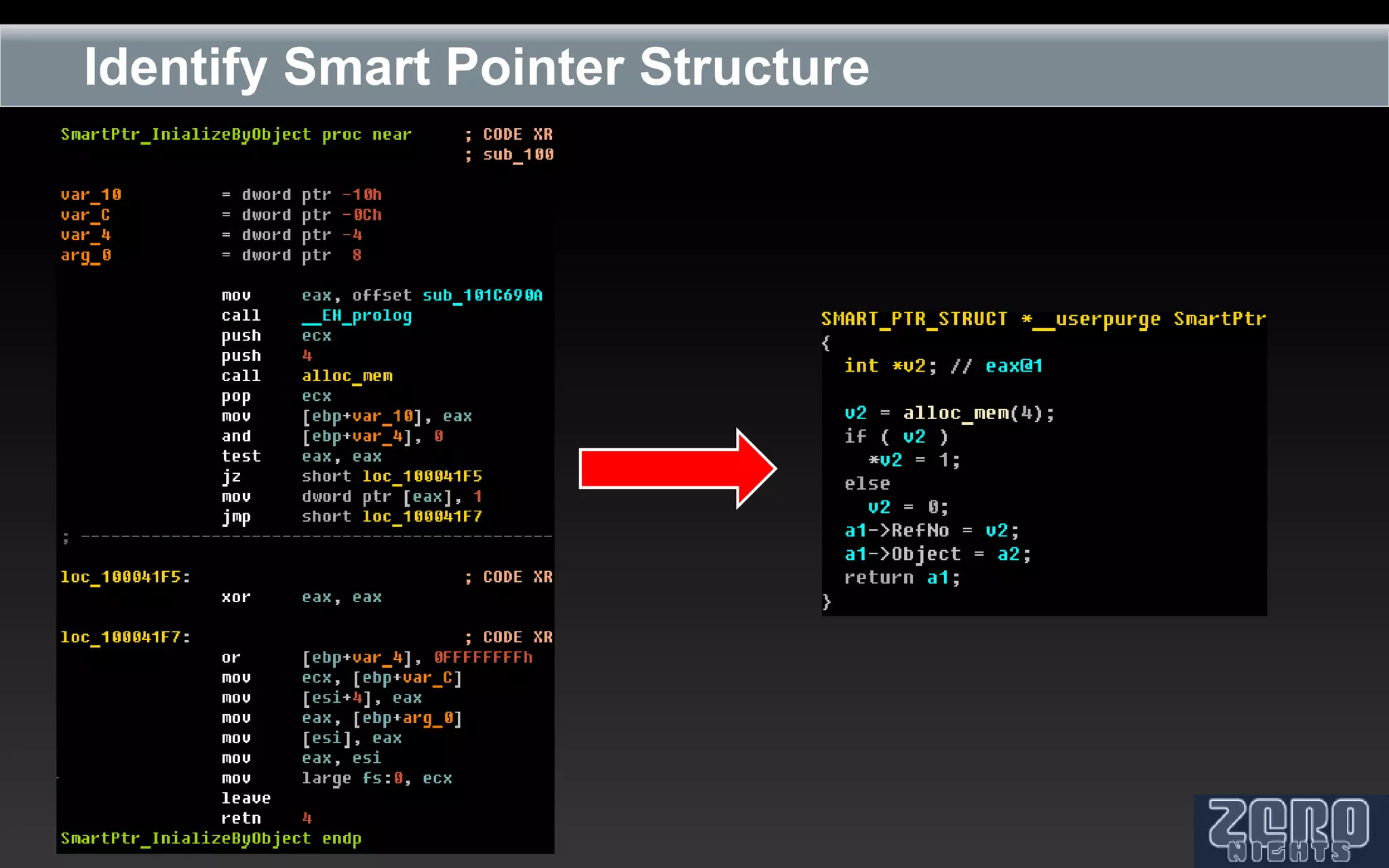
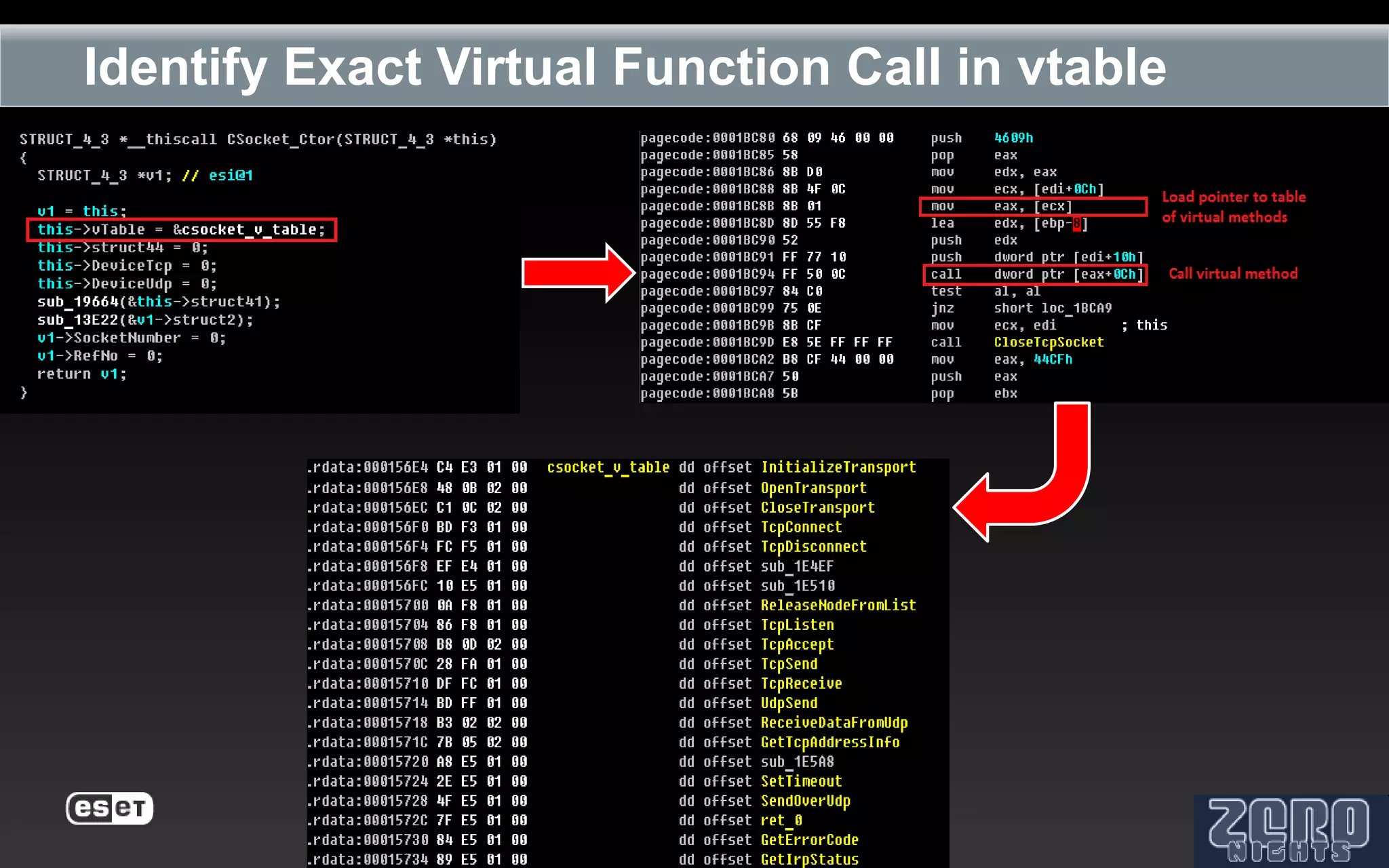
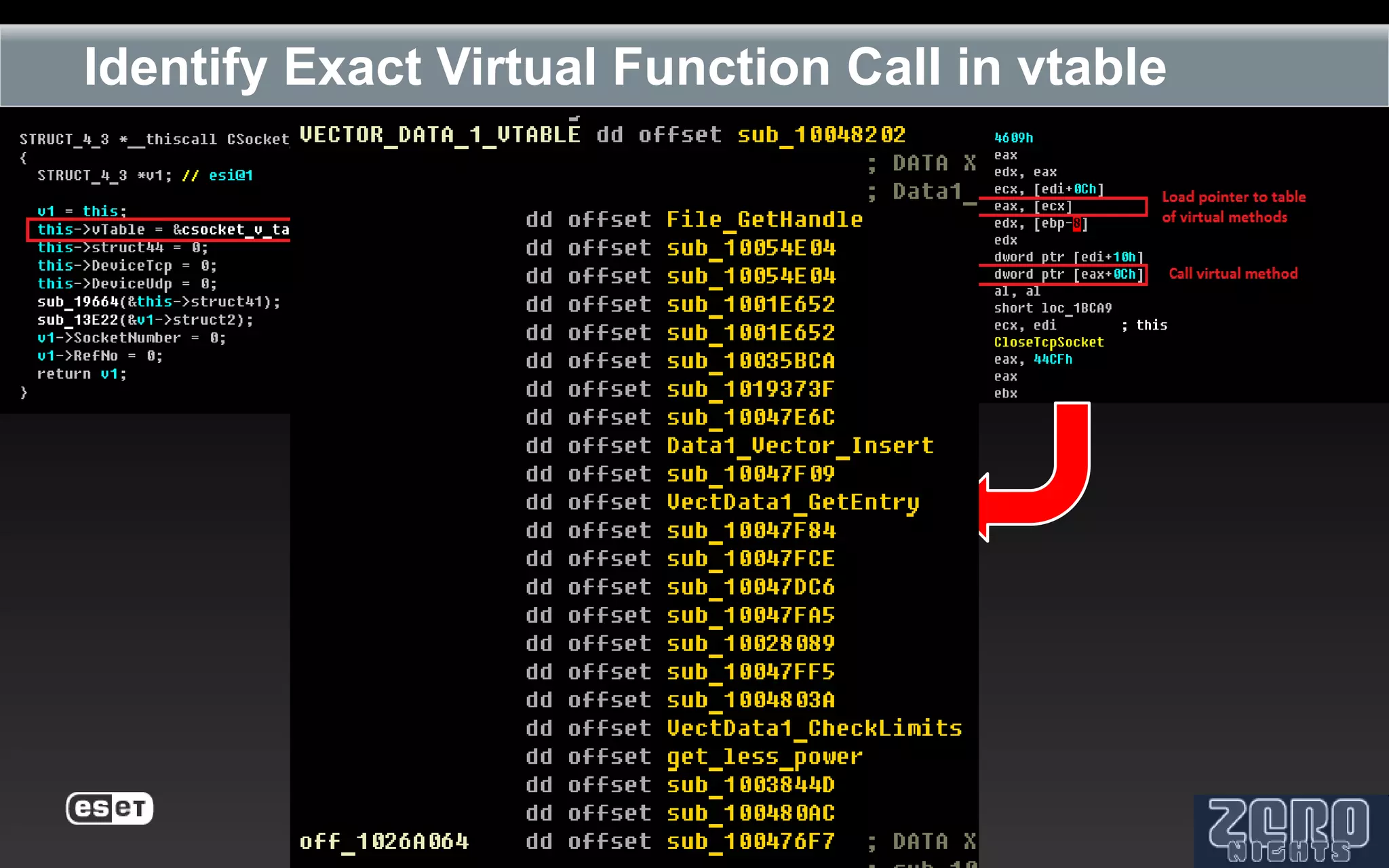
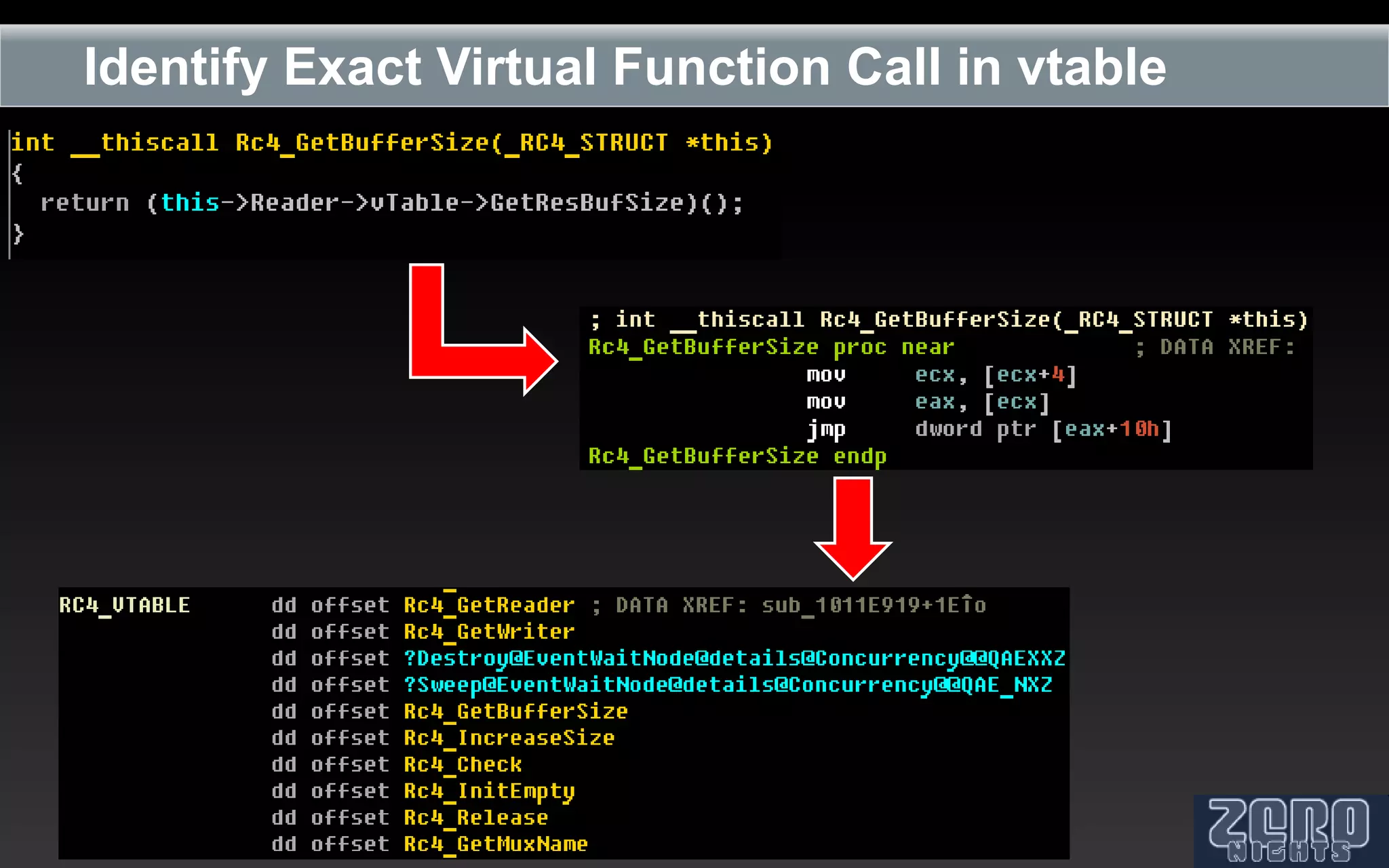
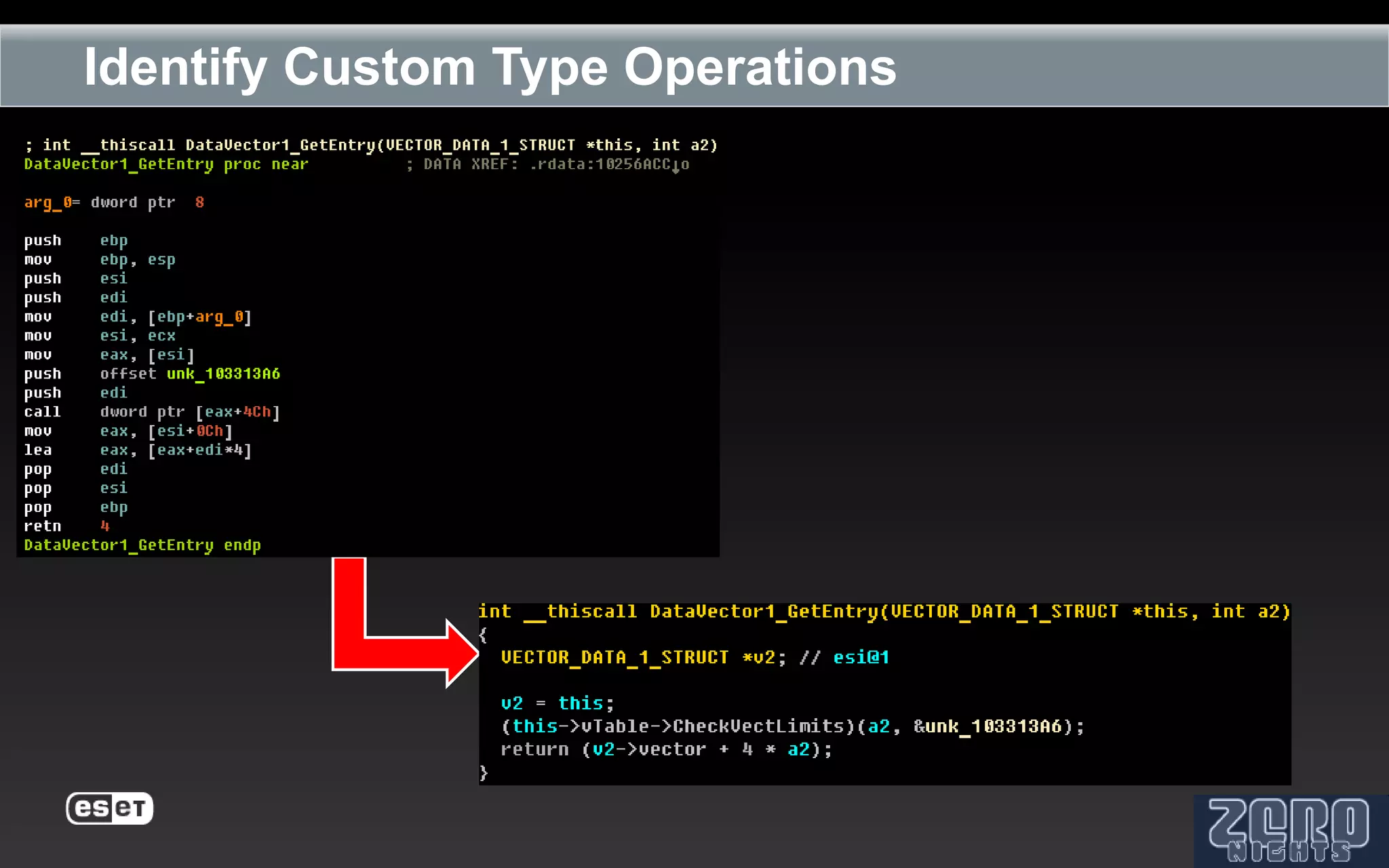
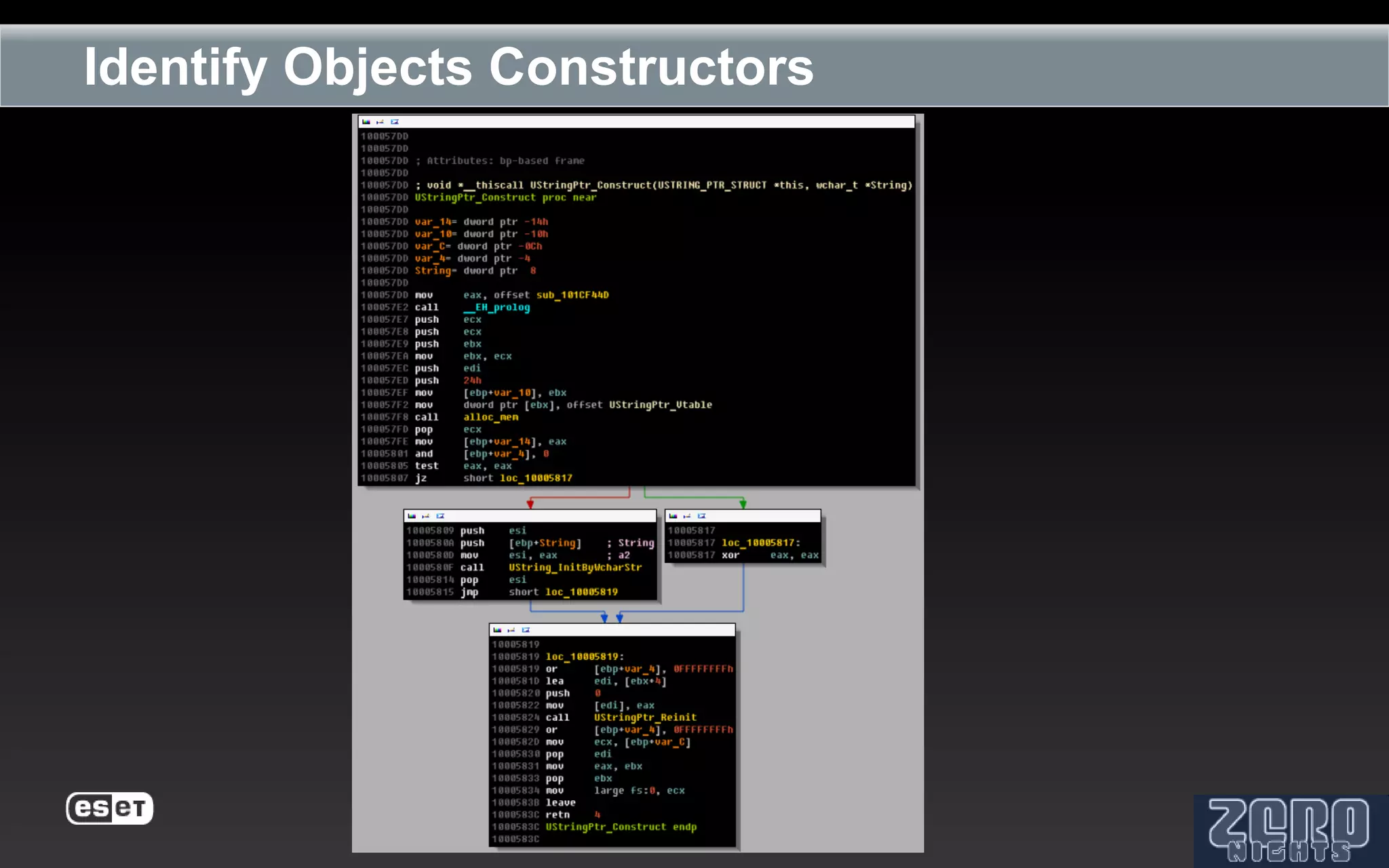
