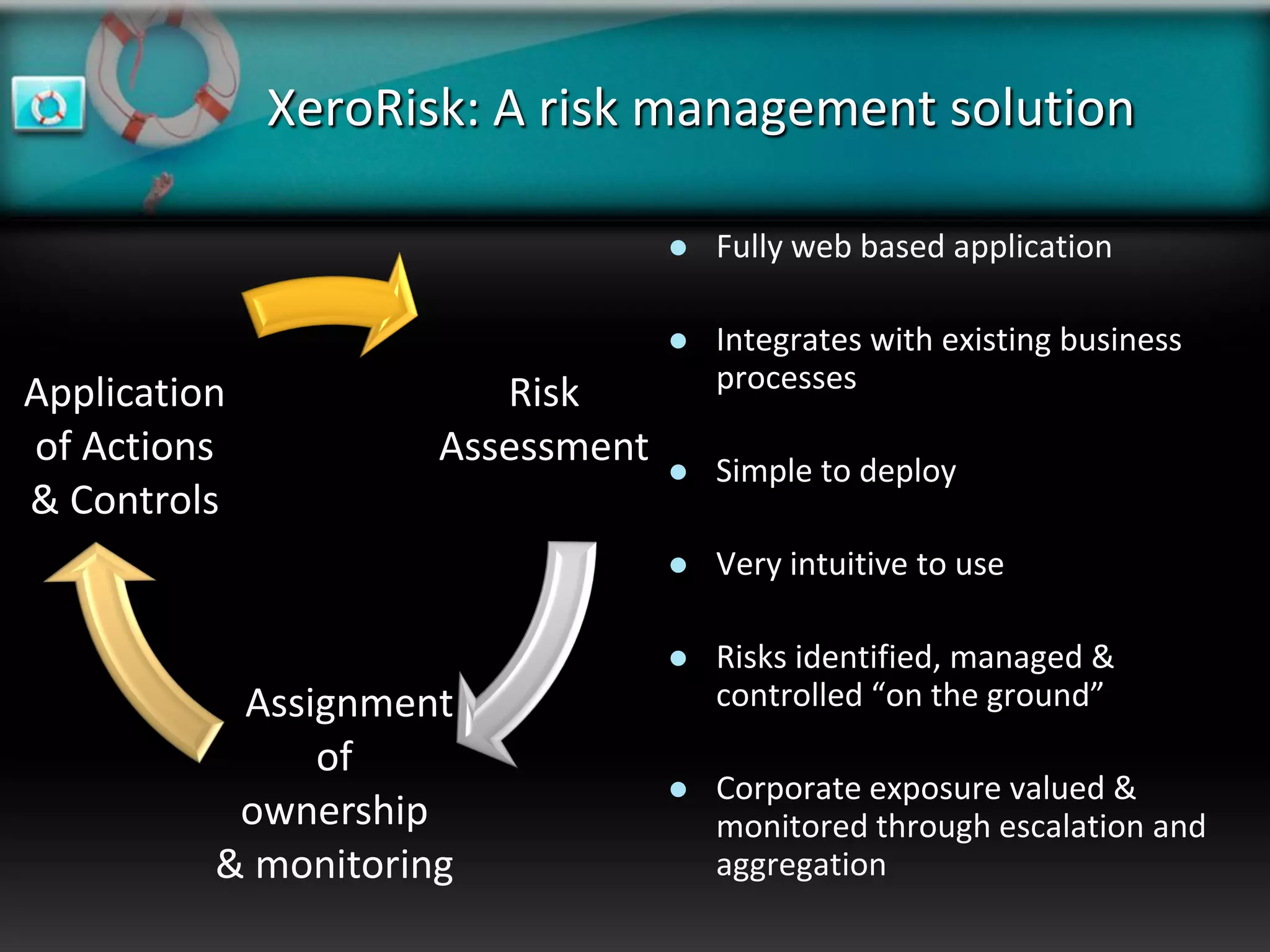
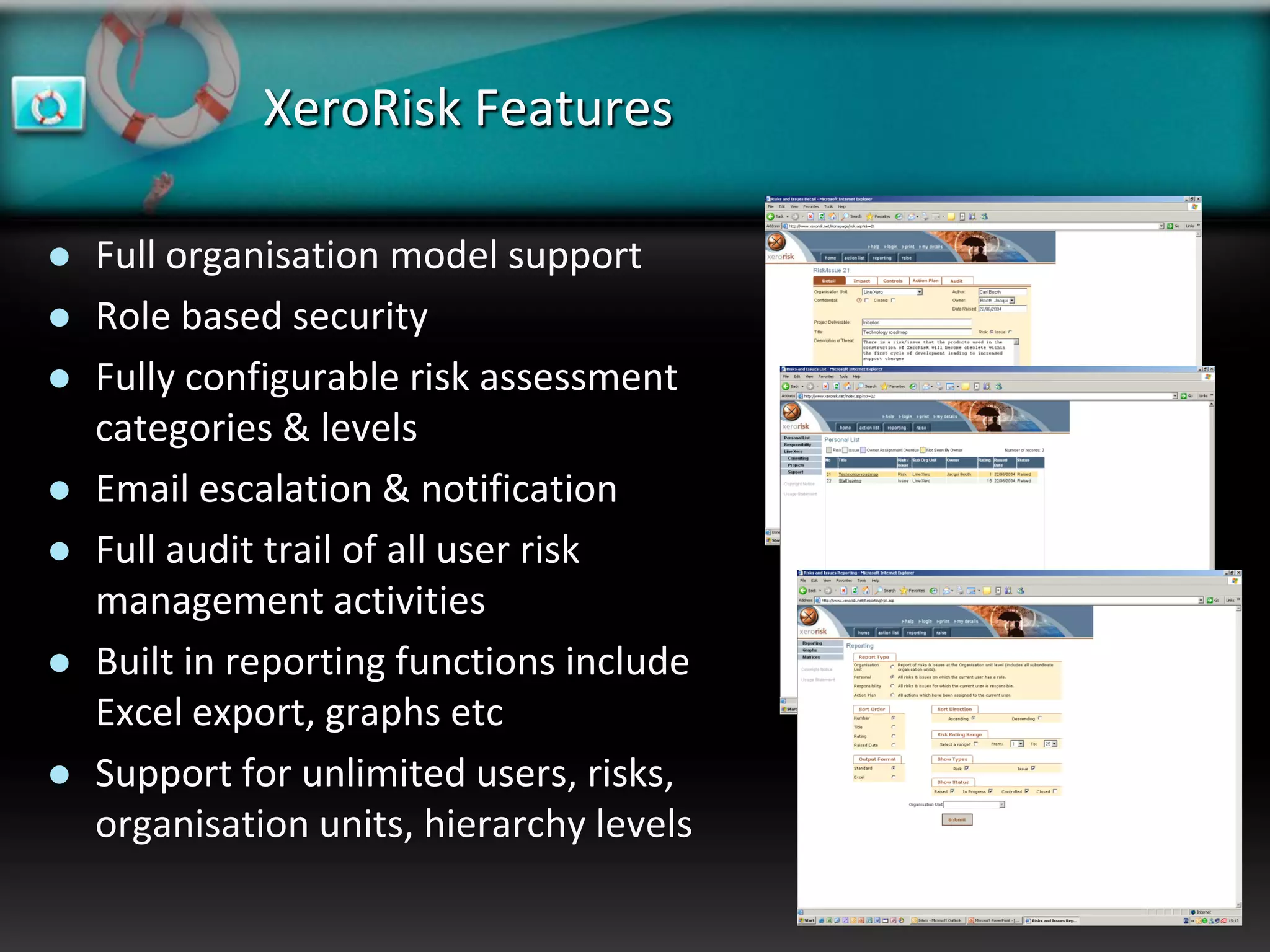
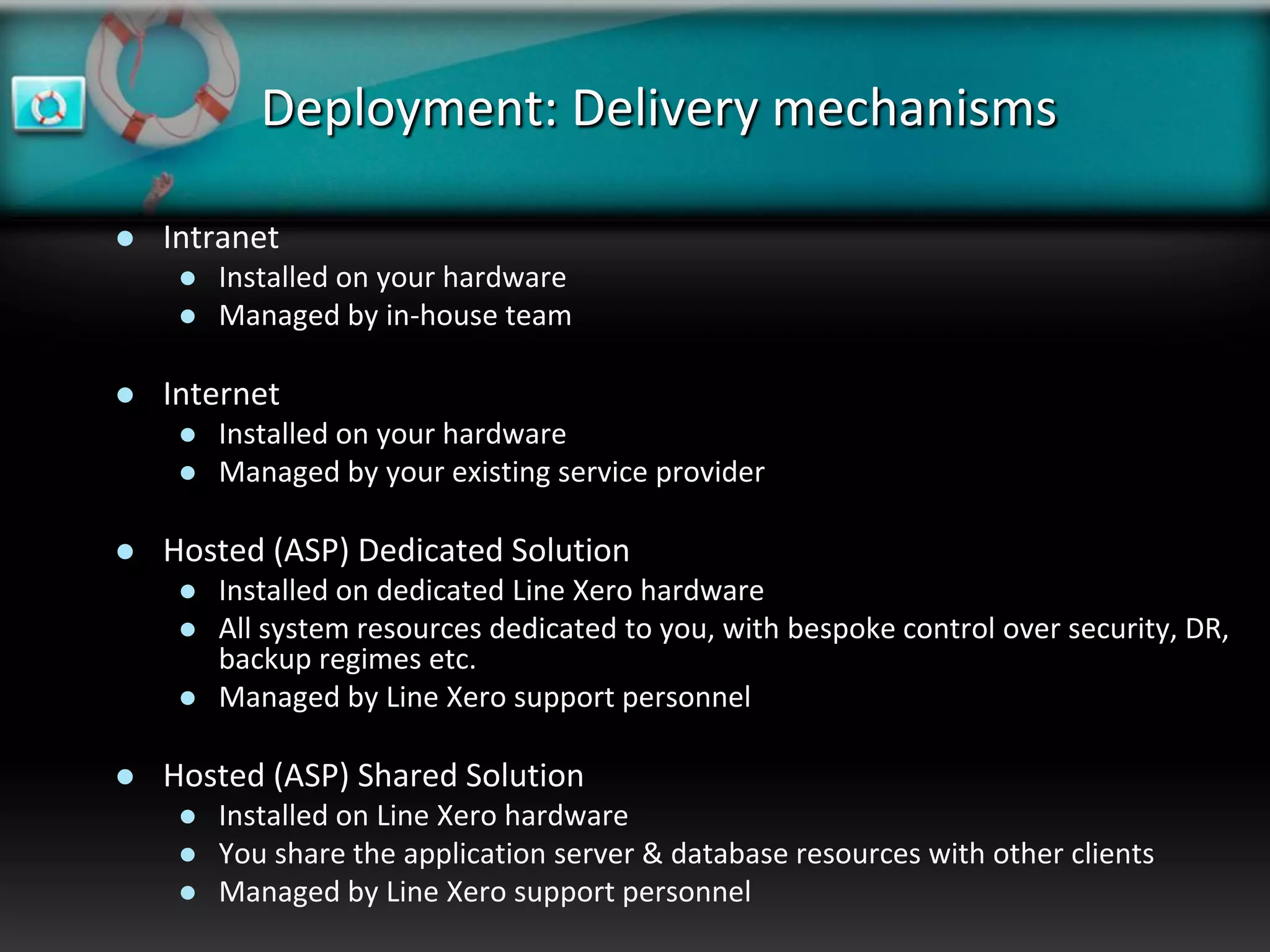
