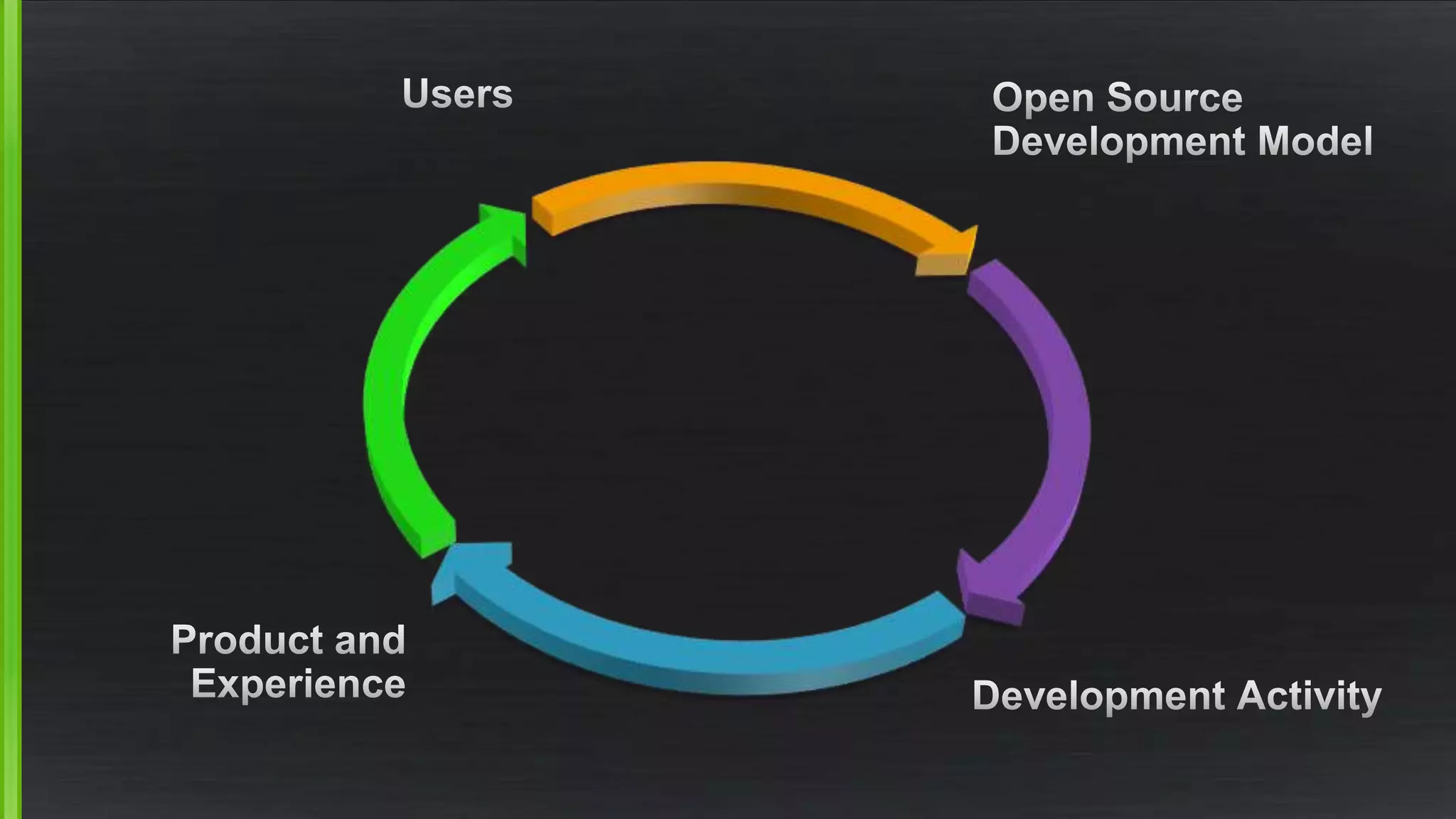
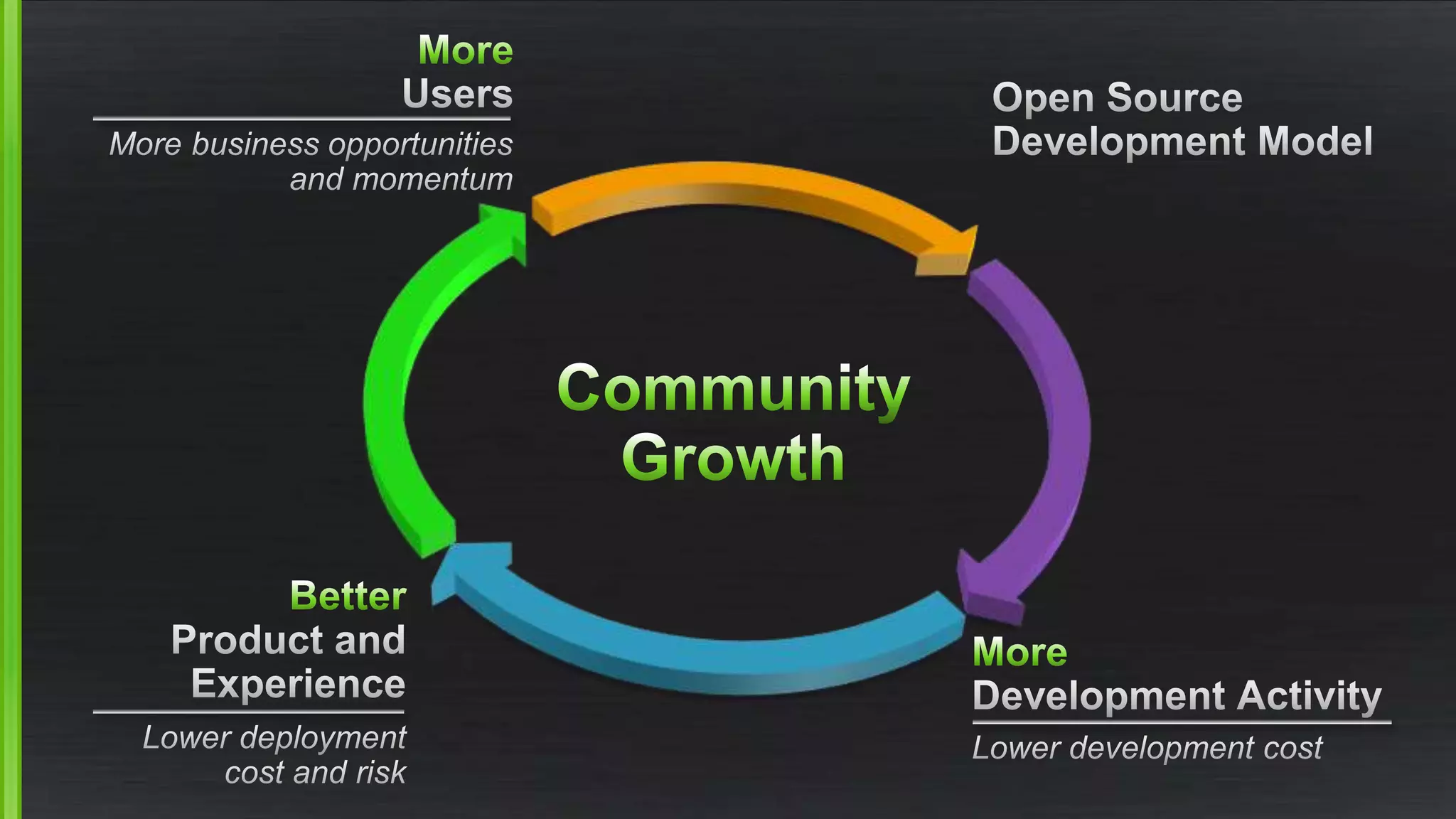
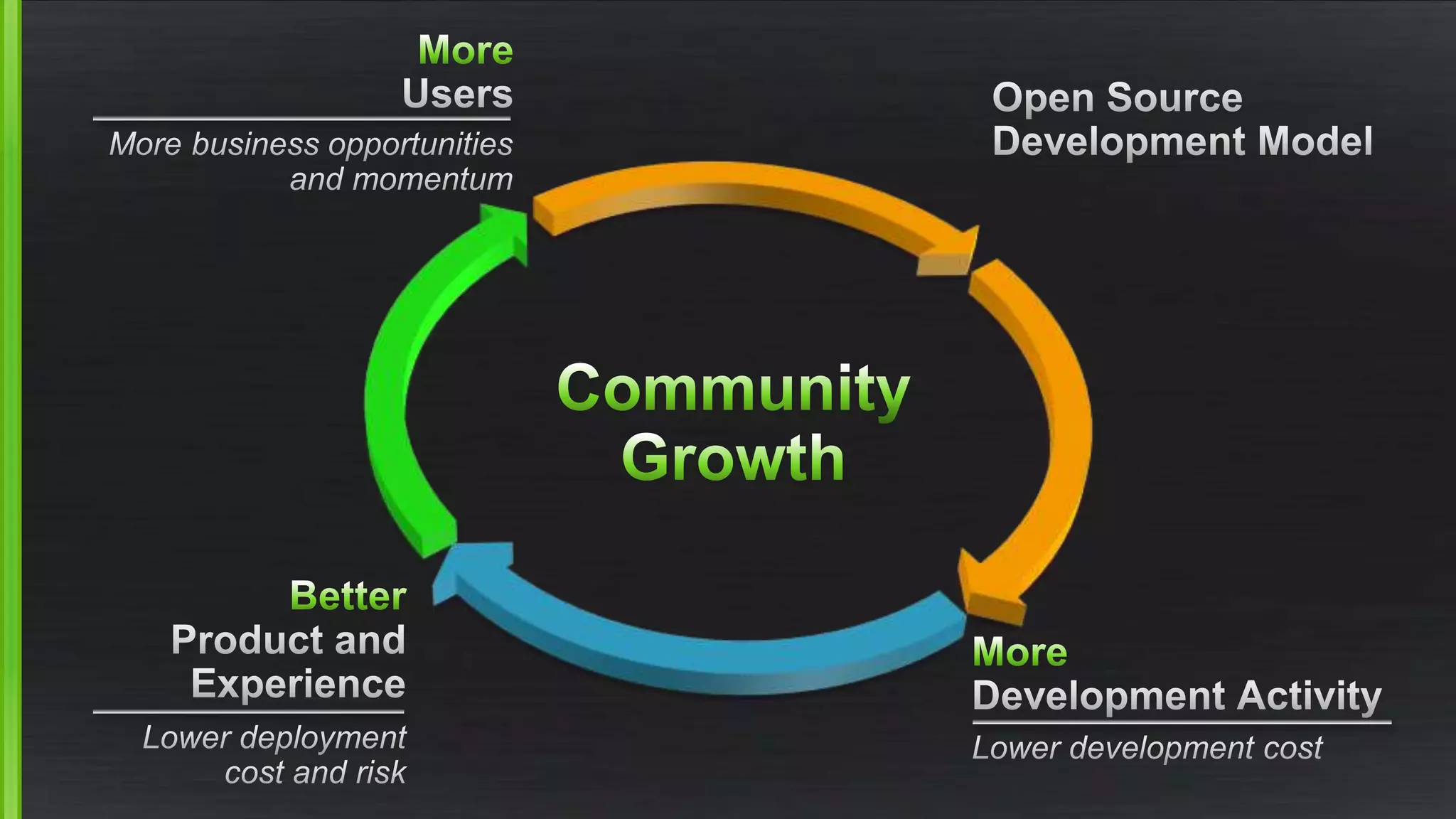
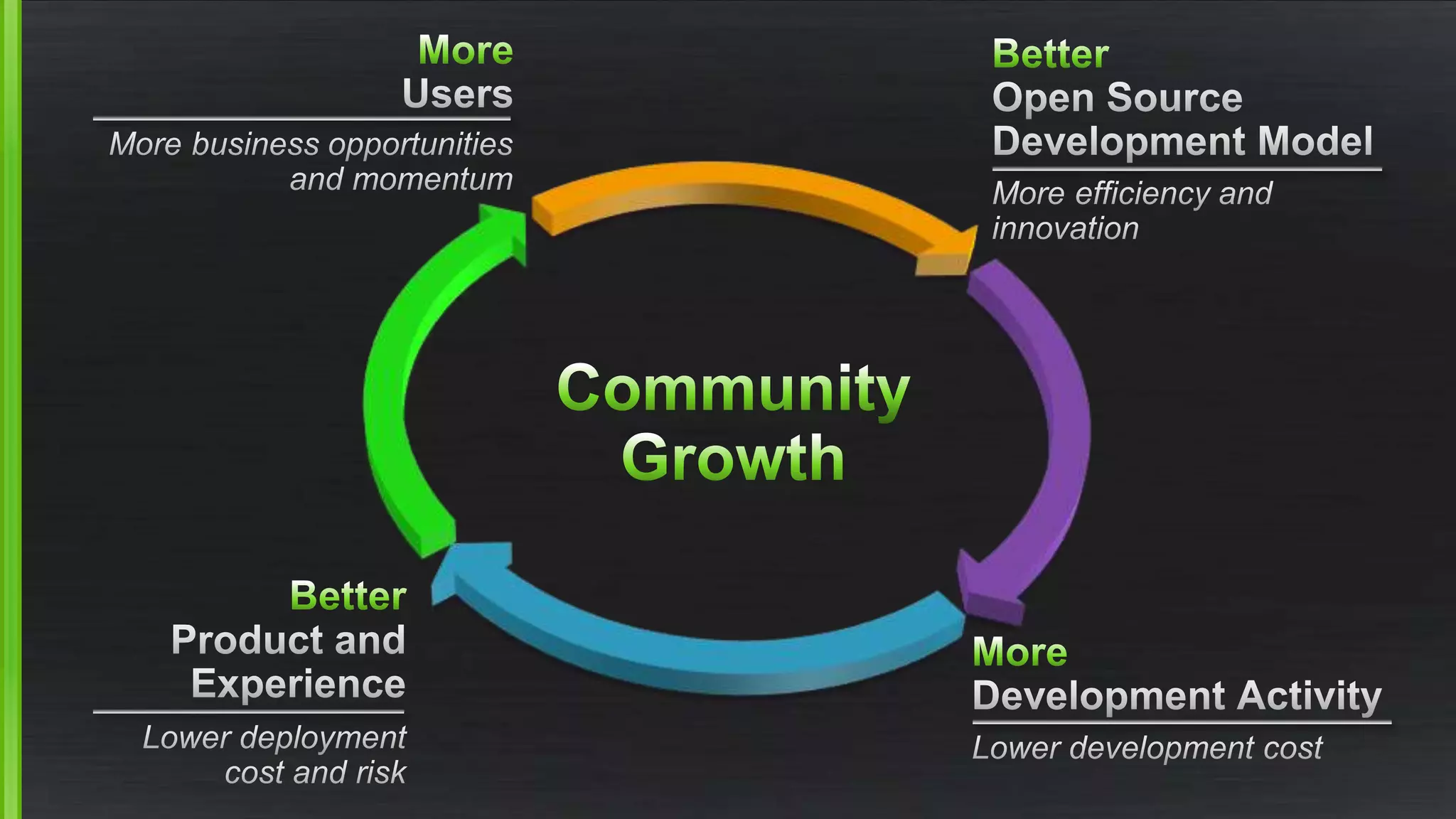