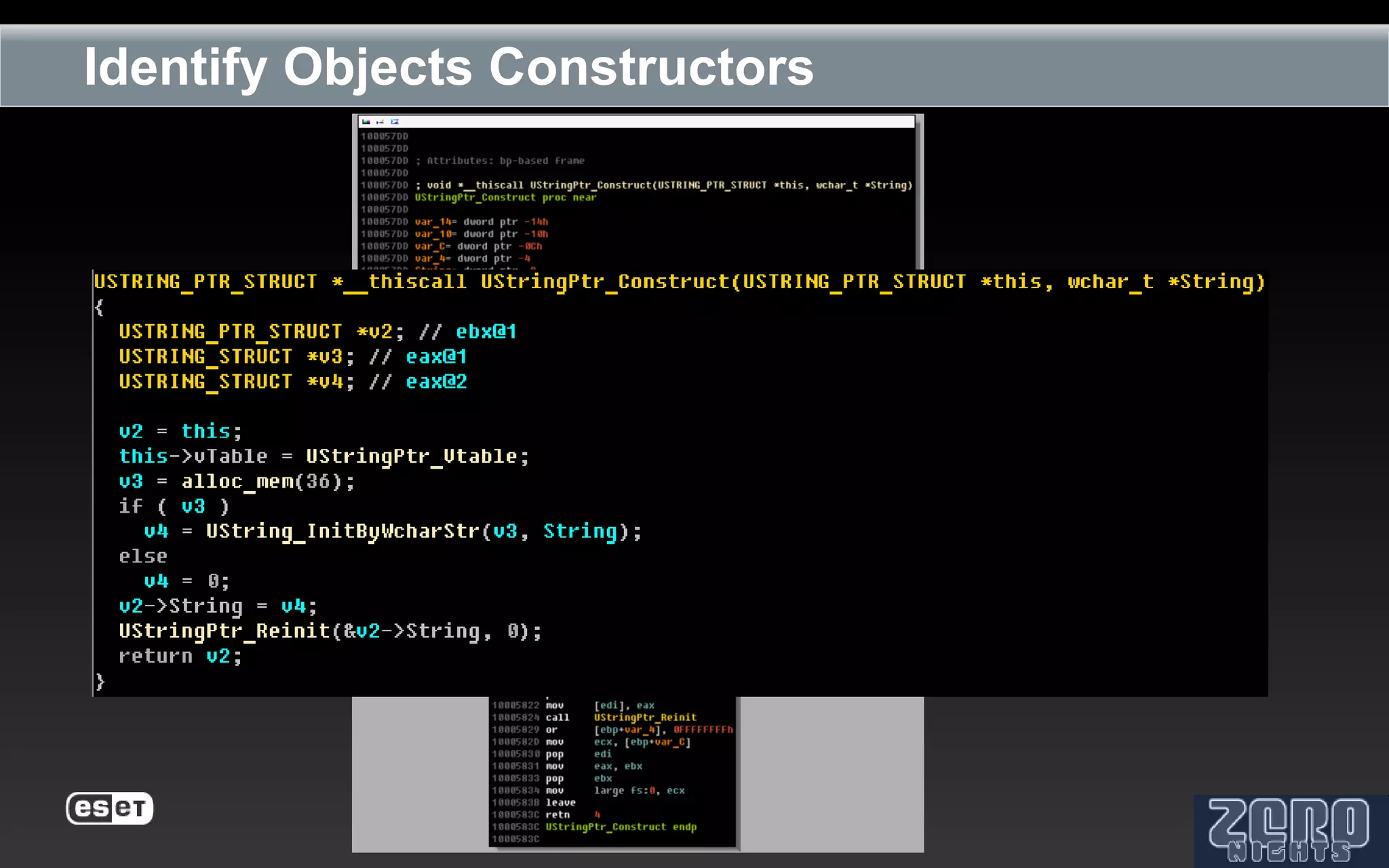
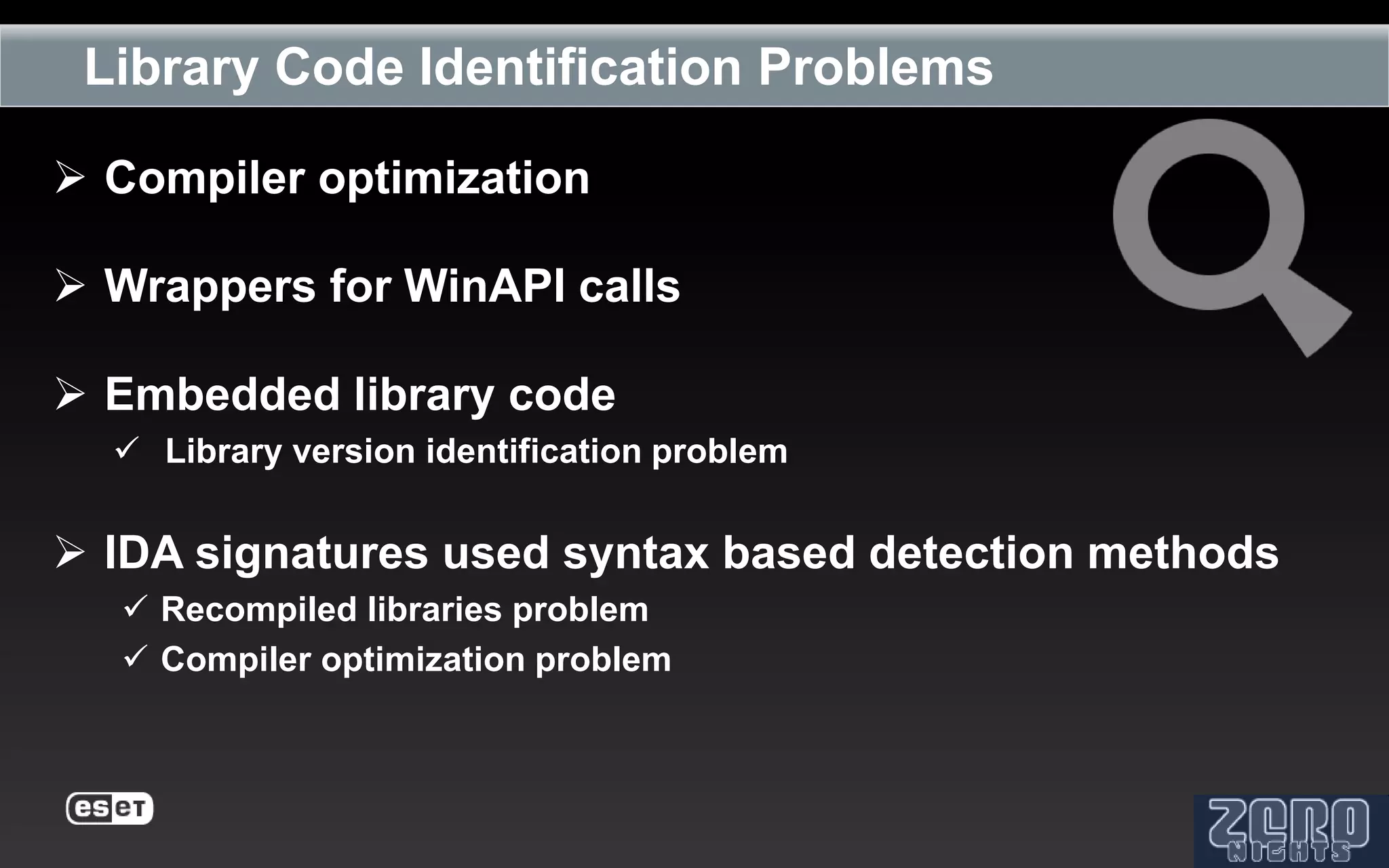
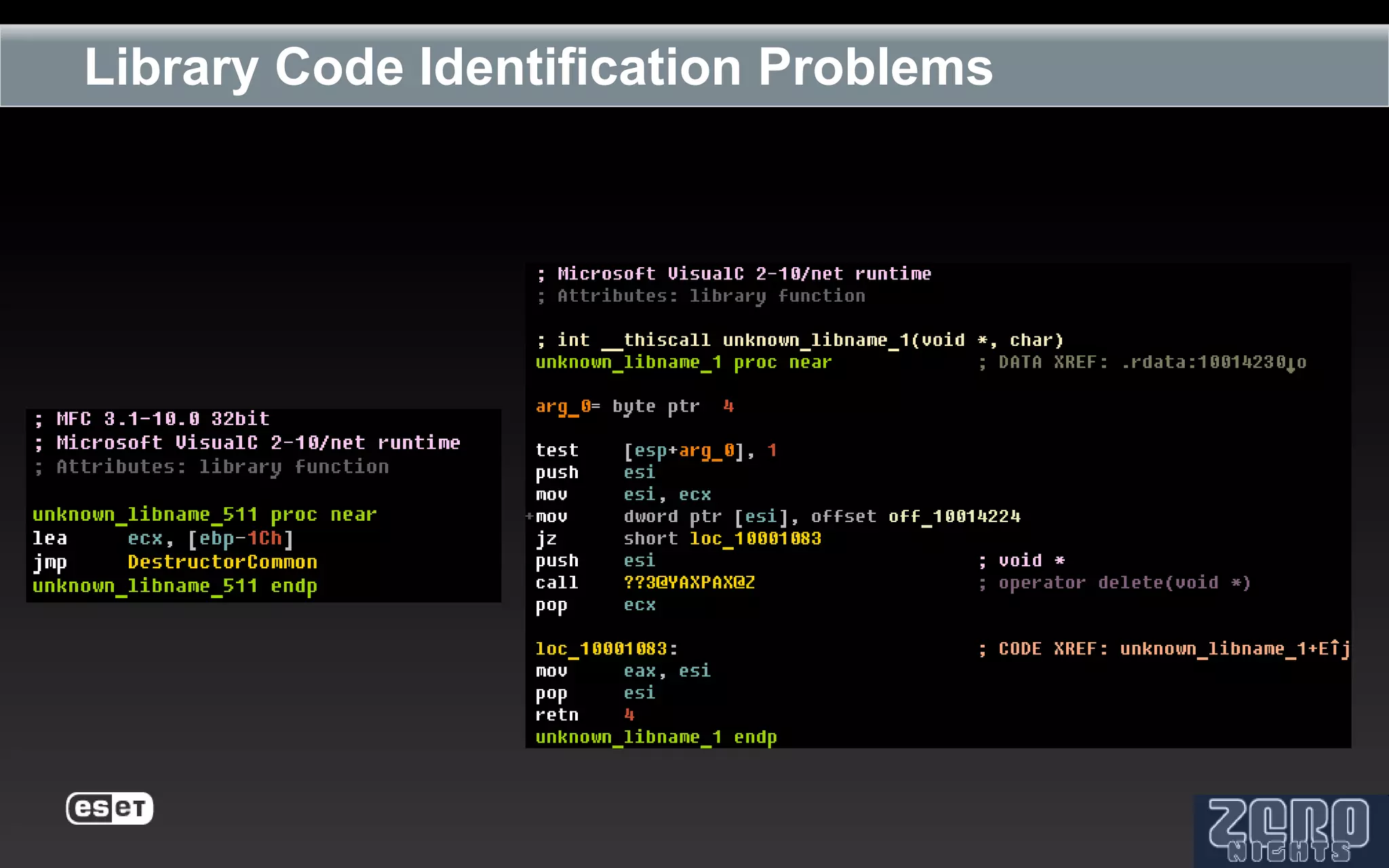
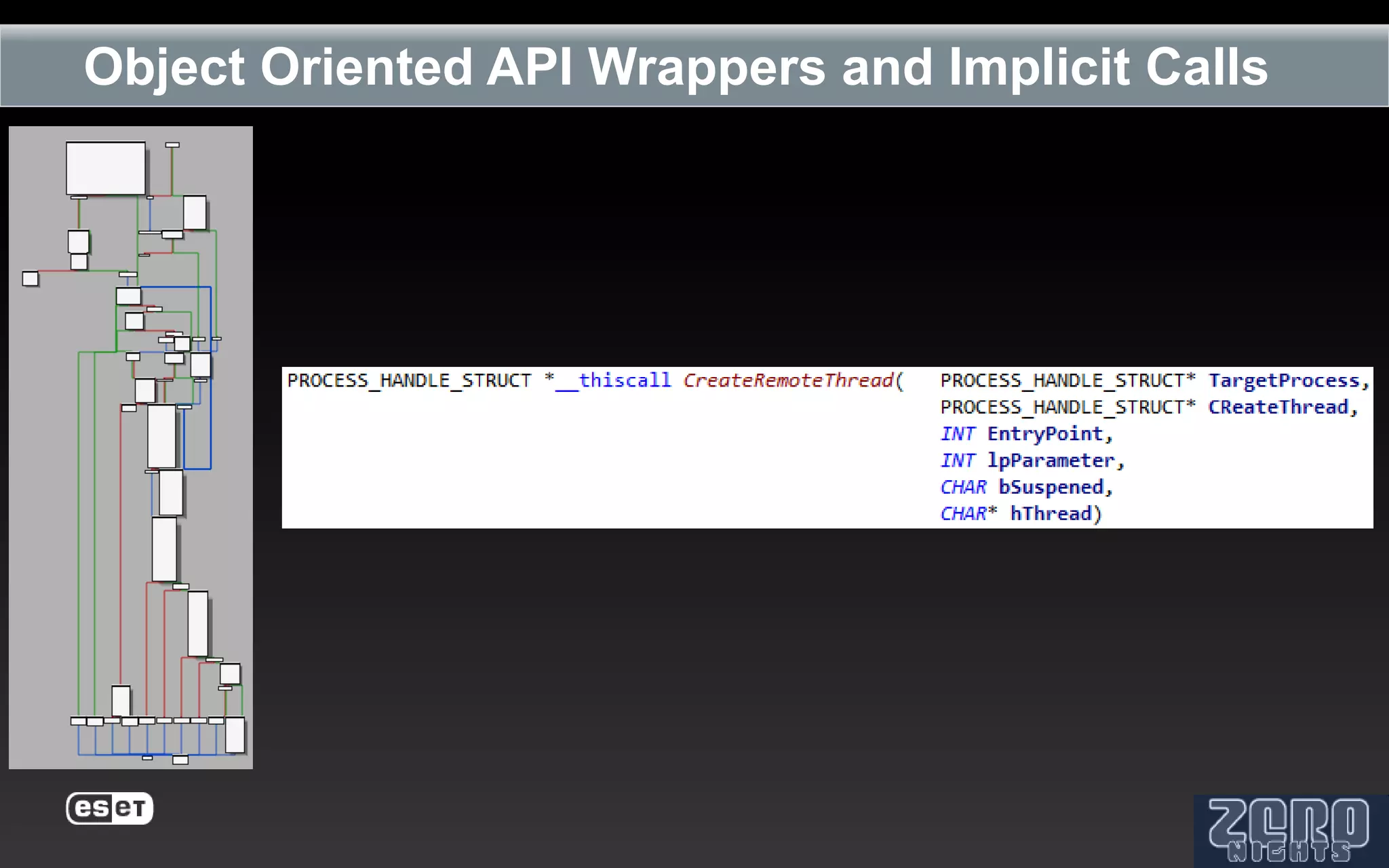
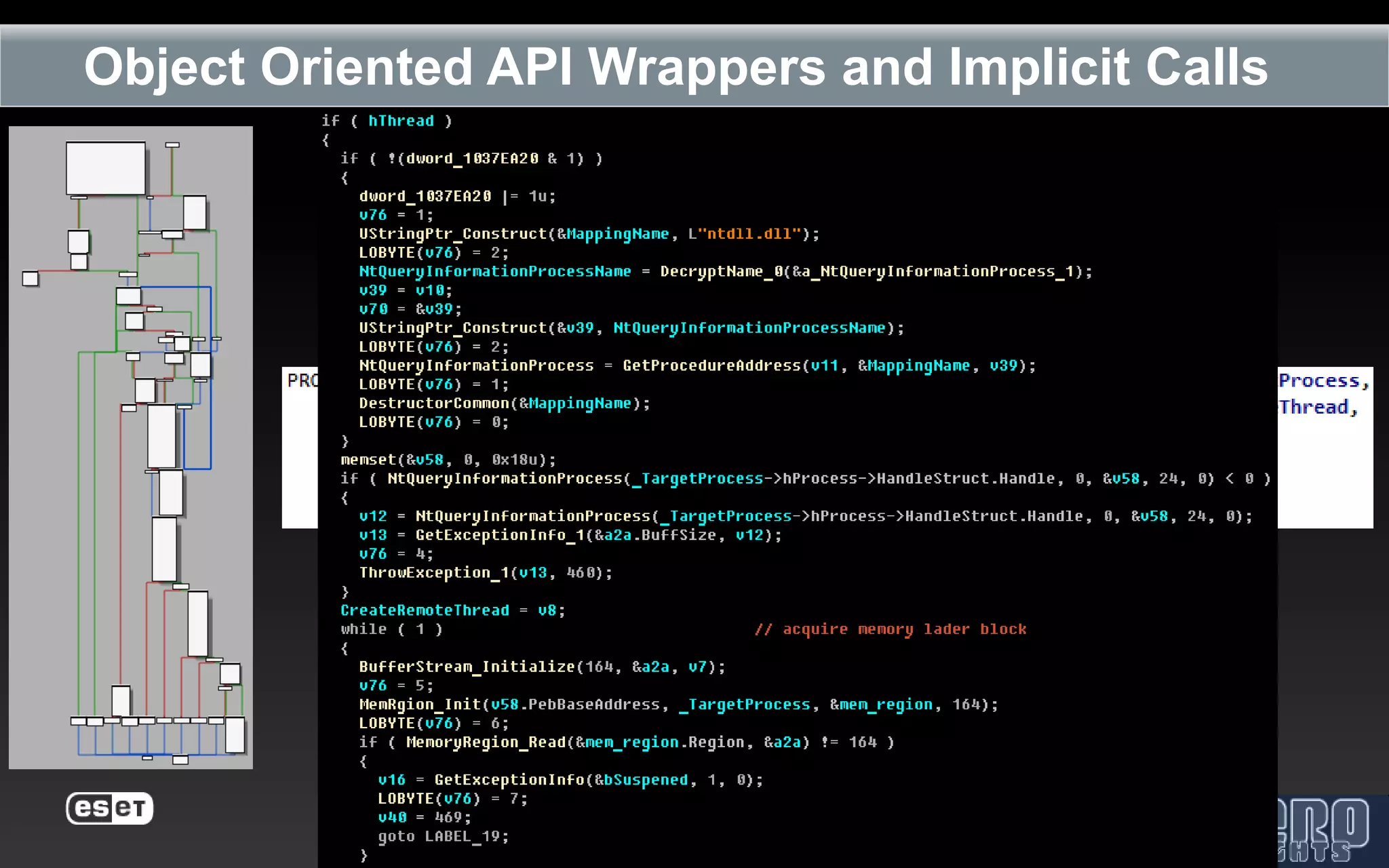
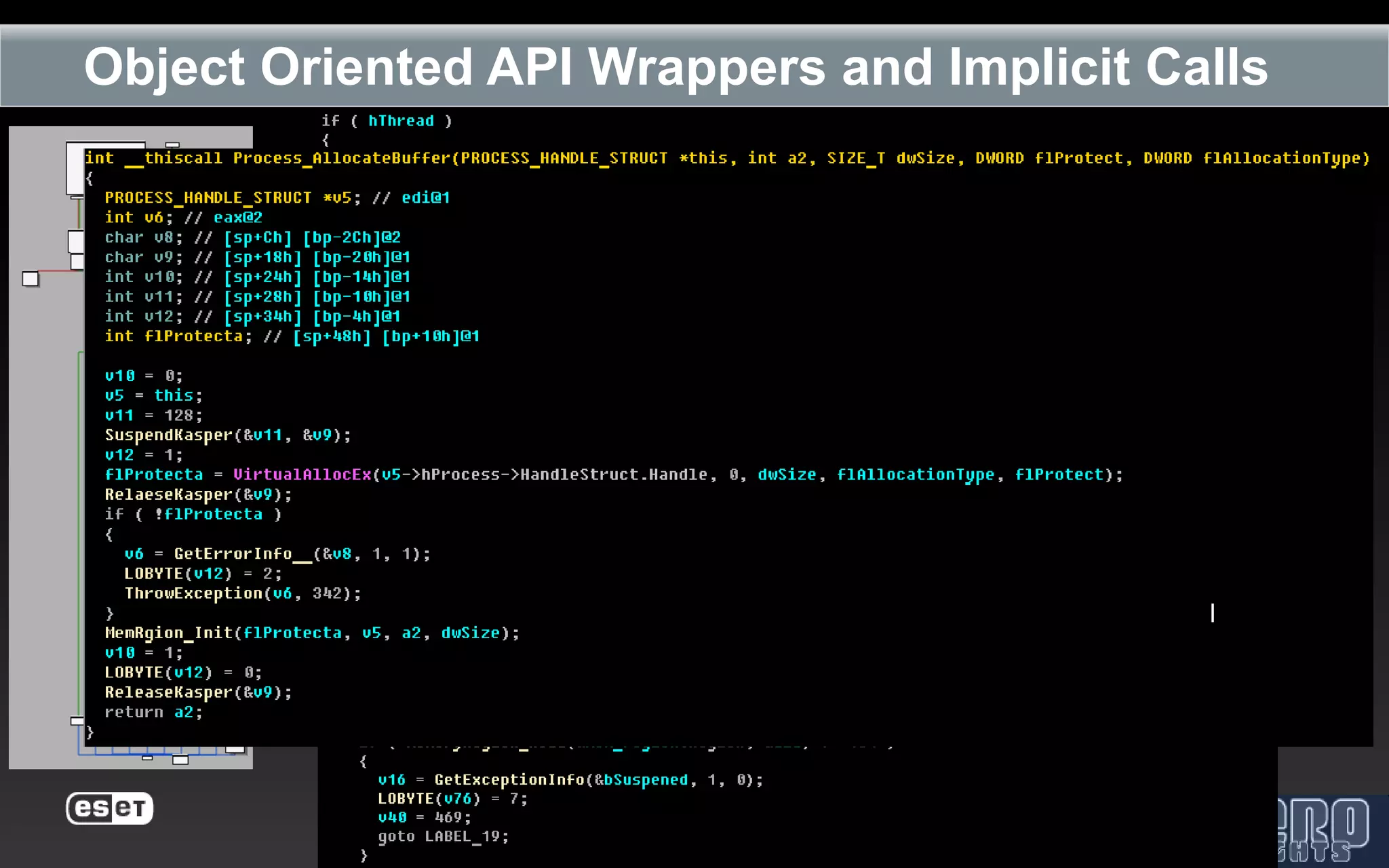
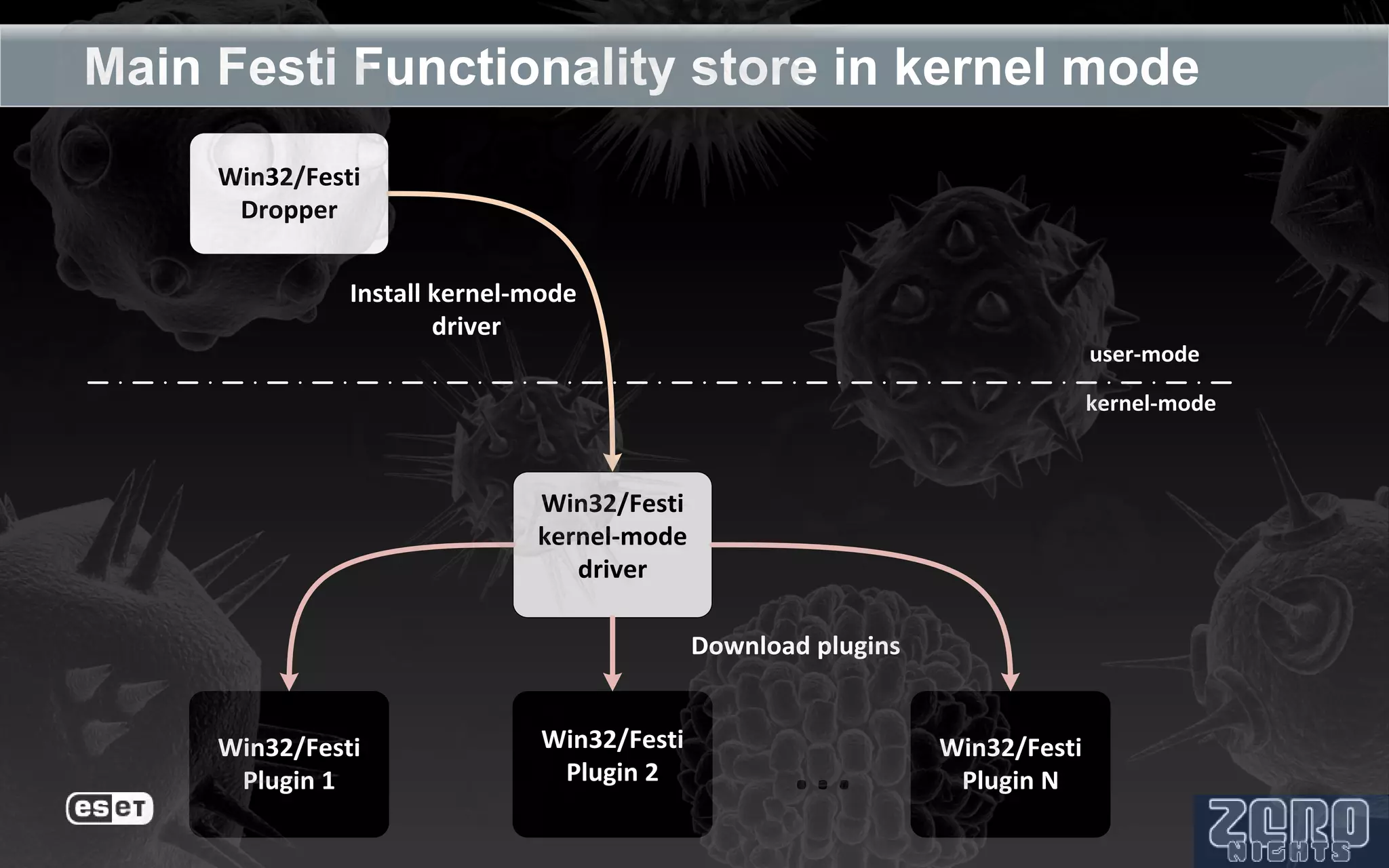
