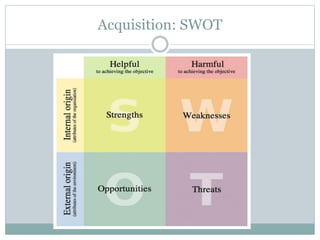
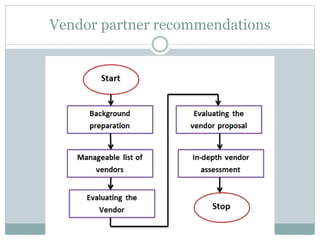
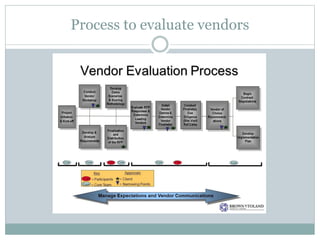
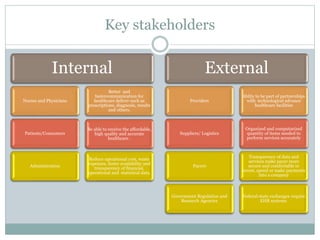
This document provides recommendations for selecting, implementing, and supporting a health information system for an organization. It identifies risks such as privacy/security of patient health information. It also notes opportunities like reducing costs and improving care quality. The document recommends evaluating vendors based on a SWOT analysis and selecting a system that meets legal/regulatory requirements and supports the organization's goals. It stresses developing a change management plan, security/privacy protections, financial sustainability, and end user support for successful implementation and ongoing use of the new system.








![References
Optical Character Recognition Technology in Health Care. (n.d.). Retrieved May 13, 2016, from
http://www.cvisiontech.com/library/ocr/file-ocr/the-use-of-optical-character-recognition-in-health-care.html
HealthIT.gov. (n.d.). Retrieved May 13, 2016, from https://www.healthit.gov/providers-professionals/faqs/how-do-i-select-vendor
HIT/EHR Vendor Contracting Checklist [Pdf]. (2011). Michigan State Medical Society.
McCall, N. (n.d.). Long Term Care: Definition, Demand,Cost,and Financing [Pdf].http://www.ache.org/pubs/1mccall.pdf
Data integration issues that a lean integration strategy can solve. (n.d.). Retrieved May 13, 2016, from
http://searchdatamanagement.techtarget.com/tutorial/Data-integration-issues-that-a-lean-integration-strategy-can-solve
Defining Change. (n.d.). Retrieved May 13, 2016, from http://www.parkeravery.co m/pov_Defining_Change_Manage ment.html
Understanding end-user support for health information technology: A theoretical framework | Shachak | Journal of Innovation in
Health Informatics. (n.d.). Retrieved May 13, 2016, from http://hijournal.bcs.org/index.p hp/jhi/article/view/810/822
Sittig, D. F., & Singh, H. (n.d.). Legal, Ethical, and Financial Dilemmas in Electronic Health Record Adoption and Use. Retrieved May
13, 2016, from http://www.ncbi.nlm.nih.gov/pmc/articles/PMC3065078/](https://image.slidesharecdn.com/9012ac14-704c-4737-8a08-69adaf9d302c-160529211102/85/WK11HIT-19-320.jpg)
![ Noraziani, K. (2013). An Overview of Electronic Medical Record Implementation in
Healthcare System: Lesson to Learn [Pdf]. Department of Community Health, Universiti
Kebangsaan Malaysia Medical Centre, Malaysia 1 Center for Applied Management
Studies, 2 Faculty of Business Management, University Technology MARA, Malaysia.
Wager, K. A., Lee, F. W., & Glaser, J. P. (2013). Health care information systems: A
practical approach for health care management (3rd ed.). San Francisco, CA: Jossey-
Bass.Chapter 11, “Security of Health Care Information Systems” (pp. 351-391)
Improving Quality in Long-Term Care. (n.d.). Retrieved March 21, 2016, from
http://www.commonwealthfund.org/publications/literature-
abstracts/2010/aug/improving-quality-in-long-term-care
New CMS rules may spur EHR uptake. (2015). Retrieved May 13, 2016, from
http://www.healthcareitnews.com/news/long-term-cares-digital-moment
Sheehan, P. (n.d.). Technology takes off in long-term care. Retrieved May 13,
2016, from http://www.ltlmagazine.com/article/technology-takes-long-term-
care](https://image.slidesharecdn.com/9012ac14-704c-4737-8a08-69adaf9d302c-160529211102/85/WK11HIT-20-320.jpg)