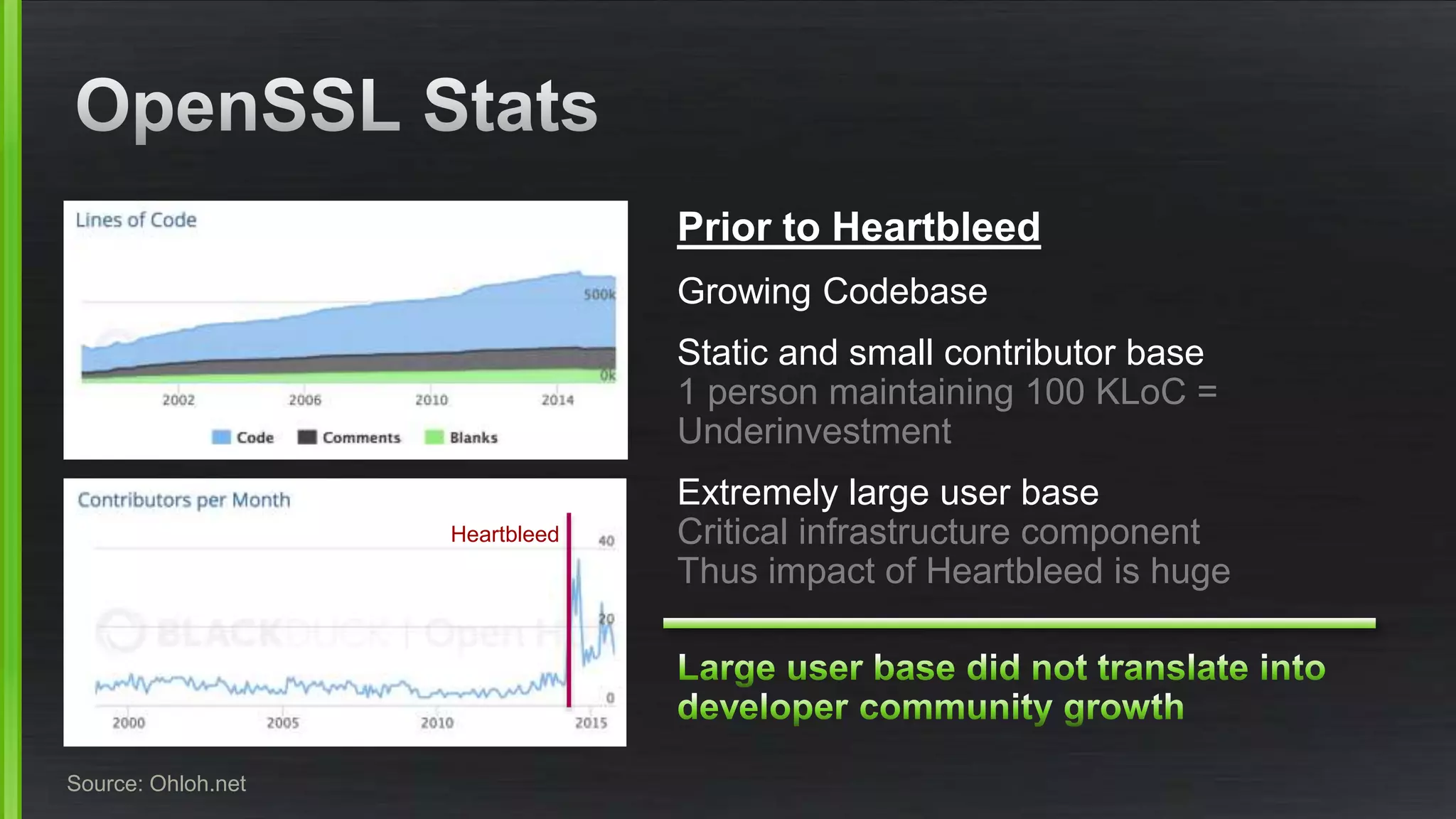
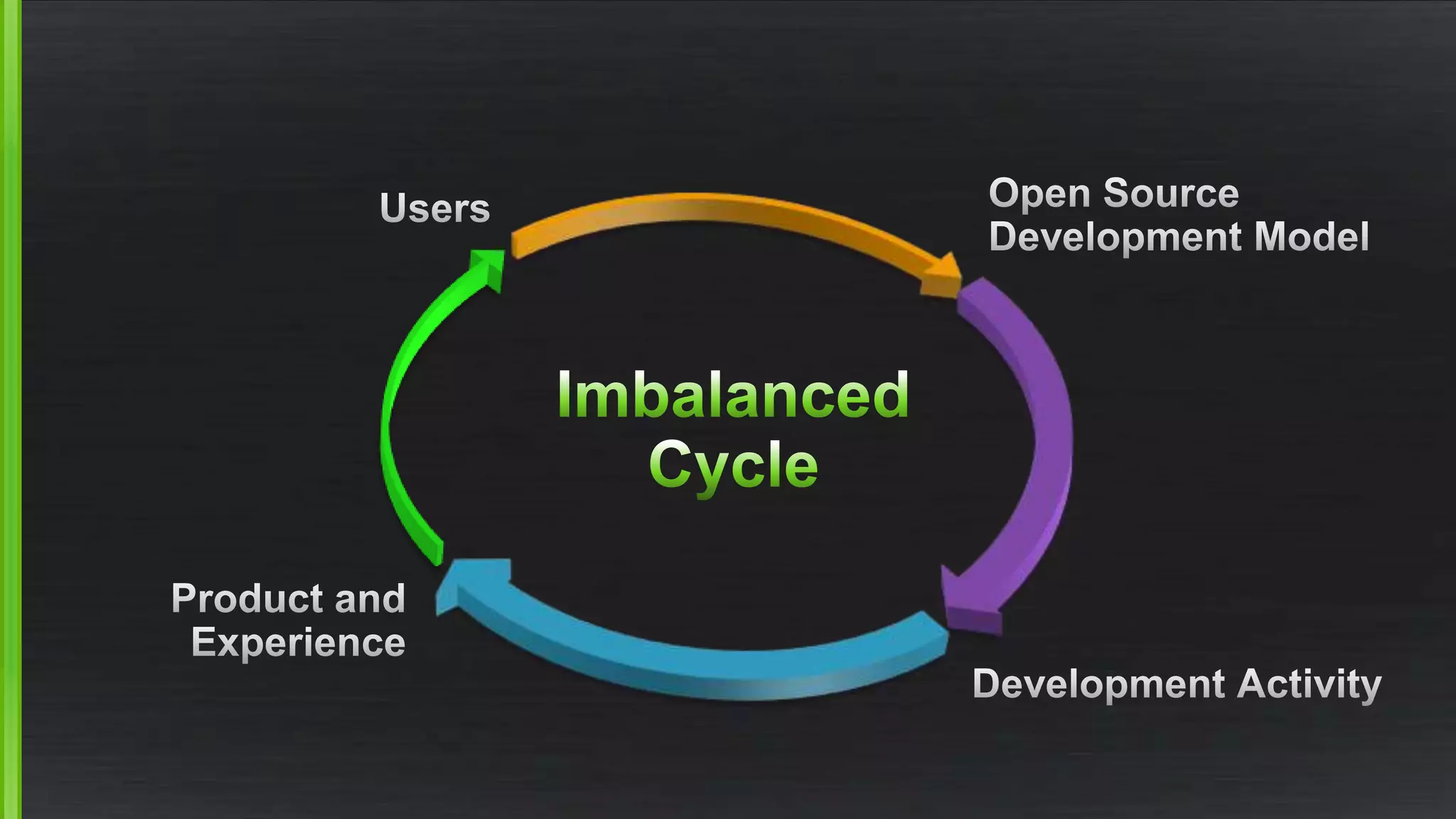
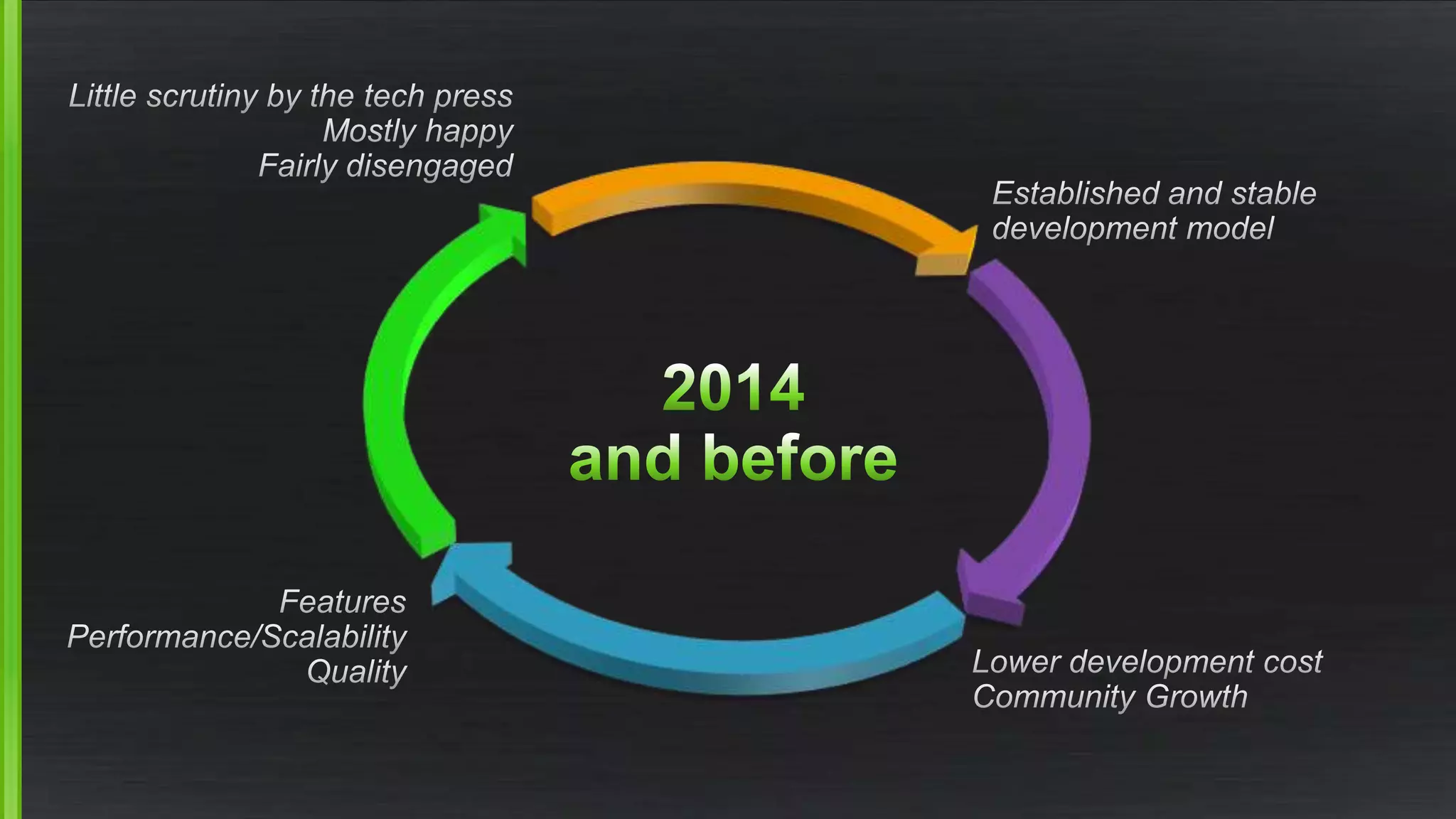
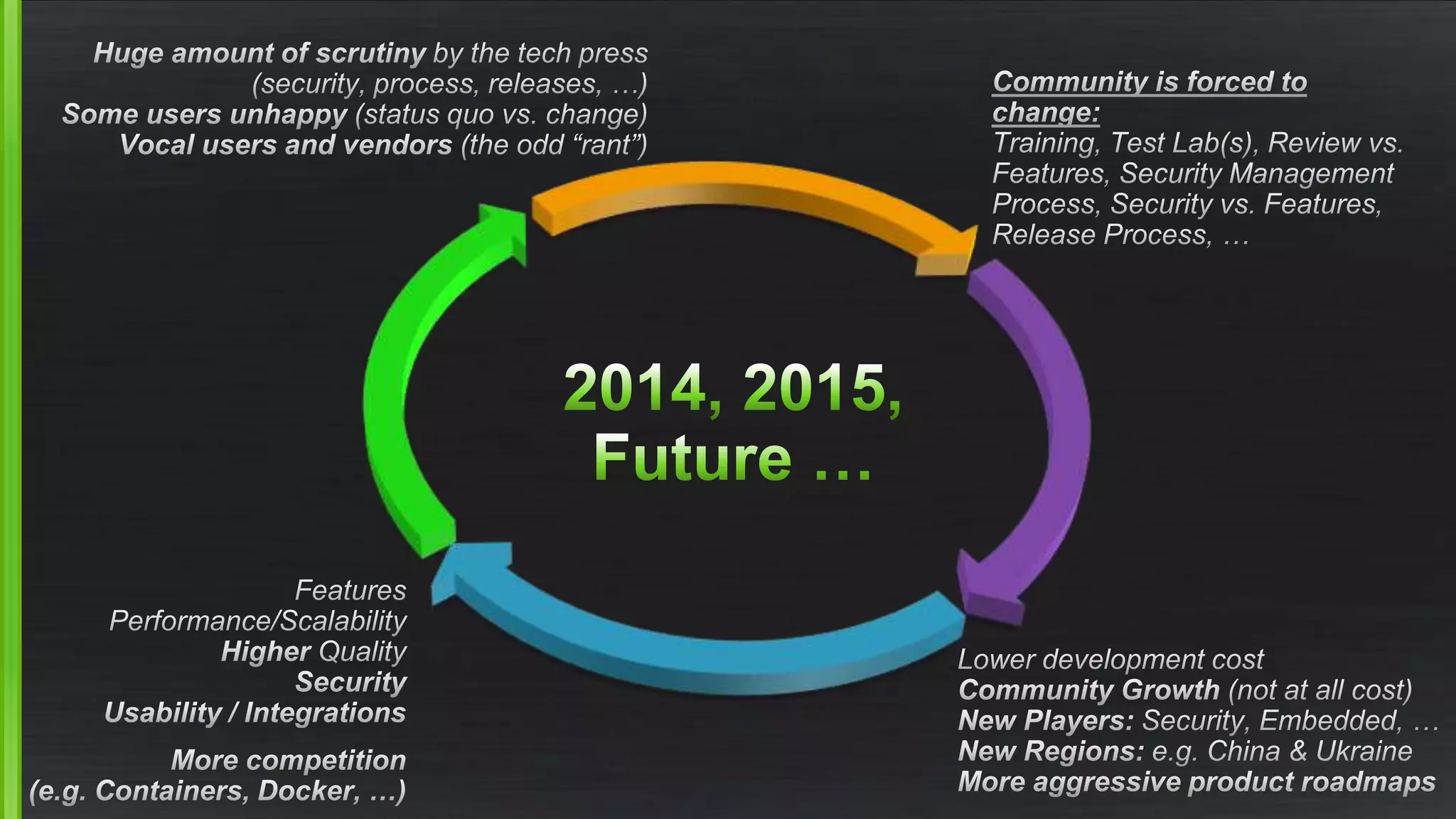
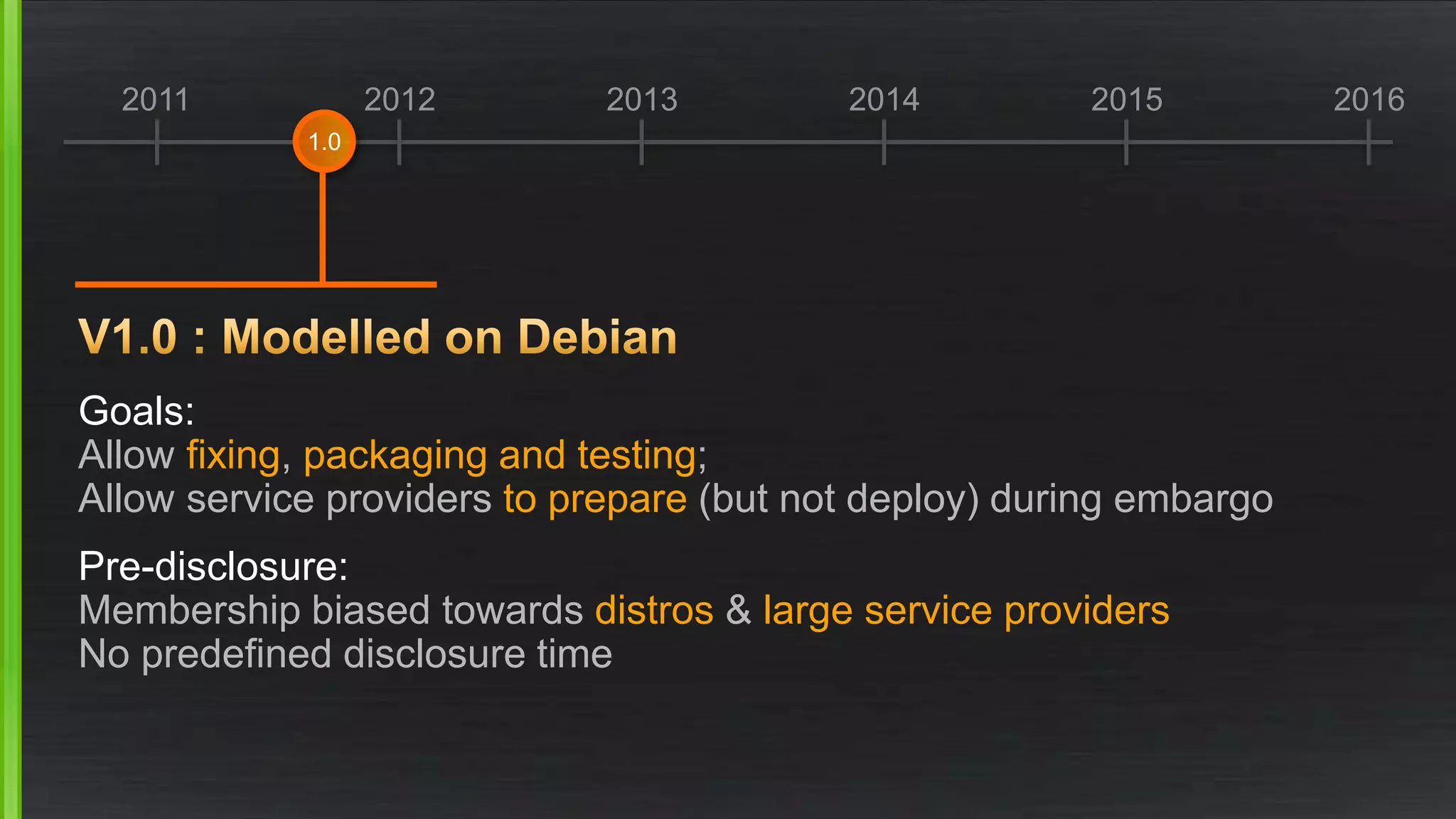