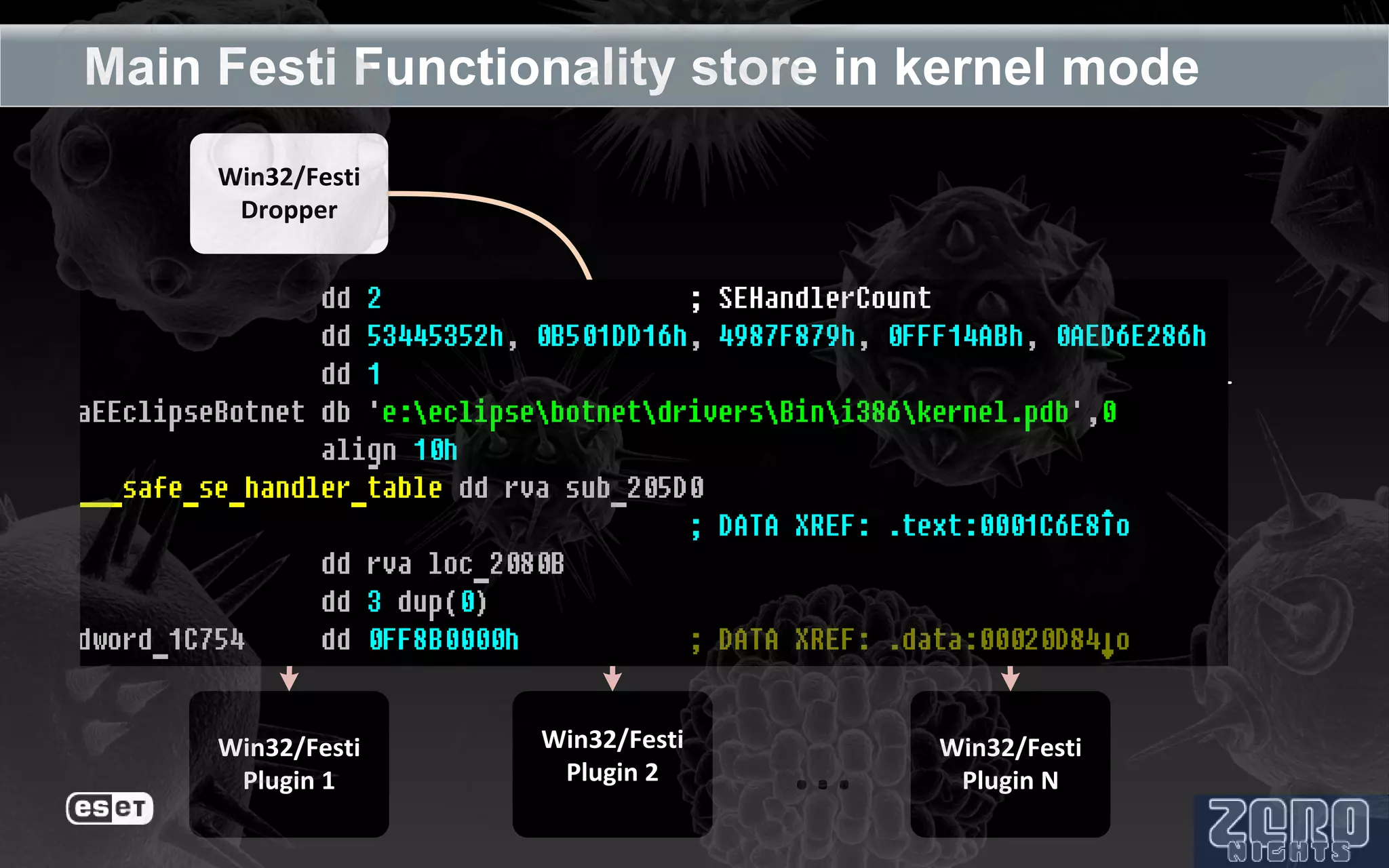
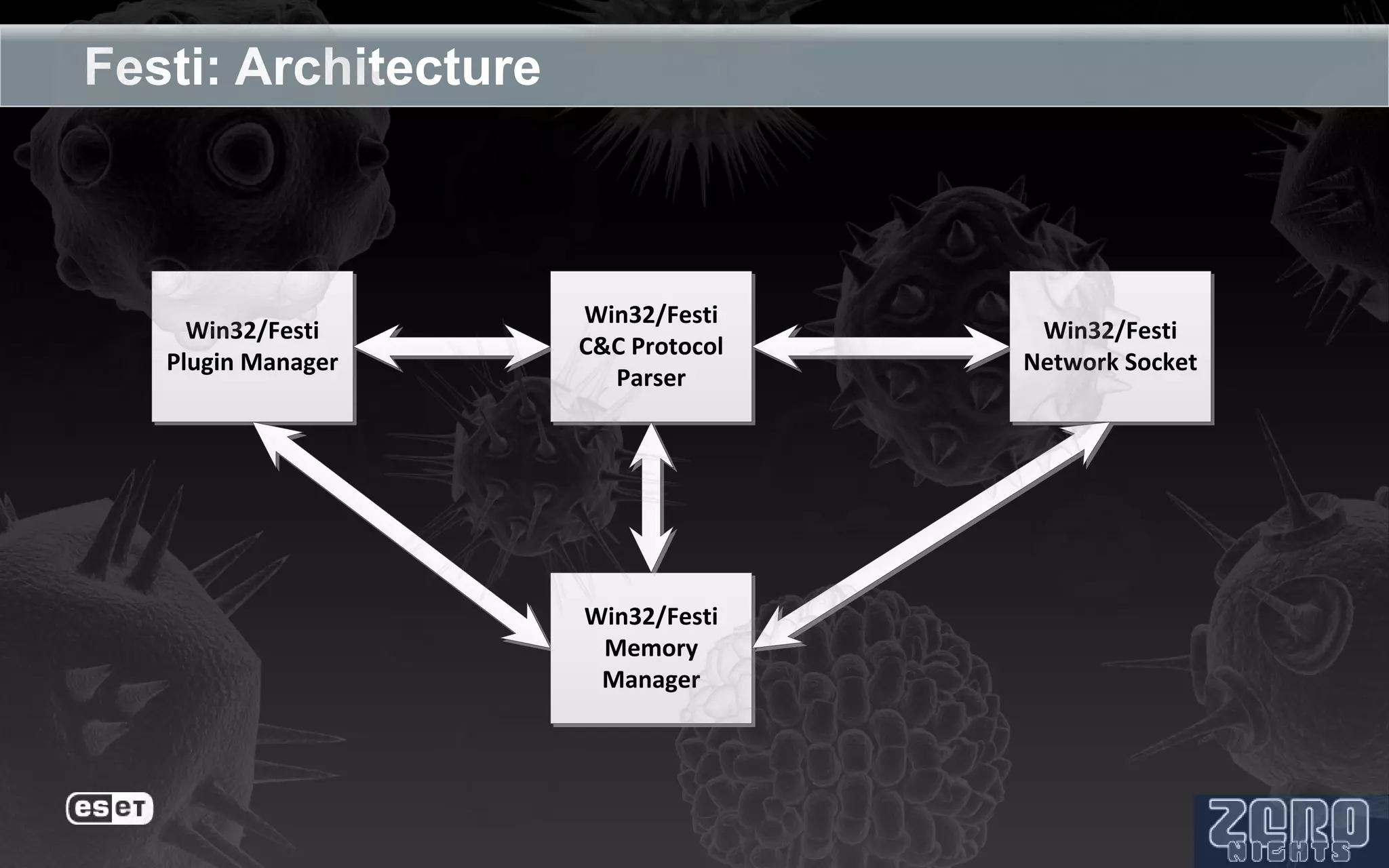
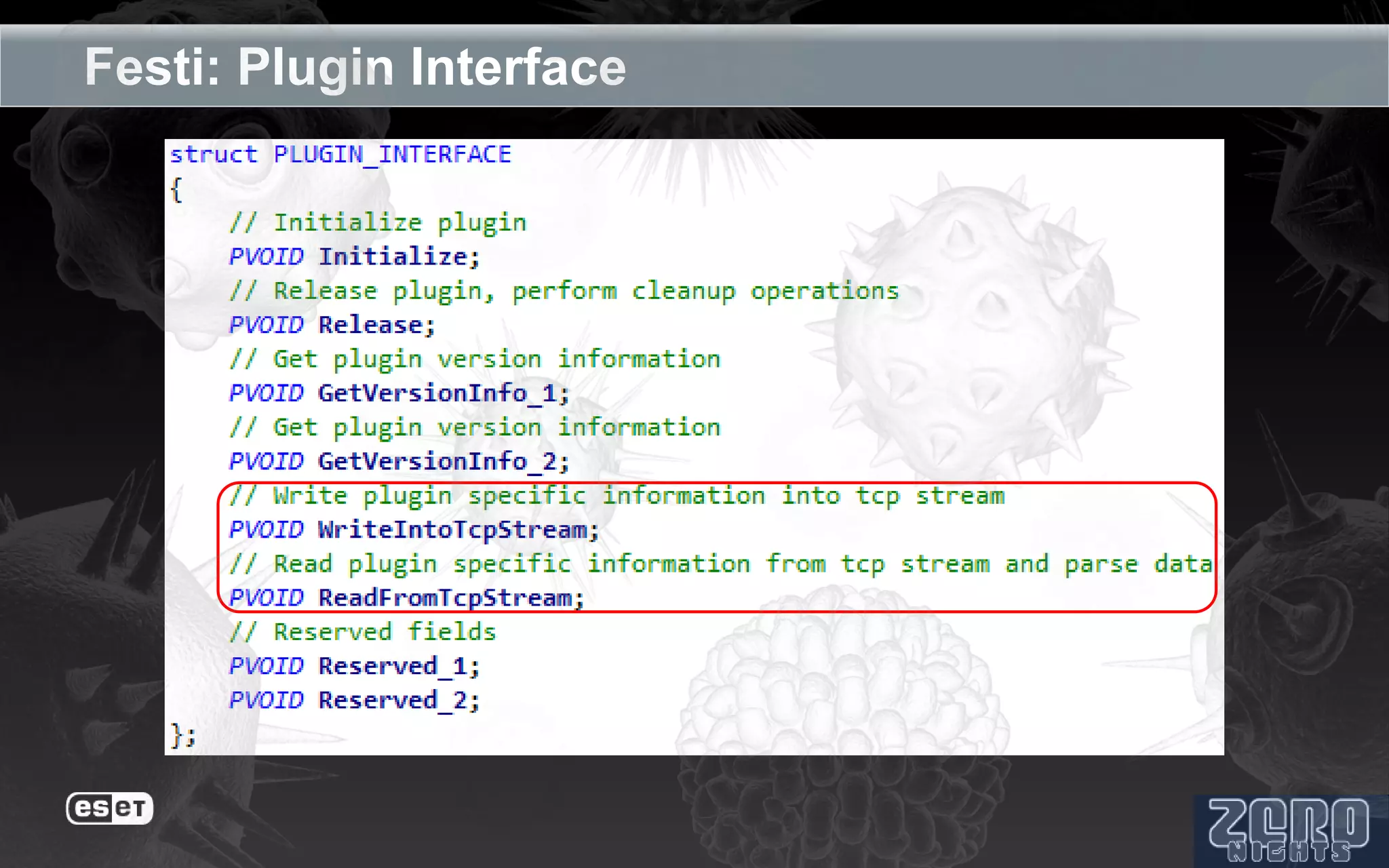
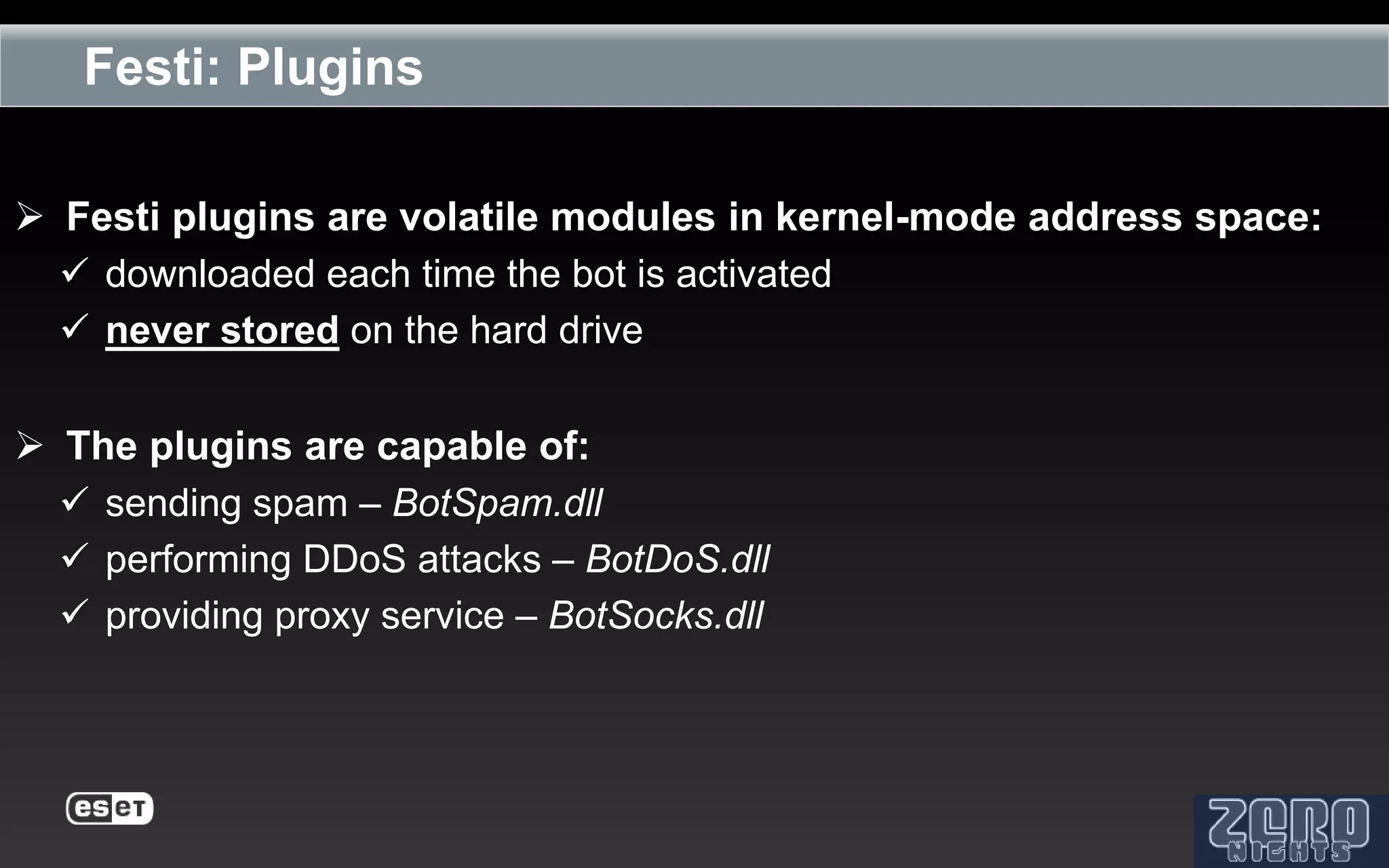
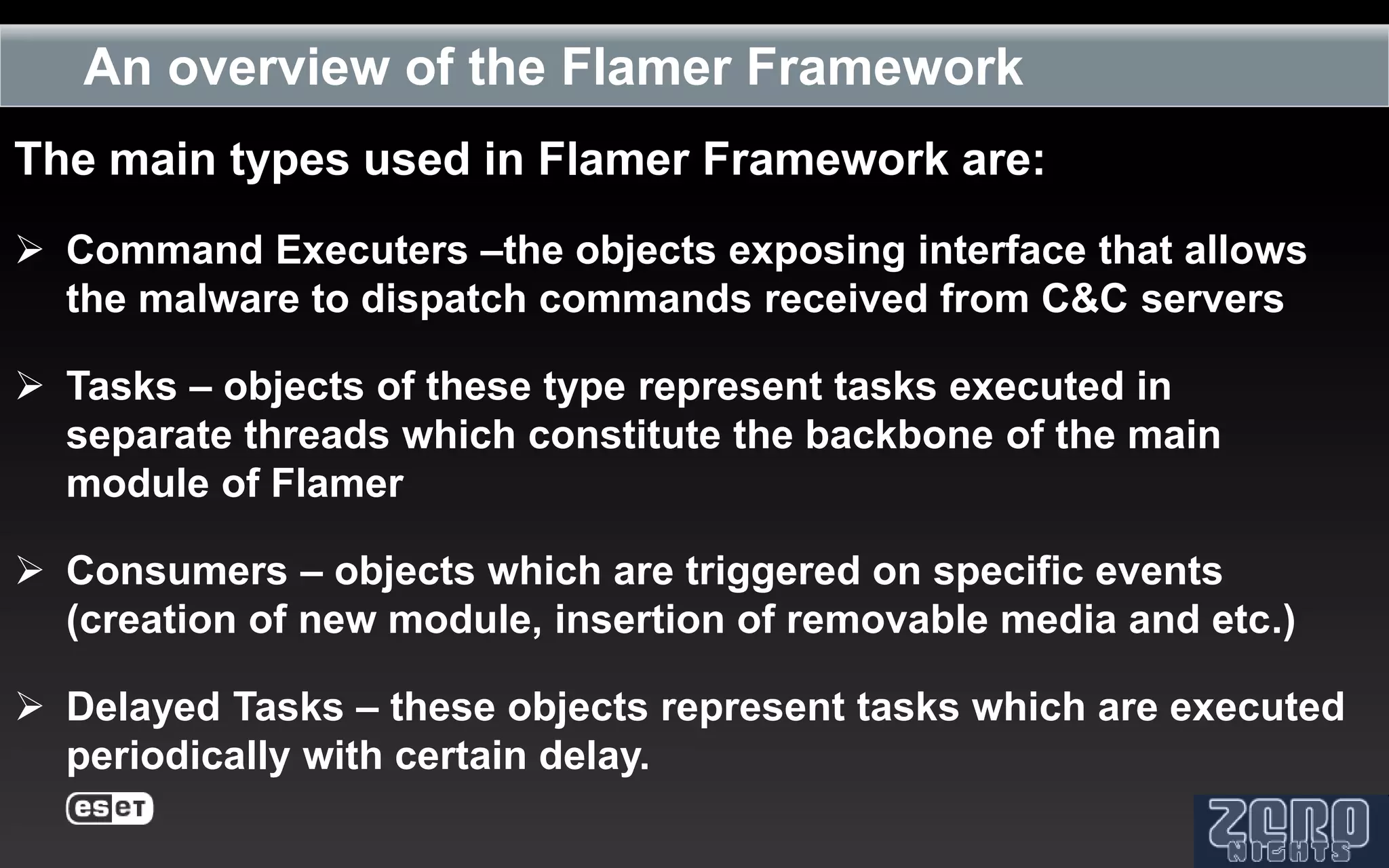
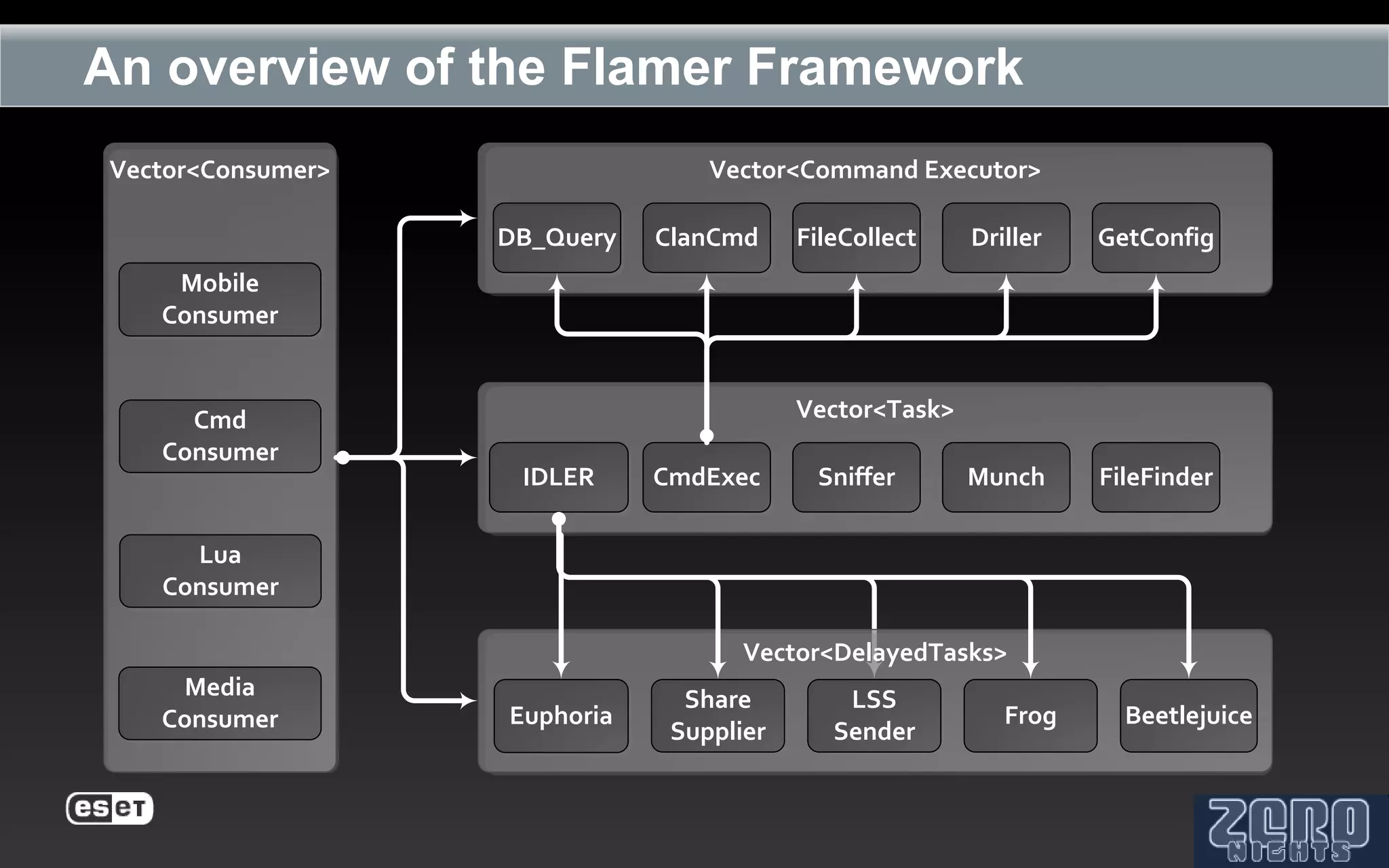