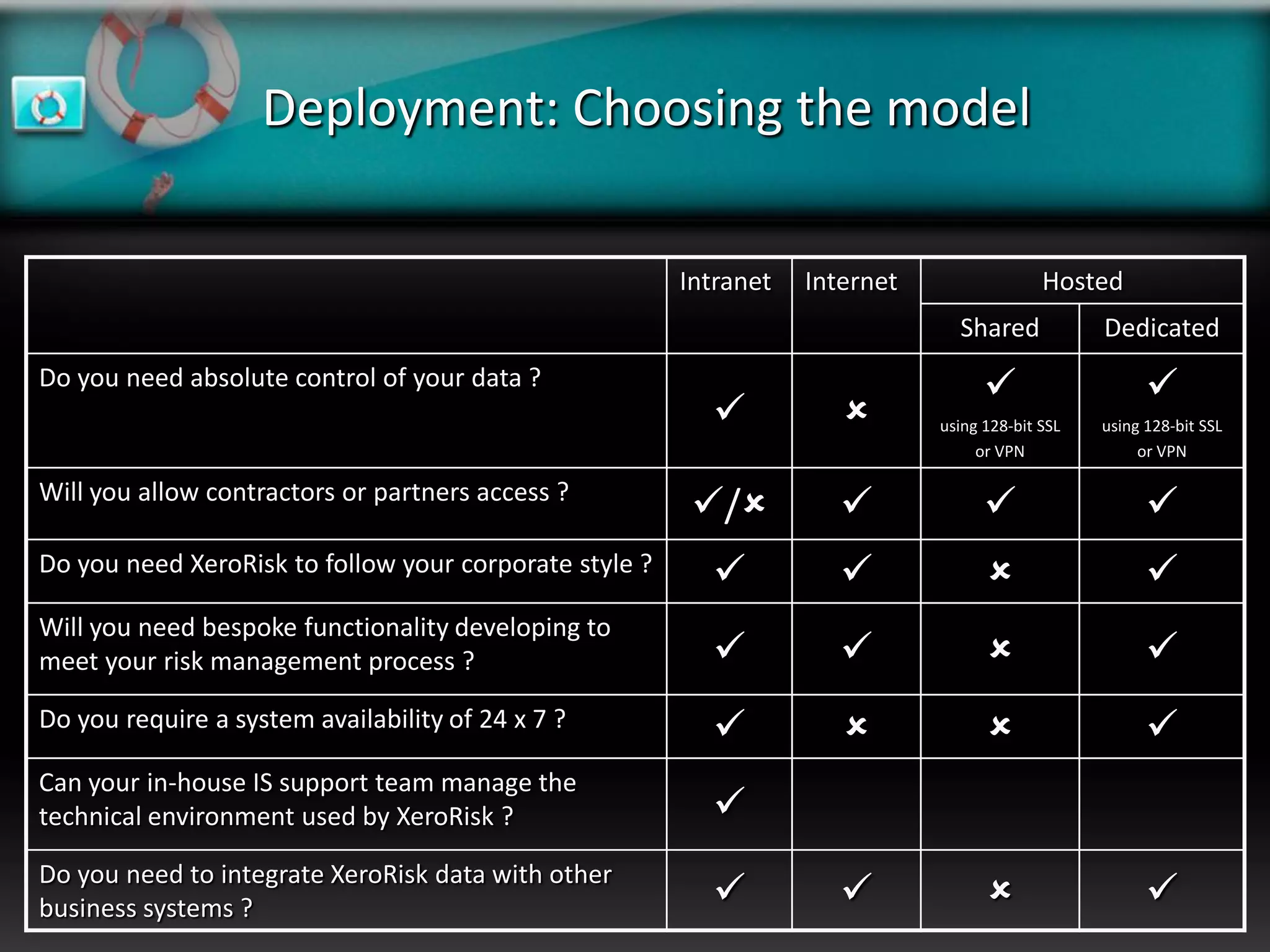
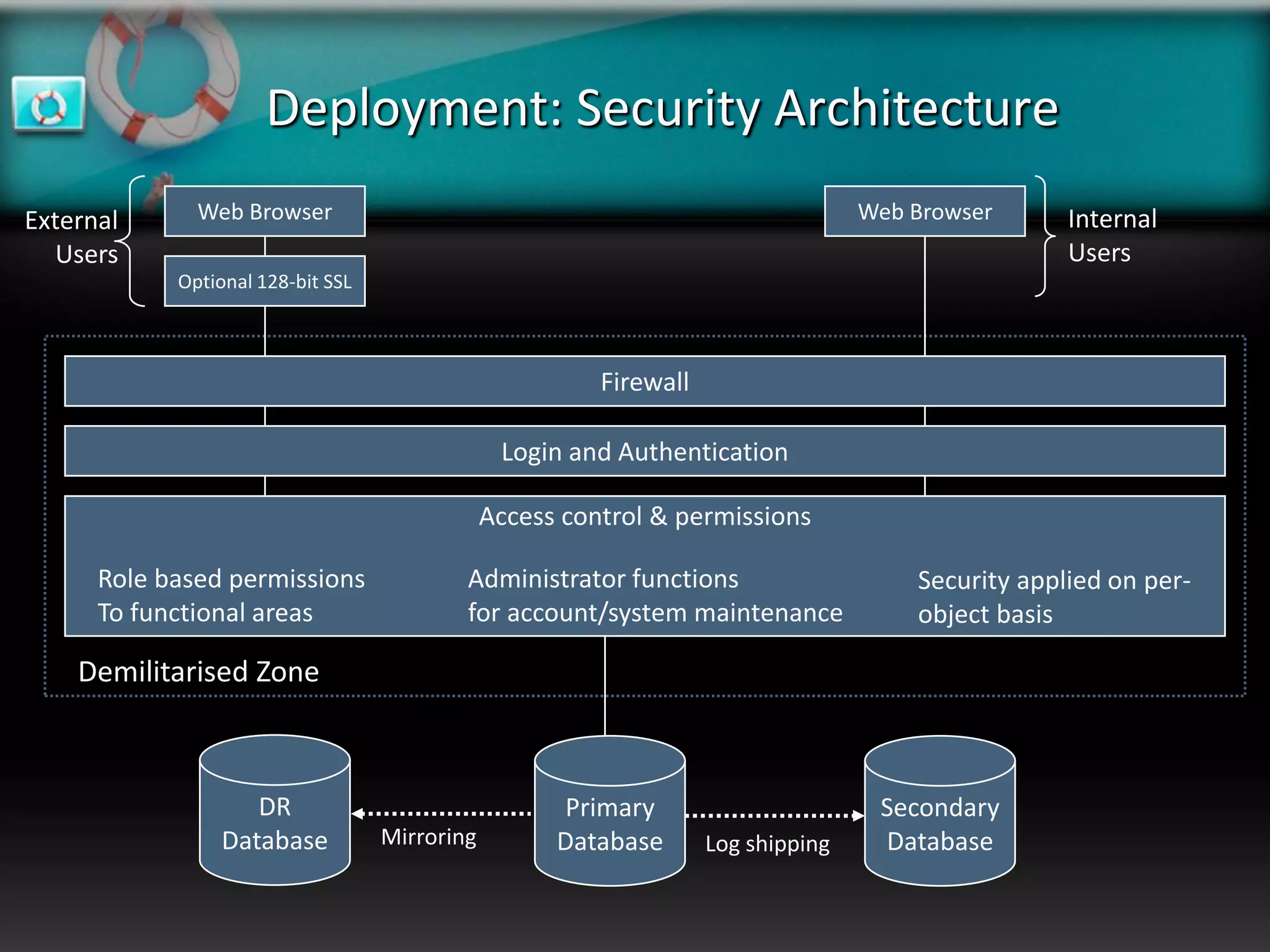