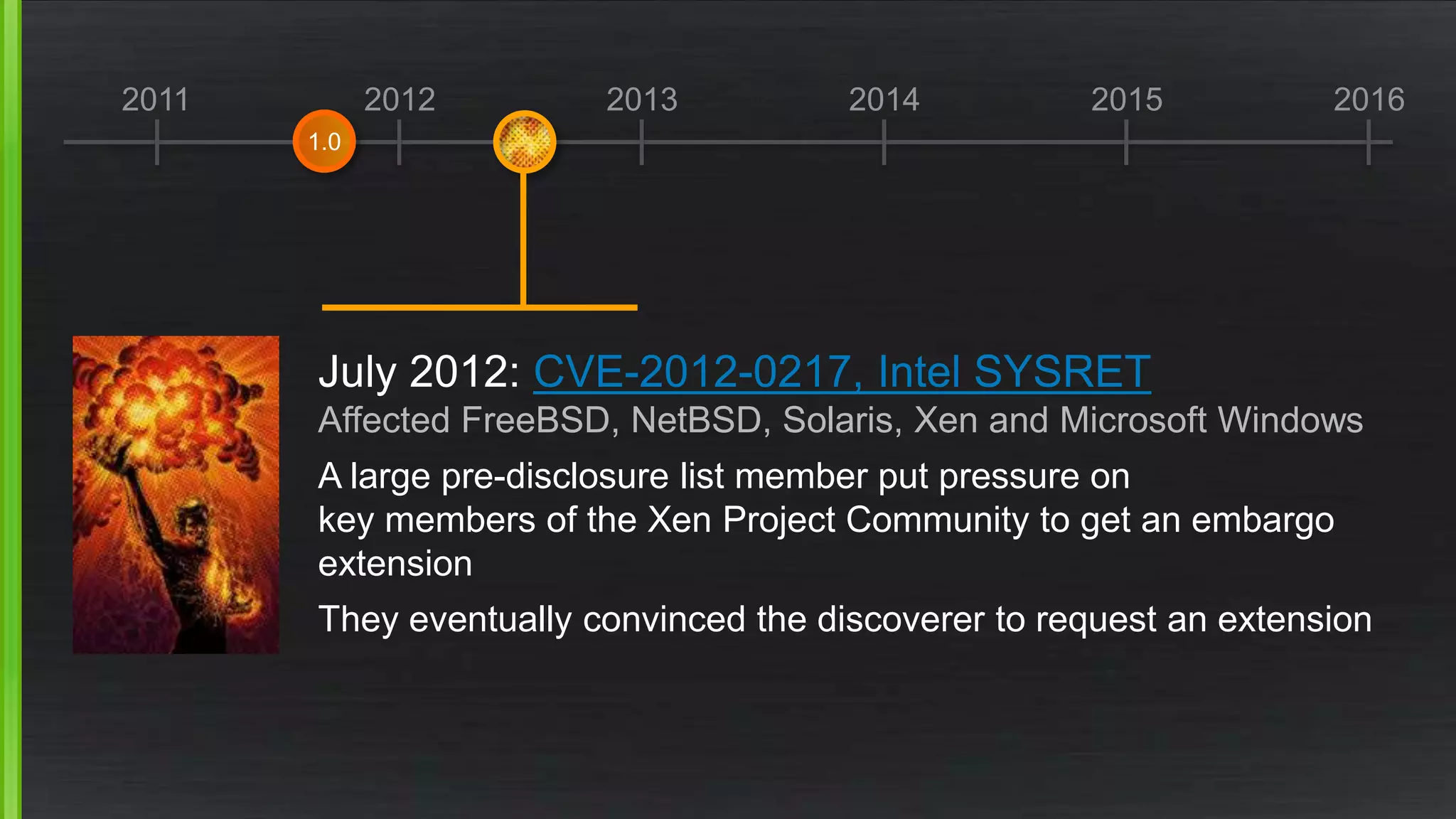
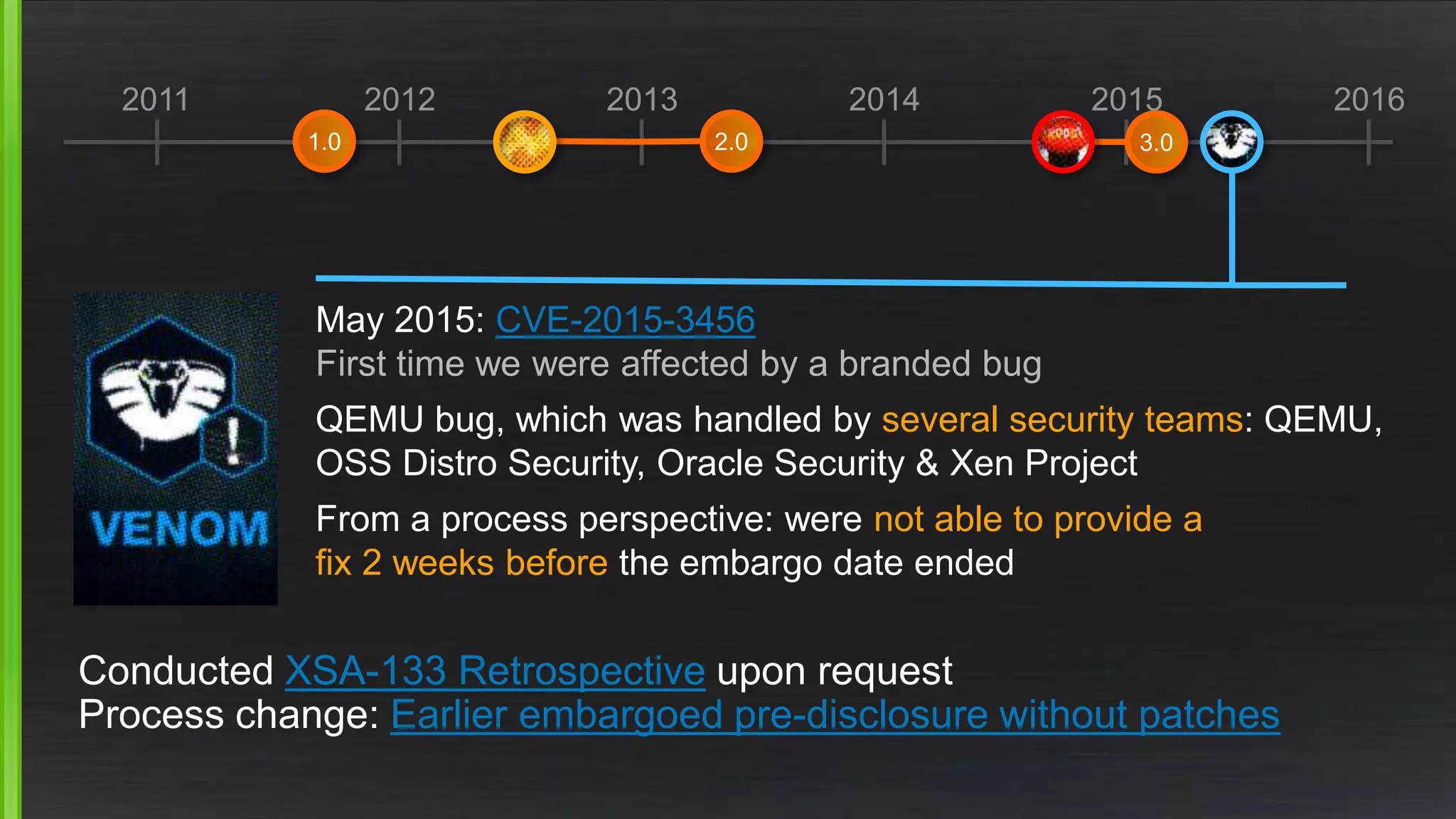
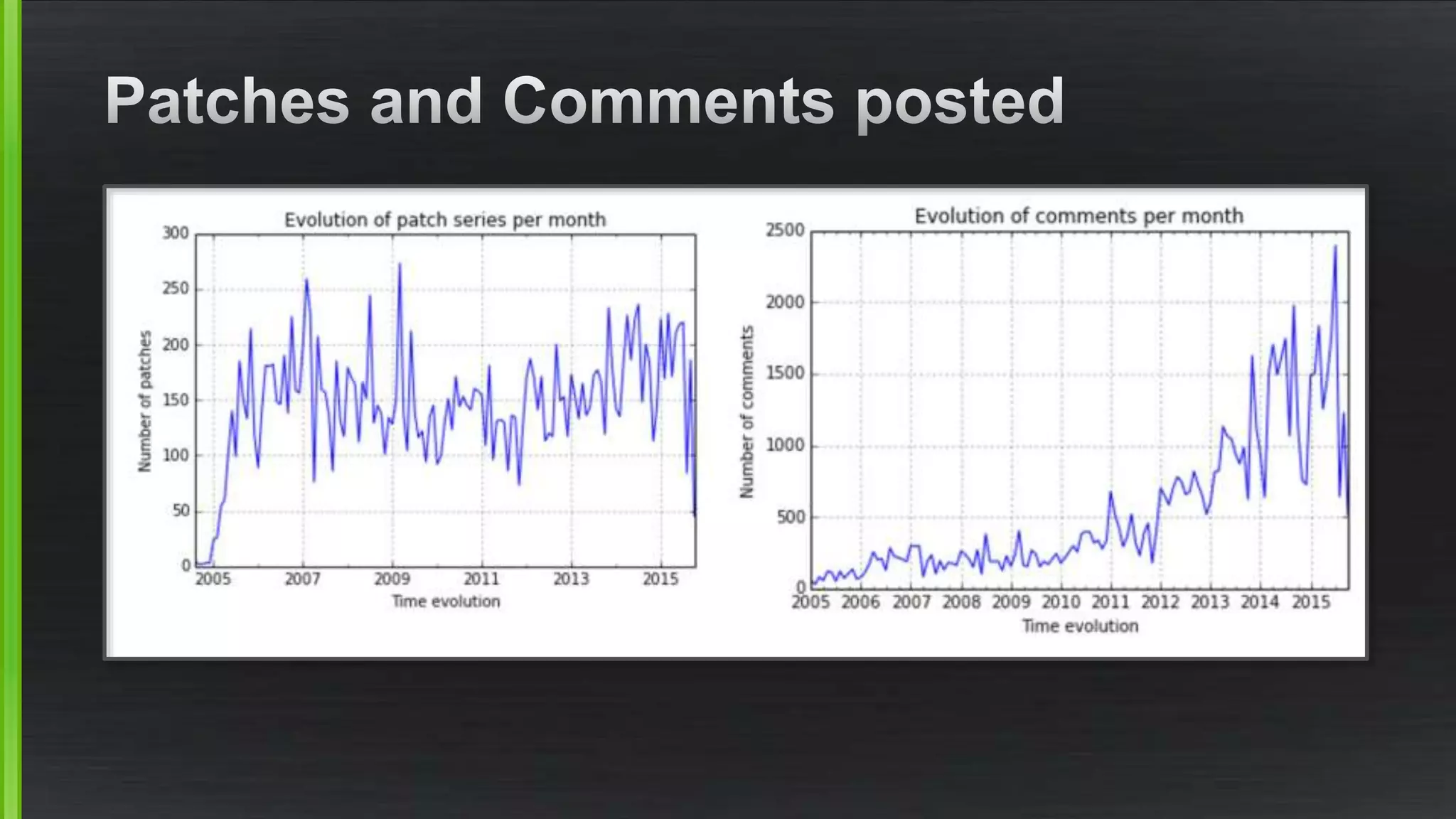
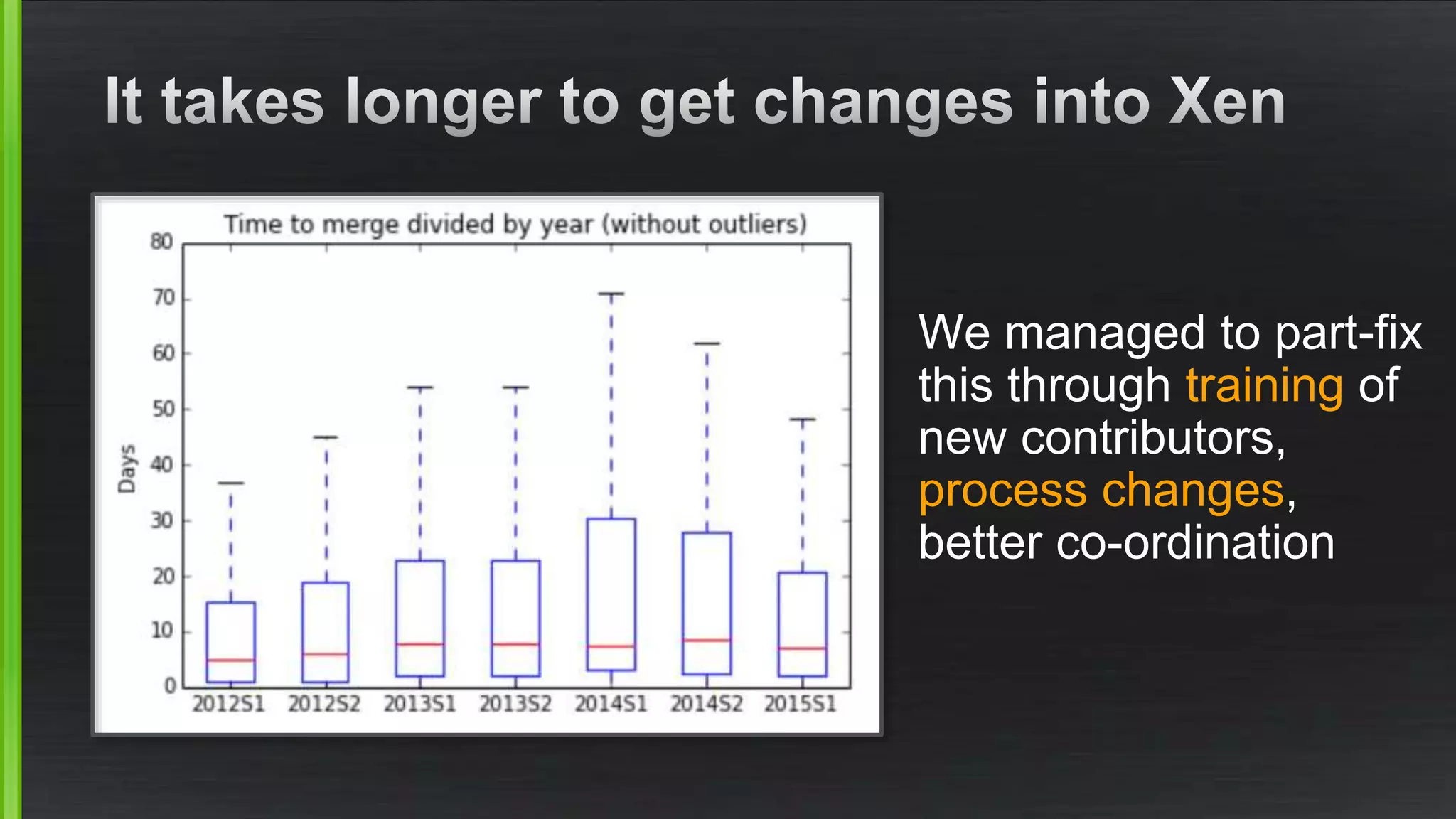