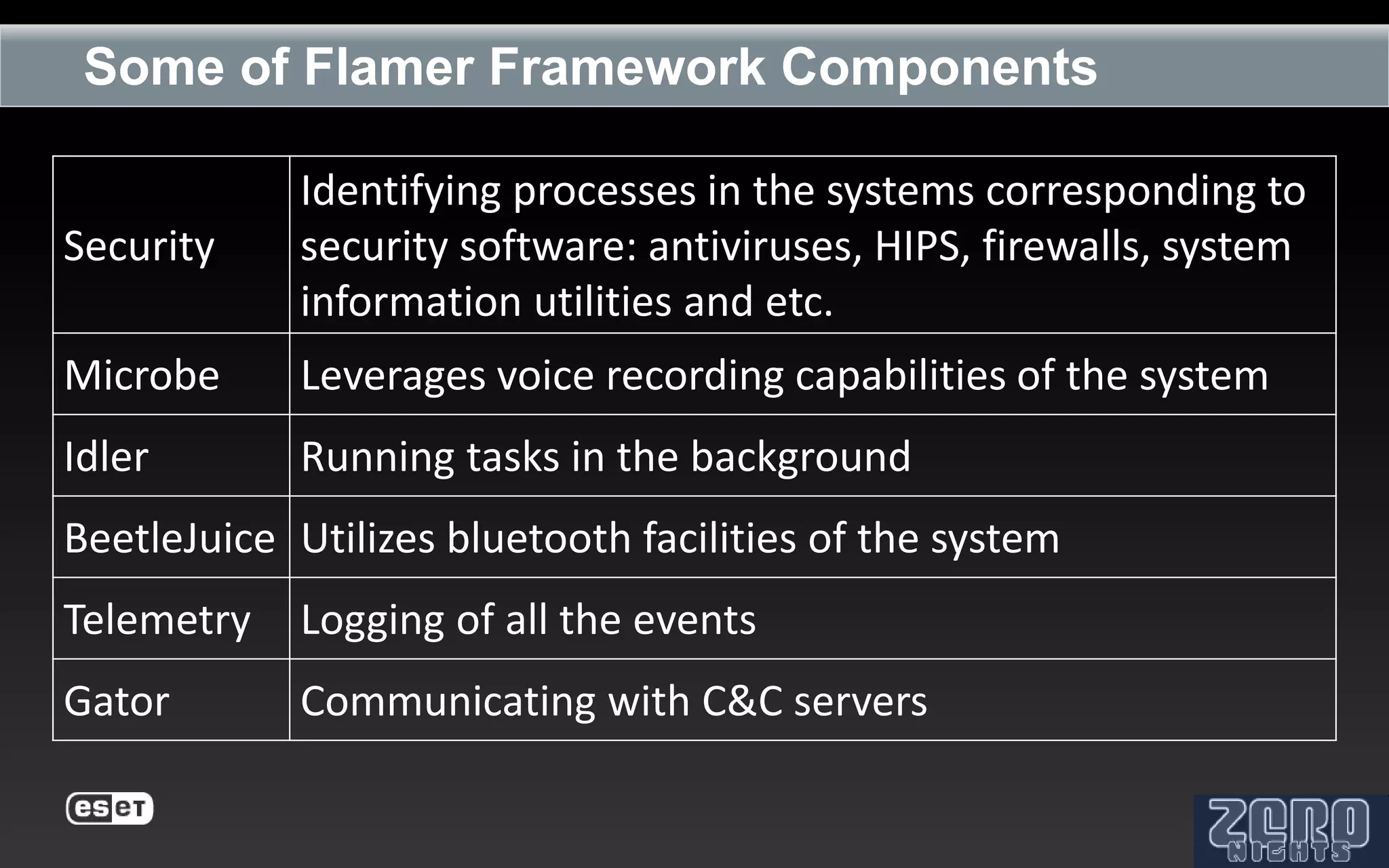
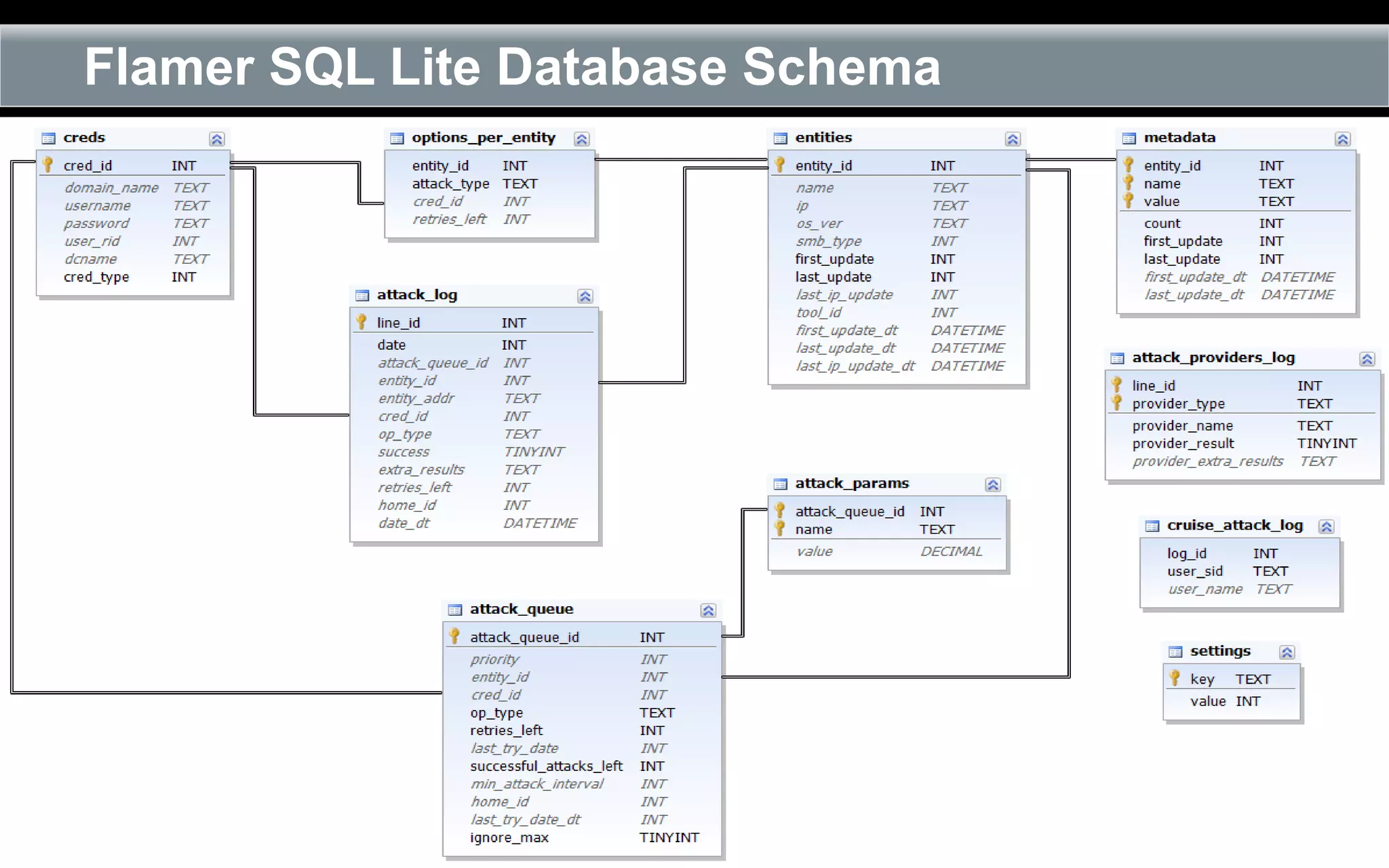
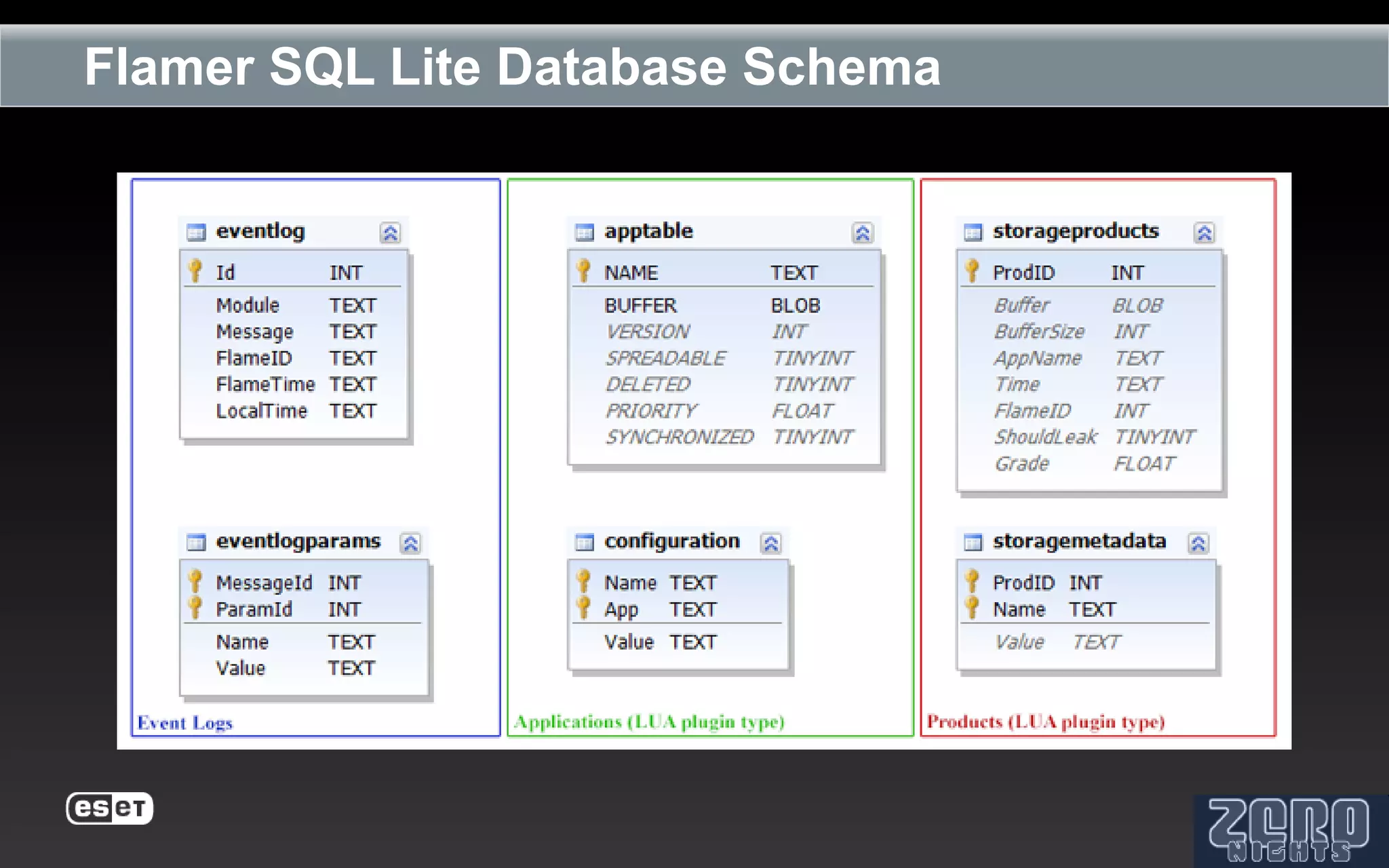
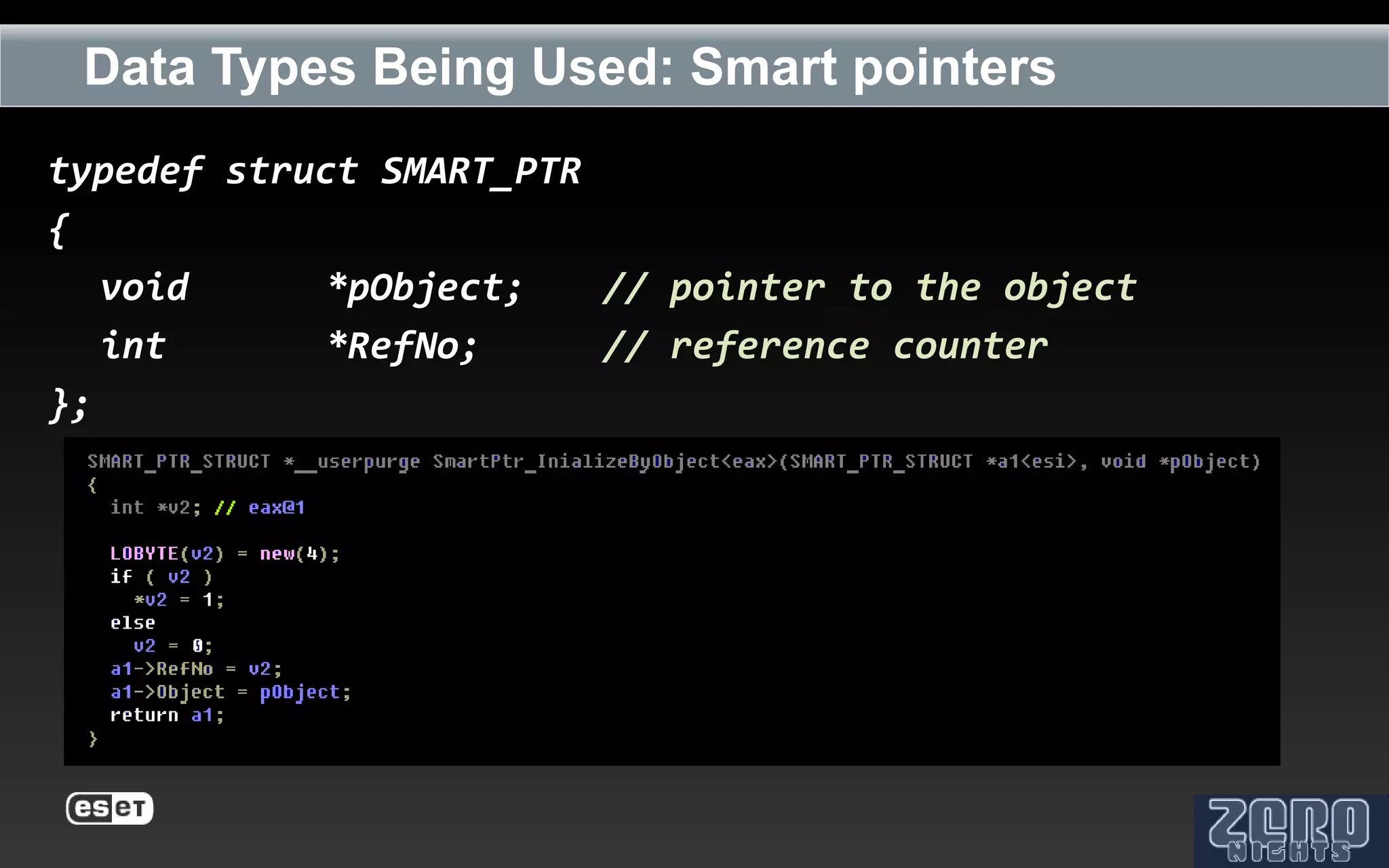
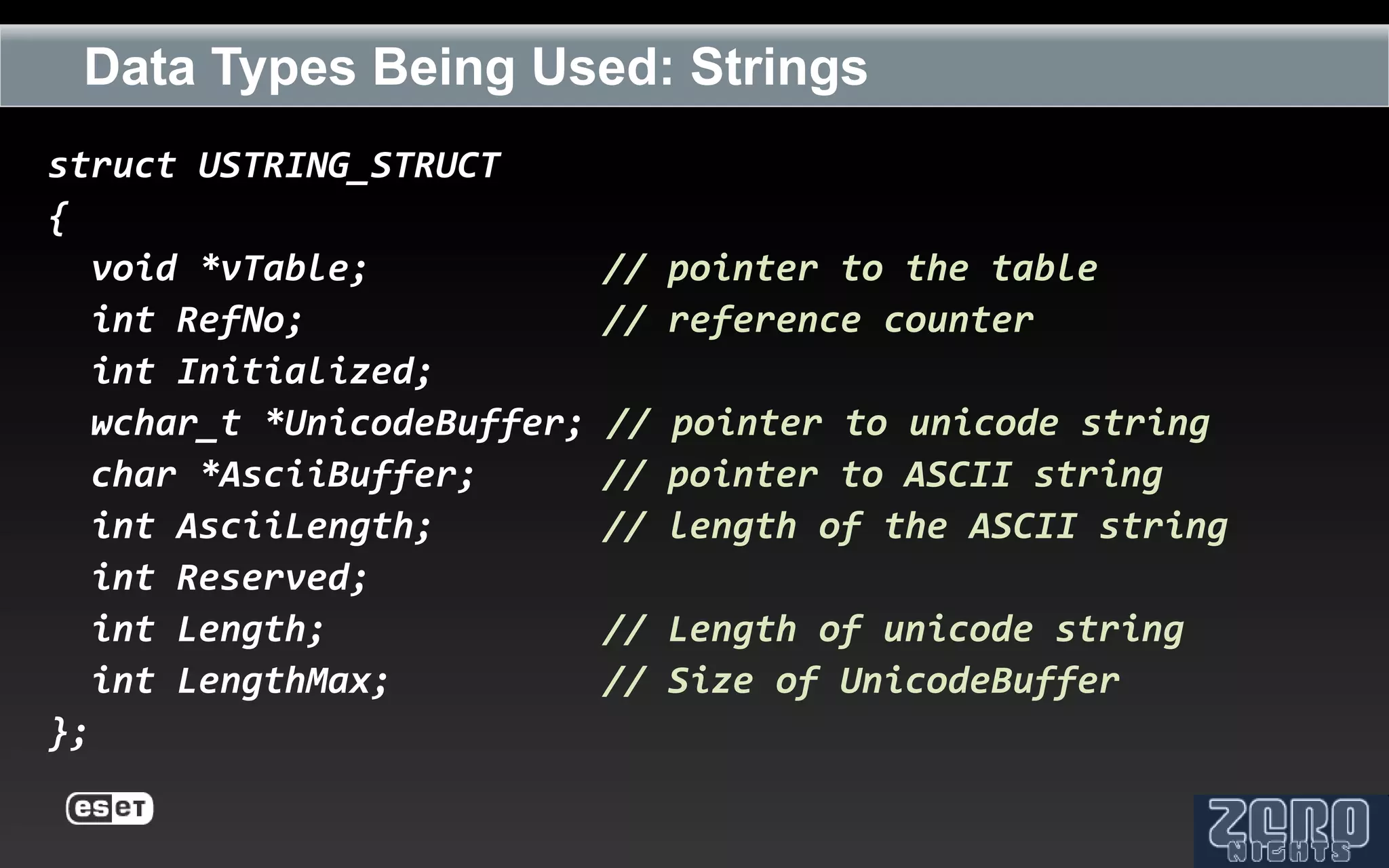
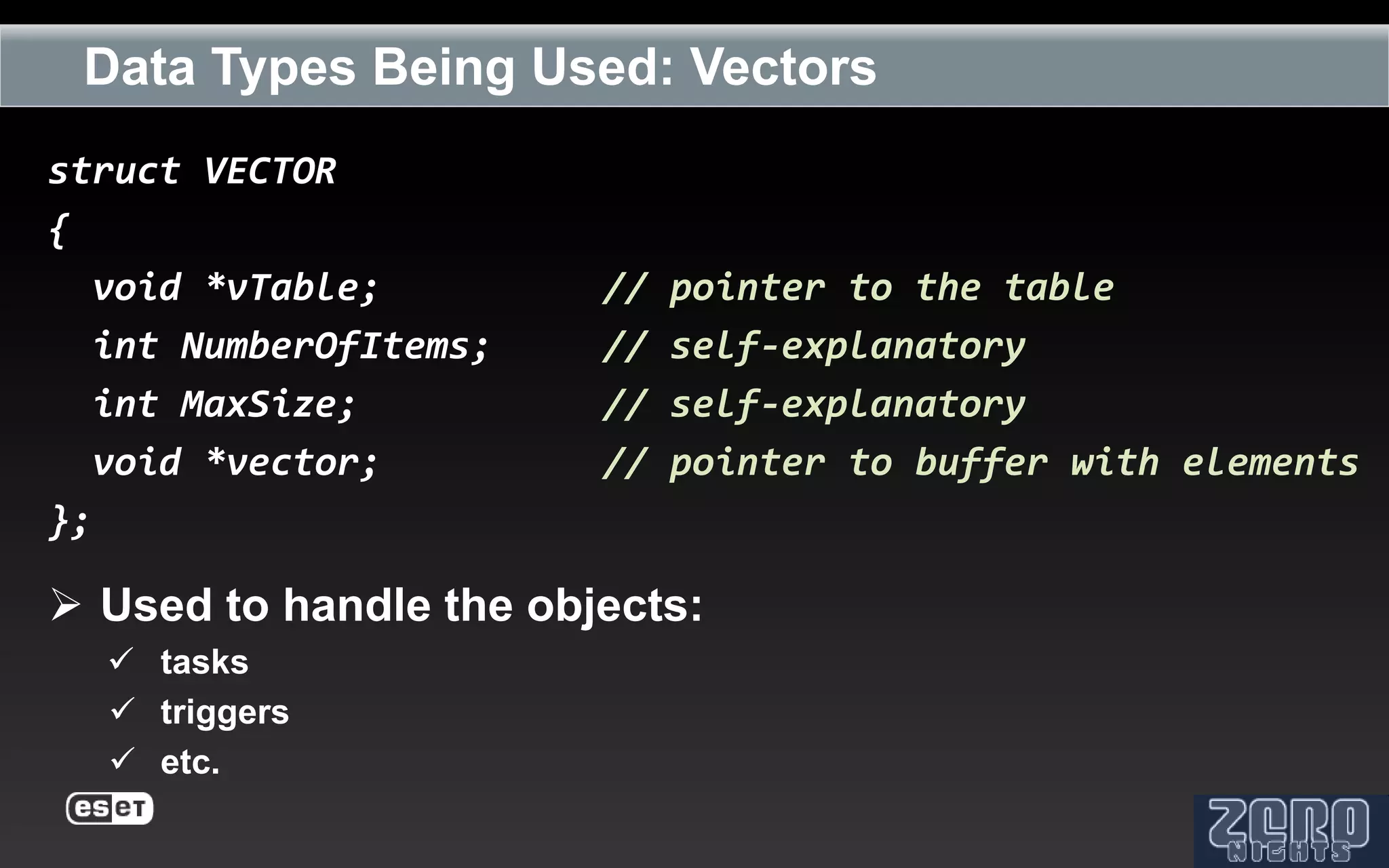
