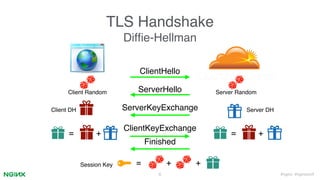
1. The document discusses TLS session resumption across multiple servers using ngx_lua. It introduces TLS handshakes and session resumption.
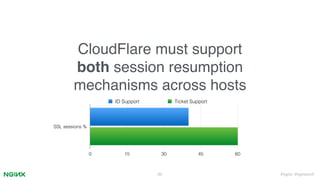
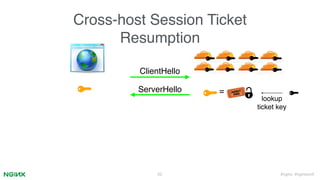
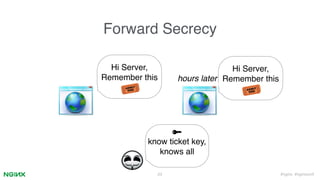
2. It describes how ngx_lua can implement cross-host session resumption via session IDs and tickets through Lua scripts while maintaining performance and forward secrecy. Small patches are needed to Nginx/OpenSSL.
3. Key aspects covered are a memcached session store interface, non-blocking I/O, ticket key encryption and rotation, and configuration via Lua scripts without modifying Nginx core. This allows cross-host session resumption compatible with TLSv1.3.

























![#nginx #nginxconf30
Sample solution: Augmented nginx conf
Set "ssl_session_cache memcached:<name>[:<host>[:<port>]]"
• Blocking I/O :(
• Need to add session encryption :(
• No tests. :(](https://image.slidesharecdn.com/zinginxconf2015-150924234723-lva1-app6892/85/Zi-nginx-conf_2015-30-320.jpg)









![#nginx #nginxconf
Ticket key rotation
• Rotate the ticket encryption key once a while
• Nginx embeds a key array as OpenSSL ex_data
40
[key_0, key_1, key_2, … key_n]
encryption decryption
[new-key, key_0, key_1, key_2, … key_n]](https://image.slidesharecdn.com/zinginxconf2015-150924234723-lva1-app6892/85/Zi-nginx-conf_2015-40-320.jpg)
![#nginx #nginxconf41
Ticket key rotation
• Lock-free key synchronization
[key_0, key_{n}, key_{n-1}, … key_1, key_0]
[key_0, new-key, key_{n-1}, …, key_1, key_0]
[new-key, new-key, key_{n-1}, …, key_1, key_0]
[new-key, key_{n-1}, new-key, …, key_1, key_0]
[new-key, key_{n-1}, key_{n-2}, …, key_0, new-key]
Key update loop](https://image.slidesharecdn.com/zinginxconf2015-150924234723-lva1-app6892/85/Zi-nginx-conf_2015-41-320.jpg)