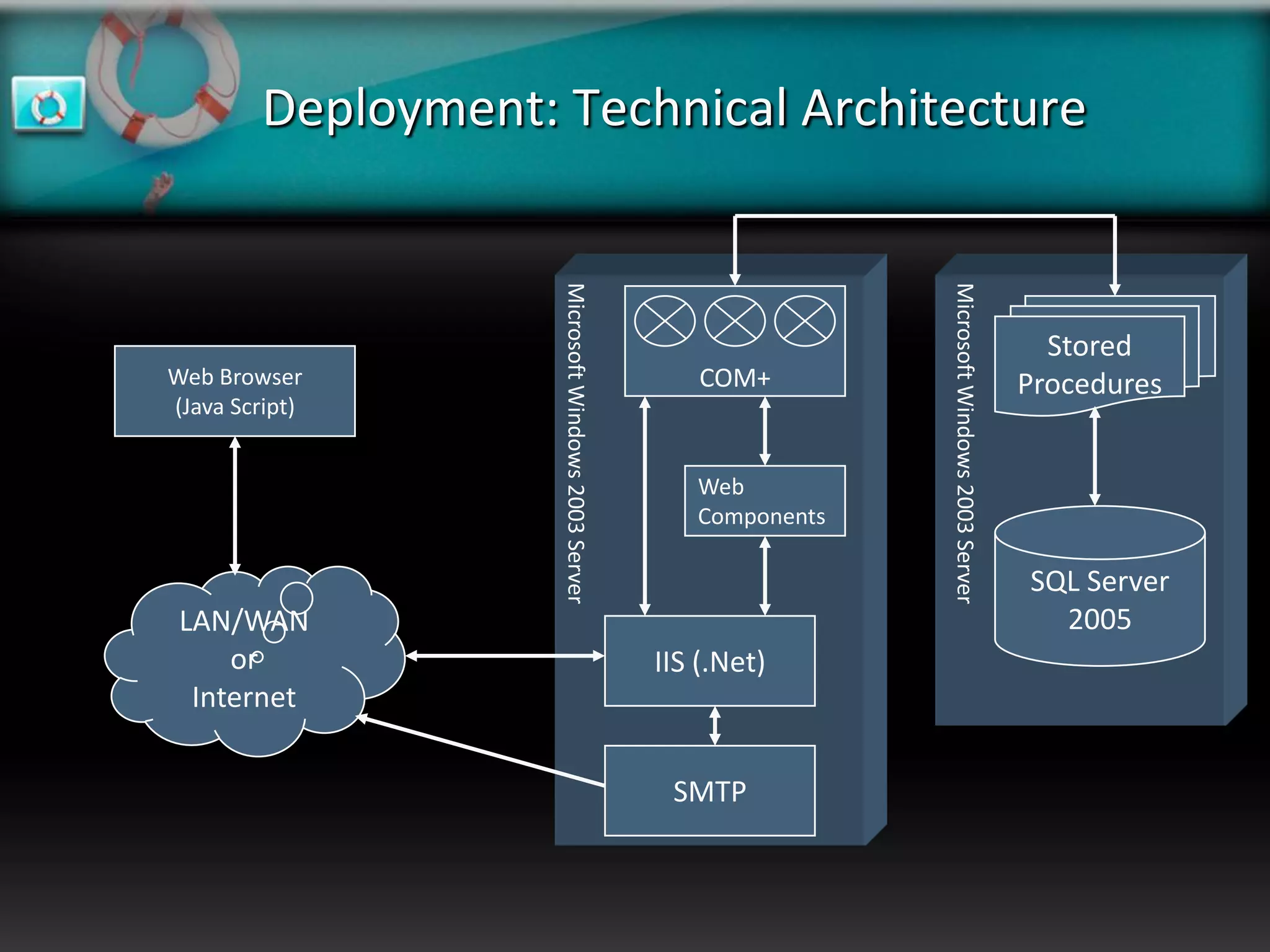
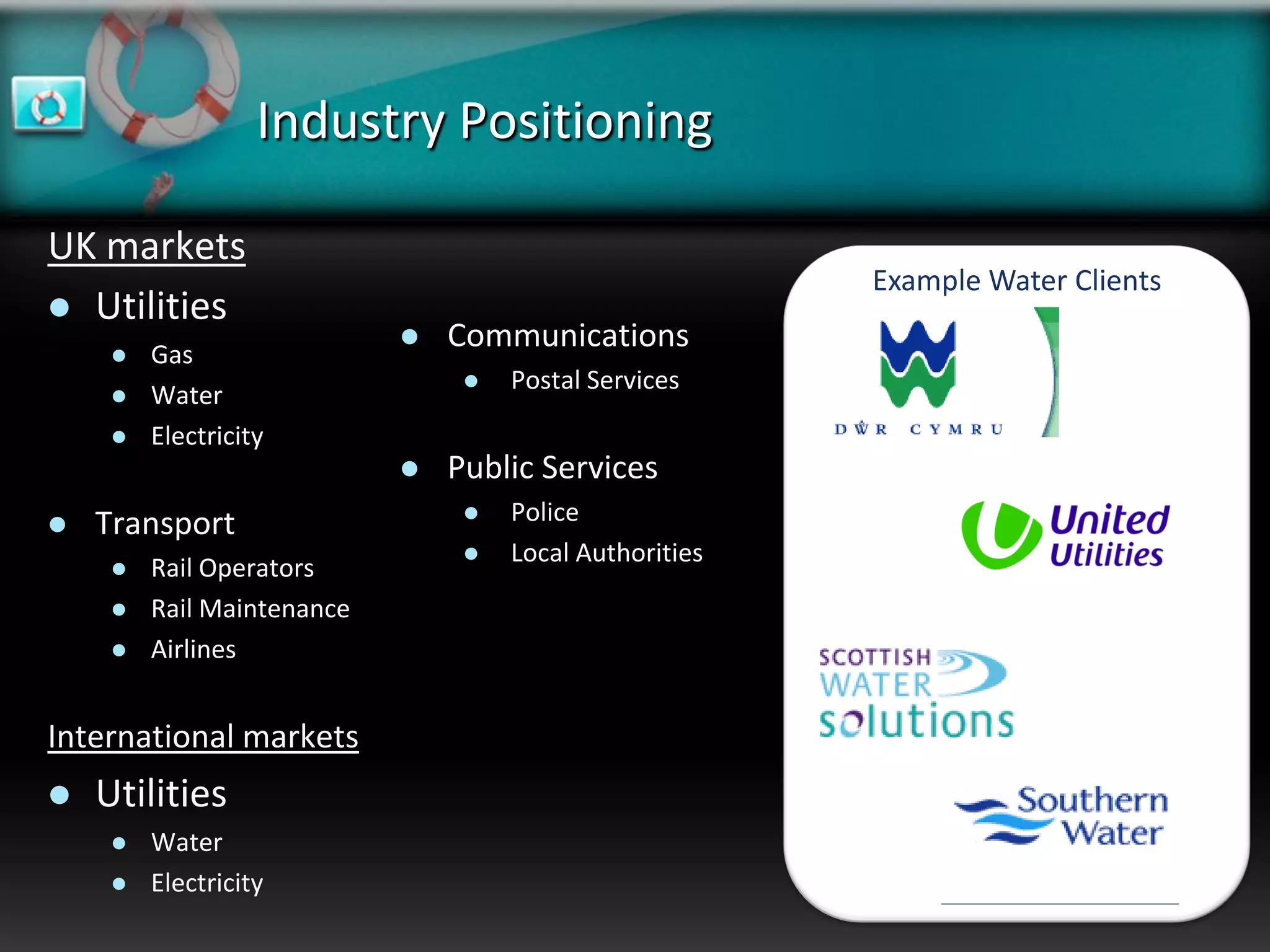
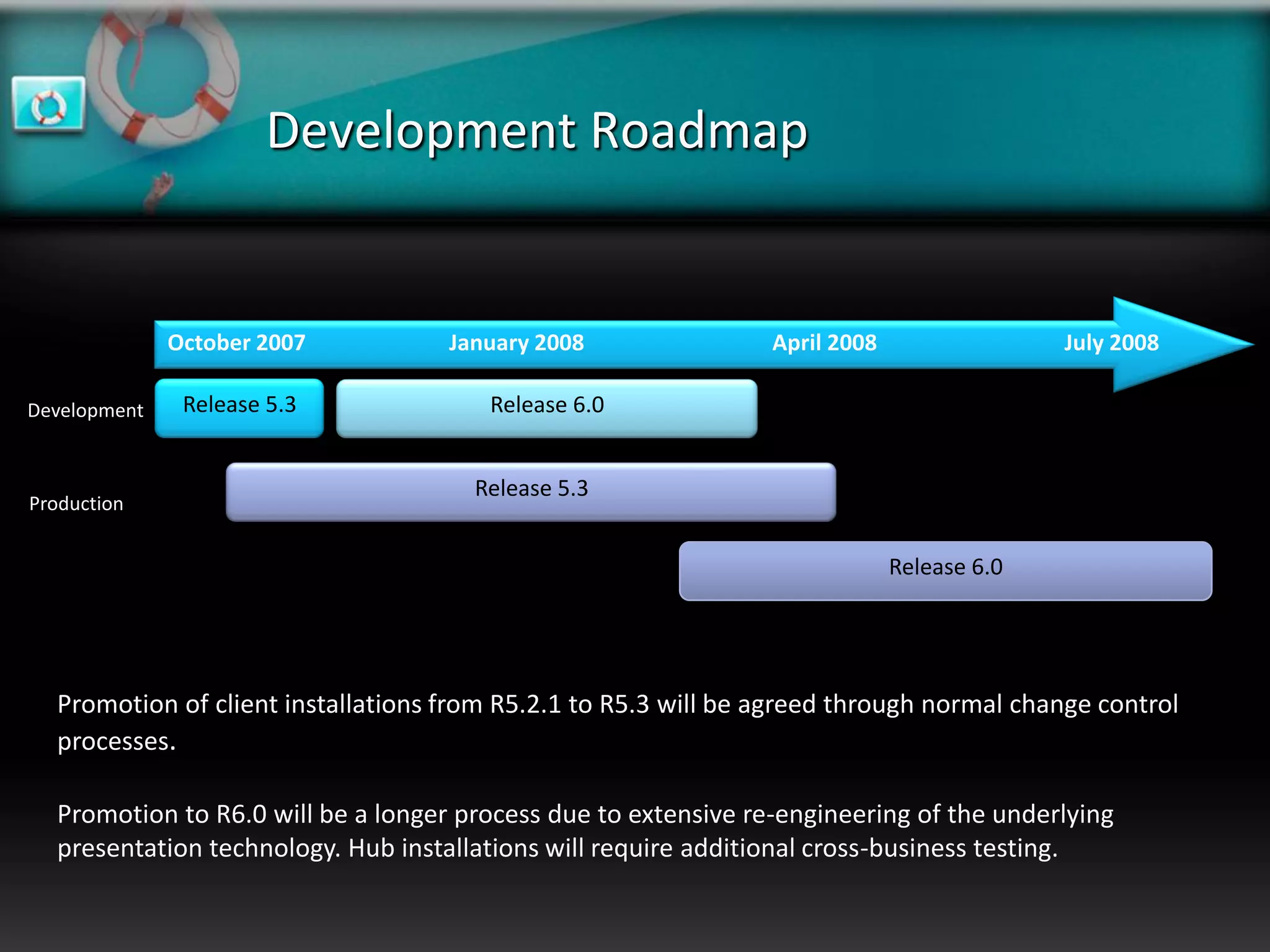