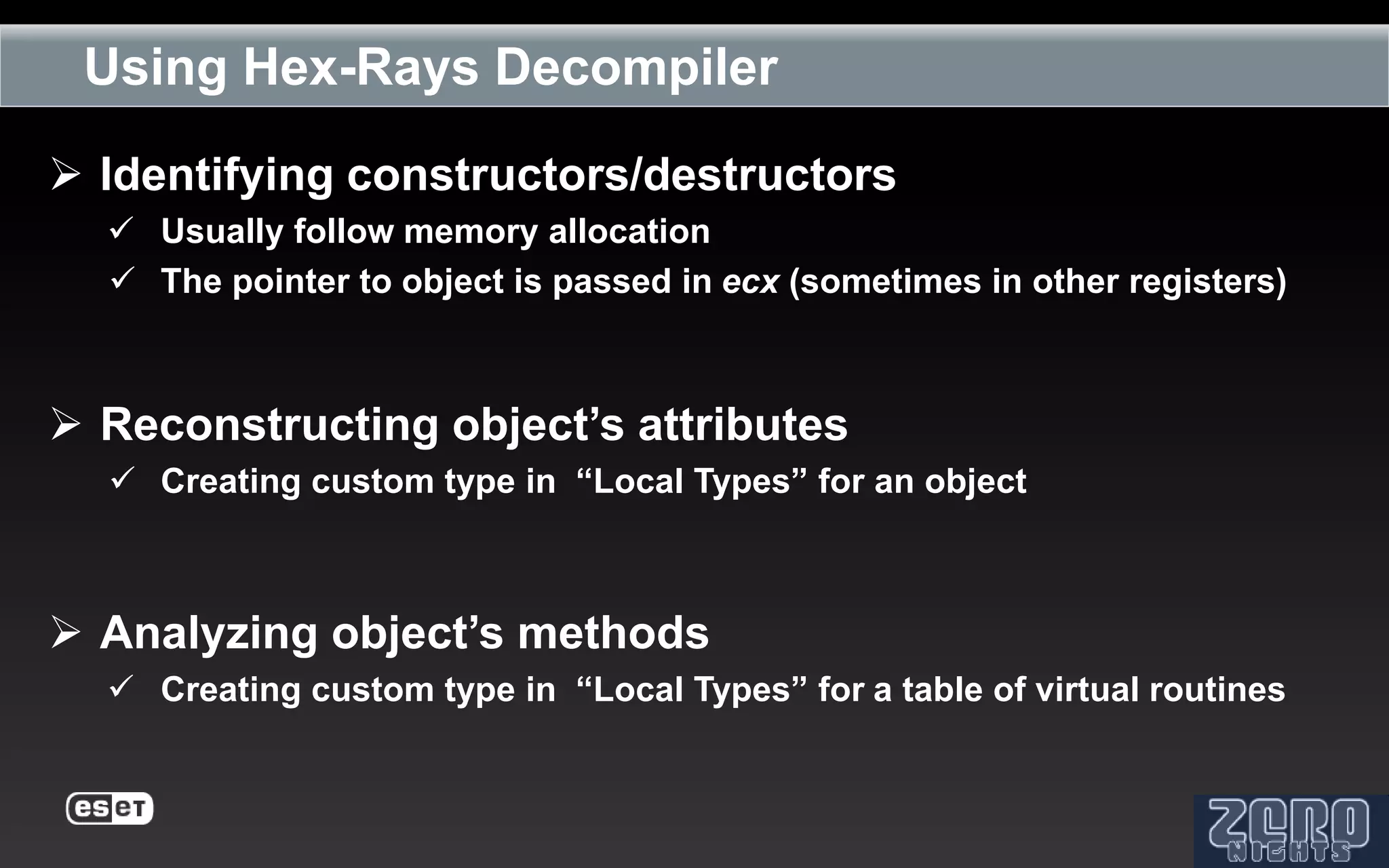
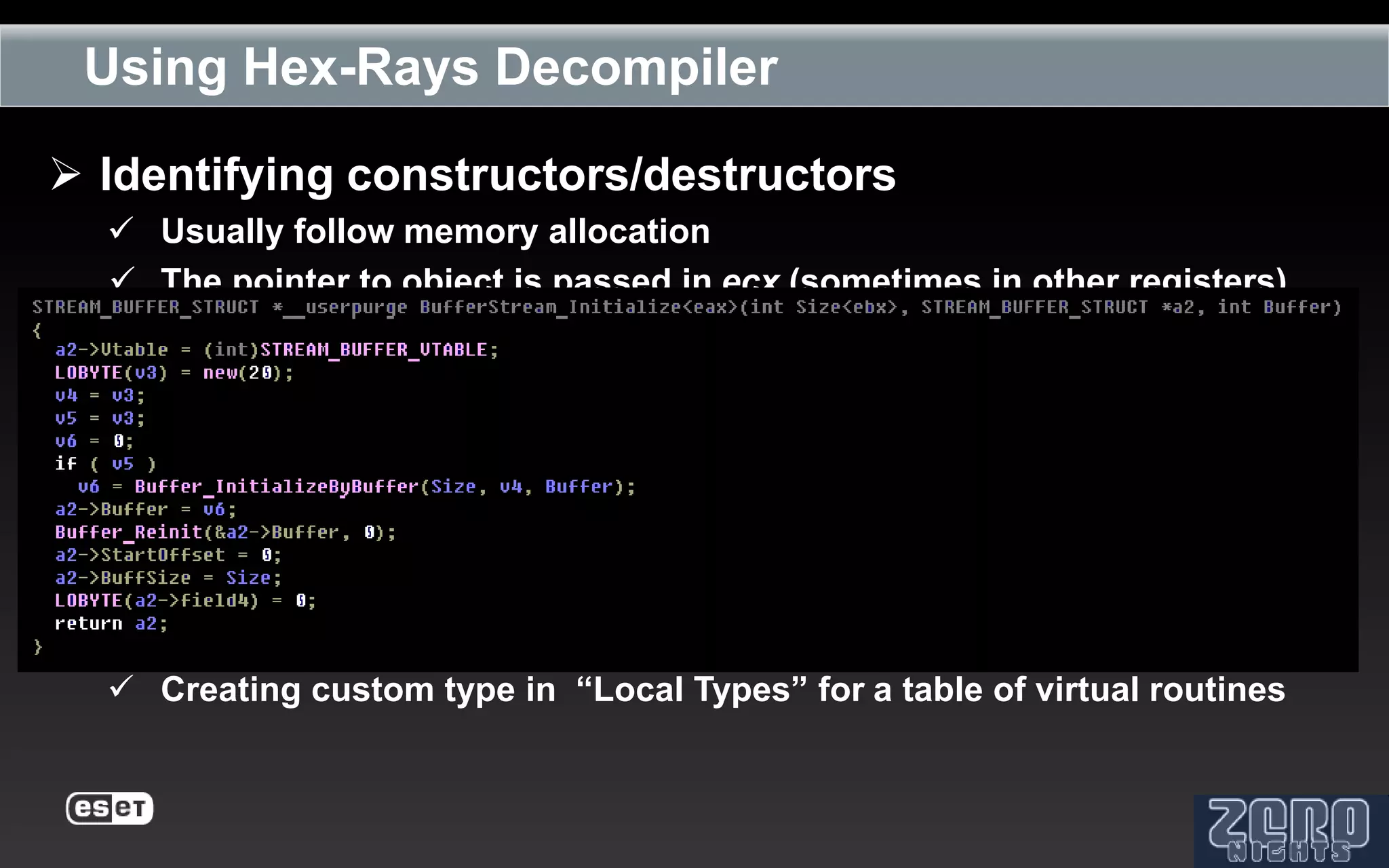
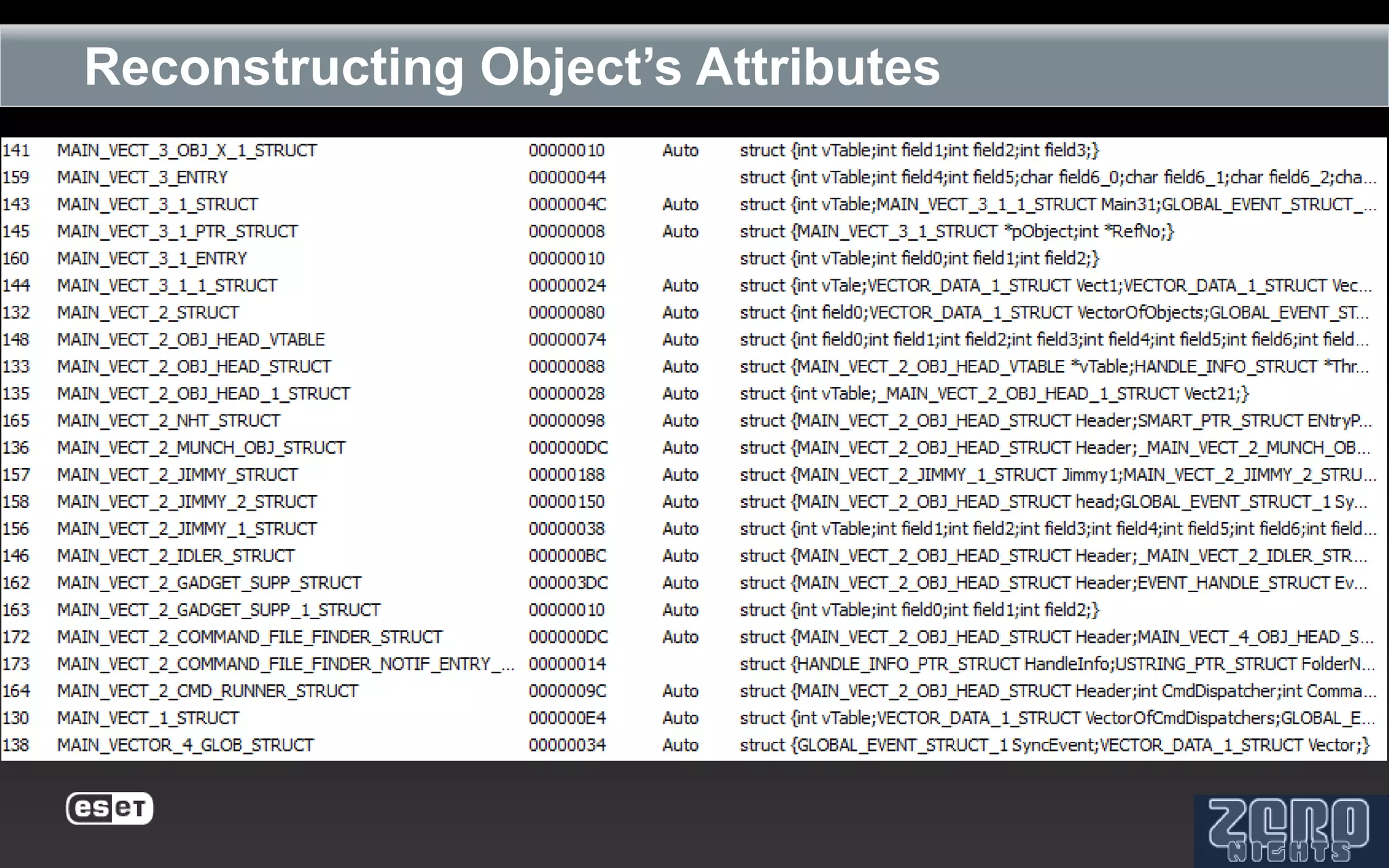
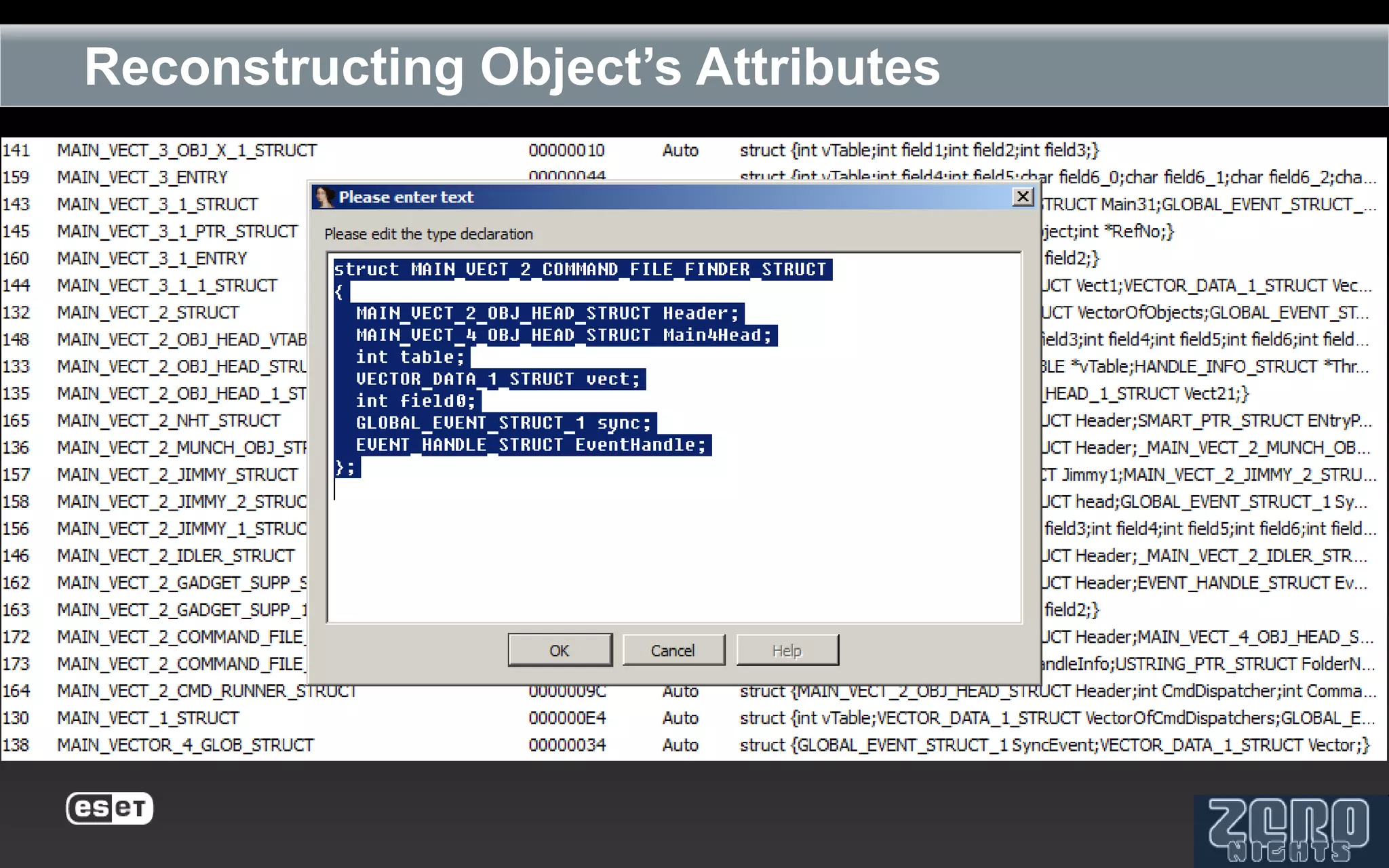
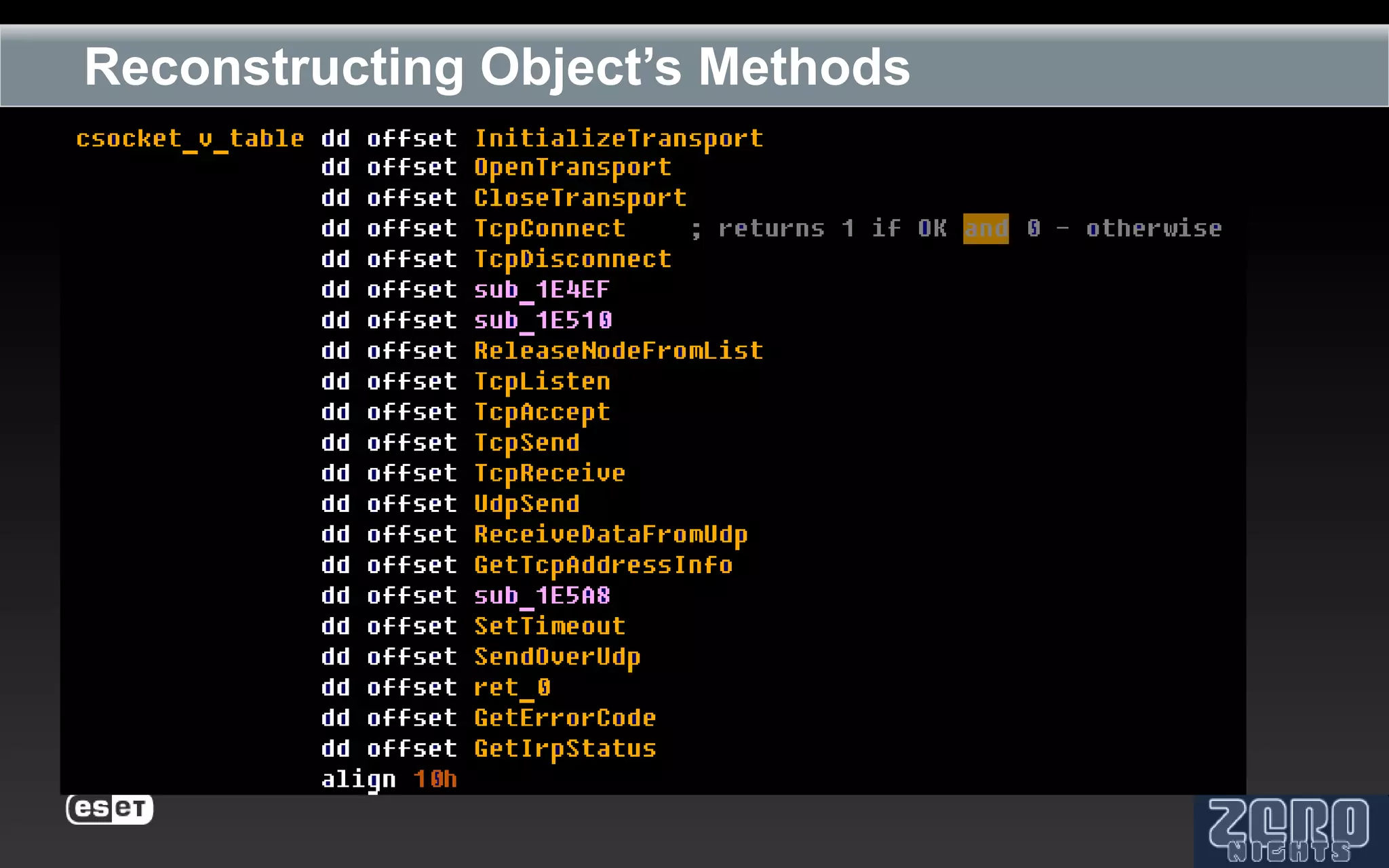
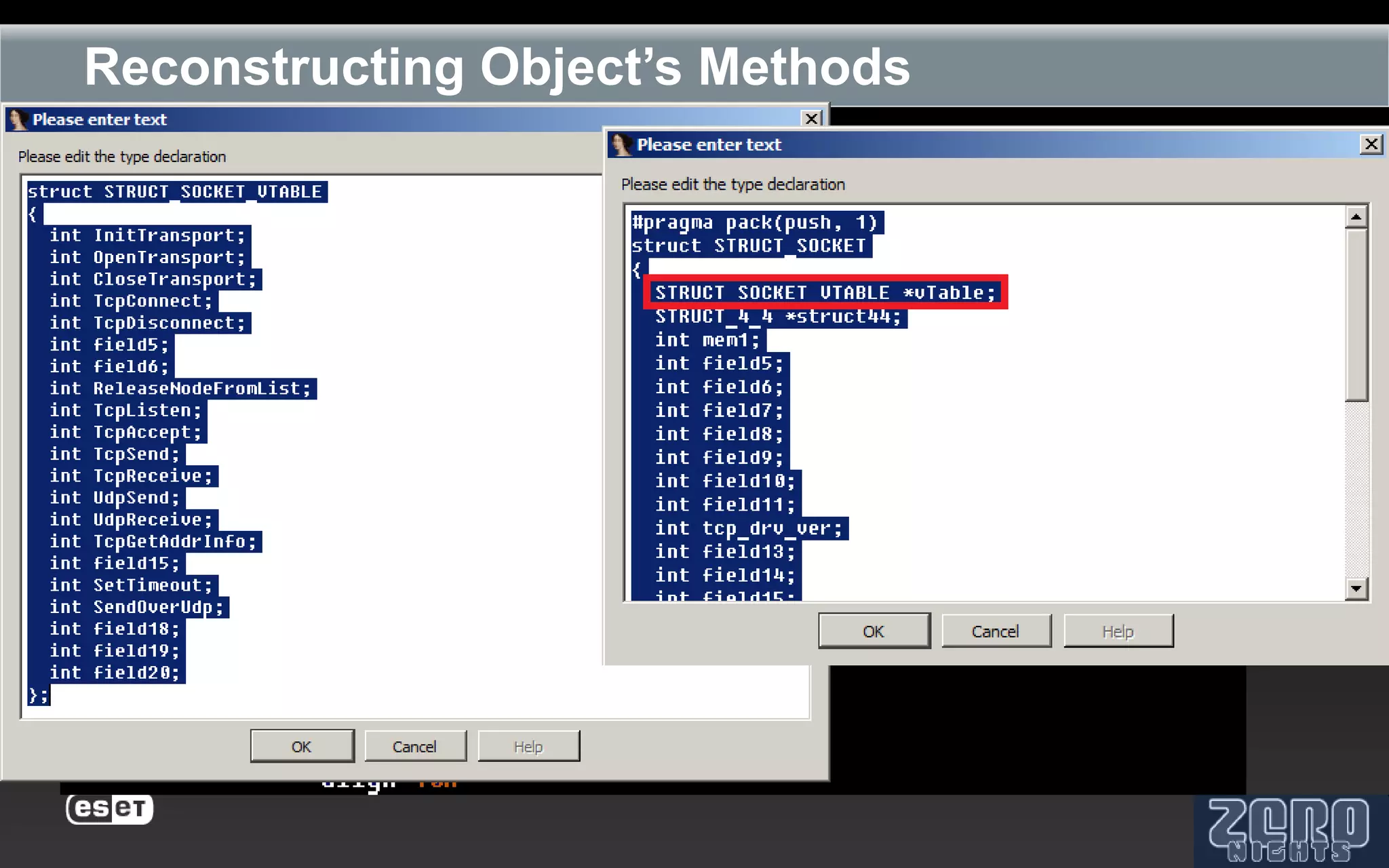
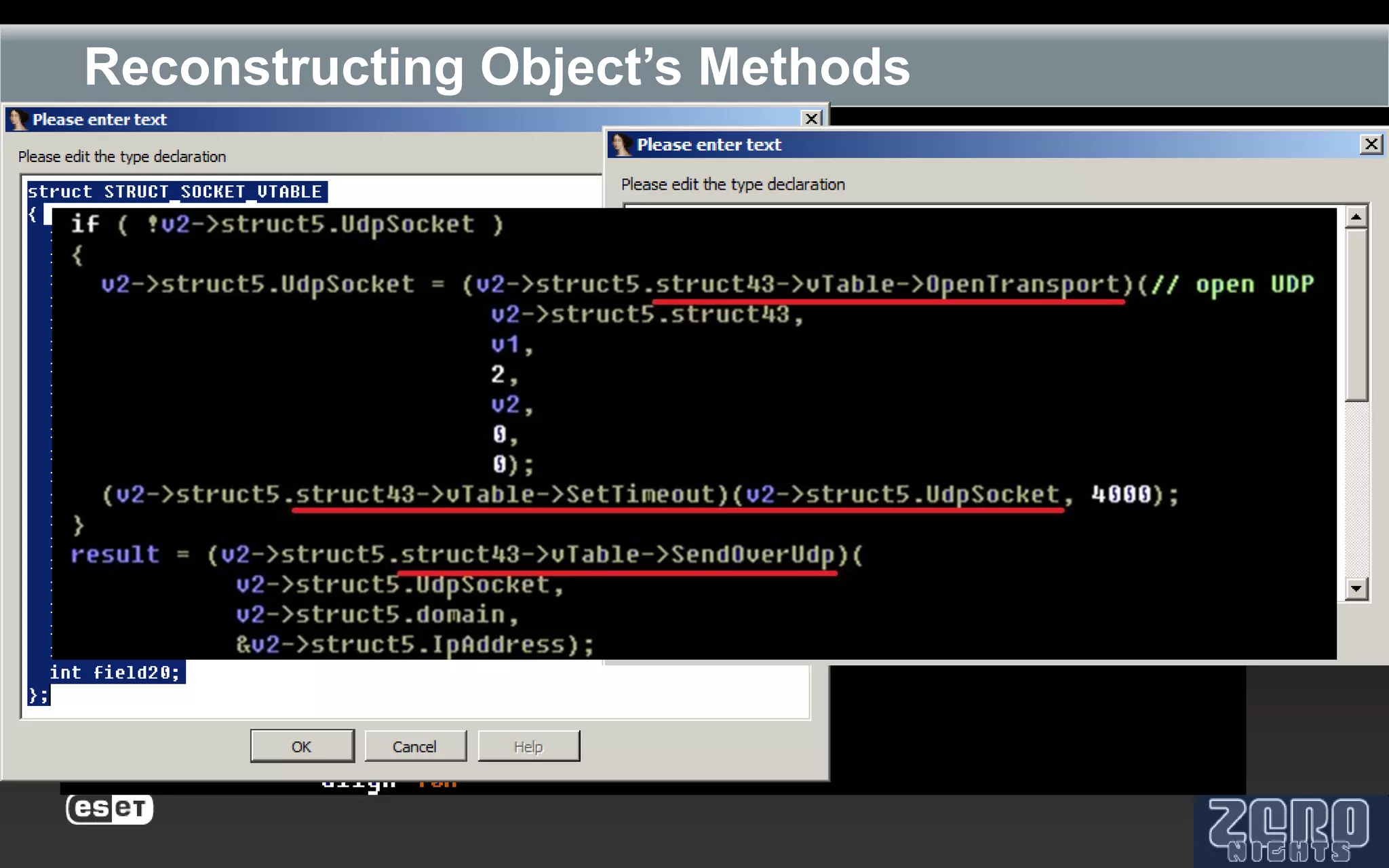