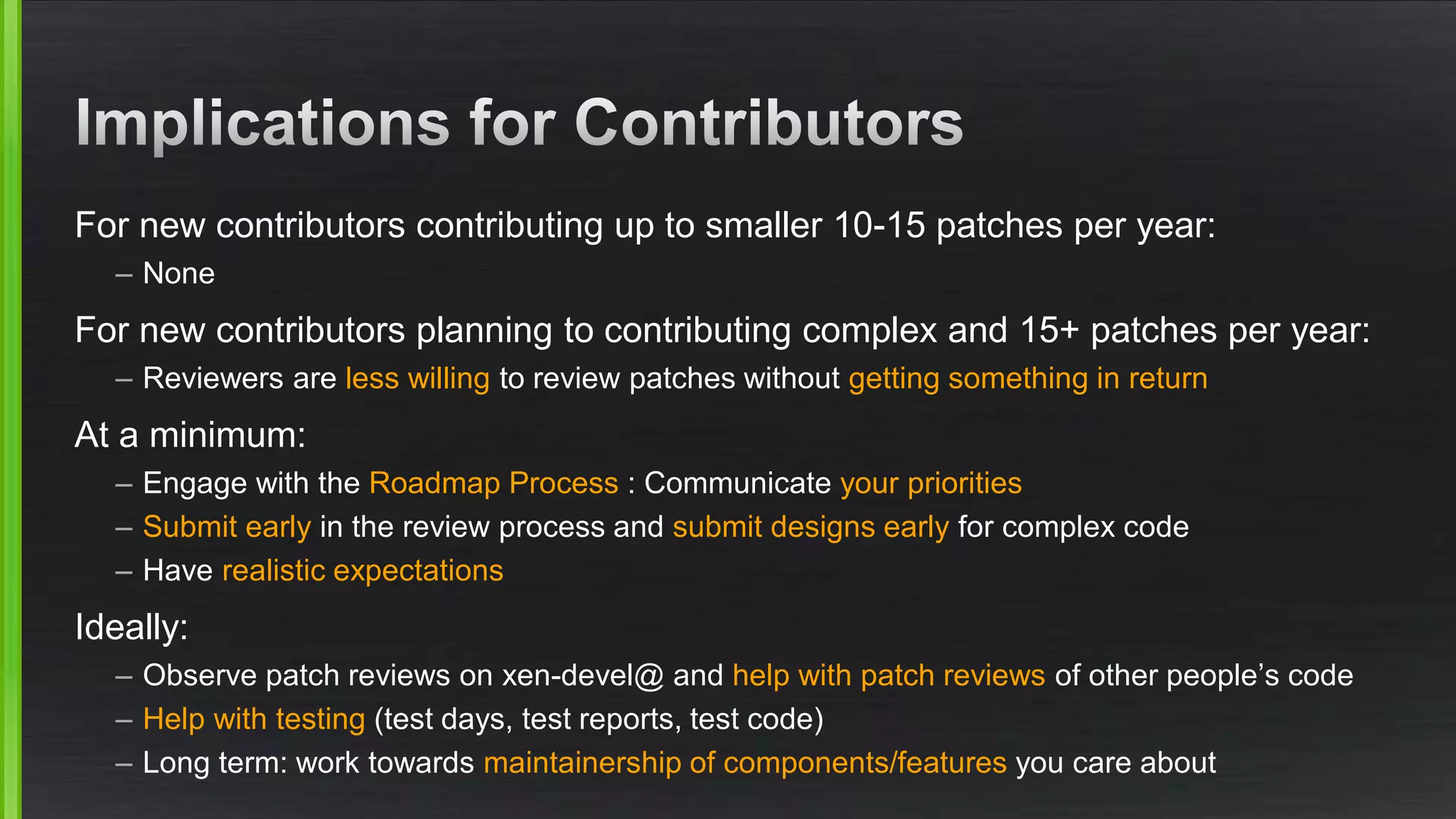
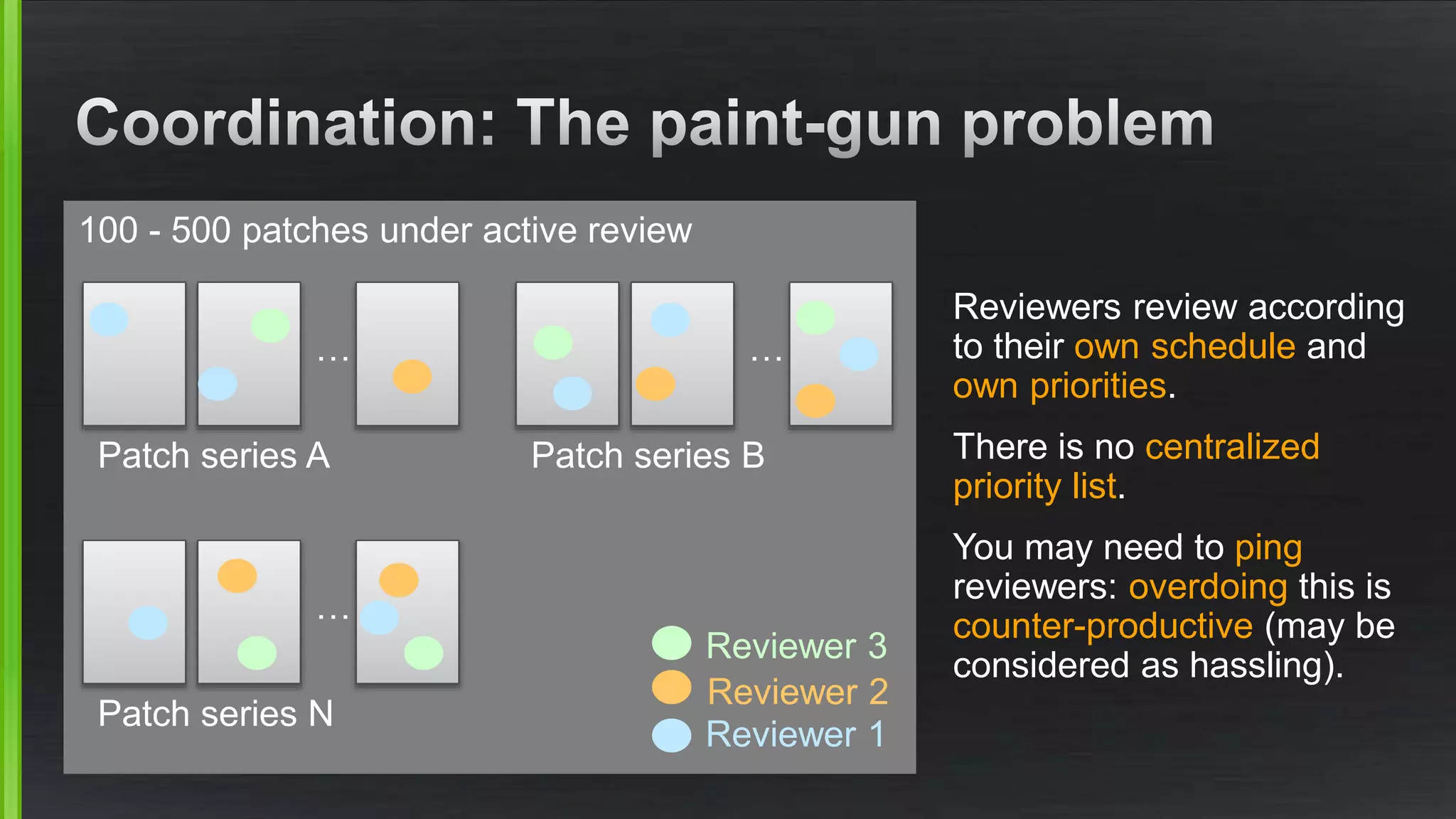
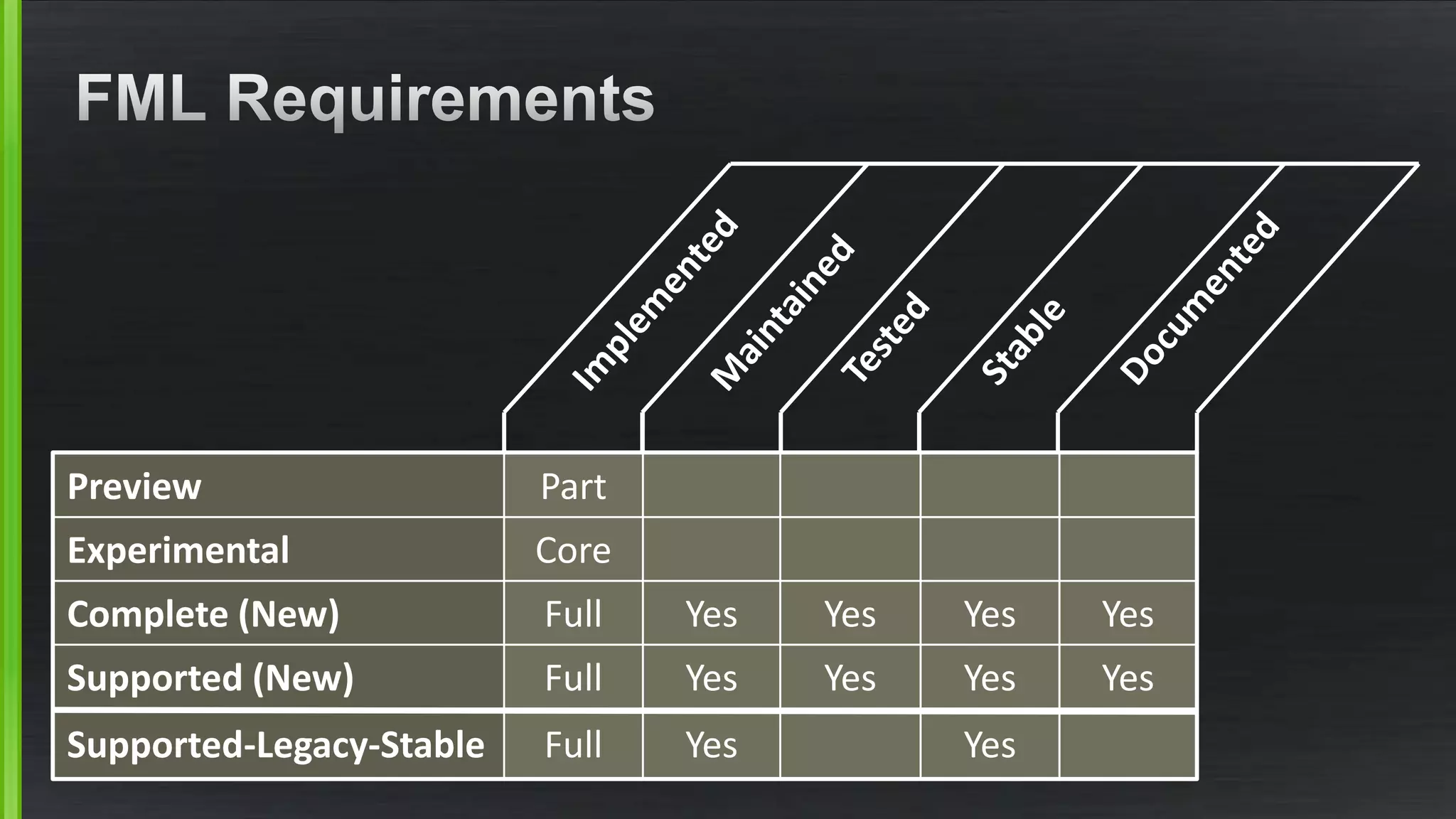
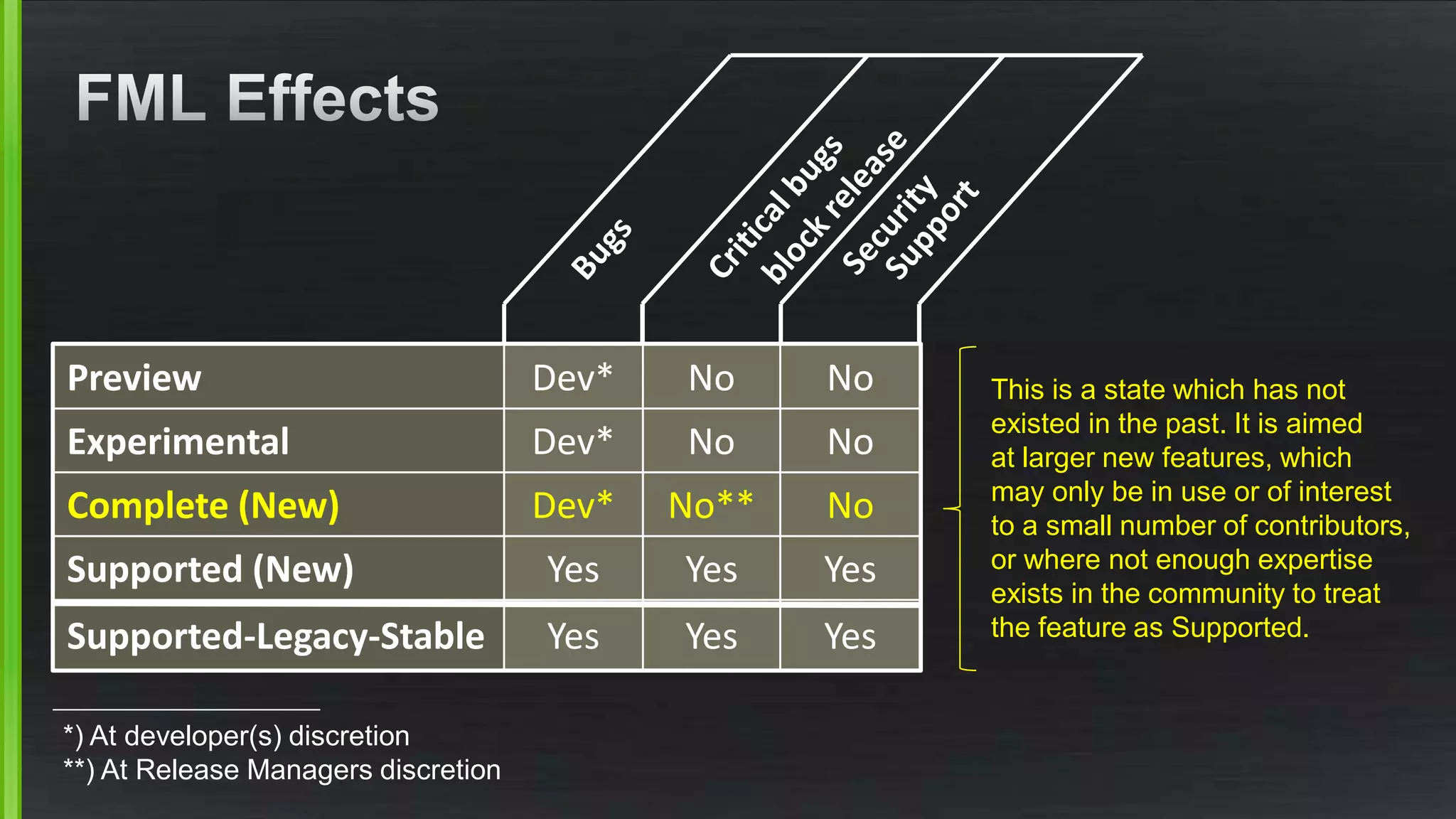
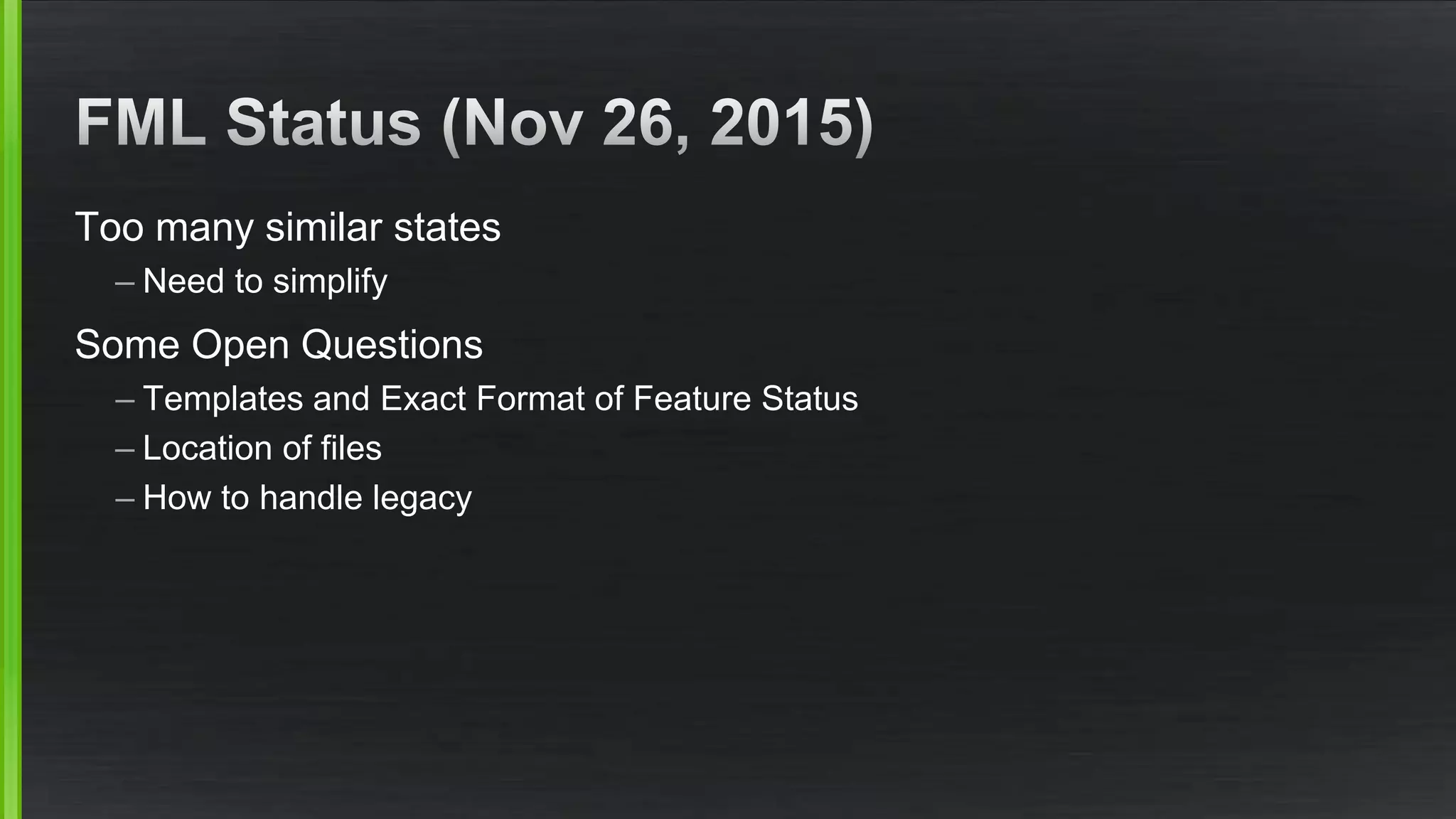