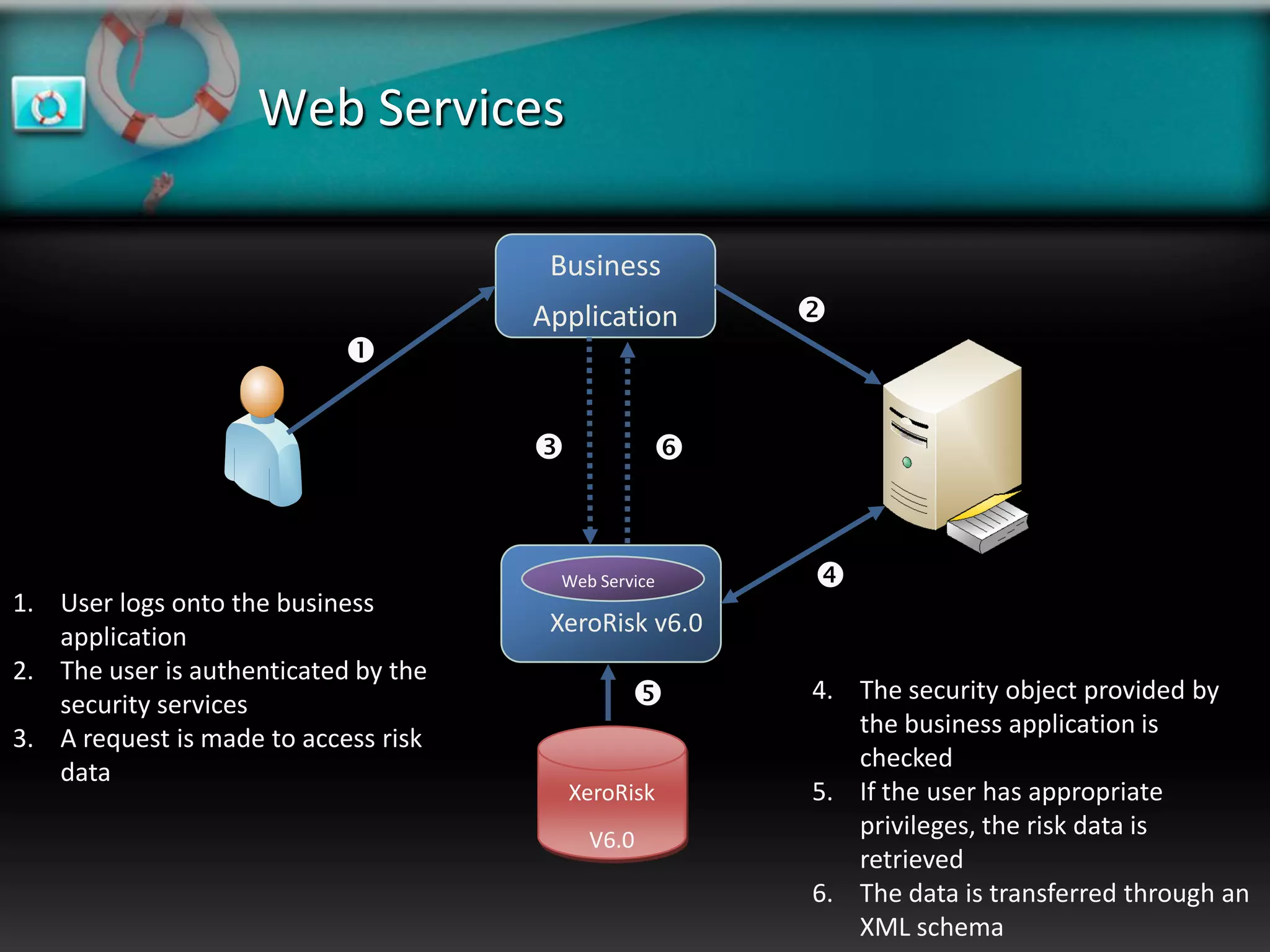
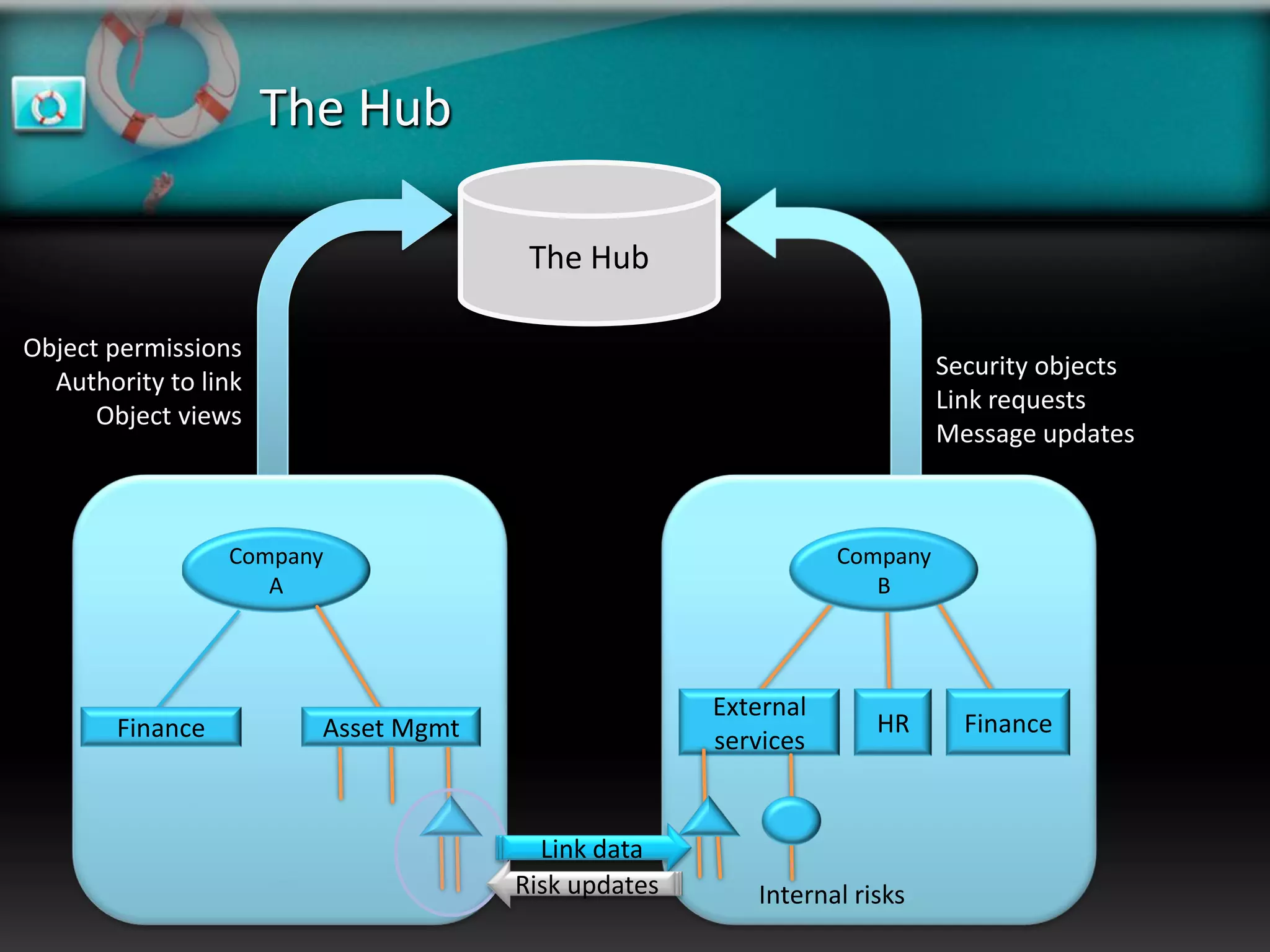
XeroRisk provides a web-based corporate risk governance solution. It offers a flexible deployment model including on-premise, hosted, and software as a service options. The software provides risk identification, assessment, monitoring and reporting capabilities. It supports risk management standards and allows integration with other business systems. Upcoming releases will include additional visualization, mobile access, and integration with a shared services hub.