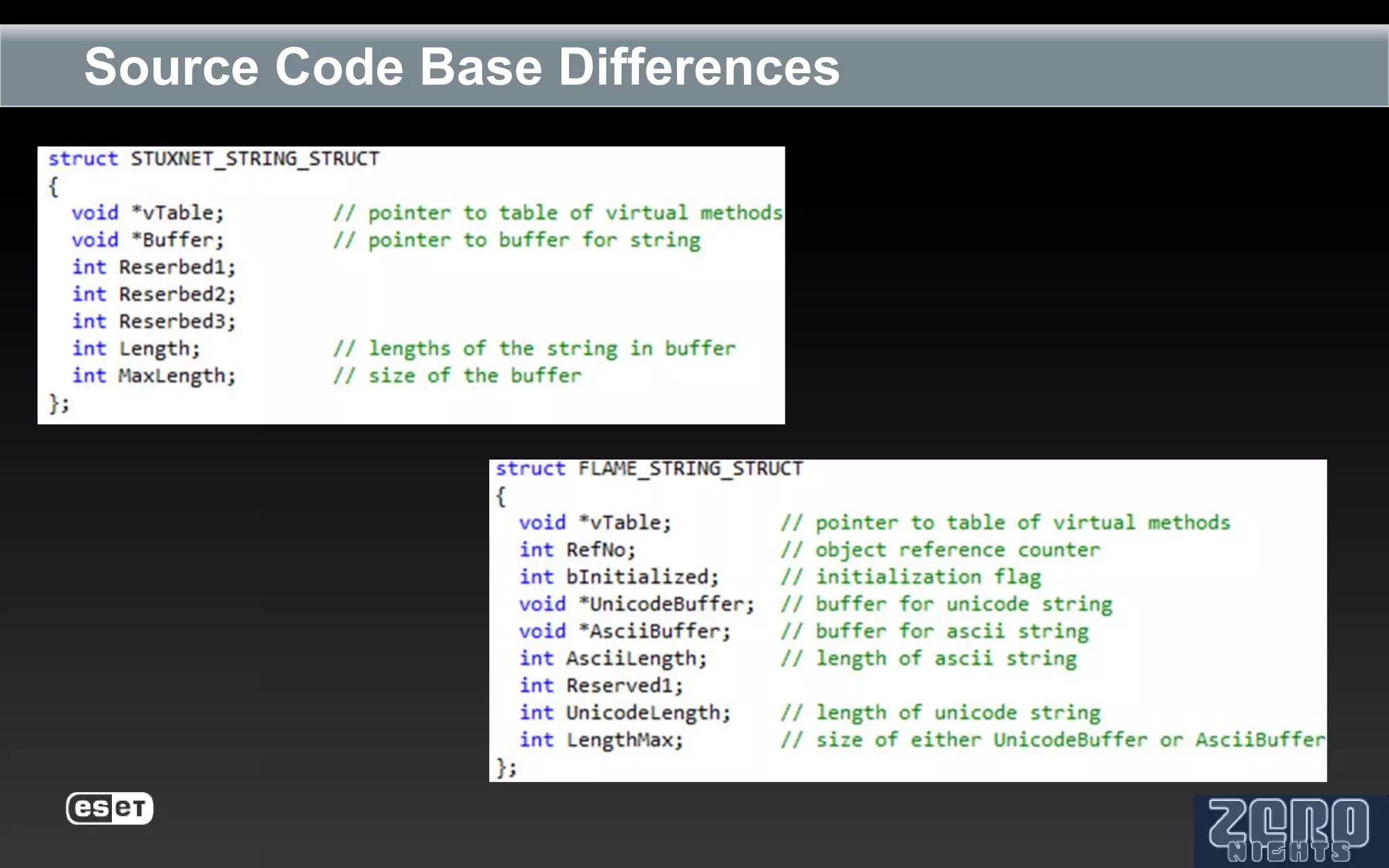
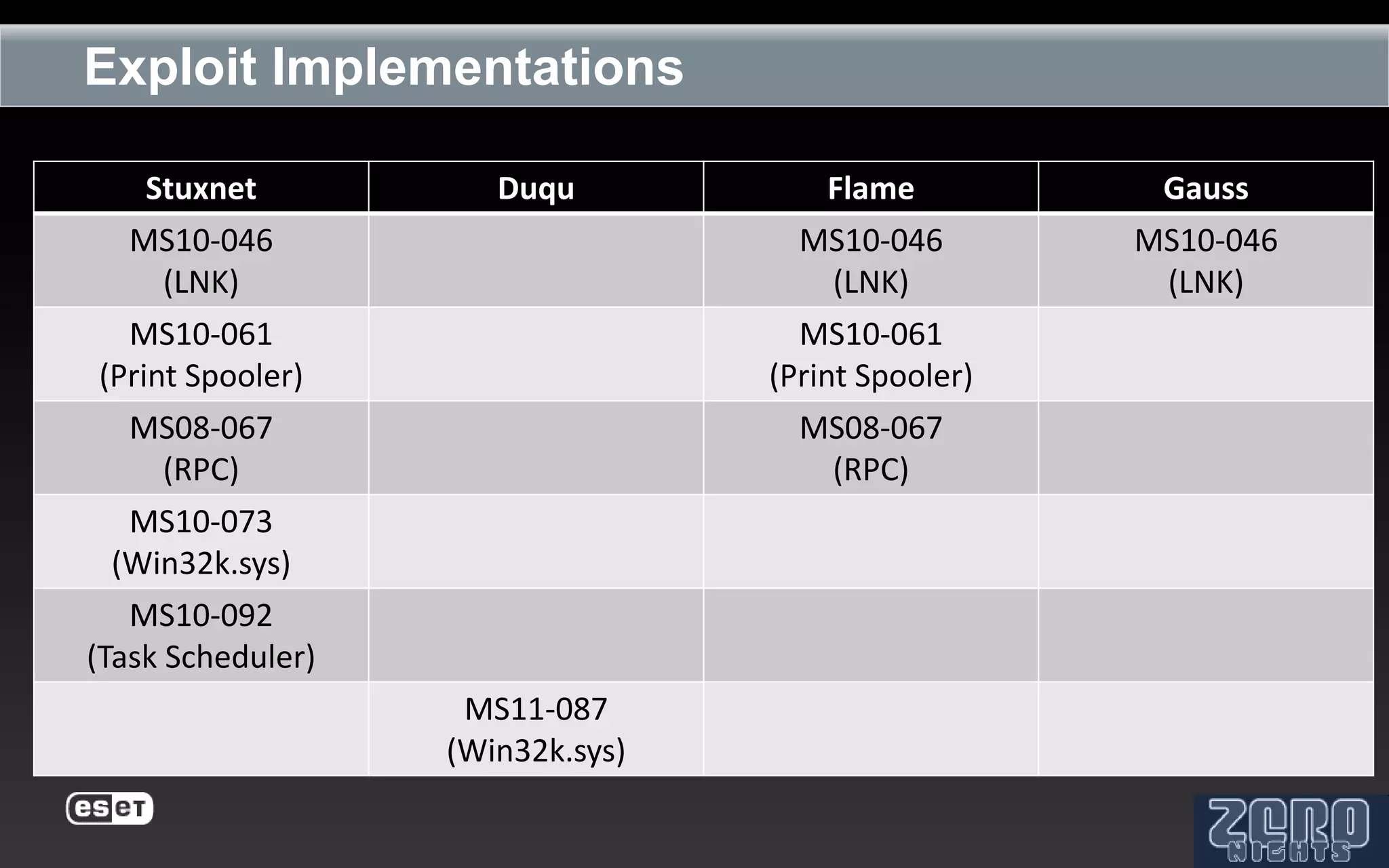
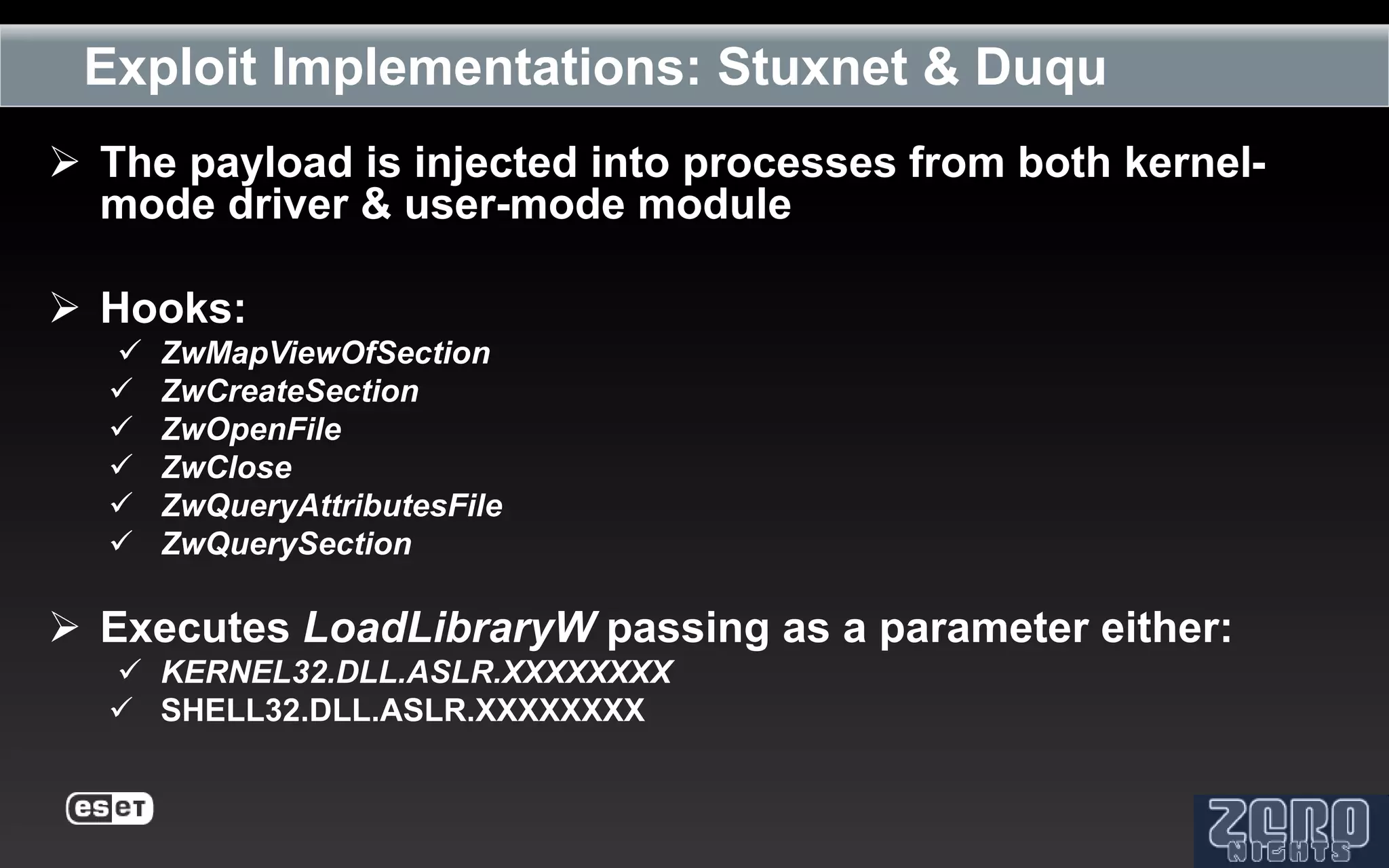
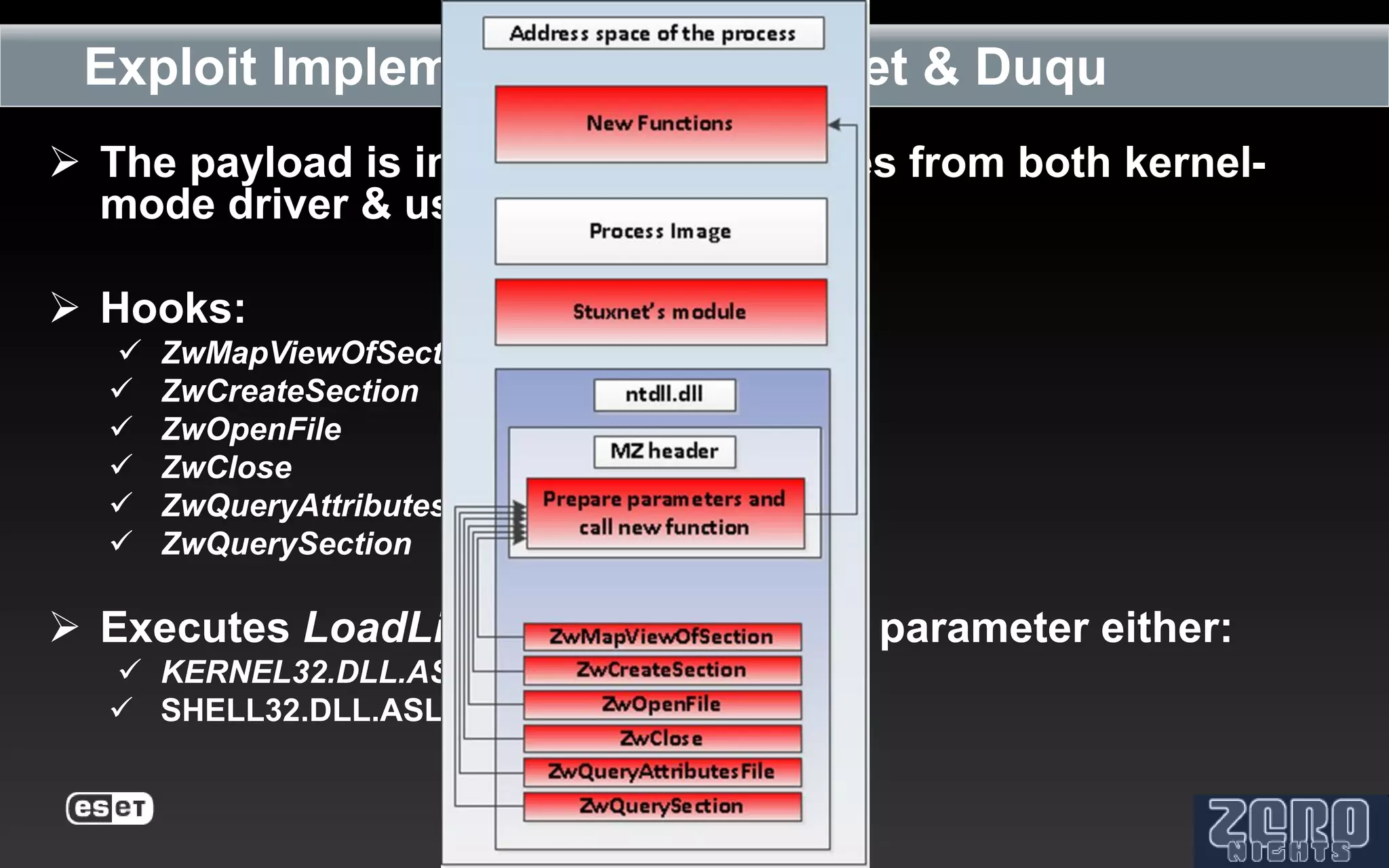
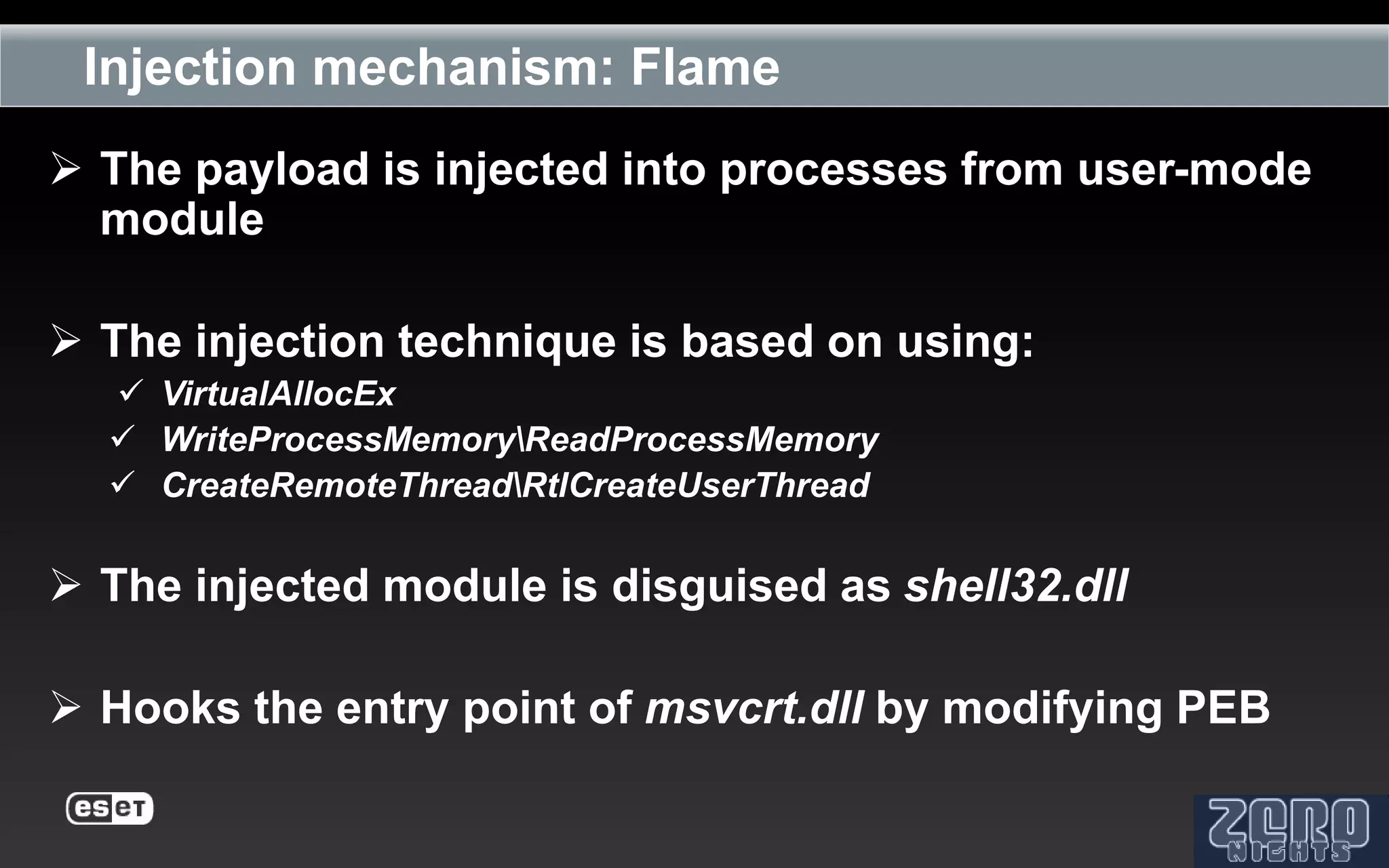
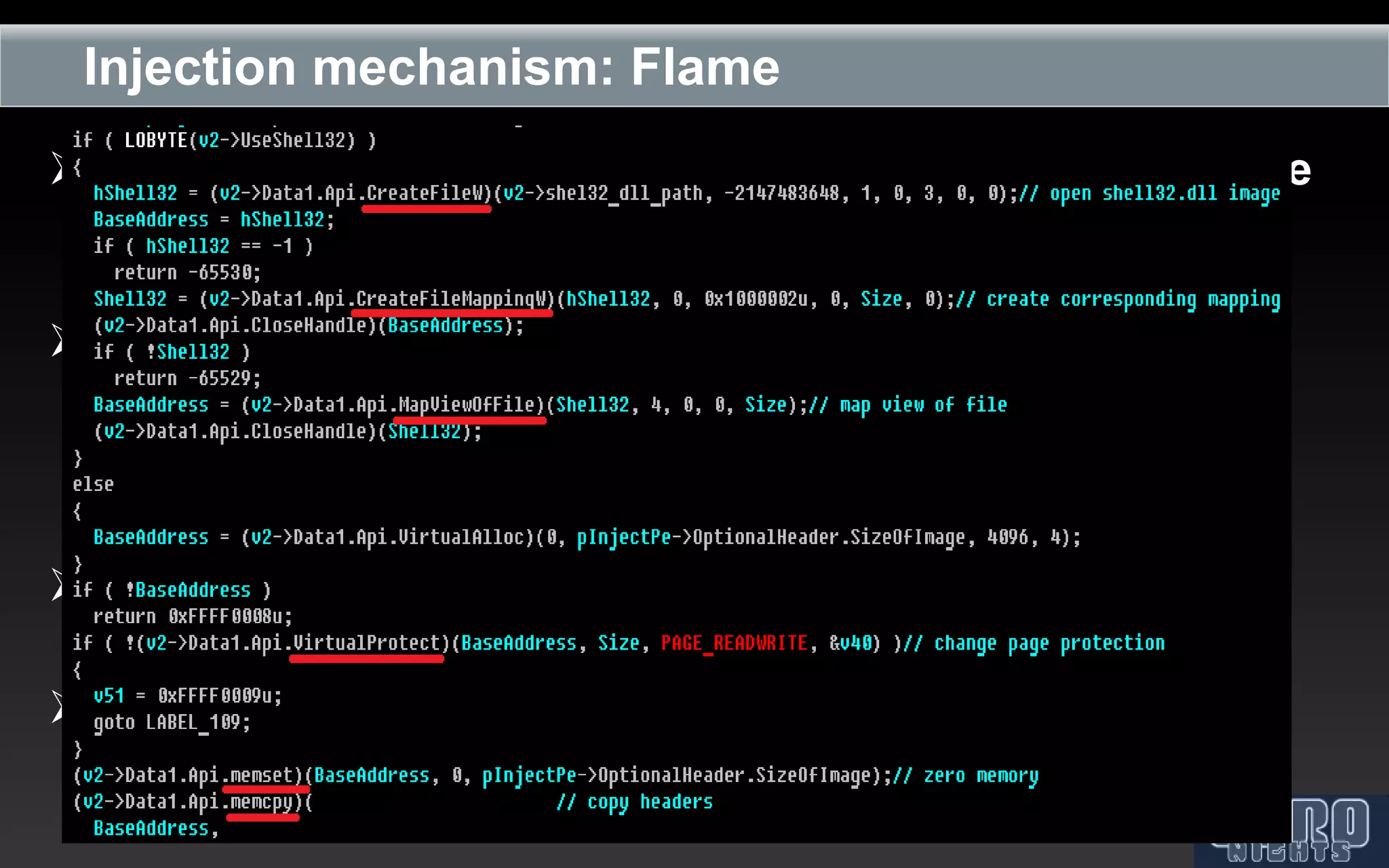