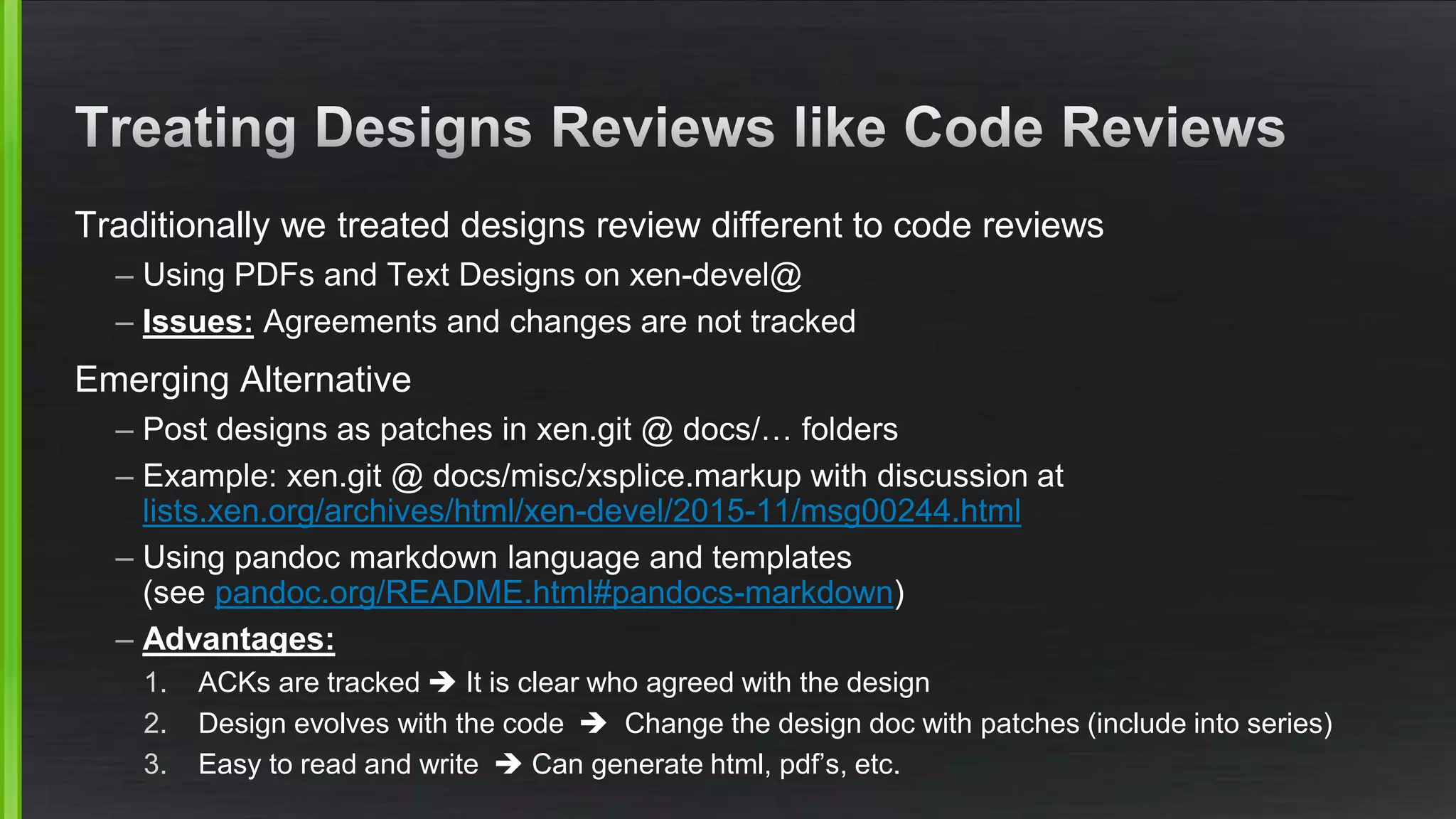
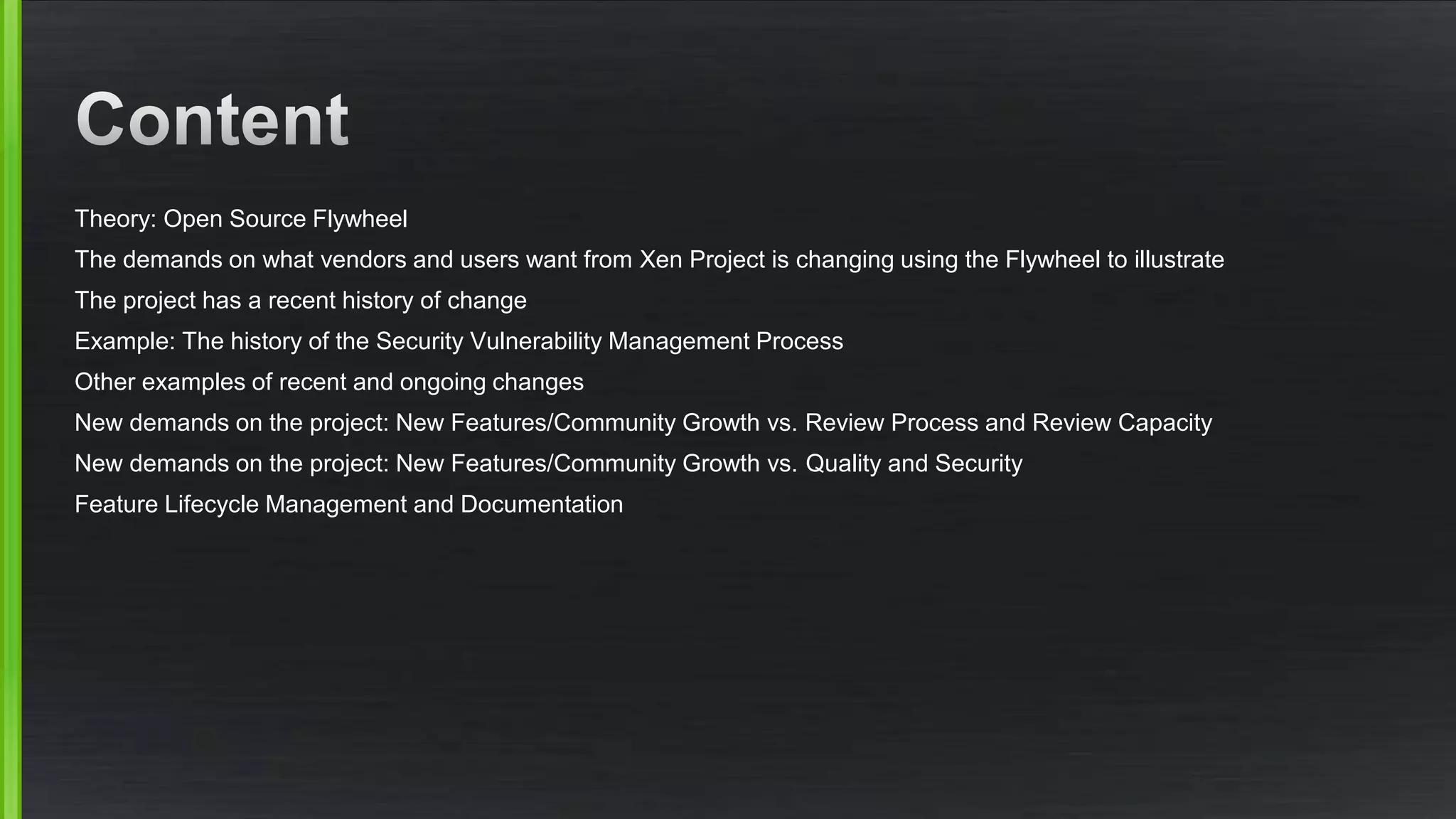
The document discusses the evolving demands on the Xen Project, detailing changes in its security vulnerability management and the increasing expectations from vendors and users. It emphasizes the need for a balanced approach to community growth, feature development, quality assurance, and security management. Additionally, it highlights the challenges faced in contribution processes, design reviews, and the impact of external factors on the project.

![[1] bit.do/optionvalue](https://image.slidesharecdn.com/xpcontributortraining-pt4culture-151126112844-lva1-app6892/75/Xen-Project-Contributor-Training-Part-4-Culture-4-2048.jpg)