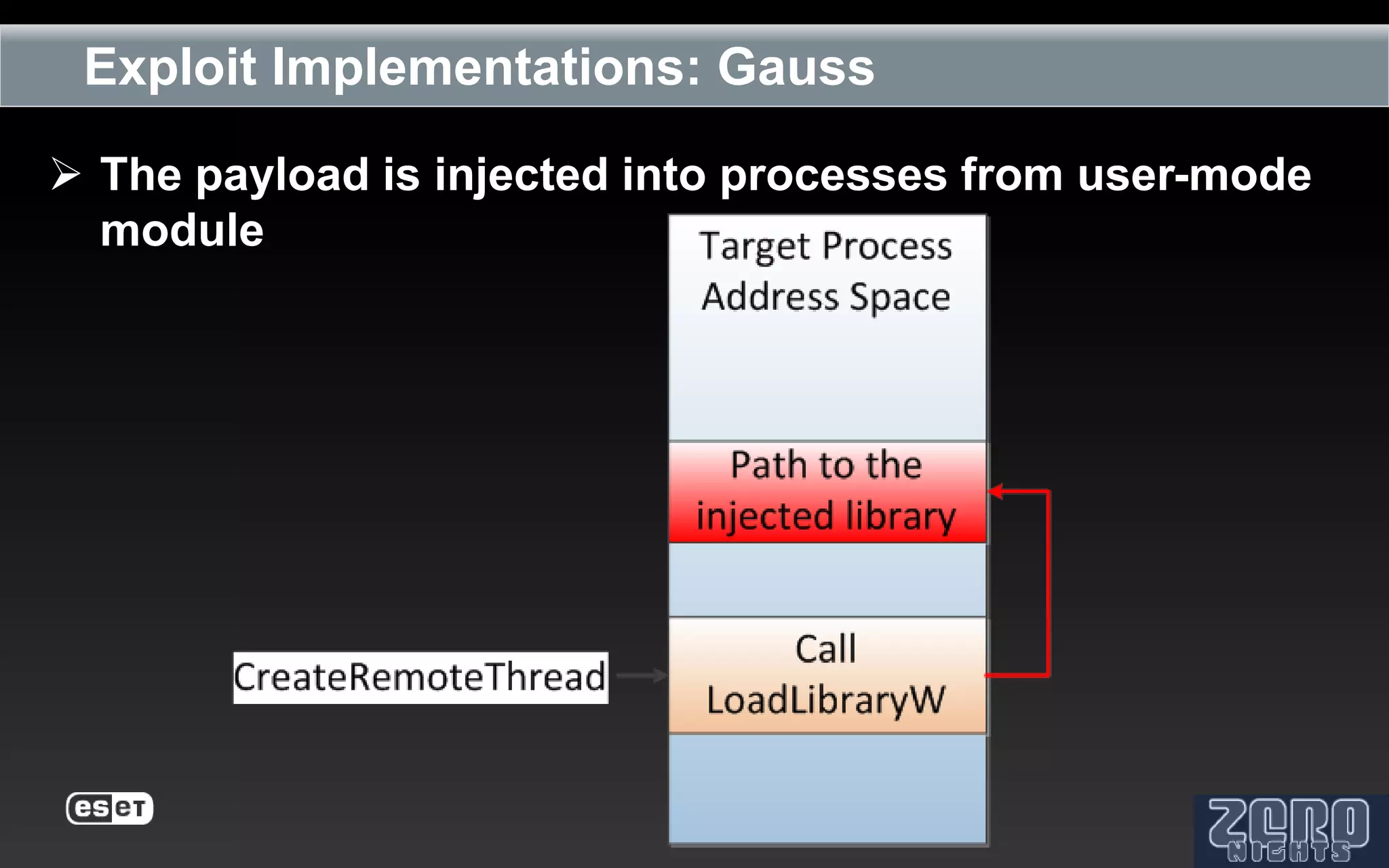
The document outlines the reverse engineering and reconstruction challenges of the Flamer malware framework in comparison to typical malware and the Stuxnet/Duqu exploits. It discusses aspects such as C++ code reconstruction, library identification issues, and the architectural components of Flamer including command executers and task management. The presentation also elaborates on the injection mechanisms used by Flamer and its relation to other malware variants.